2014-06-09 - NUCLEAR EK FROM 185.10.57[.]167 - BT.REALWESTCHESTERCOUNTY[.]COM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
CHAIN OF EVENTS
NUCLEAR EK:
- 05:57:31 UTC - 185.10.57[.]167:80 - bt.realwestchestercounty[.]com - GET /f31e4820gvtqdw.html
- 05:57:50 UTC - 185.10.57[.]167:80 - bt.realwestchestercounty[.]com - GET /3531460654/3/1402272480.jar
- 05:57:51 UTC - 185.10.57[.]167:80 - bt.realwestchestercounty[.]com - GET /f/3/1402272480/3531460654/2
- 05:57:52 UTC - 185.10.57[.]167:80 - bt.realwestchestercounty[.]com - GET /f/3/1402272480/3531460654/2/2
POST-INFECTION TRAFFIC:
- 05:58:04 UTC - 14.54.223[.]63:80 - history-later[.]su - GET /b/shoe/1480
- 05:58:07 UTC - 173.20.248[.]44:80 - gerring-serilg[.]su - GET /phocaguestbook-qq89/jquery/
- 05:58:15 UTC - 173.20.248[.]44:80 - gerring-serilg[.]su - GET /phocaguestbook-qq89/jquery/
- 05:58:29 UTC - 208.115.105[.]47:80 - proper.EBBENWOODWORKING[.]COM - POST /es/cambios.php
- 05:59:29 UTC - 173.20.248[.]44:80 - gerring-serilg[.]su - GET /uniterevolutionq-ll56/soft64.dll
- 05:59:34 UTC - 31.186.103[.]103:80 - defie-guret[.]su - GET /b/eve/37437f7382928de2151b8487
- 06:00:28 UTC - 31.186.103[.]103:80 - defie-guret[.]su - POST /b/opt/D2047CDD51E03CC4E431CE55
- 06:00:32 UTC - 31.186.103[.]103:80 - defie-guret[.]su - GET /b/letr/994920C1BEDB672D0B0A95BC
- 06:00:35 UTC - 31.186.103[.]103:80 - defie-guret[.]su - POST /b/opt/9D011F4249E86E3EFC399CAF
- 06:00:55 UTC - 31.186.103[.]103:80 - defie-guret[.]su - POST /b/req/0D478A09A56E15E910BFE778
- 06:01:15 UTC - 31.186.103[.]103:80 - defie-guret[.]su - POST /b/req/23B74C8637E75EDD8236AC4C
CLICKFRAUD TRAFFIC BEGINS:
- 06:01:16 UTC - 192.162.19[.]34:80 - country-search[.]com - GET /
- 06:01:16 UTC - 192.162.19[.]34:80 - bubblegum-search[.]com - GET /
- 06:01:16 UTC - 192.162.19[.]34:80 - aquariums-search[.]com - GET /
- 06:01:16 UTC - 192.162.19[.]34:80 - projects-search[.]com - GET /
- 06:01:16 UTC - 192.162.19[.]34:80 - ecored-search[.]com - GET /
- 06:01:16 UTC - 192.162.19[.]34:80 - phantom-search[.]com - GET /
- 06:01:16 UTC - 192.162.19[.]34:80 - provide-search[.]com - GET /
- 06:01:16 UTC - 192.162.19[.]34:80 - truth-search[.]com - GET /
- 06:01:16 UTC - 192.162.19[.]34:80 - available-search[.]com - GET /
