2013-10-13 - BEWARE OF ALTERNATIVES TO GOOGLE PLAY
By default, recent versions of Android OS prevent installing apps that are not from the Play Store (the official Android market at play.google.com). Why? Because the apps in these unofficial app markets are not vetted by Google (who develops the Android OS).
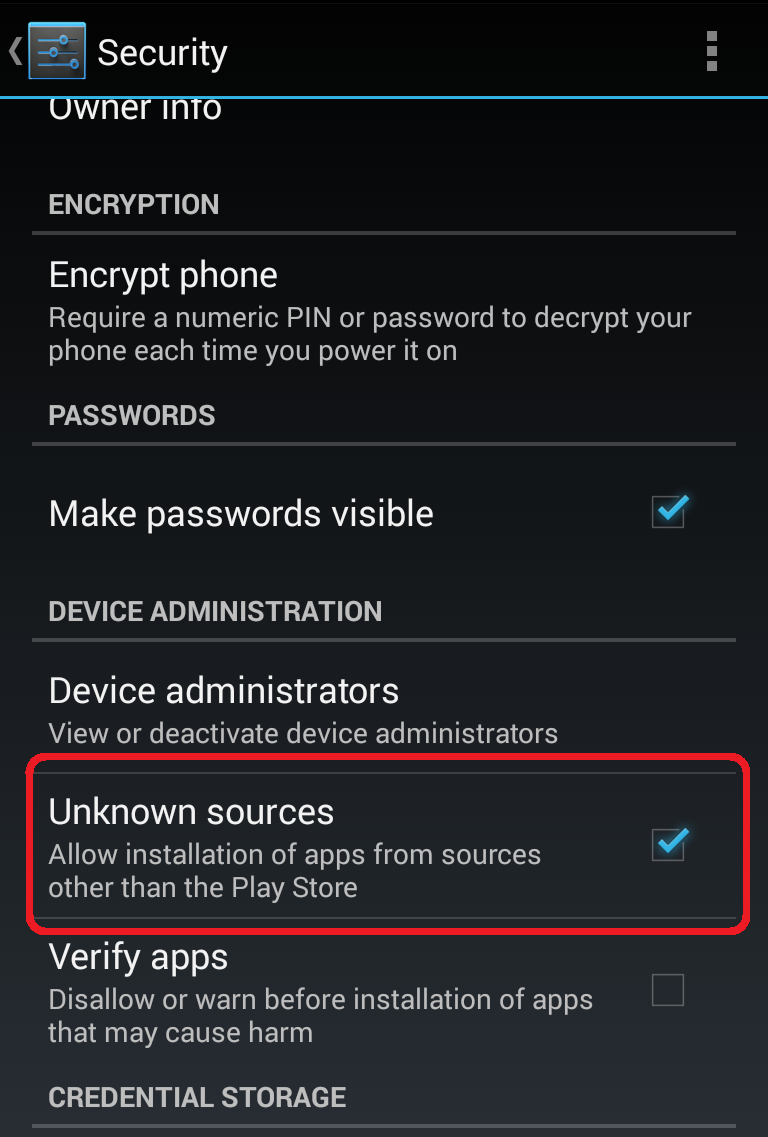
You can change this on your Android phone or tablet by updating the following security setting:
Settings --> Security --> Unknown sources --> Allow installation of apps from sources other than the Play Store
NOTE: For the purpose of this blog entry, I un-checked the
Verify Apps section, which you should leave on by default.
Let's see what happens when we install an app from one of these unofficial Android app markets...
The website www.1mobile.com is one of the many alternatives to the Play Shore. 1mobile.com has a client that handles your app downloads, or you can directly download the APK files using a web browser. The 1mobile Market boasts a list of more than 60,000 apps that includes "almost any app to any mobile that either has regular market restrictions or has been previously removed from the default android market" (source).
A popular game right now is Candy Crush, which is published by King[.]com according to Wikipedia. The entry for the official Android app on Google's Play Store confirms this.
What does 1Mobile have on Candy Crush? A search on the site shows three choices for this game.
Of the three choices, one is the official version from King[.]com, which is a 42.2 MB file. The other two choices appear to be from generically-named game developers. The file sizes are much smaller than the official King[.]com version.
- Publisher: King[.]com - Size 42.2 MB - hxxp[:]//www.1mobile[.]com/candy-crush-saga-651798.html
- Publisher: GAMES - Size: 1.13 MB - hxxp[:]//www.1mobile[.]com/candy-crush-saga-free-773366.html
- Publisher: TOP FREE GAMES - Size: 1.12 MB - hxxp[:]//www.1mobile[.]com/candy-crush-saga-free-769750.html
Let's install one of these other apps on a Nexus 4 running Android version 4.3. The Nexus 4 is using WiFi, and the traffic is being monitored by Security Onion.
