2014-03-11 - FIESTA EK
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
TRAFFIC
INFECTION TRAFFIC:
- 2014-03-11 16:01:19 UTC - 173.255.244[.]72 - www.mappery[.]com - GET /
- 2014-03-11 16:01:21 UTC - 209.239.113[.]39 - dkjcupyoen.myvnc[.]com - Fiesta EK traffic
- 2014-03-11 16:10:33 UTC - 213.242.245[.]241 port 443 - POST /76EB1199A9E23152CD009BEC7C1C4EA0FA43D17388
ASPROX BOTNET STYLE TRAFFIC FROM THE INFECTED HOST:
- 2014-03-11 16:05:49 UTC - 91.121.197[.]165:8080 - 91.121.197[.]165:8080 - POST /76EB1199A9E23152CD009BEC7C1C4EA0FA43D17388 (application/x-www-form-urlencoded)
- 2014-03-11 16:05:56 UTC - 46.244.10[.]231:80 - get-smokers[.]com - GET /b/shoe/951
- 2014-03-11 16:05:56 UTC - 109.163.239[.]243:80 - ecab-cap[.]com - GET /libw6/jquery/
- 2014-03-11 16:06:19 UTC - 109.163.239[.]243:80 - ecab-cap[.]com - GET /libw6/jquery/
- 2014-03-11 16:06:55 UTC - 91.121.197[.]165:8080 - 91.121.197[.]165:8080 - POST /76EB1199A9E23152CD009BEC7C1C4EA0FA43D17388 (application/x-www-form-urlencoded)
- 2014-03-11 16:08:36 UTC - 109.163.239[.]243:80 - ecab-cap[.]com - GET /k2/soft64.dll
