2014-01-10 - DOTKACHEF EXPLOIT KIT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
The DotkaChef exploit kit was discovered sometime in the first half of 2013, and EmergingThreats started releasing signatures on this EK as early as 2013-06-29.
In recent weeks, this exploit kit appears to have gained a little more prominence, because a few blog posts and articles have appeared last month (December 2013). The two below are a good example of what I've seen:
- https://web.archive.org/web/20140221101248/http://www.kahusecurity.com/2013/analyzing-dotkachef-exploit-pack/
- https://web.archive.org/web/20131211044648/http://www.malekal.com/2013/12/04/malvertising-at-aduserver-com-lead-to-dotkachef-ek/
Today, I happened across two compromised web sites that generated traffic to a DotkaChef EK domain. Let's take a closer look at these infections.
ALERTS
I used Security Onion to monitor a vulnerable VM running a 32-bit version of Windows 7 with Java 6 update 25. The infection traffic generated the following events in Sguil:
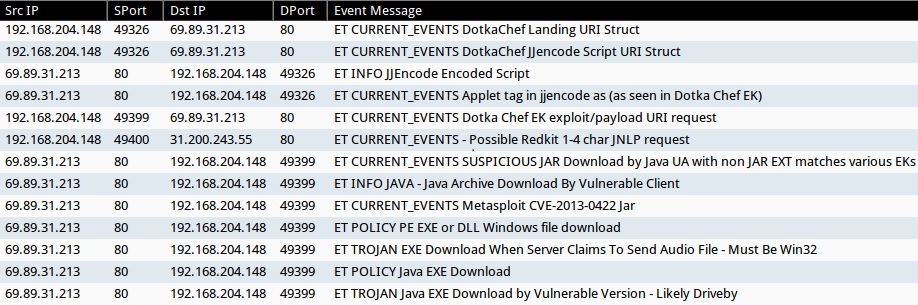
Screen shot of Sguil events for this infection.
- ET CURRENT_EVENTS DotkaChef Landing URI Struct
- ET CURRENT_EVENTS DotkaChef JJencode Script URI Struct
- ET INFO JJEncode Encoded Script
- ET CURRENT_EVENTS Applet tag in jjencode as (as seen in Dotka Chef EK)
- ET CURRENT_EVENTS DotkaChef exploit/payload URI request
- ET CURRENT_EVENTS - Possible Redkit 1-4 char JNLP request
- ET CURRENT_EVENTS SUSPICIOUS JAR Download by Java UA with non JAR EXT matches various EKs
