2013-08-23 - G01PACK EXPLOIT KIT SENDS RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2013-08-23-g01pack-EK-traffic.pcap.zip 1.7 MB (1,710,284 bytes)
- 2013-08-23-g01pack-EK-malware.zip 245.1 kB (245,082 bytes)
NOTES:
Searching through the CLEAN MX realtime database, I found a compromised site named mpraid3[.]com. According to the whois on the domain name, noraud3[.]com was registered on 2013-08-21, only 2 days prior to this blog entry. It was registered through DomainContext, Inc. From what I can tell, this is a registrar based in Russia. The domain is hosted on 192.133.137[.]142, which is registered to Serverel[.]com, a hosting provider based in Sunnyvale, California.
When we visit that website in a vulnerable Windows host, it doesn't go to a website, but redirects to some malicious code that provides a blank page. Within a few seconds, the vulnerable Windows host is infected with "ransomware" that locks your computer with a fake notice as shown below...
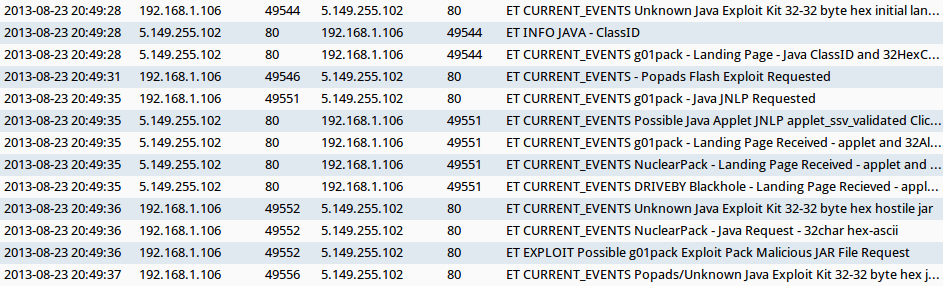
SNORT EVENTS
Using Security Onion to monitor a vulnerable Windows computer, the following events triggered in Sguil when typing mpraid3[.]com into a web browser:
- 20:49:28 - 192.168.1[.]106 port 49544 - 5.149.255[.]102 port 80 - ET CURRENT_EVENTS Unknown Java Exploit Kit 32-32 byte hex initial landing
- 20:49:28 - 5.149.255[.]102 port 80 - 192.168.1[.]106 port 49544 - ET INFO JAVA - ClassID
- 20:49:28 - 5.149.255[.]102 port 80 - 192.168.1[.]106 port 49544 - ET CURRENT_EVENTS g01pack - Landing Page - Java ClassID and 32HexChar.jar
- 20:49:31 - 192.168.1[.]106 port 49546 - 5.149.255[.]102 port 80 - ET CURRENT_EVENTS - Popads Flash Exploit Requested
- 20:49:35 - 192.168.1[.]106 port 49551 - 5.149.255[.]102 port 80 - ET CURRENT_EVENTS g01pack - Java JNLP Requested
- 20:49:35 - 5.149.255[.]102 port 80 - 192.168.1[.]106 port 49551 - ET CURRENT_EVENTS Possible Java Applet JNLP applet_ssv_validated Click To Run Bypass
- 20:49:35 - 5.149.255[.]102 port 80 - 192.168.1[.]106 port 49551 - ET CURRENT_EVENTS g01pack - Landing Page Received - applet and 32AlphaNum.jar
- 20:49:35 - 5.149.255[.]102 port 80 - 192.168.1[.]106 port 49551 - ET CURRENT_EVENTS NuclearPack - Landing Page Received - applet and 32HexChar.jar
- 20:49:35 - 5.149.255[.]102 port 80 - 192.168.1[.]106 port 49551 - ET CURRENT_EVENTS DRIVEBY Blackhole - Landing Page Recieved - applet and flowbit
- 20:49:36 - 192.168.1[.]106 port 49552 - 5.149.255[.]102 port 80 - ET CURRENT_EVENTS Unknown Java Exploit Kit 32-32 byte hex hostile jar
- 20:49:36 - 192.168.1[.]106 port 49552 - 5.149.255[.]102 port 80 - ET CURRENT_EVENTS NuclearPack - Java Request - 32char hex-ascii
- 20:49:36 - 192.168.1[.]106 port 49552 - 5.149.255[.]102 port 80 - ET EXPLOIT Possible g01pack Exploit Pack Malicious JAR File Request
- 20:49:37 - 192.168.1[.]106 port 49556 - 5.149.255[.]102 port 80 - ET CURRENT_EVENTS Popads/Unknown Java Exploit Kit 32-32 byte hex java payload request
INFECTION TRAFFIC
The first HTTP GET request was to mpraid3[.]com on 192.133.137[.]142, which returned a 302 with a redirect to the malware delivery domain at kucf.3wasnev[.]info on 5.149.255[.]102.
