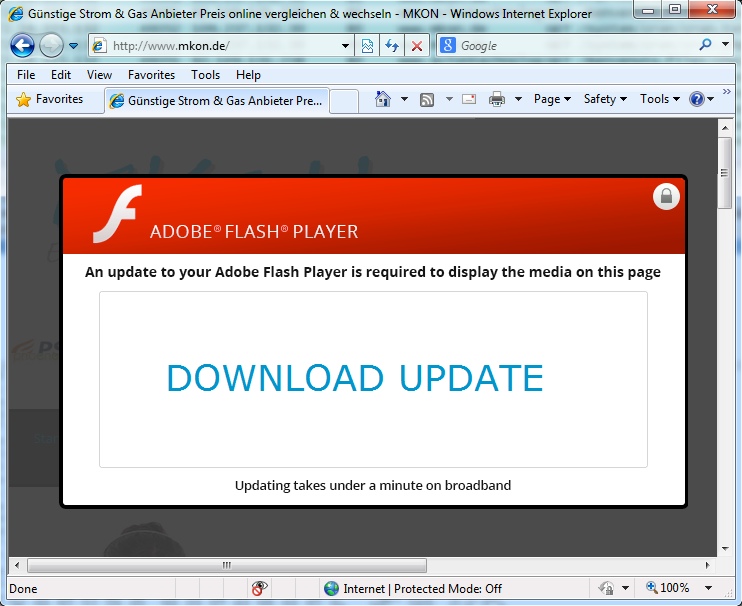
2014-04-29 - TODAY'S FAKE FLASH UPDATER HOSTED ON MICROSOFT ONEDRIVE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
MICROSOFT ONEDIRVE IP ADDRESSES HOSTING THE MALWARE:
- 134.170.104[.]176 - xmeazw.dm2301.livefilestore[.]com
- 134.170.109[.]176 - xmeazw.dm2304.livefilestore[.]com
NOTES:
- Found 3 more today while I was searching for exploit kits... Read: comromised website --> fake Flash updater notice --> Microsoft OneDrive hosting the malware
- rubikon[.]bg --> site[.]lt --> xmeazw.dm2301.livefilestore[.]com
- webradio-powerplay[.]de --> www.emiliabayer[.]com --> xmeazw.dm2304.livefilestore[.]com
- www.mkon[.]de --> aviontechnology[.]it --> xmeazw.dm2301.livefilestore[.]com
TODAY'S EXAMPLES
comromised website --> fake Flash updater notice --> Microsoft OneDrive hosting the malware
rubikon[.]bg --> site[.]lt --> xmeazw.dm2301.livefilestore[.]com
- 01:15:32 UTC - 87.120.40[.]168:80 - rubikon[.]bg - GET /
- 01:15:34 UTC - 87.120.40[.]168:80 - rubikon[.]bg - GET /stmenu.js
- 01:15:34 UTC - 87.120.40[.]168:80 - rubikon[.]bg - GET /jquery-1.5.1.min.js
- 01:15:34 UTC - 87.120.40[.]168:80 - rubikon[.]bg - GET /jquery.backstretch.min.js
- 01:15:34 UTC - 87.120.40[.]168:80 - rubikon[.]bg - GET /scroll.js
- 01:15:34 UTC - 87.120.40[.]168:80 - rubikon[.]bg - GET /menu.js
- 01:15:37 UTC - 79.98.26[.]193:80 - site[.]lt - GET /DmXRpr9F.php?id=11966723
- 01:15:38 UTC - 79.98.26[.]193:80 - site[.]lt - GET /DmXRpr9F.php?id=11966724
- 01:15:40 UTC - 87.120.40[.]168:80 - rubikon[.]bg - GET /stcode.js
- 01:15:41 UTC - 79.98.26[.]193:80 - site[.]lt - GET /DmXRpr9F.php?id=11966727
- 01:15:42 UTC - 79.98.26[.]193:80 - site[.]lt - GET /DmXRpr9F.php?id=11966731
- 01:15:43 UTC - 79.98.26[.]193:80 - site[.]lt - GET /DmXRpr9F.php?id=11966726
- 01:15:59 UTC - 79.98.26[.]193:80 - site[.]lt - GET /DmXRpr9F.php?html=27
- 01:16:01 UTC - 79.98.26[.]193:80 - site[.]lt - GET /checker.php
- 01:16:09 UTC - 134.170.104[.]176:443 - xmeazw.dm2301.livefilestore[.]com
- 01:16:09 UTC - 134.170.104[.]176:443 - xmeazw.dm2301.livefilestore[.]com
- 01:16:16 UTC - 79.98.26[.]193:80 - site[.]lt - GET /checker.php
HTTPS link from fake Flash updater notice:
- xmeazw.dm2301.livefilestore[.]com - GET /y2mSHM8N1E-7Gfshvhe-3l5_NCUYzZkHGEXj8qEH-GcjtG_g_V5w8CMY4LprNB-r4CnT2wwGiIr6QrS-QJWSB_UvS398df7NmzgpCQ
A0XUdzx8/FlashUpdater.exe
comromised website --> fake Flash updater notice --> Microsoft OneDrive hosting the malware