- ET INFO JAVA - Java Archive Download By Vulnerable Client
- ET CURRENT_EVENTS Metasploit CVE-2013-0422 Jar
- ET POLICY PE EXE or DLL Windows file download
- ET TROJAN EXE Download When Server Claims To Send Audio File - Must Be Win32
- ET POLICY Java EXE Download
- ET TROJAN Java EXE Download by Vulnerable Version - Likely Driveby
INFECTION CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 31.200.243[.]55 - www.psicologia-online[.]com - compromised website - generates traffic to a redirect domain
- 103.31.186[.]40 - seris[.]biz - redirect domain - redirects traffic from the compromised website to the exploit domain
- 69.89.31[.]213 - kanon-finale[.]com - Domain hosting the DotkaChef EK - delivers the java exploit and EXE payload
INITIAL INFECTION CHAIN:
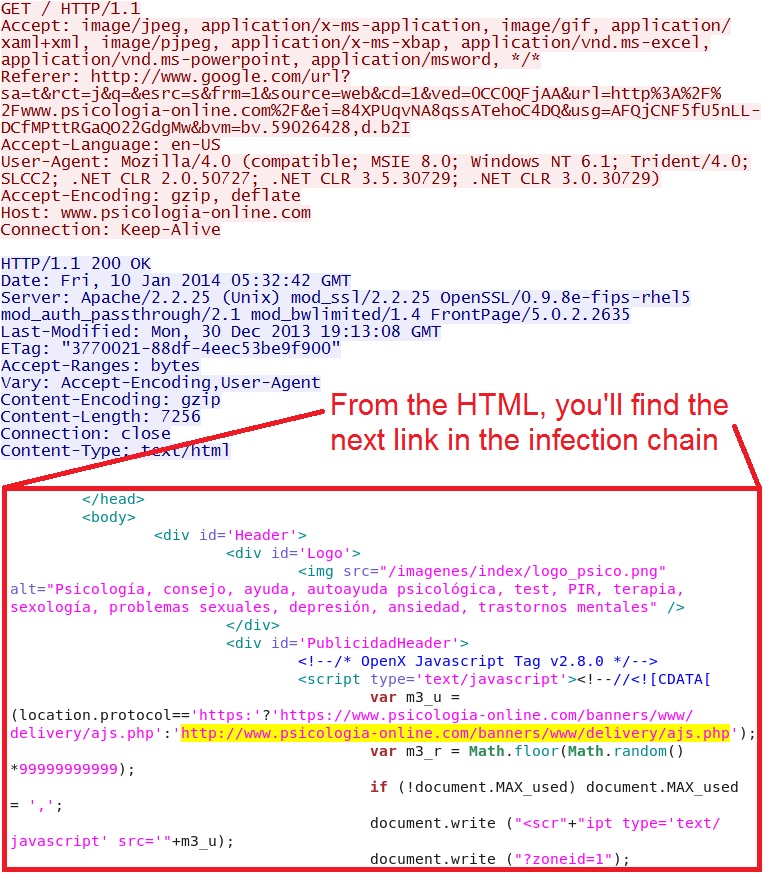
- 05:32:45 UTC - 31.200.243[.]55 port 80 - www.psicologia-online[.]com - GET /
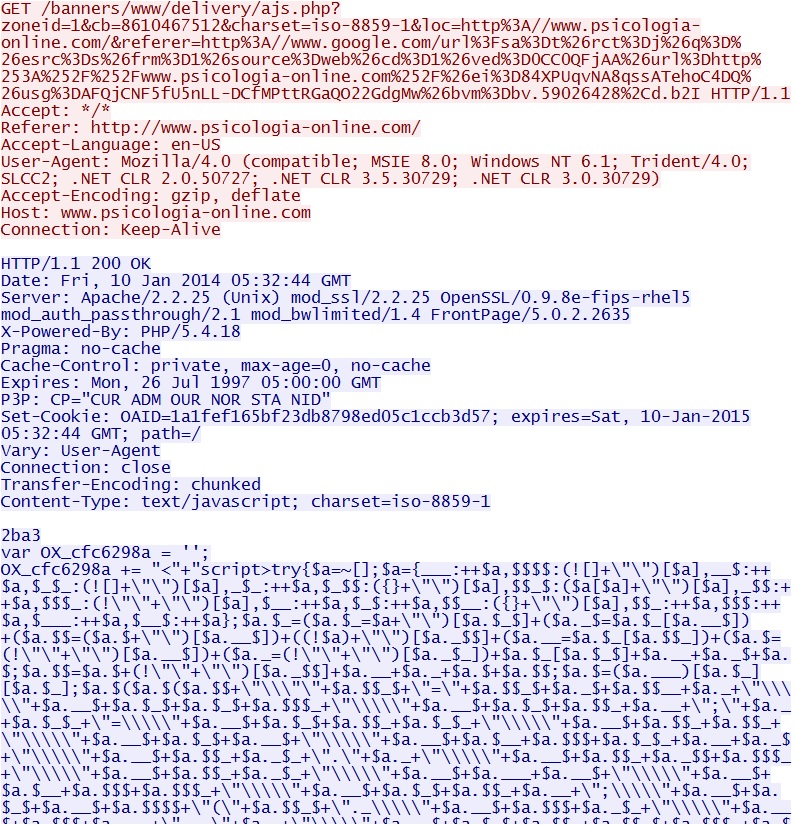
- 05:32:47 UTC - 31.200.243[.]55 port 80 - www.psicologia-online[.]com - GET /banners/www/delivery/ajs.php?zoneid=1&cb=8610467512
&charset=iso-8859-1&loc=http%3A//www.psicologia-online[.]com/&referer=http%3A//www.google.com/url%3Fsa%3Dt%26rct%3Dj%26q%3D%26esrc%3Ds%26frm
%3D1%26source%3Dweb%26cd%3D1%26ved%3D0CC0QFjAA%26url%3Dhxxp%253A%252F%252Fwww.psicologia-online[.]com%252F%26ei%3D84XPUiqvNA8q
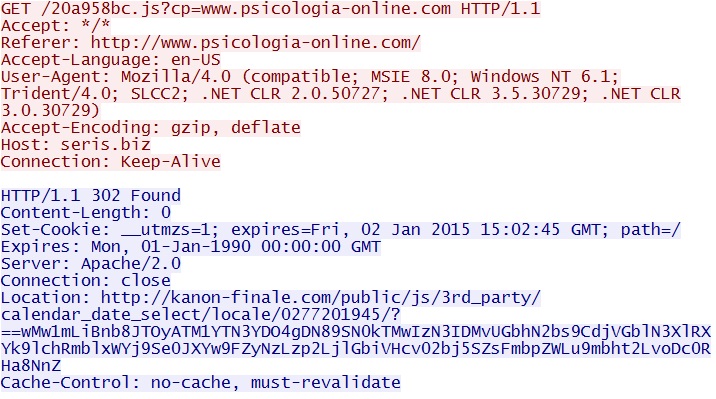
ssATehoC4DQ%26usg%3DAFQjCNF5fU5nLL-DCfMPttRGaQO22GdgMw%26bvm%3Dbv.59026428%2Cd.b2I - 05:32:47 UTC - 103.31.186[.]40 port 80 - seris[.]biz - GET /20a958bc.js?cp=www.psicologia-online[.]com
