2013-08-10 - BLACKHOLE EXPLOIT KIT FROM 173.246.105[.]15 - ELIEHABIB[.]COM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2013-08-10-Blackhole-EK-traffic.pcap.zip 1.2 MB (1,212,047 bytes)
- 2013-08-10-Blackhole-EK-malware.zip 378.5 kB (378,534 bytes)
NOTES:
Within the past week or so, some people have noted another fake efax phishing campaign with "message@inbound.efax[.]com" as a spoofed sending address. Dynamoo's Blog has a write-up where one of these phishing emails generates traffic with eliehabib[.]com as a malware payload site. In Dynamoo's Blog, the malware payload URL is eliehabib[.]com/topic/seconds-exist-foot.php. I found a similar URL dated 07 July 2013 that was probably used in the phishing campaign, too. In this case was eliehabib[.]com/topic/regard_alternate_sheet.php was the malware payload URL.
I could not replicate the infection chain of events before the eliehabib[.]com URL, but let's examine the Snort IDS events and the traffic if someone would've went to the malware payload URL...
SNORT EVENTS
As usual, I set up a bare-metal instal of Windows 7 SP1 with IE 8 and Java Runtime Environment 6 update 25. Monitoring this setup was an installation of Security Onion. When I visited eliehabib[.]com/topic/regard_alternate_sheet.php on the vulnerable host, the following events triggered in Sguil:

- 173.246.105[.]15 port 80 - 192.168.1[.]106 port 49161 - ET CURRENT_EVENTS SUSPICIOUS JAR Download by Java UA with non JAR EXT matches various EKs
- 173.246.105[.]15 port 80 - 192.168.1[.]106 port 49161 - ET INFO JAVA - Java Archive Download By Vulnerable Client
- 192.168.1[.]106 port 49162 - 173.246.105[.]15 port 80 - ET CURRENT_EVENTS BlackHole EK Variant Payload Download
- 173.246.105[.]15 port 80 - 192.168.1[.]106 port 49162 - ET INFO EXE - Served Attached HTTP
- 173.246.105[.]15 port 80 - 192.168.1[.]106 port 49162 - ET INFO Packed Executable Download
- 173.246.105[.]15 port 80 - 192.168.1[.]106 port 49162 - ET CURRENT_EVENTS DRIVEBY Blackhole - Payload Download - info.exe
- 173.246.105[.]15 port 80 - 192.168.1[.]106 port 49162 - ET POLICY PE EXE or DLL Windows file download
- 173.246.105[.]15 port 80 - 192.168.1[.]106 port 49162 - ET TROJAN Java EXE Download by Vulnerable Version - Likely Driveby
- 69.162.154[.]23 port 80 - 192.168.1[.]106 port 49170 - ET SHELLCODE Possible Call with No Offset TCP Shellcode
- 69.162.154[.]23 port 80 - 192.168.1[.]106 port 49170 - ET POLICY PE EXE or DLL Windows file download
INFECTION TRAFFIC
Infection from the malware delivery domain:
- 07:16:47 GMT - 192.168.1[.]106 port 49159 - 173.246.105[.]15 port 80 - GET /topic/regard_alternate_sheet.php
- 07:16:56 GMT - 192.168.1[.]106 port 49161 - 173.246.105[.]15 port 80 - GET /topic/regard_alternate_sheet.php?sCgjKzq=XxMXwha&AfptP=QsWlvzPz [Java exploit]
- 07:16:57 GMT - 192.168.1[.]106 port 49162 - 173.246.105[.]15 port 80 - GET /topic/regard_alternate_sheet.php?Ef=5632562f57&Ee=2i2e542i322f572j2h2g&R=2d&Gz=f&bj=Z [malicious binary: Trojan downloader]
Two more malware downloads caused by the Trojan downloader:
- 07:18:18 GMT - 192.168.1[.]106 port 49170 - 69.162.154[.]23 port 80 - GET /s86.exe
- 07:18:24 GMT - 192.168.1[.]106 port 49172 - 95.130.11[.]213 port 80 - GET /
INFECTION TRAFFIC DETAILS
GET /topic/regard_alternate_sheet.php
IP address: 173.246.105[.]15
domain name: eliehabib[.]com
Events: None
In some cases, you might have a Snort event for an exploit kit landing page, based on a string match in the HTTP GET request. This is a relatively new landing page pattern in the URL, and based on what I've seen so far, we might not get a Snort rule for it.
This sets up the HTTP GET request for the Java exploit...
GET /topic/regard_alternate_sheet.php?sCgjKzq=XxMXwha&AfptP=QsWlvzPz
IP address: 173.246.105[.]15
domain name: eliehabib[.]com
Events:
- ET CURRENT_EVENTS SUSPICIOUS JAR Download by Java UA with non JAR EXT matches various EKs
- ET INFO JAVA - Java Archive Download By Vulnerable Client
Screenshot of traffic:
The Java exploit is successful, and it retrieves the first malicious binary...