webradio-powerplay[.]de --> www.emiliabayer[.]com --> xmeazw.dm2304.livefilestore[.]com
- 02:44:00 UTC - 88.198.55[.]148:80 - webradio-powerplay[.]de - GET /
- 02:44:01 UTC - 88.198.55[.]148:80 - webradio-powerplay[.]de - GET /news.php
- 02:44:01 UTC - 88.198.55[.]148:80 - webradio-powerplay[.]de - GET /includes/jquery/jquery.js
- 02:44:02 UTC - 88.198.55[.]148:80 - webradio-powerplay[.]de - GET /includes/jscript.js
- 02:44:03 UTC - 88.198.55[.]148:80 - webradio-powerplay[.]de - GET /infusions/advanced_online_panel/includes/tooltip.js
- 02:44:05 UTC - 181.224.139[.]87:80 - www.emiliabayer[.]com - GET /3wgvnxqn.php?id=111527479
- 02:44:07 UTC - 181.224.139[.]87:80 - www.emiliabayer[.]com - GET /3wgvnxqn.php?html=27
- 02:44:08 UTC - 181.224.139[.]87:80 - www.emiliabayer[.]com - GET /checker.php
- 02:44:23 UTC - 181.224.139[.]87:80 - www.emiliabayer[.]com - GET /checker.php
- 02:44:38 UTC - 134.170.109[.]176:443 - xmeazw.dm2304.livefilestore[.]com
- 02:44:38 UTC - 181.224.139[.]87:80 - www.emiliabayer[.]com - GET /checker.php
- 02:44:53 UTC - 181.224.139[.]87:80 - www.emiliabayer[.]com - GET /checker.php
HTTPS link from fake Flash updater notice:
- xmeazw.dm2304.livefilestore[.]com - GET /y2mBtol82kkE74DcxuB2b14AxNTn8d44cfUgbkqLLlE6PTN3PaU3iImsgoq_eIl_HFjGvRssHi_xLv84RztnAgw1PSqGObpJDR3npeD4n-
BZEk/FlashUpdater.exe
comromised website --> fake Flash updater notice --> Microsoft OneDrive hosting the malware
www.mkon[.]de --> aviontechnology[.]it --> xmeazw.dm2301.livefilestore[.]com
- 02:48:31 UTC - 109.237.132[.]30:80 - www.mkon[.]de - GET /
- 02:48:33 UTC - 109.237.132[.]30:80 - www.mkon[.]de - GET /files/theme/js/jquery.selectnav.js
- 02:48:33 UTC - 109.237.132[.]30:80 - www.mkon[.]de - GET /assets/js/f14e9a439d7d.js
- 02:48:33 UTC - 109.237.132[.]30:80 - www.mkon[.]de - GET /files/theme/js/back-to-top.js
- 02:48:33 UTC - 109.237.132[.]30:80 - www.mkon[.]de - GET /files/theme/js/doubletaptogo.js
- 02:48:34 UTC - 109.237.132[.]30:80 - www.mkon[.]de - GET /assets/jquery/ui/1.10.3/jquery-ui.min.js
- 02:48:34 UTC - 62.149.128[.]163:80 - aviontechnology[.]it - GET /Benvenuto_files/JY9W7Vrb.php?id=
- 02:48:34 UTC - 109.237.132[.]30:80 - www.mkon[.]de - GET /assets/html5shiv/3.7.0/html5shiv.js
- 02:48:34 UTC - 109.237.132[.]30:80 - www.mkon[.]de - GET /assets/swipe/2.0/js/swipe.min.js
- 02:48:34 UTC - 109.237.132[.]30:80 - www.mkon[.]de - GET /assets/jquery/colorbox/1.4.31/js/colorbox.min.js