Here are all the actors involved in this traffic:
- 192.133.137[.]142 - mpraid3[.]com - a compromised or purposely malicious website that responds with a redirect to the malware delivery domain.
- 5.149.255[.]102 - kucf.3wasnev[.]info - the malware delivery domain the provides the java exploit and the initial malware
- 91.216.163[.]217 - ywgcecumyoquee[.]org - first callback domain, where the infected computer sends an HTTP POST
- 188.64.172[.]12 - rightclickcoast[.]info - second callback domain that sends the infected host more malicious files
Here's an overview of the infection traffic:
- 20:49:28 - 192.168.1[.]106 port 49543 - 192.133.137[.]142 port 80 - GET /
- 20:49:28 - 192.133.137[.]142 port 80 - 192.168.1[.]106 port 49543 - 302 Moved Temporarily
- 20:49:28 - 192.168.1[.]106 port 49544 - 5.149.255[.]102 port 80 - GET /?52c4cd7199af493d987fa2366f66c99b=r9&5eec33d94eb1695a176b0322ddf07048=mpraid3[.]com
- 20:49:28 - 5.149.255[.]102 port 80 - 192.168.1[.]106 port 49544 - 200 OK (text/html)
- 20:49:31 - 192.168.1[.]106 port 49546 - 5.149.255[.]102 port 80 - GET /6c2c7b0be76e03a583fc65dc488fdbff/c8d54b59e486a9fc421fcd4f70f5a36e.swf
- 20:49:31 - 5.149.255[.]102 port 80 - 192.168.1[.]106 port 49546 - 404 Not Found (text/html)
- 20:49:32 - 192.168.1[.]106 port 49550 - 5.149.255[.]102 port 80 - GET /favicon.ico
- 20:49:32 - 5.149.255[.]102 port 80 - 192.168.1[.]106 port 49550 - 404 Not Found (text/html)
- 20:49:35 - 192.168.1[.]106 port 49551 - 5.149.255[.]102 port 80 - GET /6c2c7b0be76e03a583fc65dc488fdbff/a73370ca160391ecf91ebf547b502d7a.jnlp
- 20:49:35 - 5.149.255[.]102 port 80 - 192.168.1[.]106 port 49551 - 200 OK
- 20:49:36 - 192.168.1[.]106 port 49552 - 5.149.255[.]102 port 80 - GET /6c2c7b0be76e03a583fc65dc488fdbff/5ce0ac3225e2cc25264b5f827f176f51.jar
- 20:49:36 - 5.149.255[.]102 port 80 - 192.168.1[.]106 port 49552 - 200 OK (application/x-java-archive)
- 20:49:36 - 192.168.1[.]106 port 49553 - 5.149.255[.]102 port 80 - GET /6c2c7b0be76e03a583fc65dc488fdbff/5ce0ac3225e2cc25264b5f827f176f51.jar
- 20:49:37 - 5.149.255[.]102 port 80 - 192.168.1[.]106 port 49553 - 200 OK (application/x-java-archive)
- 20:49:36 - 192.168.1[.]106 port 49554 - 5.149.255[.]102 port 80 - GET /6c2c7b0be76e03a583fc65dc488fdbff/5ce0ac3225e2cc25264b5f827f176f51.jar
- 20:49:37 - 5.149.255[.]102 port 80 - 192.168.1[.]106 port 49554 - 200 OK (application/x-java-archive)
- 20:49:37 - 192.168.1[.]106 port 49557 - 5.149.255[.]102 port 80 - GET /6c2c7b0be76e03a583fc65dc488fdbff/5ce0ac3225e2cc25264b5f827f176f51.jar
- 20:49:38 - 5.149.255[.]102 port 80 - 192.168.1[.]106 port 49557 - 200 OK (application/x-java-archive)