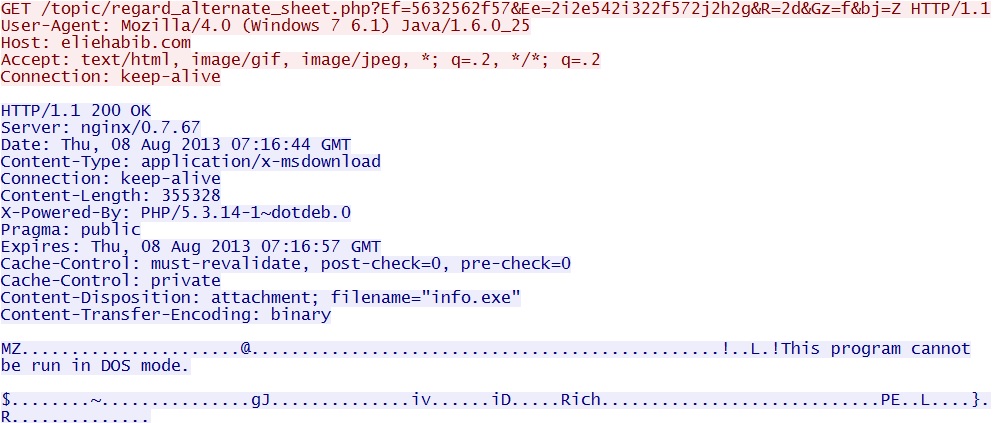
GET /topic/regard_alternate_sheet.php?Ef=5632562f57&Ee=2i2e542i322f572j2h2g&R=2d&Gz=f&bj=Z
IP address: 173.246.105[.]15
domain name: eliehabib[.]com
Events:
- ET CURRENT_EVENTS BlackHole EK Variant Payload Download
- ET INFO EXE - Served Attached HTTP
- ET INFO Packed Executable Download
- ET CURRENT_EVENTS DRIVEBY Blackhole - Payload Download - info.exe
- ET POLICY PE EXE or DLL Windows file download
- ET TROJAN Java EXE Download by Vulnerable Version - Likely Driveby
Screenshot of traffic:
The first malicious binary is apparently a Trojan downloader, because we see a follow-up HTTP GET request which is not using Java as a user agent...
GET /s86.exe
IP address: 69.162.154[.]23
domain name: davidgartonministry[.]org
Events:
- ET SHELLCODE Possible Call with No Offset TCP Shellcode
- ET POLICY PE EXE or DLL Windows file download
Screenshot of traffic:
GET /
IP address: 95.130.11[.]213
domain name: finddecisions[.]com
Events: none
Screenshot of traffic:
This callback traffic might just be to check if the domain is available. There's no data sent back, and we see other TCP traffic to 95.130.11[.]213 that happened outside of port 80. We also see other UDP and TCP traffic to various IP addresses...
TCP traffic:
- 50.65.158[.]6
- 64.84.8[.]194 (RST each time in reply)
- 64.233.134[.]54 (no response)
- 76.65.212[.]217 (no response)
- 76.241.58[.]101 (no response)
- 95.130.11[.]213
- 130.251.186[.]103
- 173.246.105[.]15 (RST each time in reply)
- 184.148.89[.]74 (no response)
- 206.255.103[.]64
UDP traffic:
- 1.168.39[.]189
- 50.65.158[.]6
- 64.61.15[.]190
- 64.233.134[.]54
- 67.4.45[.]112
- 67.214.72[.]156
- 68.94.8[.]194
- 68.127.83[.]159
- 69.115.119[.]227
- 75.80.50[.]135
- 76.65.212[.]217
- 76.241.58[.]101
- 78.87.111[.]91
- 79.214.59[.]185
- 88.68.122[.]74
- 99.26.122[.]34
- 99.146.98[.]160
- 99.181.10[.]118
- 108.74.172[.]39
- 108.210.216[.]93
- 108.234.133[.]110
- 130.251.186[.]103
- 157.100.168[.]252
- 170.163.130[.]162
- 173.209.69[.]2
- 174.6.141[.]85
- 178.238.233[.]29
- 184.148.89[.]74
- 189.253.90[.]151
- 203.45.203[.]83
- 206.255.103[.]64
- 212.72.150[.]186
- 213.219.135[.]87
PRELIMINARY MALWARE ANALYSIS
https://www.virustotal.com/gui/file/d1d127d60ca94a8a1779c9d978c4eadfdd5dbb3683a87f2bd1cbc963b09a9a36File name: java-exploit-from-173.246.105[.]15.jarhttps://www.virustotal.com/gui/file/18e332ef248116d5b72eef8be7aea9e2ea756ecf0e9dae0d294d2ffaf178ade7
File size: 19.8 KB ( 19,792 bytes )
File name: info.exehttps://www.virustotal.com/gui/file/883490ebce9703ab22525f4763327458cf045d9b68c50ba29c898e7b1d9b7883
File size: 355.3 KB ( 355,328 bytes )
File name: s86.exe
File size: 147.5 KB ( 147,456 bytes )
Click here to return to the main page.