2014-05-06 - FLASHPACK EK FROM 89.121.252[.]70 - LCHHMBA[.]COM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
PREVIOUS FLASHPACK EK TRAFFIC ON THIS BLOG:
- 2014-03-29 FlashPack EK from 31.31.196[.]12 - fm.gen[.]tr
- 2014-04-03 FlashPack EK from 78.157.209[.]194 - forexforum.gen[.]tr
- 2014-04-12 FlashPack EK from 176.102.37[.]55 - kliftpres[.]com
- 2014-04-13 FlashPack EK from 176.102.37[.]55 - weoikcus[.]org
- 2014-04-17 FlashPack EK from 178.33.85[.]108 - gecekiyafetleri.gen[.]tr
- 2014-05-06 FlashPack EK from 89.121.252[.]70 - lchhmba[.]com
CHAIN OF EVENTS
FLASHPACK EK:
- 05:34:59 UTC - 89.121.252[.]70 - 5tcq1yyzey8kafdq1nmvqtw.lchhmba[.]com - GET /index.php?c=cHVobXVsa2Y9bnYmdGltZT0xNDA1MDYwNDQ2MTE1Nzg2MDc0NyZzcm
M9MTc2JnN1cmw9d3d3LnRvbGx5d29vZC5uZXQmc3BvcnQ9ODAma2V5PTU1QTRENzQ2JnN1cmk9Lw== - 05:35:00 UTC - 89.121.252[.]70 - 5tcq1yyzey8kafdq1nmvqtw.lchhmba[.]com - GET /favicon.ico
- 05:35:00 UTC - 89.121.252[.]70 - 5tcq1yyzey8kafdq1nmvqtw517653bf85b673be642451e29219fd2fd.lchhmba[.]com - GET /index2.php
- 05:35:01 UTC - 89.121.252[.]70 - 5tcq1yyzey8kafdq1nmvqtw517653bf85b673be642451e29219fd2fd.lchhmba[.]com - GET /favicon.ico
- 05:35:02 UTC - 89.121.252[.]70 - 5tcq1yyzey8kafdq1nmvqtw.lchhmba[.]com - GET /tresting/avalonr/allow.php
- 05:35:02 UTC - 89.121.252[.]70 - 5tcq1yyzey8kafdq1nmvqtw.lchhmba[.]com - GET /tresting/avalonr/js/pd.php?id=357463713179797a6579386b61666471316e6d76717477
3531373635336266383562363733626536343234353165323932313966643266642e6c6368686d62612e636f6d - 05:35:04 UTC - 89.121.252[.]70 - 5tcq1yyzey8kafdq1nmvqtw.lchhmba[.]com - POST /tresting/avalonr/json.php (application/x-www-form-urlencoded)
- 05:35:05 UTC - 89.121.252[.]70 - 5tcq1yyzey8kafdq1nmvqtw.lchhmba[.]com - GET /tresting/avalonr/msie.php
- 05:35:05 UTC - 89.121.252[.]70 - 5tcq1yyzey8kafdq1nmvqtw.lchhmba[.]com - GET /tresting/avalonr/silver.php
- 05:35:05 UTC - 89.121.252[.]70 - 5tcq1yyzey8kafdq1nmvqtw.lchhmba[.]com - GET /tresting/avalonr/javadb.php
- 05:35:05 UTC - 89.121.252[.]70 - 5tcq1yyzey8kafdq1nmvqtw.lchhmba[.]com - GET /tresting/avalonr/flash2014.php
- 05:35:05 UTC - 89.121.252[.]70 - 5tcq1yyzey8kafdq1nmvqtw.lchhmba[.]com - GET /tresting/avalonr/include/ba1993db48c5677b5ef9b9b59885e573.eot
- 05:35:07 UTC - 89.121.252[.]70 - 5tcq1yyzey8kafdq1nmvqtw.lchhmba[.]com - GET /tresting/avalonr/include/ff28ee9d59d6f49ac7bec1d70b0e0688.eot
- 05:35:08 UTC - 89.121.252[.]70 - 5tcq1yyzey8kafdq1nmvqtw.lchhmba[.]com - GET /tresting/avalonr/loadsilver.php
