2014-06-03 - ANGLER EK FROM 85.25.43[.]60 PORT 2980 - JUGOSLAAVIENFISUN.DVDANDGIFTS[.]CO[.]ZA
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- This is the first time I've seen Angler EK use a non-standard port for HTTP
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 77.93.218[.]17 - www.racionalcz[.]cz - Comrpomised website
- 141.101.117[.]21 - 8bfd2cd9[.]eu - Redirect
- 85.25.43[.]60 - jugoslaavienfisun.dvdandgifts[.]co[.]za:2980 - Angler EK on TCP port 2980
- 108.162.196[.]238 - afpstatstrack[.]pw - Post-infection callback from sandbox analysis
COMPROMISED WEBSITE AND REDIRECT:
- 06:27:49 - www.racionalcz[.]cz - GET /
- 06:27:55 - 8bfd2cd9[.]eu - GET /script.html?0.9801302868625199
ANGLER EK:
- 06:27:58 - jugoslaavienfisun.dvdandgifts[.]co[.]za:2980 - GET /6ixxz709c7.php
- 06:28:18 - jugoslaavienfisun.dvdandgifts[.]co[.]za:2980 - GET /preYUIdZbBMpGFTaCjpz6xbqWEZNEgRFAjTue09AwvP4YWrYyx1tPWVG6rVtWjH8
- 06:28:21 - jugoslaavienfisun.dvdandgifts[.]co[.]za:2980 - GET /RBh8sPEUVNf0K_DYznq1da9I1lZnuVuhfzi8Ntnwbnt7UTYEzKiQP-GtxkOVsgLa
- 06:28:26 - jugoslaavienfisun.dvdandgifts[.]co[.]za:2980 - GET /pRPQTx387JTKdo5oOGEn3sX1vq6anRKyezt3t2Q4g0EJoguk6hCgIgmlZzNPb9k4
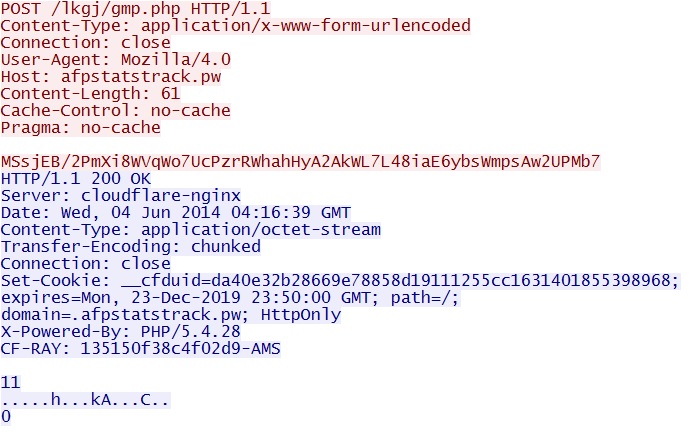
TRAFFIC FROM SANDBOX ANALYSIS OF MALWARE PAYLOAD:
- 108.162.196[.]238 port 80 - afpstatstrack[.]pw - POST /lkgj/gmp.php
PRELIMINARY MALWARE ANALYSIS
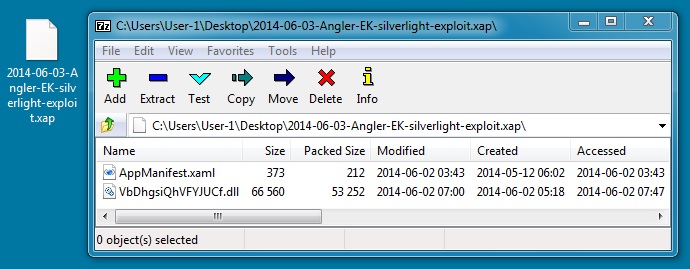
SILVERLIGHT EXPLOIT
File name: 2014-06-03-Angler-EK-silverlight-exploit.xap
File size: 53,913 bytes
MD5 hash: 5613d0312a0acf3a86f4d427b645dc5e
Detection ratio: 1 / 52
First submission: 2014-06-04 04:16:00 UTC
VirusTotal link: https://www.virustotal.com/en/file/92d5995e66e913e97286d436a048de0459e7c21a29b93d7febd1ead880a43963/analysis/
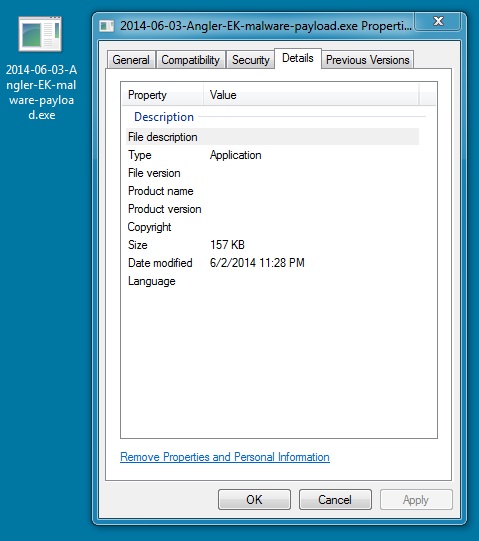
MALWARE PAYLOAD
File name: 2014-06-03-Angler-EK-malware-payload.exe
File size: 161,280 bytes
MD5 hash: 942f89a745e22b6d6156b77717eaa14c
Detection ratio: 3 / 51
First submission: 2014-06-03 09:29:11 UTC
VirusTotal link: https://www.virustotal.com/en/file/65c3ec6d48f5b3d9e77b48793461fe689d6110e3dade714a0251c02ae8db35ad/analysis/
ALERTS
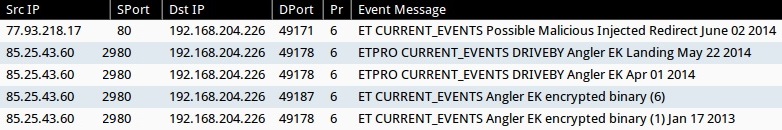
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion)
Emerging Threats and ETPRO rulesets:
NOTE: I used tcprewrite to change the port on 85.23.43[.]60 from 2980 to 80, and I used tcpreplay to generate the Angler EK events. On a default Security Onion install, you would only see the first event.
- 77.93.218[.]17:80 - ET CURRENT_EVENTS Possible Malicious Injected Redirect June 02 2014 (sid:2018514)
- 85.25.43[.]60:2980 - ETPRO CURRENT_EVENTS DRIVEBY Angler EK Landing May 22 2014 (sid:2808076)
- 85.25.43[.]60:2980 - ETPRO CURRENT_EVENTS DRIVEBY Angler EK Apr 01 2014 (sid:2807913)
- 85.25.43[.]60:2980 - ET CURRENT_EVENTS Angler EK encrypted binary (6) (sid:2018510)
- 85.25.43[.]60:2980 - ET CURRENT_EVENTS Angler EK encrypted binary (1) Jan 17 2013 (sid:2017984)
ALERTS FOR PCAP FROM MALWR SANDBOX ANALYSIS:
- 108.162.196[.]238:80 - ET TROJAN Andromeda Checkin (sid:2016223)
HIGHLIGHTS FROM THE TRAFFIC
Callback traffic from sandbox analysis of the malware payload:
Click here to return to the main page.