2014-01-08 - NEUTRINO EK
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
A quick post on traffic for another VM infected through Neturino EK...
INFECTION CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 67.227.151[.]164 - help.lockergnome[.]com - infected website
- 46.20.227[.]195 - shiningstarscleaningservice[.]com - redirect domain
- 212.83.188[.]39 - quohyiin.dikarlos[.]com - Neutrino EK domain
INFECTION CHAIN:
- 00:36:04 UTC - 67.227.151[.]164 - help.lockergnome[.]com - GET /office/Highlight-part-picture-Word--ftopict688815.html
- 00:36:05 UTC - 46.20.227[.]195 - hsiammyy7hdin7jqu6hfnjt.shiningstarscleaningservice[.]com - GET /index.php?v=emdsenpxPXNvaiZ0aW1lPTE0MDEwNzIzMjMtNzM3MzE0NjMzJnNy
Yz0zMzYmc3VybD1oZWxwLmxvY2tlcmdub21lLmNvbSZzcG9ydD04MCZrZXk9NERGQkI5QzUmc3VyaT0vb2ZmaWNlL0hpZ2hsaWdodC1wYXJ0LXBpY3R1cmUtV29yZC0tZnR
vcGljdDY4ODgxNS5odG1s - 00:36:06 UTC - 46.20.227[.]195 - hsiammyy7hdin7jqu6hfnjt53365382c8e420ee542452677cded84d6.shiningstarscleaningservice[.]com - GET /index2.php
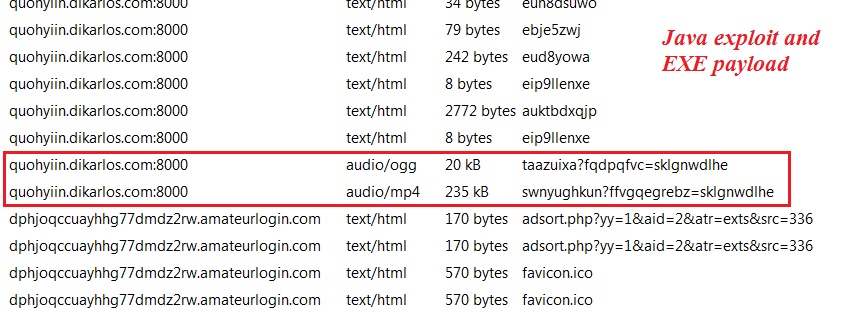
- 00:36:07 UTC - 212.83.188[.]39 - quohyiin.dikarlos[.]com:8000 - GET /ndffrps?klqcxbsn=3410575
- 00:36:08 UTC - 212.83.188[.]39 - quohyiin.dikarlos[.]com:8000 - GET /zgaqwbhsxee
- 00:36:09 UTC - 212.83.188[.]39 - quohyiin.dikarlos[.]com:8000 - GET /eofsrr3capt52?ff898ia802=2rucy4b&qwa9um3od6=eirykdac9&vrme4kcw0d=m19lb7gc&xr8u4=eoj
- 00:36:09 UTC - 212.83.188[.]39 - quohyiin.dikarlos[.]com:8000 - POST /ewk2n8g8e
- 00:36:09 UTC - 212.83.188[.]39 - quohyiin.dikarlos[.]com:8000 - POST /ea9ssaa
- 00:36:09 UTC - 212.83.188[.]39 - quohyiin.dikarlos[.]com:8000 - POST /e7xwm5qzry
- 00:36:09 UTC - 212.83.188[.]39 - quohyiin.dikarlos[.]com:8000 - POST /etsvgkdg
- 00:36:09 UTC - 212.83.188[.]39 - quohyiin.dikarlos[.]com:8000 - POST /etys8e5z939x
- 00:36:13 UTC - 212.83.188[.]39 - quohyiin.dikarlos[.]com:8000 - POST /auktbdxqjp
- 00:36:13 UTC - 212.83.188[.]39 - quohyiin.dikarlos[.]com:8000 - POST /eip9llenxe
- 00:36:13 UTC - 212.83.188[.]39 - quohyiin.dikarlos[.]com:8000 - POST /euh8dsuwo
- 00:36:13 UTC - 212.83.188[.]39 - quohyiin.dikarlos[.]com:8000 - POST /ebje5zwj
- 00:36:13 UTC - 212.83.188[.]39 - quohyiin.dikarlos[.]com:8000 - POST /eud8yowa
- 00:36:22 UTC - 212.83.188[.]39 - quohyiin.dikarlos[.]com:8000 - GET /taazuixa?fqdpqfvc=sklgnwdlhe
- 00:36:22 UTC - 212.83.188[.]39 - quohyiin.dikarlos[.]com:8000 - GET /META-INF/services/javax.xml.datatype.DatatypeFactory
- 00:36:23 UTC - 212.83.188[.]39 - quohyiin.dikarlos[.]com:8000 - GET /swnyughkun?ffvgqegrebz=sklgnwdlhe
PRELIMINARY MALWARE ANALYSIS
Java exploit from 212.83.188[.]39 port 8000 (quohyiin.dikarlos[.]com):
SHA256 hash: f3ccab0af7589ff0018eeb6b7d8d14f84ee8561ae148dc90e4cbf34d95eb53a3
File name: 2014-01-08-java-exploit-from-neutrino-domain.jar File size: 20,008 bytes
Detection ratio: 7 / 47
First submitted: 2014-01-04 23:05:25 UTC
EXE payload from 212.83.188[.]39 port 8000 (quohyiin.dikarlos[.]com):
SHA256 hash: 7630bc8964eb3dfe40f9402823f319eba57b4c8f29da1a30614aebe0dc399141/a>
File name: 2014-01-08-EXE-payload-from-neutrino-domain.exe File size: 235,820 bytes
Detection ratio: 11 / 47
First submitted: 2014-01-08 15:09:49 UTC
Click here to return to the main page.