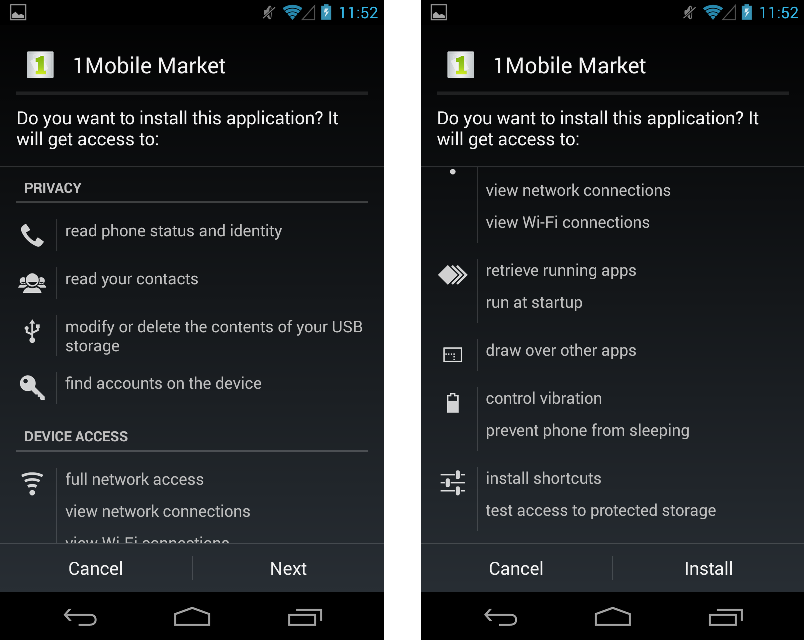
Even though the security settings allow us to download an app from someplace other than the Play Store, we still get a warning, as seen below:
When you install that app, which is named candy.crush.saga.free_quickdownload_201.apk, it's not Candy Crush, but the 1Mobile Market app.
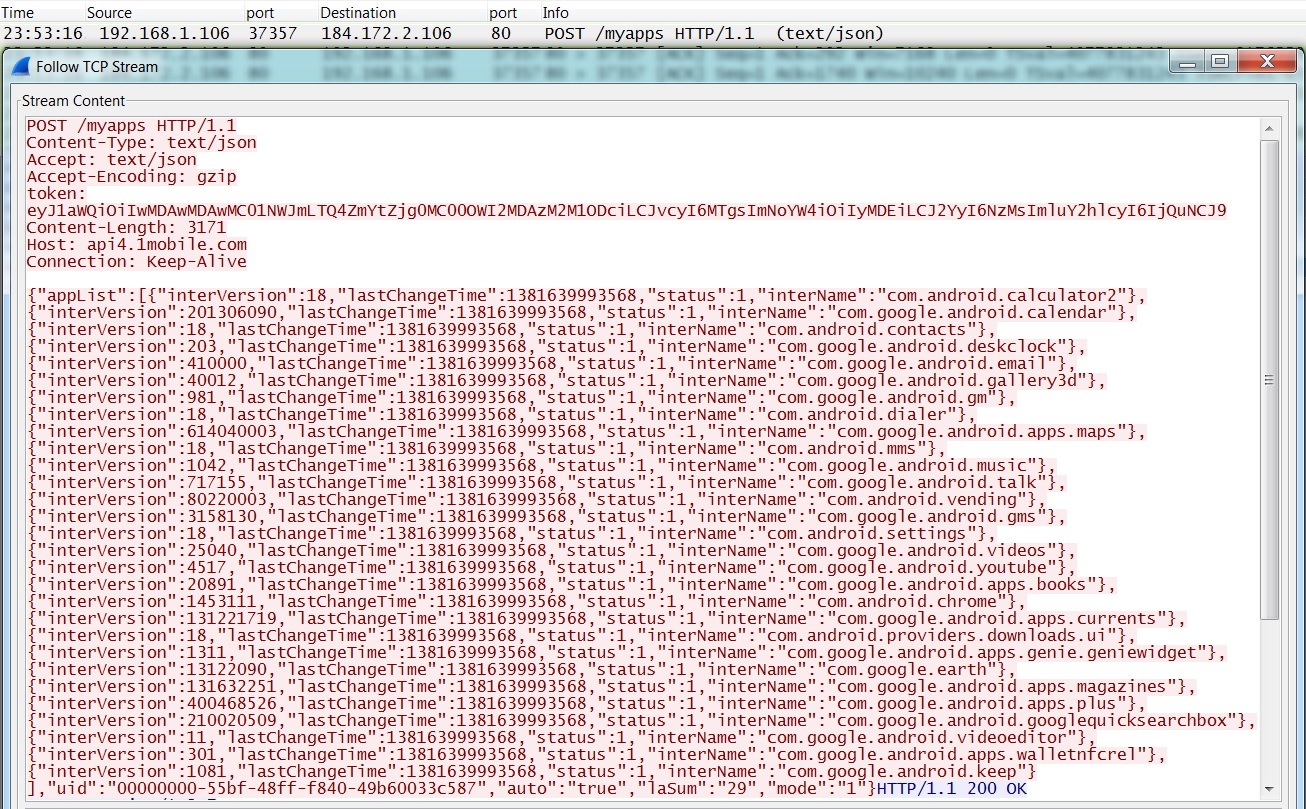
From this point we see adware-type traffic from the 1Mobile Market app. For example, the app sent a list of installed apps on the Nexus 4 to api4.1mobile[.]com:
We also see plenty of traffic to 1mobile and other related domains:
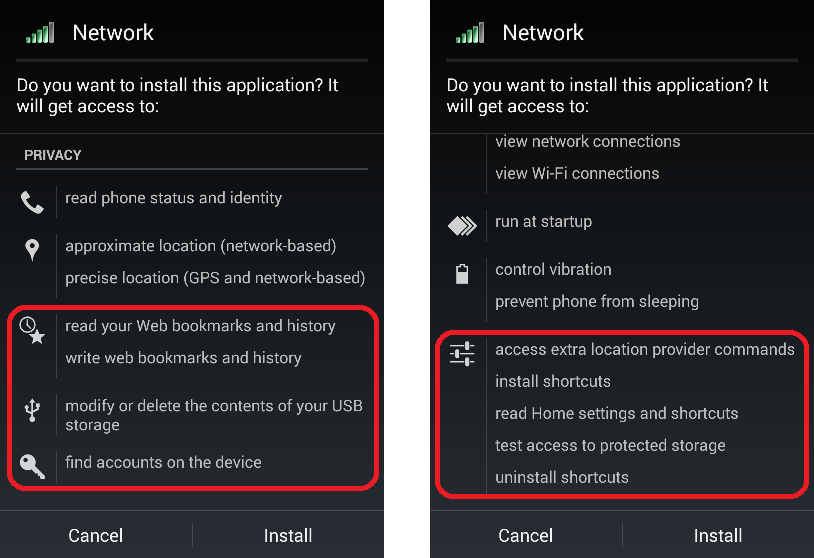
After the 1Mobile Market app was installed, visiting the same web page to download Candy Crush returned a different file named candy.crush.saga.free_384.apk.
This new app isn't Candy Crush, but something called "Network." When installed, the app asks for even more permissions than the 1Mobile Market app. I've highlighted some of the more worrisome permissions below:
Once this app was installed, Security Onion system generated two Snort events...
SNORT EVENTS
Here are the Snort events:
- 05:06:50 GMT - 192.168.1[.]106 port 35789 - 217.65.34[.]4 port 80 - ET MOBILE_MALWARE Android/Plankton.P Commands Request to CnC Server
