2014-03-06 - MALICIOUS ANDROID APP
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
INTRODUCTION
Reviewing IDS alerts at work, I came across a malicious URL. It was a simple redirect to a malicious Android app. I wanted to share this information, so I recreated the traffic at home with a Android phone I use to check out malicious apps.
DETAILS
This Android malware appears to be the "Not Compatible" trojan. The malware is spread through spam from compromised email accounts. If an Android device accesses the link, the malicious APK file is sent.
- https://news.softpedia.com/news/Cybercriminals-Use-Hijacked-Yahoo-Accounts-to-Spread-New-NotCompatible-Trojan-366985.shtml
- https://www.f-secure.com/v-descs/trojan-proxy-android-notcompatible.shtml
- https://web.archive.org/web/20140330045456/https://www.threattracksecurity.com/it-blog/android-trojan-notcompatible-gets-an-upgrade/
Here is a more recent link concerning my malware infection today:
THE INFECTION
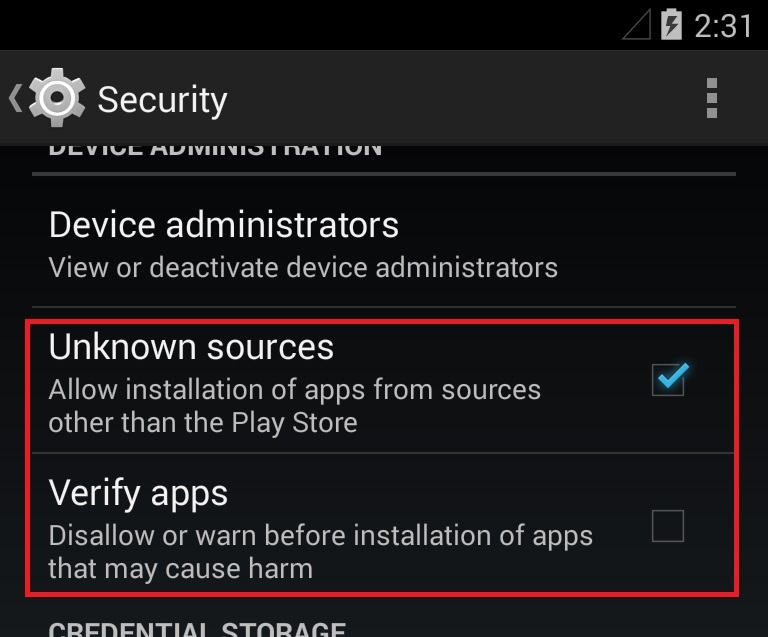
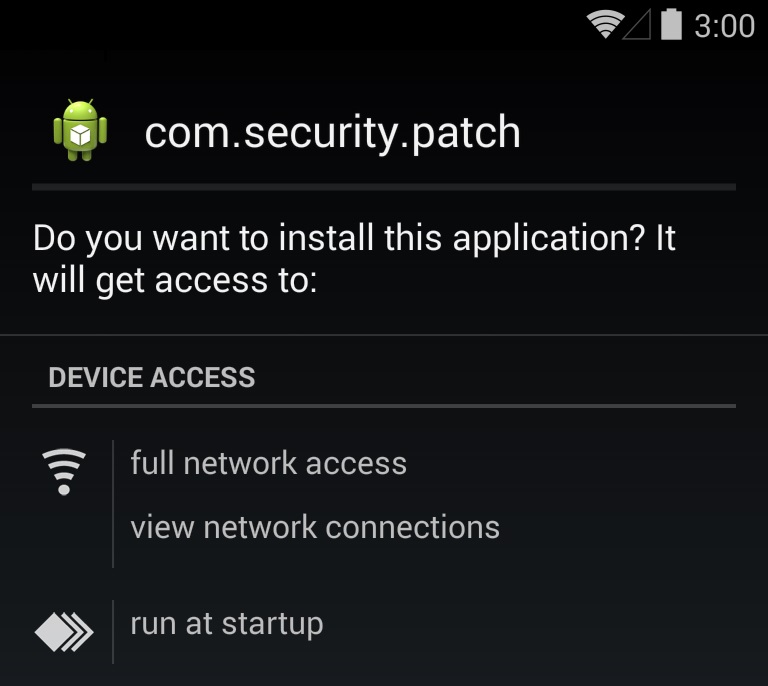
To infect an Android phone with this app, first go into the security settings and change the permissions.
Allow the installation of apps from unkown sources, and don't verify apps.
