2014-01-27 - GOON EK
ASSOCIATED FILES:
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
PREVIOUS ENTRIES ON GOON EK TRAFFIC
- 2013-12-26 - Goon Exploit Kit traffic (Java exploit)
- 2014-01-13 - Goon EK uses MSIE exploit to deliver malware downloader (Internet Explorer exploit)
This time, the Goon EK domain used a Microsoft Silverlight exploit.
TRAFFIC
ALERTS
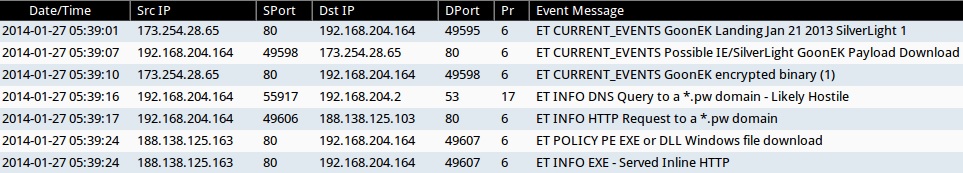
- 05:39:01 UTC - 173.254.28[.]65:80 - ET CURRENT_EVENTS GoonEK Landing Jan 21 2013 SilverLight 1
- 05:39:07 UTC - 173.254.28[.]65:80 - ET CURRENT_EVENTS Possible IE/SilverLight GoonEK Payload Download
- 05:39:10 UTC - 173.254.28[.]65:80 - ET CURRENT_EVENTS GoonEK encrypted binary (1)
- 05:39:16 UTC - [local host]:53 - ET INFO DNS Query to a *.pw domain - Likely Hostile
- 05:39:17 UTC - 188.138.125[.]103:80 - ET INFO HTTP Request to a *.pw domain
- 05:39:24 UTC - 188.138.125[.]163:80 - ET POLICY PE EXE or DLL Windows file download
- 05:39:24 UTC - 188.138.125[.]163:80 - ET INFO EXE - Served Inline HTTP
ASSOCIATED DOMAINS
- 74.220.219[.]124 - www.tcnp[.]com - Compromised website
- 176.31.24[.]102 - no domain name - Redirect
- 173.254.28[.]65 - gingerasiaescorts[.]com - Goon EK domain
- 188.138.125[.]103 - seosaw[.]pw - Malware callback domain
- 188.138.125[.]103 - now.googlefast[.]pw - Malware callback domain
INFECTION CHAIN OF EVENTS
- 05:38:58 UTC - 74.220.219[.]124 - www.tcnp[.]com - GET /blog
- 05:39:00 UTC - 176.31.24[.]102 - 176.31.24[.]102 - GET /post.php?id=3880804199
- 05:39:01 UTC - 173.254.28[.]65 - gingerasiaescorts[.]com - GET /xmlbrowser.aspx?pro-cache=ocdg&tmp-index=1969
- 05:39:07 UTC - 173.254.28[.]65 - gingerasiaescorts[.]com - GET /themes/cn/jqueryviewer.xap
- 05:39:07 UTC - 173.254.28[.]65 - gingerasiaescorts[.]com - GET /38705295.mp3
NOTE: The pcap also has the following post-infection callback traffic:
- 05:39:17 UTC - 188.138.125[.]103 - seosaw[.]pw - POST /wq782jwoqkQy19qkdh27hqudqj/order.php?page=104
- 05:39:24 UTC - 188.138.125[.]163 - now.googlefast[.]pw - GET /remote/index.php?u=22&hulio
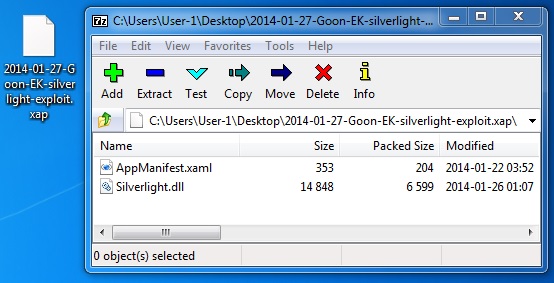
File name: 2014-01-27-Goon-EK-silverlight-exploit.xap
File size: 7,039 bytes
MD5 hash: 8e7a86c7d27d1eea7df0534b8879022f
Virus Total link: https://www.virustotal.com/en/file/1440714aeae4db23b3536cf88041d5bb84edd86e9f851b747df958f64293156a/analysis/
Detection ratio: 2 / 49
First submission to VirusTotal: 2014-01-26 15:29:10 UTC
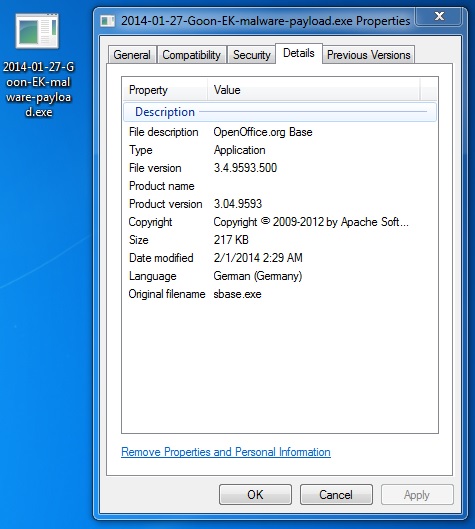
File name: 2014-01-27-Goonk-EK-malware-payload.exe
File size: 222,208 bytes
MD5 hash: d343946f3100566fa9949dd0d5ad2fac
Virus Total link: https://www.virustotal.com/en/file/ea7c1b1e79b041f9a76e92d7fc6bfd26150f0a58eb43ebd9c0e12eff55490370/analysis/
Detection ratio: 26 / 50
First submission to VirusTotal: 2014-01-28 19:51:30 UTC
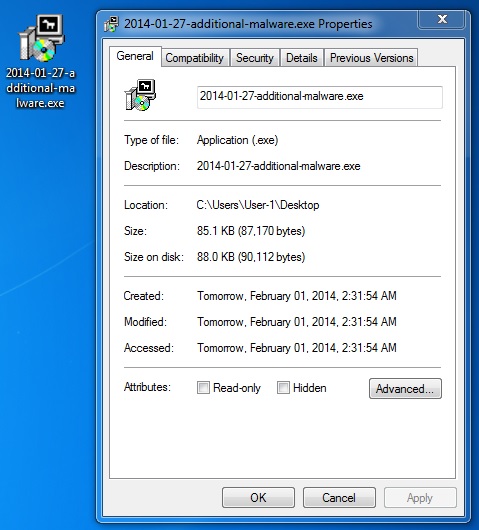
File name: 2014-01-27-additional-malware.exe
File size: 87,170 bytes
MD5 hash: dcc1f720310928b86de4c7efe19866a7
Virus Total link: https://www.virustotal.com/en/file/1a111faf9e50408f5fa9d9150694b86669dbfba2e768041394855780c0cd0936/analysis/
Detection ratio: 33 / 50
First submission to VirusTotal: 2014-02-01 02:40:00 UTC
Click here to return to the main page.