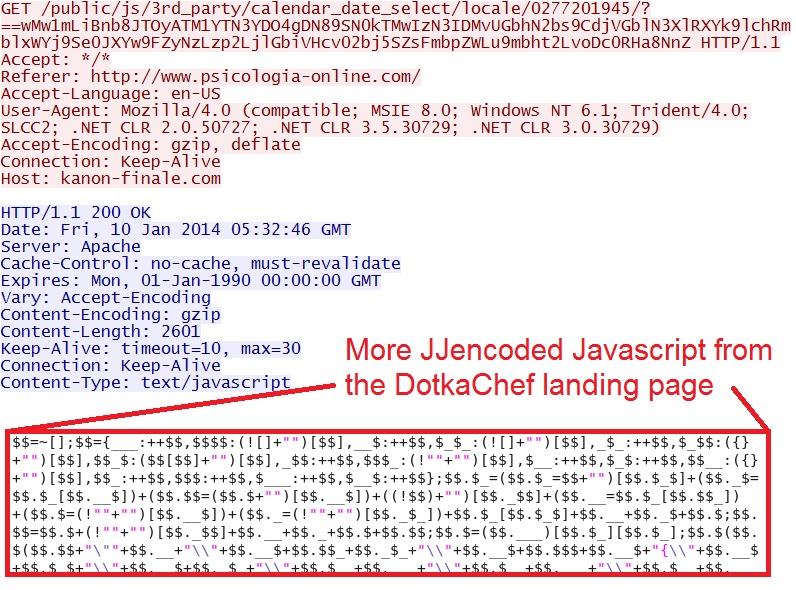
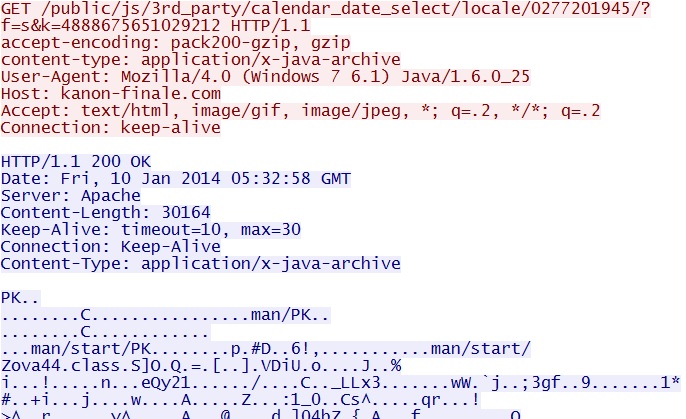
- 05:32:48 UTC - 69.89.31[.]213 port 80 - kanon-finale[.]com - GET /public/js/3rd_party/calendar_date_select/locale/0277201945/[base64 encoded string, reversed]
- 05:33:00 UTC - 69.89.31[.]213 port 80 - kanon-finale[.]com - GET /public/js/3rd_party/calendar_date_select/locale/0277201945/?f=s&k=4888675651029212
- 05:33:00 UTC - 69.89.31[.]213 port 80 - kanon-finale[.]com - GET /public/js/3rd_party/calendar_date_select/locale/0277201945/?f=s&k=4888675651029212
- 05:33:01 UTC - 69.89.31[.]213 port 80 - kanon-finale[.]com - GET /public/js/3rd_party/calendar_date_select/locale/0277201945/?f=s&k=4888675651029212
- 05:33:01 UTC - 69.89.31[.]213 port 80 - kanon-finale[.]com - GET /public/js/3rd_party/calendar_date_select/locale/0277201945/?f=s&k=4888675651029212
- 05:33:01 UTC - 69.89.31[.]213 port 80 - kanon-finale[.]com - GET /public/js/3rd_party/calendar_date_select/locale/0277201945/?f=s&k=4888675651029212
- 05:33:01 UTC - 69.89.31[.]213 port 80 - kanon-finale[.]com - GET /public/js/3rd_party/calendar_date_select/locale/0277201945/?f=npb.mp3&k=4888675651029223
INFECTION TRAFFIC DETAILS
IP address: 31.200.243[.]55 port 80
domain name:
HTTP request: GET /
Screenshot of traffic:
IP address: 31.200.243[.]55 port 80
domain name:
HTTP request: GET /banners/www/delivery/ajs.php?zoneid=1&cb=8610467512&charset=iso-8859-1&loc=http%3A//www.psicologia-online[.]com/&