- 05:06:50 GMT - 192.168.1[.]106 port 35789 - 217.65.34[.]4 port 80 - ET POLICY Android.Plankton/Tonclank Successful Installation Device Information POST
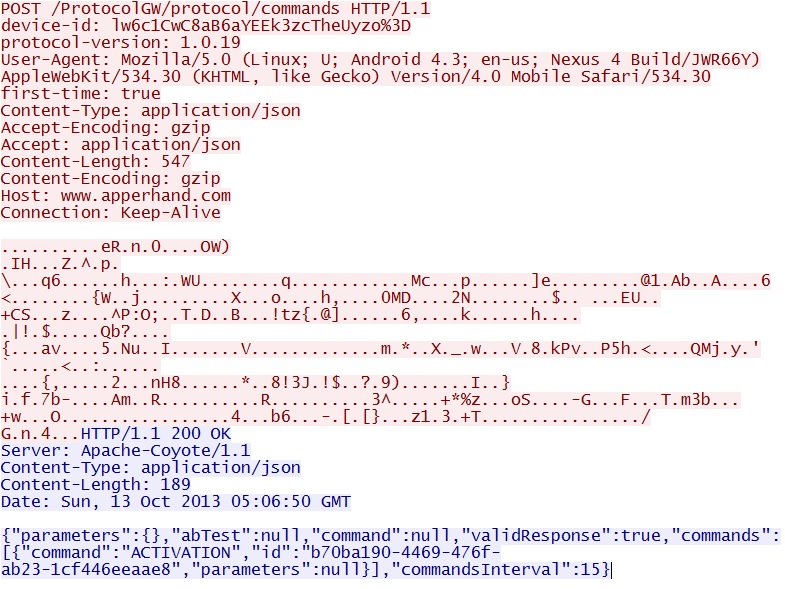
Here is the traffic that generated them:
POST /ProtocolGW/protocol/commands
IP address: 217.65.36[.]4 port 80
domain name: www.apperhand[.]com
Snort events:
- ET MOBILE_MALWARE Android/Plankton.P Commands Request to CnC Server
- ET POLICY Android.Plankton/Tonclank Successful Installation Device Information POST"; flow:established,to_server; content:"POST"
Screenshot of traffic:
FINAL NOTES
candy.crush.saga.free_384.apk is adware related to the Apperhand Software Development Kit (SDK). The Sourcefire team that created these Snort rules wrote a blog post about the Apperhand SDK here. To make a long story short, these types of apps fall into a gray area of crappy adware more than outright malware.
Even though it falls under adware, most people wouldn't actually want this stuff on their phone or tablet. If you see these Snort alerts on your network, find the user and let them know about it. To ensure you get rid of this adware, try a factory data reset on the phone. The reset will erase all of your stored data, but it will definitely get rid of the adware.
If you have any comments on this blog entry, send an email to admin@malware-traffic-analysis.net.
Click here to return to the main page.