- 06:01:16 UTC - 192.162.19[.]34:80 - available-search[.]com - GET /
- 06:01:16 UTC - 192.162.19[.]34:80 - travels-search[.]com - GET /
- 06:01:16 UTC - 192.162.19[.]34:80 - blues-search[.]com - GET /
PRELIMINARY MALWARE ANALYSIS
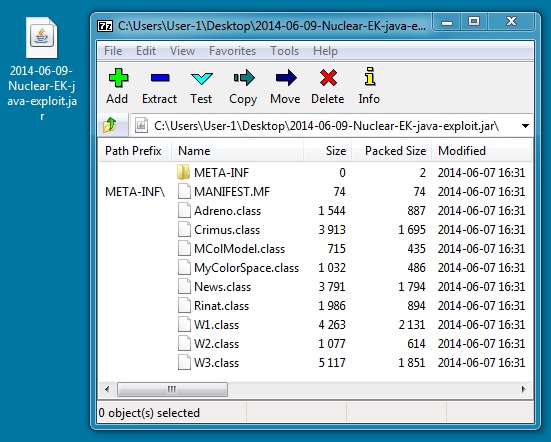
JAVA EXPLOIT
File name: 2014-06-09-Nuclear-EK-java-exploit.jar
File size: 12,167 bytes
MD5 hash: fcde039872d8596bc8304cbebb139b93
Detection ratio: 1 / 51
First submission: 2014-06-09 08:16:47 UTC
VirusTotal link: https://www.virustotal.com/en/file/d14526ffae471a7910f4c93ff327ca64a154b84f3cf061b8ce3b169de01b8236/analysis/
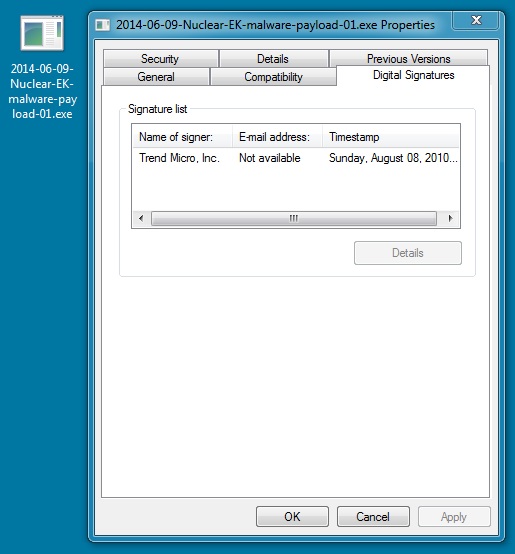
MALWARE PAYLOAD (1 OF 2)
File name: 2014-06-09-Nuclear-EK-malware-payload-01.exe
File size: 154,960 bytes
MD5 hash: 28af2419726b96e9f7a43212f481b371
Detection ratio: 5 / 52
First submission: 2014-06-09 15:11:58 UTC
VirusTotal link: https://www.virustotal.com/en/file/f02792d0cabb7a6a86486738330cddace48ac2b3ced21c86a11f4331a08b24f1/analysis/
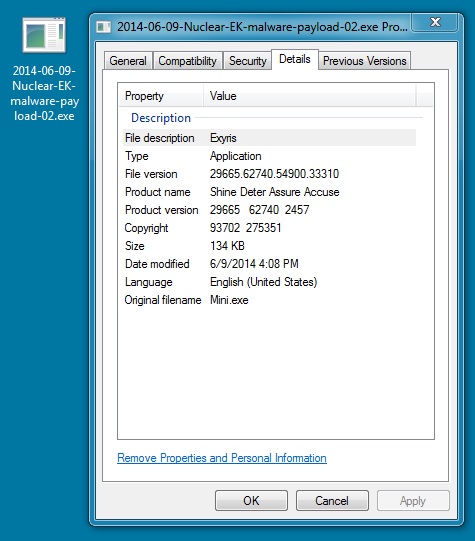
MALWARE PAYLOAD (2 OF 2)
File name: 2014-06-09-Nuclear-EK-malware-payload-02.exe
File size: 137,216 bytes
MD5 hash: 997c01baf8c7b664f214ce0d4dfaee97
Detection ratio: 4 / 52
First submission: 2014-06-09 15:12:09 UTC
VirusTotal link: https://www.virustotal.com/en/file/a567448233d252a53a4d546f1e33047f8cd3971d3f0aeac56086d04ef25a2ee7/analysis/
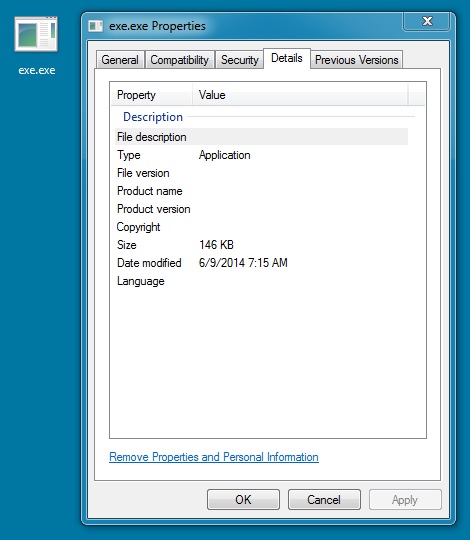
POST-INFECTION MALWARE
File name: exe.exe
Stored in the user's AppData\Local\Temp directory as: UpdateFlashPlayer_88fd1df4.exe
File size: 149,512 bytes
MD5 hash: e548e7e3a65dd40a781815de4e381f41
Detection ratio: 11 / 52
First submission: 2014-06-09 07:29:25 UTC
VirusTotal link: https://www.virustotal.com/en/file/88b092e3328babee786b01796fc80c1f893411892a88437a4592a13b660bd741/analysis/
ALERTS
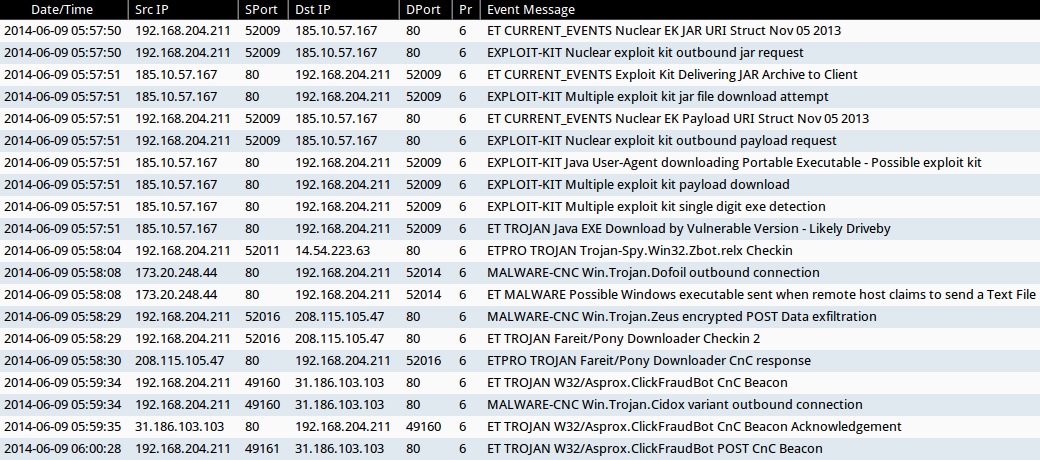
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion)
Emerging Threats and ETPRO rulesets:
- 2014-06-09 05:57:50 UTC - 185.10.57[.]167:80 - ET CURRENT_EVENTS Nuclear EK JAR URI Struct Nov 05 2013 (sid:2017666)
- 2014-06-09 05:57:51 UTC - 185.10.57[.]167:80 - ET CURRENT_EVENTS Exploit Kit Delivering JAR Archive to Client (sid:2014526)