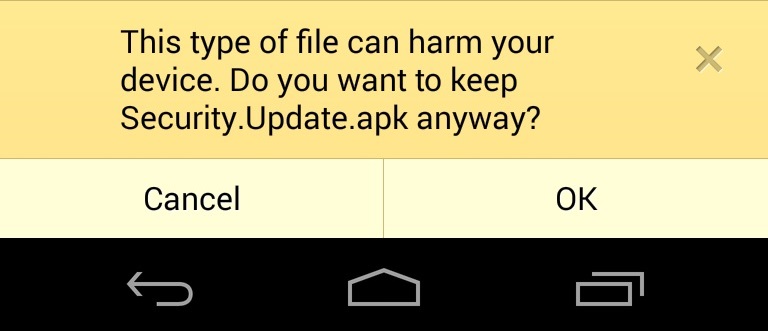
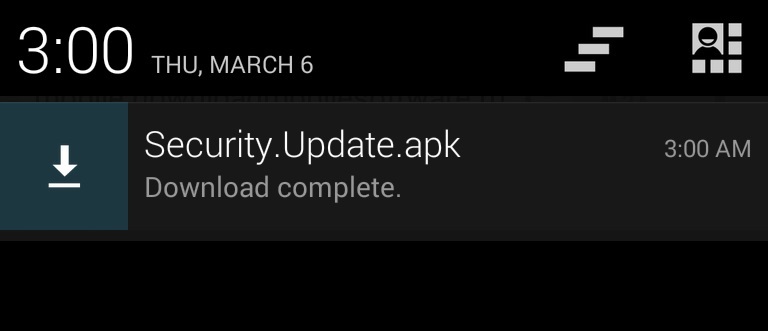
When I accessed the URL, it asked if I wanted to save the APK file. A notification shows the file is downloaded. The app can be installed by double-tapping the notification.
As with any other app, you'll see what permissions the app requests when you install it.
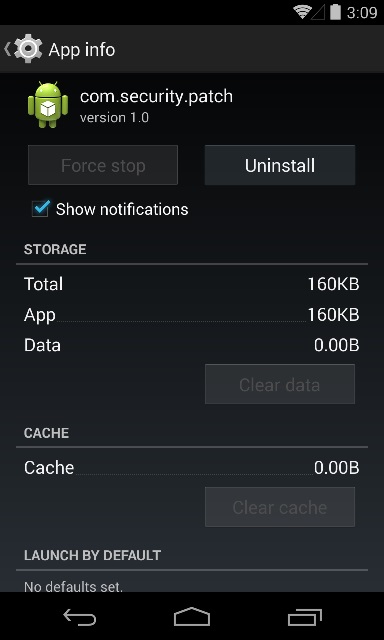
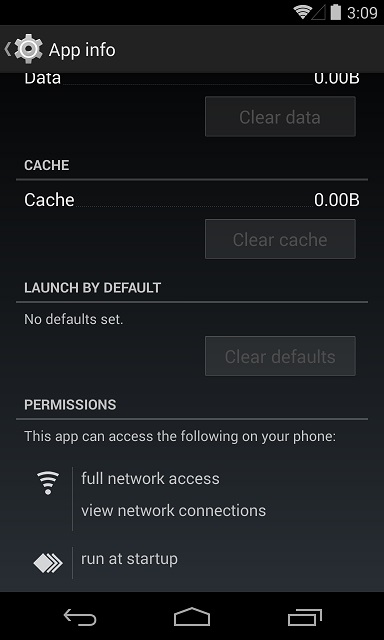
After installation, go to settings -> apps. Select the app from the list to see more infromation about it.
The app didn't do anything in the short time I had it on my test phone. That Android phone is only running as a WiFi device without any phone service. After nothing happened, I reset the phone to factory conditions. Let's review the WiFi network traffic on this...
NETWORK TRAFFIC
ASSOCIATED DOMAINS
- 142.11.194[.]109 - billions2buy[.]com - Redirect link
- 109.236.85[.]243 - mobile.downloadmobilesoftware[.]ru - Sends the malicious Android app
CHAIN OF EVENTS
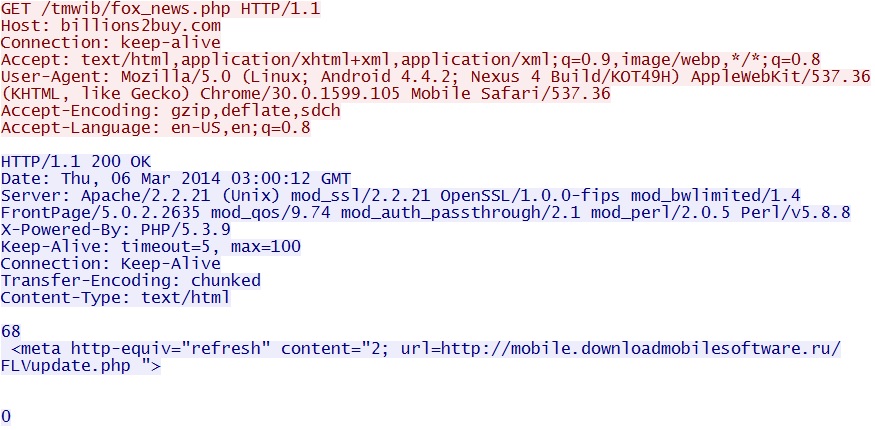
- 2014-03-06 03:00:12 UTC - 142.11.194[.]109:80 - billions2buy[.]com - GET /tmwib/fox_news.php
- 2014-03-06 03:00:12 UTC - HTTP/1.1 200 OK (text/html)