- 20:49:37 - 192.168.1[.]106 port 49556 - 5.149.255[.]102 port 80 - GET /6c2c7b0be76e03a583fc65dc488fdbff/0
- 20:49:38 - 5.149.255[.]102 port 80 - 192.168.1[.]106 port 49556 - 200 OK (text/html)
- 20:49:38 - 192.168.1[.]106 port 49558 - 5.149.255[.]102 port 80 - GET /6c2c7b0be76e03a583fc65dc488fdbff/0
- 20:49:39 - 5.149.255[.]102 port 80 - 192.168.1[.]106 port 49558 - 200 OK (text/html)
- 20:49:38 - 192.168.1[.]106 port 49559 - 5.149.255[.]102 port 80 - GET /6c2c7b0be76e03a583fc65dc488fdbff/1
- 20:49:38 - 5.149.255[.]102 port 80 - 192.168.1[.]106 port 49559 - 404 Not Found (text/html)
- 20:49:39 - 192.168.1[.]106 port 49562 - 5.149.255[.]102 port 80 - GET /6c2c7b0be76e03a583fc65dc488fdbff/1
- 20:49:39 - 5.149.255[.]102 port 80 - 192.168.1[.]106 port 49562 - 404 Not Found (text/html)
- 20:49:39 - 192.168.1[.]106 port 49560 - 5.149.255[.]102 port 80 - GET /6c2c7b0be76e03a583fc65dc488fdbff/2
- 20:49:39 - 5.149.255[.]102 port 80 - 192.168.1[.]106 port 49560 - 404 Not Found (text/html)
- 20:49:40 - 192.168.1[.]106 port 49564 - 5.149.255[.]102 port 80 - GET /6c2c7b0be76e03a583fc65dc488fdbff/2
- 20:49:40 - 5.149.255[.]102 port 80 - 192.168.1[.]106 port 49564 - 404 Not Found (text/html)
- 20:49:39 - 192.168.1[.]106 port 49561 - 5.149.255[.]102 port 80 - GET /6c2c7b0be76e03a583fc65dc488fdbff/3
- 20:49:39 - 5.149.255[.]102 port 80 - 192.168.1[.]106 port 49561 - 404 Not Found (text/html)
- 20:49:40 - 192.168.1[.]106 port 49565 - 5.149.255[.]102 port 80 - GET /6c2c7b0be76e03a583fc65dc488fdbff/3
- 20:49:40 - 5.149.255[.]102 port 80 - 192.168.1[.]106 port 49565 - 404 Not Found (text/html)
- 20:49:39 - 192.168.1[.]106 port 49563 - 5.149.255[.]102 port 80 - GET /6c2c7b0be76e03a583fc65dc488fdbff/4
- 20:49:40 - 5.149.255[.]102 port 80 - 192.168.1[.]106 port 49563 - 200 OK (text/html)
- 20:49:40 - 192.168.1[.]106 port 49566 - 5.149.255[.]102 port 80 - GET /6c2c7b0be76e03a583fc65dc488fdbff/4
- 20:49:42 - 5.149.255[.]102 port 80 - 192.168.1[.]106 port 49566 - 200 OK (text/html)
- 20:49:56 - 192.168.1[.]106 port 49568 - 91.216.163[.]217 port 80 - POST /
- 20:49:56 - 91.216.163[.]217 port 80 - 192.168.1[.]106 port 49568 - 200 OK (text/html)
- 20:52:43 - 192.168.1[.]106 port 49569 - 188.64.172[.]12 port 80 - GET /contact/jutfofnoygfquobinmnsdk-qcuquxwpjkmsjz_osdhqruunbrkqtmvqksiitksdirkjz-rkfczhxlcavrzvhelx-.html
- 20:52:46 - 188.64.172[.]12 port 80 - 192.168.1[.]106 port 49569 - 200 OK (application/octet-stream)
- 20:52:50 - 192.168.1[.]106 port 49569 - 188.64.172[.]12 port 80 - PUT /forum/crkgoxpydrrc_zrxq_judn_ezvldkwfjtpr_pawbbc-tyvk-clpb-igybddcqldtmvykq-ksygplsyfmfanh_itty_vkrc.php