- 2014-06-09 05:57:51 UTC - 185.10.57[.]167:80 - ET CURRENT_EVENTS Nuclear EK Payload URI Struct Nov 05 2013 (sid:2017667)
- 2014-06-09 05:57:51 UTC - 185.10.57[.]167:80 - 192.168.204.211:52009 - ET TROJAN Java EXE Download by Vulnerable Version - Likely Driveby (sid:2013036)
- 2014-06-09 05:58:04 UTC - 14.54.223[.]63:80 - ETPRO TROJAN Trojan-Spy.Win32.Zbot.relx Checkin (sid:2807742)
- 2014-06-09 05:58:08 UTC - 173.20.248[.]44:80 - ET MALWARE Possible Windows executable sent when remote host claims to send a Text File (sid:2008438)
- 2014-06-09 05:58:29 UTC - 208.115.105[.]47:80 - ET TROJAN Fareit/Pony Downloader Checkin 2 (sid:2014411)
- 2014-06-09 05:58:30 UTC - 208.115.105[.]47:80 - ETPRO TROJAN Fareit/Pony Downloader CnC response (sid:2805976)
- 2014-06-09 05:59:34 UTC - 31.186.103[.]103:80 - ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon (sid:2018096)
- 2014-06-09 05:59:35 UTC - 31.186.103[.]103:80 - ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon Acknowledgement (sid:2018097)
- 2014-06-09 06:00:28 UTC - 31.186.103[.]103:80 - ET TROJAN W32/Asprox.ClickFraudBot POST CnC Beacon (sid:2018098)
Sourcefire VRT ruleset:
- 2014-06-09 05:57:50 UTC - 185.10.57[.]167:80 - EXPLOIT-KIT Nuclear exploit kit outbound jar request (sid:30219)
- 2014-06-09 05:57:51 UTC - 185.10.57[.]167:80 - EXPLOIT-KIT Multiple exploit kit jar file download attempt (sid:27816)
- 2014-06-09 05:57:51 UTC - 185.10.57[.]167:80 - EXPLOIT-KIT Nuclear exploit kit outbound payload request (sid:30220)
- 2014-06-09 05:57:51 UTC - 185.10.57[.]167:80 - EXPLOIT-KIT Java User-Agent downloading Portable Executable - Possible exploit kit (sid:25042)
- 2014-06-09 05:57:51 UTC - 185.10.57[.]167:80 - EXPLOIT-KIT Multiple exploit kit payload download (sid:28593)
- 2014-06-09 05:57:51 UTC - 185.10.57[.]167:80 - EXPLOIT-KIT Multiple exploit kit single digit exe detection (sid:28423)
- 2014-06-09 05:58:08 UTC - 173.20.248[.]44:80 - MALWARE-CNC Win.Trojan.Dofoil outbound connection (sid:28809)
- 2014-06-09 05:58:29 UTC - 208.115.105[.]47:80 - MALWARE-CNC Win.Trojan.Zeus encrypted POST Data exfiltration (sid:27919)
- 2014-06-09 05:59:34 UTC - 31.186.103[.]103:80 - MALWARE-CNC Win.Trojan.Cidox variant outbound connection (sid:29356)
Click here to return to the main page.