Shortly after the Asprox-botnet callback traffic, my machine started sending out Asprox-botnet malspam:
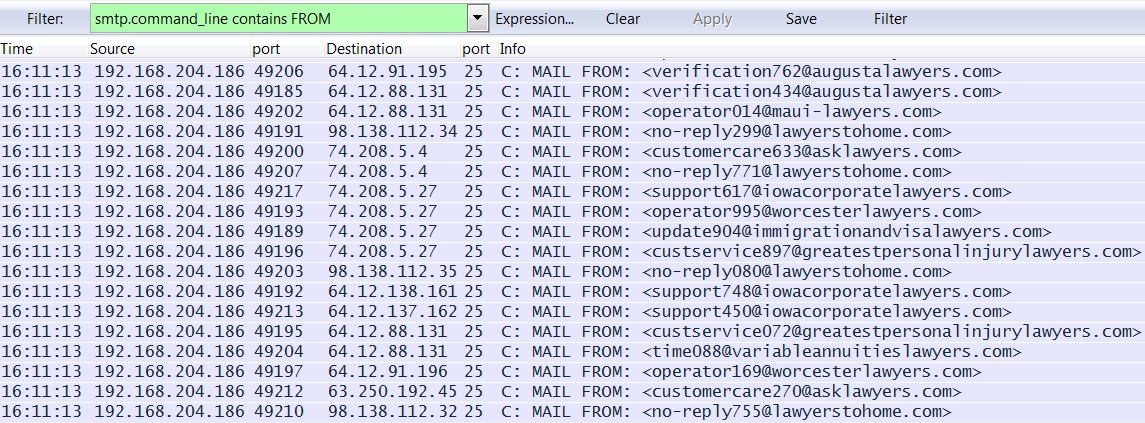
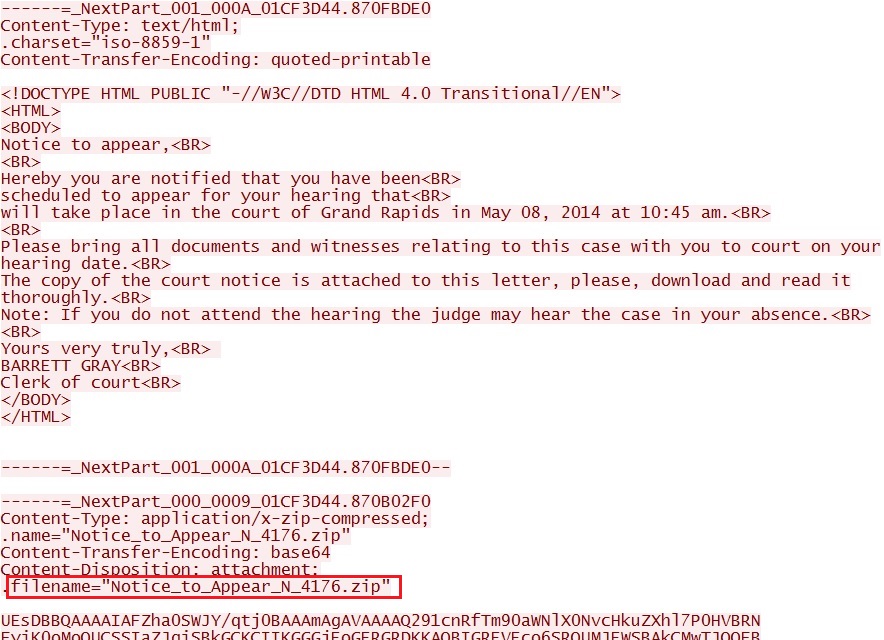
ALERTS
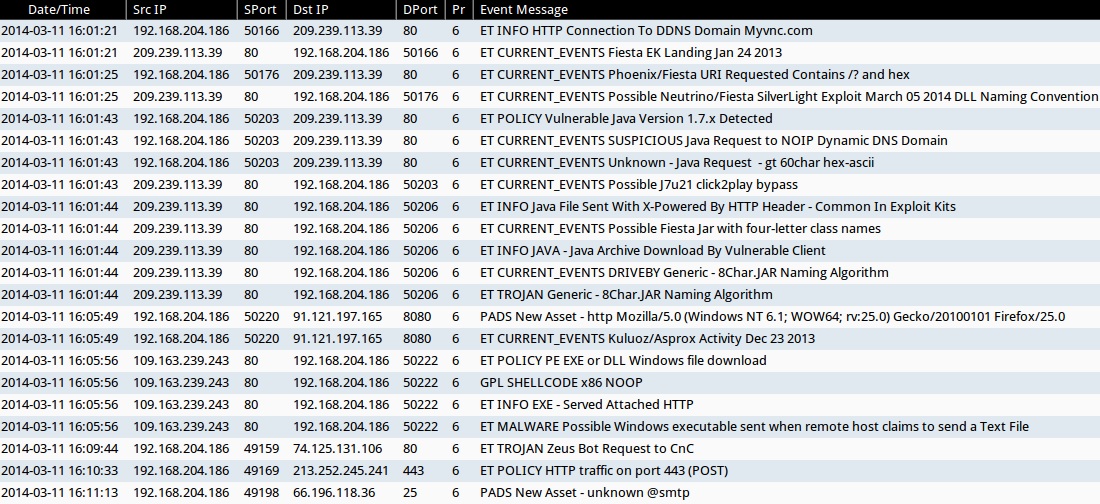
Here's what I saw for alerts on Security Onion:
MALWARE
Here's the malware info:
2014-03-11 Silverlight exploit (same as my Fiesta EK infection on 2014-03-09):
https://www.virustotal.com/en/file/c9fb7cbbc084f64ec44cd93eb294920cf801f37bfca42d37f5d7dd0aaa83fedb/analysis/
2014-03-11 Java exploit (same as my Fiesta EK infection on 2014-03-09):
https://www.virustotal.com/en/file/3c4a475c7bf334eff3baed3adfad18dae63df8fa925630478b9eedbd94f351d5/analysis/
2014-03-11 malware payload: 01394553707483.exe
https://www.virustotal.com/en/file/a53018328fa4d5b2d6148eae6eeee4e12292cff1acea5a77d2568c1bffd89390/analysis/
2014-03-11 follow-up malware: UpdateFlashPlayer_ae6914ec.exe
https://www.virustotal.com/en/file/36531452b9d111d851c449e08f5d2a354e146270f5b2033a82727b340c8e9d1e/analysis/
Click here to return to the main page.