- 20:52:50 - 188.64.172[.]12 port 80 - 192.168.1[.]106 port 49569 - 200 OK
- 20:52:44 - 192.168.1[.]106 port 49570 - 188.64.172[.]12 port 80 - GET /forum/dknqzajpfcgtdh-xspf-qpnorggdiqduosnsxo_bhrksh-juvr-jxix-xjru-nnqu-eyjkgtdump_eane-vqqr-tuofli-ks.php
- 20:52:45 - 188.64.172[.]12 port 80 - 192.168.1[.]106 port 49570 - 200 OK (application/octet-stream)
- 20:52:52 - 192.168.1[.]106 port 49570 - 188.64.172[.]12 port 80 - PUT /contact/oeex-jlbwip-nadwwiprroyn-nbfq-kkvn-kssixxdhnqquphvayt-crejzoyvixoxrt-nnoy-fmoprzjvpifzxjlxsu.html
- 20:52:52 - 188.64.172[.]12 port 80 - 192.168.1[.]106 port 49570 - 200 OK
INFECTION TRAFFIC DETAILS
GET /
IP address: 192.133.137[.]142
domain name: mpraid3[.]com
Sguil events: None
Screenshot of the traffic:
GET /?52c4cd7199af493d987fa2366f66c99b=r9&5eec33d94eb1695a176b0322ddf07048=mpraid3[.]com
IP address: 5.149.255[.]102
domain name: kucf.3wasnev[.]info
Sguil events:
- ET CURRENT_EVENTS Unknown Java Exploit Kit 32-32 byte hex initial landing
- ET INFO JAVA - ClassID
- ET CURRENT_EVENTS g01pack - Landing Page - Java ClassID and 32HexChar.jar
Screenshot of traffic:
GET /6c2c7b0be76e03a583fc65dc488fdbff/c8d54b59e486a9fc421fcd4f70f5a36e.swf
IP address: 5.149.255[.]102
domain name: kucf.3wasnev[.]info
Sguil event:
- ET CURRENT_EVENTS - Popads Flash Exploit Requested
Screenshot of traffic:
GET /6c2c7b0be76e03a583fc65dc488fdbff/a73370ca160391ecf91ebf547b502d7a.jnlp
IP address: 5.149.255[.]102
domain name: kucf.3wasnev[.]info
Sguil events:
- ET CURRENT_EVENTS g01pack - Java JNLP Requested
- ET CURRENT_EVENTS Possible Java Applet JNLP applet_ssv_validated Click To Run Bypass
- ET CURRENT_EVENTS g01pack - Landing Page Received - applet and 32AlphaNum.jar
- ET CURRENT_EVENTS NuclearPack - Landing Page Received - applet and 32HexChar.jar
- ET CURRENT_EVENTS DRIVEBY Blackhole - Landing Page Recieved - applet and flowbit
Screenshot of traffic:
GET /6c2c7b0be76e03a583fc65dc488fdbff/5ce0ac3225e2cc25264b5f827f176f51.jar
IP address: 5.149.255[.]102
domain name: kucf.3wasnev[.]info
Sguil events:
- ET CURRENT_EVENTS Unknown Java Exploit Kit 32-32 byte hex hostile jar
- ET CURRENT_EVENTS NuclearPack - Java Request - 32char hex-ascii
- ET EXPLOIT Possible g01pack Exploit Pack Malicious JAR File Request
Screenshot of traffic:
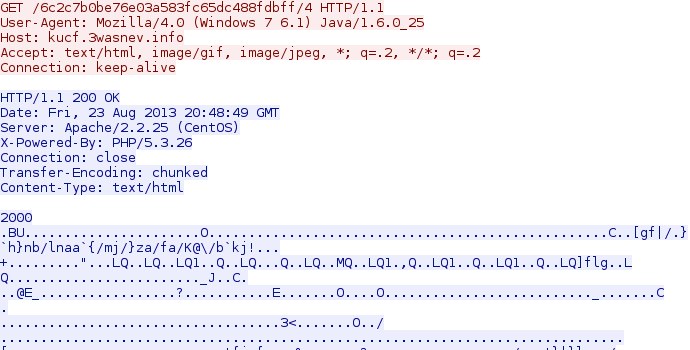
GET /6c2c7b0be76e03a583fc65dc488fdbff/0
IP address: 5.149.255[.]102
domain name: kucf.3wasnev[.]info
Sguil event:
- ET CURRENT_EVENTS Popads/Unknown Java Exploit Kit 32-32 byte hex java payload request
Screenshot of traffic:
This is an executable that's been XOR-ed with 2A (hexadecimal for the asterisk symbol "*") on each byte. Here's what the beginning of the file looks like in a hex editor before it's decoded:There are a few different ways to convert the file. For example, the following Python script should do the trick, assuming the file you extract from Wireshark is named extracted-file.bin:Here's what it looks like after every byte is XOR-ed with 0x2A:b = bytearray(open('extracted-file.bin', 'rb').read()) for i in range(len(b)): b[i] ^= 0x2A open('output-binary.exe', 'wb').write(b)
GET /6c2c7b0be76e03a583fc65dc488fdbff/4
IP address: 5.149.255[.]102
domain name: kucf.3wasnev[.]info
Screenshot of traffic:
This was the second executable. In this case, each byte is XOR-ed with 0x0f. If you review the PCAP, you'll see each malicious executable was sent twice, with a different character used to XOR each binary.
The following callback traffic occurred, and some more malicious files were returned. Review the PCAP for further information on this additional traffic.
- 91.216.163[.]217 - ywgcecumyoquee[.]org - POST /
- 188.64.172[.]12 - rightclickcoast[.]info - GET /contact/jutfofnoygfquobinmnsdk-qcuquxwpjkmsjz_osdhqruunbrkqtmvqksiitksdirkjz-rkfczhxlcavrzvhelx-.html
- 188.64.172[.]12 - rightclickcoast[.]info - PUT /forum/crkgoxpydrrc_zrxq_judn_ezvldkwfjtpr_pawbbc-tyvk-clpb-igybddcqldtmvykq-ksygplsyfmfanh_itty_vkrc.php
- 188.64.172[.]12 - rightclickcoast[.]info - GET /forum/dknqzajpfcgtdh-xspf-qpnorggdiqduosnsxo_bhrksh-juvr-jxix-xjru-nnqu-eyjkgtdump_eane-vqqr-tuofli-ks.php
- 188.64.172[.]12 - rightclickcoast[.]info - PUT /contact/oeex-jlbwip-nadwwiprroyn-nbfq-kkvn-kssixxdhnqquphvayt-crejzoyvixoxrt-nnoy-fmoprzjvpifzxjlxsu.html
PRELIMINARY MALWARE ANALYSIS
Java exploit from 5.149.255[.]102 (kucf.3wasnev[.]info):
https://www.virustotal.com/gui/file/8c95ee3c4ba389dab0dd1d54fef00728a9bac3344df04bbf46994829478479d6
File name: java-exploit-from-kucf.3wasnev[.]info.jar
File size: 15.9 KB ( 15,900 bytes )
First malicious executable from 5.149.255[.]102 (kucf.3wasnev[.]info):
https://www.virustotal.com/gui/file/fc01b4102926c8975de5831b470d3e2ab2b5f105a0143e33397d89d0f35060f5
File name: first-malicious-executable-from-kucf.3wasnev[.]info.exe
File size: 186.4 KB ( 186,369 bytes )
Second malicious executable from 5.149.255[.]102 (kucf.3wasnev[.]info):
https://www.virustotal.com/gui/file/bfae1b2a7cd32bc4cc58d9779baefc5f1e3b9f6f1eca34061a53c1360025ef4f
File name: second-malicious-executable-from-kucf.3wasnev[.]info.exe
File size: 282.6 KB ( 282,625 bytes )
Click here to return to the main page.