referer=hxxp%3A//www.google[.]com/url%3Fsa%3Dti%26rct%3Dj%26q%3D%26esrc%3Ds%26frm%3D1%26source%3Dweb%26cd%3D1%26ved%3D
0CC0QFjAA%26url%3Dhxxp%253A%252F%252Fwww.psicologia-online[.]com%252F%26ei%3D84XPUqvNA8qssATehoC4DQ%26usg%3DAFQjCNF
5fU5nLL-DCfMPttRGaQO22GdgMw%26bvm%3Dbv.59026428%2Cd.b2I
Screenshot of traffic:
The script that's returned is JJencoded. Kahu Security has a well-written article describing this obfuscation technique (see https://web.archive.org/web/20140927041742/http://www.kahusecurity.com/2013/jjencode-script-leads-to-drive-by/ for details). In this case, the JJencoded global variable name is $a, but there's other obfuscation here that I haven't been able to figure out.
IP address: 103.31.186[.]40 port 80
domain name: seris[.]biz
HTTP request: GET /20a958bc.js?cp=www.psicologia-online[.]com
Screenshot of traffic:
This is the redirect that generates a 302 Found to the DotkaChef exploit domain.
IP address: 69.89.31[.]213 port 80
domain name: kanon-finale[.]com
HTTP request: GET /public/js/3rd_party/calendar_date_select/locale/0277201945/[base64 encoded string, reversed]
Screenshot of traffic:
This landing page has more JJencoded Javascript. The global variable is $$ but once again, there's some additional obfuscation
that prevents me from decoding this.
IP address: 69.89.31[.]213 port 80
domain name: kanon-finale[.]com
HTTP request: GET /public/js/3rd_party/calendar_date_select/locale/0277201945/?f=s&k=4888675651029212
Screenshot of traffic:
This is the Java exploit.