- 05:35:15 UTC - 89.121.252[.]70 - 5tcq1yyzey8kafdq1nmvqtw.lchhmba[.]com - GET /tresting/avalonr/include/cdc7118beea93333dd84394740de6b79.jar
- 05:35:15 UTC - 89.121.252[.]70 - 5tcq1yyzey8kafdq1nmvqtw.lchhmba[.]com - GET /tresting/avalonr/include/cdc7118beea93333dd84394740de6b79.jar
- 05:35:17 UTC - 89.121.252[.]70 - 5tcq1yyzey8kafdq1nmvqtw.lchhmba[.]com - GET /tresting/avalonr/loaddb.php
- 05:36:10 UTC - 89.121.252[.]70 - 5tcq1yyzey8kafdq1nmvqtw.lchhmba[.]com - GET /software.php?05060536576195906
POST-INFECTION TRAFFIC:
- 05:35:21 UTC - 5.77.49[.]215 port 61107 - GET /stat?uid=100&downlink=1111&uplink=1111&id=002502BE&statpass=bpass&version=20140506&features=30i
&guid=99734915-aab3-4673-bce4-7a80112a56f6&comment=20140506&p=0&s= - 05:35:21 UTC - 5.77.49[.]215 port 31562 - Glupteba-style callback traffic
- 05:38:00 UTC - 173.194.116[.]179 - www.google[.]com - GET /robots.txt
- 05:38:01 UTC - 174.143.144[.]69 port 25 - GET /
- 05:38:03 UTC - 173.194.116[.]176 - www.google[.]com - GET /robots.txt
- 05:38:01 UTC - 174.143.144[.]69 port 25 - GET /
PRELIMINARY MALWARE ANALYSIS
JAVA EXPLOIT
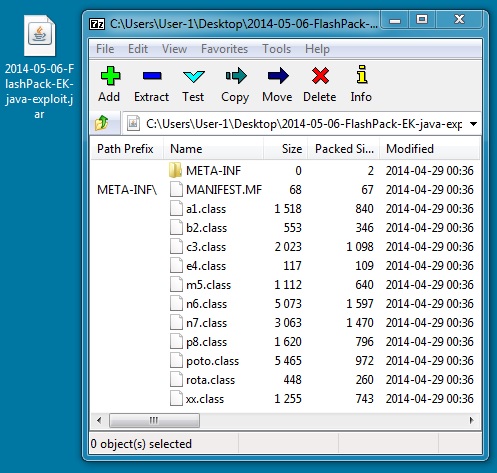
File name: 2014-05-06-FlashPack-EK-java-exploit.jar
File size: 10,408 bytes
MD5 hash: ad97fb241a7f8ec33d36a7735e5693d7
Detection ratio: 5 / 52
First submission: 2014-05-06 05:54:17 UTC
VirusTotal link: https://www.virustotal.com/en/file/35e59f62804e8fe688c6536ce0007f7cf8b65dc7924fc6531b6b5d87603664f1/analysis/
SILVERLIGHT EXPLOIT (SENT AS FIRST .EOT FILE)
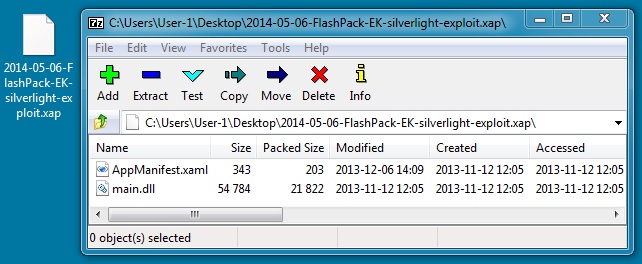
File name: 2014-05-06-FlashPack-EK-silverlight-exploit.xap
File size: 22,319 bytes
MD5 hash: 0fdf64c3cdd5d592fdb357fbba5efeec
Detection ratio: 30 / 52
First submission: 2014-03-13 18:36:49 UTC
VirusTotal link: https://www.virustotal.com/en/file/119fdd3aa3154ce53e8df0dcebfb9469fced6c76c1668cb0d8a1f98106a5ea98/analysis/
FIRST MALWARE FILE NOTED (SENT AS SECOND .EOT FILE)
File name: 2014-05-06-FlashPack-EK-malware-01.dll
File size: 13,312 bytes
MD5 hash: 2ecd2f198f4c2ef219c7c20f07213c1a
Detection ratio: 3 / 52
First submission: 2014-05-06 05:58:35 UTC
VirusTotal link: https://www.virustotal.com/en/file/9481f5aef96d811fd497bc9cfd579419bec035771c0ffc181f794dd9fabb819d/analysis/
MALWARE PAYLOAD
File name: 2014-05-06-FlashPack-EK-malware-payload.exe
File size: 106,937 bytes
MD5 hash: 4e59aff2917f5185573624260853d73d
Detection ratio: 4 / 52
First submission: 2014-05-06 05:55:14 UTC
VirusTotal link: https://www.virustotal.com/en/file/b18b10d43482e1eae6c51fab4c15b42e76a72555f3545a3412a2b69c217e08cf/analysis/
LAST MALWARE DOWNLOADED