- 02:48:34 UTC - 109.237.132[.]30:80 - www.mkon[.]de - GET /assets/jquery/tablesorter/2.0.5/js/tablesorter.js
- 02:48:34 UTC - 109.237.132[.]30:80 - www.mkon[.]de - GET /files/theme/js/selectnav-custom.js
- 02:48:34 UTC - 109.237.132[.]30:80 - www.mkon[.]de - GET /files/theme/js/doubletaptogo_custom.js
- 02:48:34 UTC - 109.237.132[.]30:80 - www.mkon[.]de - GET /assets/jquery/mediaelement/2.13.1/js/mediaelement-and-player.min.js
- 02:48:34 UTC - 62.149.131[.]238:80 - www.aviontechnology[.]it - GET /Benvenuto_files/JY9W7Vrb.php?id=
- 02:48:41 UTC - 62.149.131[.]238:80 - www.aviontechnology[.]it - GET /Benvenuto_files/JY9W7Vrb.php?html=27
- 02:48:42 UTC - 62.149.131[.]238:80 - www.aviontechnology[.]it - GET /Benvenuto_files/checker.php
- 02:48:58 UTC - 62.149.131[.]238:80 - www.aviontechnology[.]it - GET /Benvenuto_files/checker.php
- 02:49:12 UTC - 62.149.131[.]238:80 - www.aviontechnology[.]it - GET /Benvenuto_files/checker.php
- 02:49:27 UTC - 62.149.131[.]238:80 - www.aviontechnology[.]it - GET /Benvenuto_files/checker.php
- 02:49:42 UTC - 62.149.131[.]238:80 - www.aviontechnology[.]it - GET /Benvenuto_files/checker.php
- 02:49:58 UTC - 62.149.131[.]238:80 - www.aviontechnology[.]it - GET /Benvenuto_files/checker.php
- 02:50:13 UTC - 62.149.131[.]238:80 - www.aviontechnology[.]it - GET /Benvenuto_files/checker.php
- 02:50:28 UTC - 62.149.131[.]238:80 - www.aviontechnology[.]it - GET /Benvenuto_files/checker.php
- 02:50:43 UTC - 62.149.131[.]238:80 - www.aviontechnology[.]it - GET /Benvenuto_files/checker.php
- 02:50:55 UTC - 134.170.104[.]176:443 - xmeazw.dm2301.livefilestore[.]com
- 02:50:58 UTC - 62.149.131[.]238:80 - www.aviontechnology[.]it - GET /Benvenuto_files/checker.php
- 02:51:13 UTC - 62.149.131[.]238:80 - www.aviontechnology[.]it - GET /Benvenuto_files/checker.php
HTTPS link from fake Flash updater notice:
- xmeazw.dm2301.livefilestore[.]com - GET /y2mF4MC8q5OpMhkvfvn05KE9nxa08rpqNA5h_mMIYII8Y_LyPhEEw_GJpmDe3jKfrrQ_FVPdh0Fe5KmwSGHRMBgMhYdsioIDeZo
q0nk-va2ehM/FlashUpdater.exe
PRELIMINARY MALWARE ANALYSIS
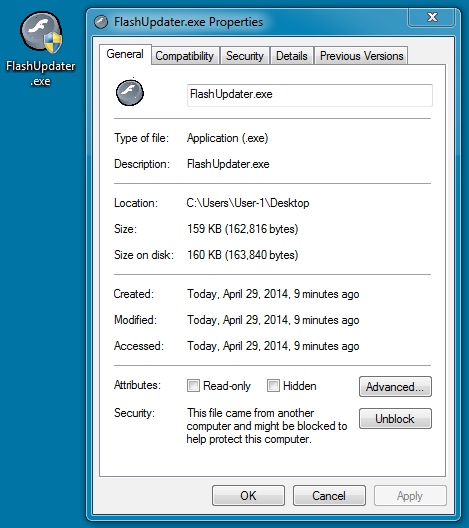
File name: FlashUpdater.exe
File size: 162,816 bytes
MD5 hash: f7193a06030e19e0d0c66dfa013481a5
Detection ratio: 3 / 51
First submission: 2014-04-29 01:25:40 UTC
VirusTotal link: https://www.virustotal.com/en/file/938700a3f84dd6ef0e414b83ad4ec132f0e94504f8ad9bbfa62eefded9ebd49b/analysis/
NOTE: This is the same file size and icon as yesterday, but a different MD5 hash.
Click here to return to the main page.