IP address: 69.89.31[.]213 port 80
domain name: kanon-finale[.]com
HTTP request: GET /public/js/3rd_party/calendar_date_select/locale/0277201945/?f=npb.mp3&k=4888675651029223
Screenshot of traffic:
This is the EXE payload.
ANOTHER INFECTION
For comparison, here's another VM infection from another site:
ASSOICATED DOMAINS:
- www.divernet[.]com - compromised website
- seris[.]biz - redirect domain
- 8www.grad[.]ru - DotkaChef EK domain
CHAIN OF EVENTS:
- 18:53:04 UTC - 93.174.137[.]139 - www.divernet[.]com - GET /
- 18:53:05 UTC - 93.174.147[.]139 - openx.divernet.com - GET /www/delivery/spcjs.php?id=1
- 18:53:10 UTC - 93.174.147[.]139 - openx.divernet.com - GET /www/delivery/spc.php?zones=1%7C2%7C3%7C4%7C5%7C6%7C57%7C9%7C10%7C11%7C12%7C13%7C14
%7C15%7C16%7C23%7C18%7C19%7C20%7C21%7C22%7C24%7C25%7C26%7C27%7C28%7C29%7C30%7C31%7C32%7C33%7C34%7C35%7C36%7C37%7C38%7C39
%7C40%7C41%7C42%7C43%7C44%7C45%7C46%7C47%7C48%7C49%7C50%7C51%7C52%7C53%7C54%7C55%7C56%7C58%7C59%7C60%7C61%7C63%7C64%7C65
%7C66%7C67%7C68%7C69%7C70%7C72%7C73%7C74%7C75%7C76%7C77%7C82%7C83%7C84%7C85%7C86%7C87%7C78%7C79%7C80%7C81&source=&r=6200048
&charset=utf-8&loc=hxxp%3A//www.divernet.com/&referer=hxxp%3A//www.google[.]com/url%3Fsa%3Dt%26rct%3Dj%26q%3D%26esrc%3Ds%26frm%3D1%26source%3Dweb%
26cd%3D1%26sqi%3D2%26ved%3D0CCoQFjAA%26url%3Dhxxp%253A%252F%252Fwww.divernet.com%252F%26ei%3DopvOUpyXFrSA2QXnv4DwDg%26usg%3DAFQjC
NHeSe4ebK0u69M-TBEGNkTZy-C-Nw%26bvm%3Dbv.59026428%2Cd.b2I - 18:53:12 UTC - 103.31.186[.]40 - seris[.]biz - GET /83059dd5.js?cp=openx.divernet.com
- 18:53:13 UTC - 85.93.134[.]203 - www.grad[.]ru - GET /forum/public/js/3rd_party/colorpicker/0490c7979e/?[base64 encoded string, reversed]
- 18:53:27 UTC - 85.93.134[.]203 - www.grad[.]ru - GET /forum/public/js/3rd_party/colorpicker/0490c7979e/?f=a&k=5797540687062433
