2014-04-06 - GOON/INFINITY EK
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
CHAIN OF EVENTS
ASSOCIATED DOMAINS
- 64.120.137[.]46 - utyuu.kirstendunnn[.]ru - Redirect
- 76.74.128[.]40 - fonsprom[.]com - Goon/Infinity EK
INFECTION TRAFFIC
- 01:49:48 UTC - utyuu.kirstendunnn[.]ru - GET /zyso.cgi?18
- 01:49:48 UTC - fonsprom[.]com - GET /updater.htm
- 01:49:49 UTC - fonsprom[.]com - GET /swf.swf
- 01:49:52 UTC - utyuu.kirstendunnn[.]ru - GET /zyso.cgi?18
- 01:49:52 UTC - fonsprom[.]com - GET /updater.htm
- 01:49:53 UTC - fonsprom[.]com - GET /1123.mp3?rnd=48046
- 01:49:55 UTC - fonsprom[.]com - GET /1123.mp3?rnd=22040
- 02:07:33 UTC - fonsprom[.]com - GET /9940.swf
- 02:07:33 UTC - fonsprom[.]com - GET /9926.xap
- 02:07:45 UTC - utyuu.kirstendunnn[.]ru - GET /favicon.ico
- 02:08:46 UTC - fonsprom[.]com - GET /7612.xml
- 02:08:46 UTC - fonsprom[.]com - GET /8064.jar
- 02:08:46 UTC - fonsprom[.]com - GET /META-INF/services/javax.xml.datatype.DatatypeFactory
PRELIMINARY MALWARE ANALYSIS
SILVERLIGHT EXPLOIT - CVE-2013-0074
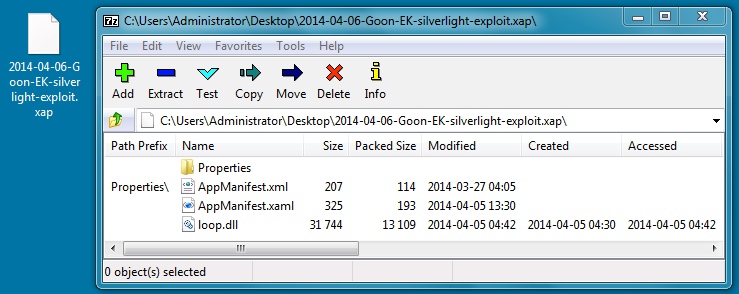
File name: 2014-04-06-Goon-EK-silverlight-exploitxap
File size: 13,802 bytes
MD5 hash: 7a44e0dc5f7f64385e5c99027e09f86c
Detection ratio: 9 / 51
First submission: 2014-04-05 11:11:25 UTC
VirusTotal link: https://www.virustotal.com/en/file/e78064ebee0249fdd98bea2ad8574719266b67feca9491d9375ff3d69f86d539/analysis/
JAVA EXPLOIT - CVE-2013-2465
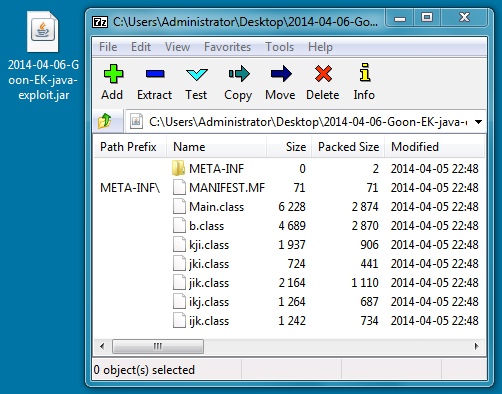
File name: 2014-04-06-Goon-EK-java-exploit.jar
File size: 10,798 bytes
MD5 hash: 4c89da4a9a79a2f8e4550bffb22ab8d7
Detection ratio: 4 / 51
First submission: 2014-04-06 02:59:27 UTC
VirusTotal link: https://www.virustotal.com/en/file/0379eacf34483452bfb564e6576e6e3140d1e9b52f978ee62921c2d307bd93e8/analysis/1396753167/
MALWARE PAYLOAD