File name: 2014-05-06-FlashPack-EK-post-infection-malware.exe
File size: 153,510 bytes
MD5 hash: a3cfa670cd32cce347cea317f5c23f89
Detection ratio: 11 / 52
First submission: 2014-05-06 05:59:20 UTC
VirusTotal link: https://www.virustotal.com/en/file/d6d701353be6799ff518f6f3bde9edb3304d688341f854705af10b5024f0fc79/analysis/
ALERTS
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion)

- 2014-05-06 05:34:59 UTC - 89.121.252[.]70:80 - ET CURRENT_EVENTS Cushion Redirection
- 2014-05-06 05:35:00 UTC - [local host]:53 - ET TROJAN Linux/Onimiki DNS trojan activity long format (Inbound)
- 2014-05-06 05:35:00 UTC - [local host]:53 - ET TROJAN Linux/Onimiki DNS trojan activity long format (Outbound)
- 2014-05-06 05:35:04 UTC - 89.121.252[.]70:80 - ET INFO JAVA - ClassID
- 2014-05-06 05:35:05 UTC - 89.121.252[.]70:80 - ET CURRENT_EVENTS Possible Safe/CritX/FlashPack Common Filename javadb.php
- 2014-05-06 05:35:05 UTC - 89.121.252[.]70:80 - ET CURRENT_EVENTS Magnitude EK (formerly Popads) - Font Exploit - 32HexChar.eot
- 2014-05-06 05:35:05 UTC - 89.121.252[.]70:80 - ET CURRENT_EVENTS Possible JavaFX Click To Run Bypass 2
- 2014-05-06 05:35:05 UTC - 89.121.252[.]70:80 - ET CURRENT_EVENTS CritX/SafePack/FlashPack SilverLight Secondary Landing
- 2014-05-06 05:35:08 UTC - 89.121.252[.]70:80 - ET CURRENT_EVENTS Safe/CritX/FlashPack SilverLight Payload
- 2014-05-06 05:35:09 UTC - 89.121.252[.]70:80 - ET POLICY PE EXE or DLL Windows file download
- 2014-05-06 05:35:09 UTC - 89.121.252[.]70:80 - ET INFO EXE - Served Inline HTTP
- 2014-05-06 05:35:09 UTC - 89.121.252[.]70:80 - ET CURRENT_EVENTS Possible CritX/SafePack/FlashPack EXE Download
- 2014-05-06 05:35:15 UTC - 89.121.252[.]70:80 - ET POLICY Vulnerable Java Version 1.7.x Detected
- 2014-05-06 05:35:15 UTC - 89.121.252[.]70:80 - ET CURRENT_EVENTS Nuclear/Safe/CritX/FlashPack - Java Request - 32char hex-ascii
- 2014-05-06 05:35:16 UTC - 89.121.252[.]70:80 - ET INFO JAR Size Under 30K Size - Potentially Hostile
- 2014-05-06 05:35:16 UTC - 89.121.252[.]70:80 - ET INFO JAVA - Java Archive Download By Vulnerable Client
- 2014-05-06 05:35:17 UTC - 89.121.252[.]70:80- ET POLICY Java EXE Download
- 2014-05-06 05:35:17 UTC - 89.121.252[.]70:80 - ET TROJAN Java EXE Download by Vulnerable Version - Likely Driveby
- 2014-05-06 05:35:21 UTC - 5.77.49[.]215:61107 - ET TROJAN Win32/Glupteba CnC Checkin
- 2014-05-06 05:36:27 UTC - 195.2.253[.]38:80 - ET INFO GENERIC SUSPICIOUS POST to Dotted Quad with Fake Browser 1
Click here to return to the main page.