- 18:53:27 UTC - 85.93.134[.]203 - www.grad[.]ru - GET /forum/public/js/3rd_party/colorpicker/0490c7979e/?f=s&k=5797540687062411
- 18:53:28 UTC - 85.93.134[.]203 - www.grad[.]ru - GET /forum/public/js/3rd_party/colorpicker/0490c7979e/?f=s&k=5797540687062411
- 18:53:28 UTC - 85.93.134[.]203 - www.grad[.]ru - GET /forum/public/js/3rd_party/colorpicker/0490c7979e/?f=s&k=5797540687062411
- 18:53:28 UTC - 85.93.134[.]203 - www.grad[.]ru - GET /forum/public/js/3rd_party/colorpicker/0490c7979e/?f=s&k=5797540687062411
- 18:53:28 UTC - 85.93.134[.]203 - www.grad[.]ru - GET /forum/public/js/3rd_party/colorpicker/0490c7979e/?f=npb.mp3&k=5797540687062444
ARTIFACTS FROM THE TRAFFIC:
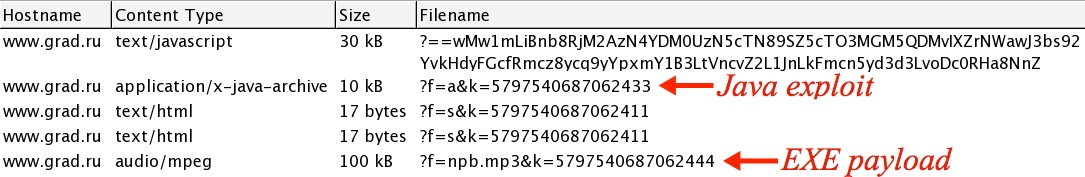
PRELIMINARY MALWARE ANALYSIS
Java exploit from 85.93.134[.]203 port 80 (www.grad[.]ru):
https://www.virustotal.com/en/file/1fa1be6254afe97b4c16d4ad17493e339616ed76750c5c9e964c4d6c962ec0ab/analysis/1389303190/
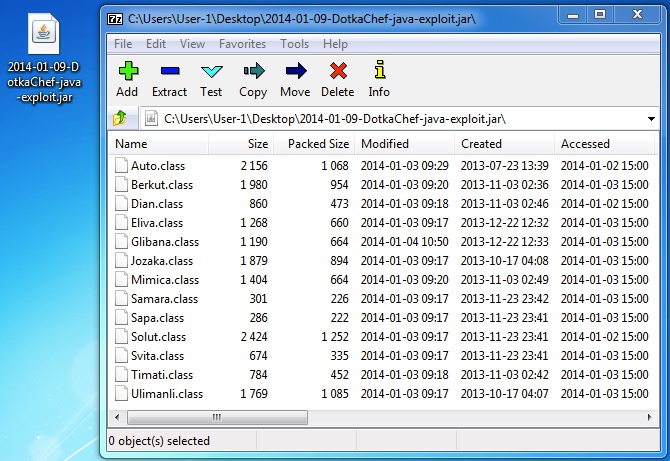
File name: 2014-01-10-DotkaChef-java-exploit.jar File size: 10,727 bytes
MD5 hash: e9f693dd04b6ebd64f9f7a18daca2387
Detection ratio: 5 / 48
First submitted: 2014-01-09 21:33:10 GMT
Kaspersky identified the Java exploit as CVE-2013-2423 which matches the Contagio list of exploits for the DotkaChef EK (see https://contagiodump.blogspot.com/2010/06/overview-of-exploit-packs-update.html).
Java archive contents:
EXE payload from 85.93.134[.]203 port 80 (www.grad[.]ru):
https://www.virustotal.com/en/file/b7b4d2274bcfc8a9c9c443589d720fa5bbcde3eefbb12f32d777d1d46159b1c3/analysis/1389303108/
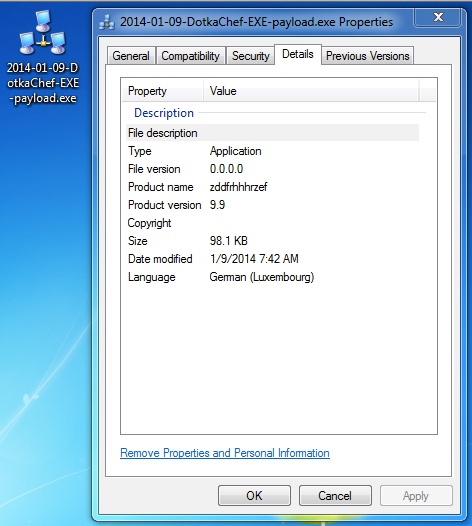
File name: 2014-01-10-DotkaChef-EXE-payload.exe File size: 100,537 bytes
MD5 hash: 0e7df6da243add3c86cdd450e09a0b2d
Detection ratio: 18 / 47
First submitted: 2014-01-09 15:19:37 GMT
Malware information:
Click here to return to the main page.