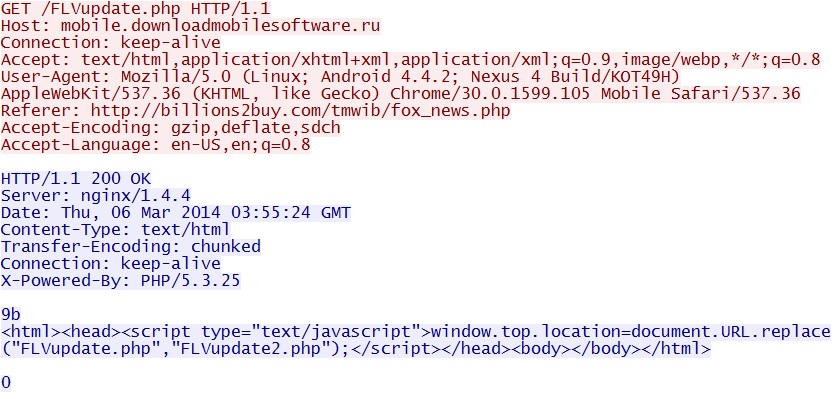
- 2014-03-06 03:00:15 UTC - 109.236.85[.]243:80 - mobile.downloadmobilesoftware[.]ru - GET /FLVupdate.php
- 2014-03-06 03:00:15 UTC - HTTP/1.1 200 OK (text/html)
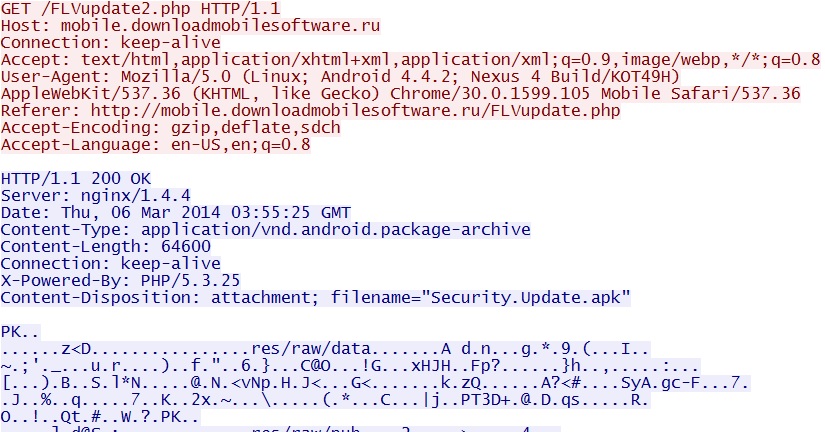
- 2014-03-06 03:00:15 UTC - 109.236.85[.]243:80 - mobile.downloadmobilesoftware[.]ru - GET /FLVupdate2.php
- 2014-03-06 03:00:26 UTC - HTTP/1.1 200 OK (application/vnd.android.package-archive)
PRELIMINARY MALWARE ANALYSIS
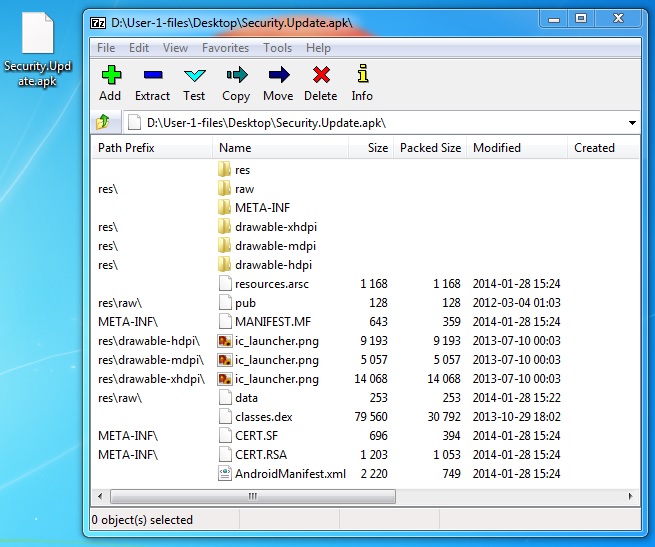
MALICIOUS ANDROID APP
File name: Security.Update.apk
File size: 64,600 bytes
MD5 hash: 02874f8cda359307723d5c0e7f4df6c2
Detection ratio: 27 / 50
First submission: 2014-02-20 19:23:39 UTC
VirusTotal link: https://www.virustotal.com/en/file/88e772f4eb3ddd9c3010d16572b859dbbe30f01b5eec53722912073d3193b17b/analysis/
ALERTS
No alerts seen for this traffic.
HIGHLIGHTS FROM THE TRAFFIC
Redirect link - billions2buy[.]com/tmwib/fox_news.php
First HTTP GET request for the malicious Android app - mobile.downloadmobilesoftware[.]ru/FLVupdate.php
Second HTTP GET request for the malicious Android app - mobile.downloadmobilesoftware[.]ru/FLVupdate2.php
Click here to return to the main page.