2014-06-23 - KULUOZ INFECTION FROM EMAIL ATTACHMENT SENT BY ASPROX BOTNET
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
PHISHING EMAIL
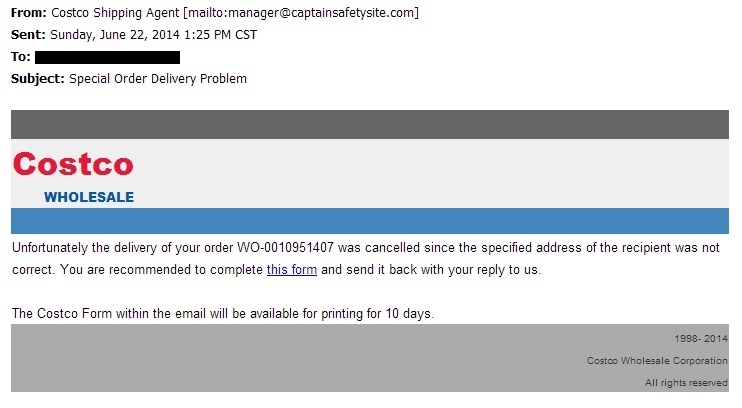
These fake Costco emails were reported as early as Dec 2013, and they're related to the Asprox botnet. Click here for a report written by Kimberly at StopMalvertising when this particular email from the Asprox botnet was noted last year.
Here's another fake Costco malicious email. Nothing really new here... I'm posting to show these emails are still being sent. We'll also see what alerts are triggering from the malware.
The link in the email for this form goes to byluhrs[.]net/handler/sys.php?cos=qOVVakHcZte3G5N5inWLznVNo3xVbsBOMSg36kazf50%3D
That link is no longer active. Fortunately, I got a copy of the malware before the link went inactive.
PRELIMINARY MALWARE ANALYSIS
DOWNLOADED FILE
File name: CostcoForm_US_San_Antonio.zip
File size: 55,412 bytes
MD5 hash: ed7a183590b5f2f850fb57d5dfda2402
Detection ratio: 2 / 54
First submission: 2014-06-23 01:47:24 UTC
VirusTotal link: https://www.virustotal.com/en/file/0e56c569ba8f9dc0703630d161d27aff13c7809a3ade3af73ed2be8157a4b643/analysis/
NOTE: The file name varies, based on the IP address you're coming from.
EXTRACTED MALWARE
File name: CostcoForm_US_San_Antonio.exe
File size: 77,824 bytes
MD5 hash: 002140df2bb9a73f1d71aac6b27880cd
Detection ratio: 2 / 54
First submission: 2014-06-23 01:48:03 UTC
VirusTotal link: https://www.virustotal.com/en/file/32d9fa23a728d3b2c0303f0d8f816368723b098ab80a6dce1c6f8e6cf2637922/analysis/
ALERTS
I executed the malware on a VM, and I also ran it through the Malwr sandbox. Both cases saw the same events. Here's what I got on the VM:
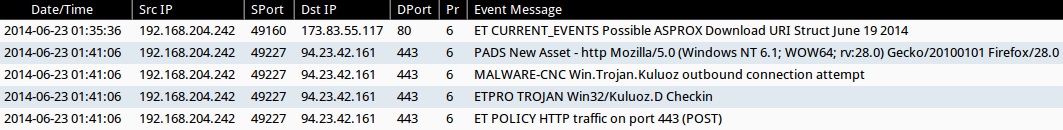
Here are the notable rules triggered from the Emerging Threats ETPRO and Sourcefire VRT rulesets:
- ET CURRENT_EVENTS Possible ASPROX Download URI Struct June 19 2014 (sid:2018589)
- ETPRO TROJAN Win32/Kuluoz.D Checkin (sid:2807771)
- MALWARE-CNC Win.Trojan.Kuluoz outbound connection attempt (sid:31244)
NOTE: These events were taken from Sguil on Security Onion
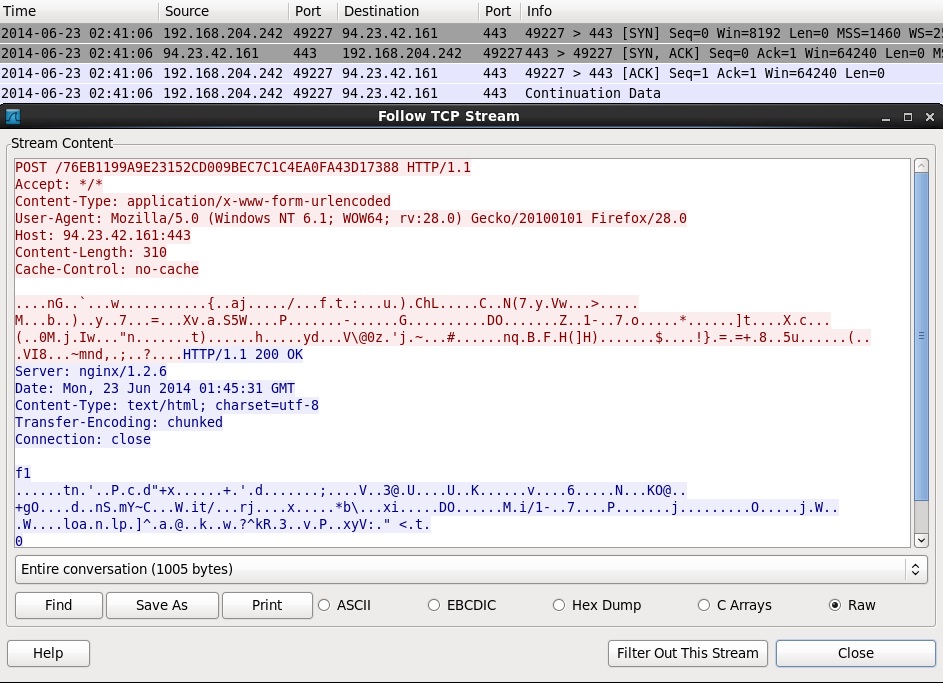
POST-INFECTION TRAFFIC
Saw the same Kuluoz callback traffic (unencrypted HTTP over port 443) on both the VM and the Malwr sandbox analysis.
The Kuluoz callback went to 94.23.42[.]161 on the VM, and it went to 92.240.237[.]66 on the Malwr sandbox analysis
Click here to return to the main page.