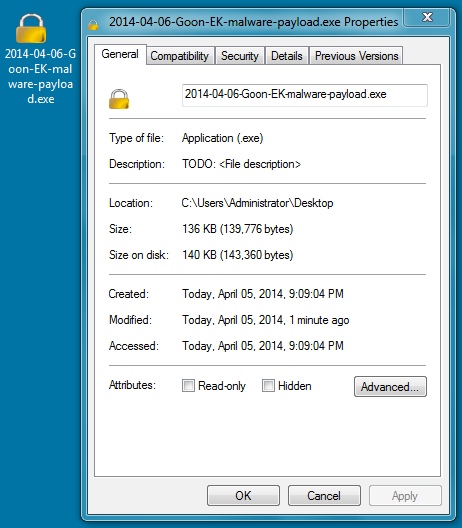
File name: 2014-04-06-Goon-EK-malware-payload.exe
File size: 139,776 bytes
MD5 hash: ed025cbe6c89c599d8cea579ab3182c3
Detection ratio: 3 / 50
First submission: 2014-04-06 02:10:01 UTC
VirusTotal link: https://www.virustotal.com/en/file/a8493d2c2ef6140f374fe405f7c6225528f08b43a63e66b310880ef07642ebf3/analysis/
ALERTS
ALERTS FROM THE INFECTION TRAFFIC (from Sguil on Security Onion)
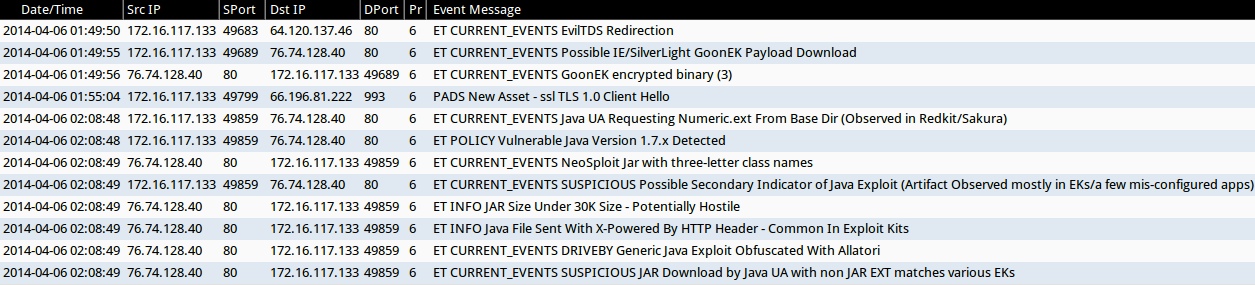
- 2014-04-06 01:49:50 UTC - 64.120.137[.]46:80 - ET CURRENT_EVENTS EvilTDS Redirection
- 2014-04-06 01:49:55 UTC - 76.74.128[.]40:80 - ET CURRENT_EVENTS Possible IE/SilverLight GoonEK Payload Download
- 2014-04-06 01:49:56 UTC - 76.74.128[.]40:80 - ET CURRENT_EVENTS GoonEK encrypted binary (3)
- 2014-04-06 02:08:48 UTC - 76.74.128[.]40:80 - ET CURRENT_EVENTS Java UA Requesting Numeric.ext From Base Dir (Observed in Redkit/Sakura)
- 2014-04-06 02:08:48 UTC - 76.74.128[.]40:80 - ET POLICY Vulnerable Java Version 1.7.x Detected
- 2014-04-06 02:08:49 UTC - 76.74.128[.]40:80 - ET CURRENT_EVENTS NeoSploit Jar with three-letter class names
- 2014-04-06 02:08:49 UTC - 76.74.128[.]40:80 - ET CURRENT_EVENTS SUSPICIOUS Possible Secondary Indicator of Java Exploit (Artifact Observed mostly in EKs/a few mis-configured apps)
- 2014-04-06 02:08:49 UTC - 76.74.128[.]40:80 - ET INFO JAR Size Under 30K Size - Potentially Hostile
- 2014-04-06 02:08:49 UTC - 76.74.128[.]40:80 - ET INFO Java File Sent With X-Powered By HTTP Header - Common In Exploit Kits
- 2014-04-06 02:08:49 UTC - 76.74.128[.]40:80 - ET CURRENT_EVENTS DRIVEBY Generic Java Exploit Obfuscated With Allatori
- 2014-04-06 02:08:49 UTC - 76.74.128[.]40:80 - ET CURRENT_EVENTS SUSPICIOUS JAR Download by Java UA with non JAR EXT matches various EKs
Click here to return to the main page.