2014-06-24 - ANGLER EK FROM 149.3.138[.]235 - POSTINGDROMERINGSLAND[.]NET
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 149.3.138[.]235 - postingdromeringsland[.]net - Angler EK
- Post-infection DNS queries: ambi[.]cc , edal[.]cc , sted[.]cc , express-shippingus[.]net , modern-shipping[.]biz , useushippinginc[.]com
- Post-infection IP addresses for HTTPS traffic: 185.26.146[.]36 , 189.127.48[.]11 , 191.101.1[.]94 , 216.3.111[.]60
ANGLER EK:
- 15:41:29 UTC - 149.3.138[.]235:80 - postingdromeringsland[.]net - GET /xef382ebkd
- 15:41:33 UTC - 149.3.138[.]235:80 - postingdromeringsland[.]net - GET /xRaB3k9bXUhUguRJVLlk7ckyT7kZj2vZgZDWqkVTdfudozt_6XHVQbgvo-dh8FhZ
- 15:42:05 UTC - 149.3.138[.]235:80 - postingdromeringsland[.]net - GET /gLQM_hYaw47PwUQb-NYITnGR5LyDi1Ms-uSMeDL0ydsliTG5a8aH6eEXO85lCSTq
- 15:42:17 UTC - 149.3.138[.]235:80 - postingdromeringsland[.]net - GET /n7ChkU3oNKY8QozXpUiBRqpQZRkvlxHFOpIIbdHr6PtnJYn4yWP8BVO3bccGd6oP
- 15:42:49 UTC - 149.3.138[.]235:80 - postingdromeringsland[.]net - GET /w3pu3mRH39qW9mYbwjFgGVMT5uaLwJiosd6GeMpBBXzc-3KNUT3-Yj9APzOnUpWM
- 15:42:53 UTC - 149.3.138[.]235:80 - postingdromeringsland[.]net - GET /_B106reyzUGXT54rRHqwL2bGIxhebtRQ3ZUUcyUg7qzDo-SHR7-WaurNThz8rp_y
POST-INFECTION TRAFFIC:
- 15:42:04 UTC - Standard query - ambi[.]cc
- 15:42:04 UTC - Standard query response - 191.101.1[.]94 A 216.3.111[.]60 A 189.127.48[.]11 A 185.26.146[.]36 A 176.122.227.28
- 15:42:04 UTC - 191.101.1[.]94 port 443
- 15:42:19 UTC - 185.26.146[.]36 port 443
- 15:42:22 UTC - Standard query - express-shippingus[.]net
- 15:42:22 UTC - Standard query response - 185.26.146[.]36 A 189.127.48[.]11 A 176.122.227.28 A 191.101.1[.]94 A 216.3.111[.]60
- 15:42:23 UTC - 185.26.146[.]36 port 443
- 15:42:24 UTC - Standard query - useushippinginc[.]com
- 15:42:24 UTC - Standard query response - 191.101.1[.]94 A 189.127.48[.]11 A 185.26.146[.]36 A 216.3.111[.]60
- 15:42:24 UTC - 191.101.1[.]94 port 443
- 15:42:25 UTC - 185.26.146[.]36 port 443
- 15:42:25 UTC - Standard query - modern-shipping[.]biz
- 15:42:25 UTC - Standard query response - 185.26.146[.]36 A 191.101.1[.]94 A 216.3.111[.]60 A 189.127.48[.]11
- 15:42:26 UTC - 185.26.146[.]36 port 443
- 15:42:26 UTC - 216.3.111[.]60 port 443
- 15:42:27 UTC - Standard query - sted[.]cc
- 15:42:27 UTC - Standard query response - 191.101.1[.]94 A 189.127.48[.]11 A 185.26.146[.]36 A 216.3.111[.]60
- 15:42:27 UTC - 191.101.1[.]94 port 443
- 15:42:28 UTC - 189.127.48[.]11 port 443
- 15:42:28 UTC - Standard query - edal[.]cc
- 15:42:28 UTC - Standard query response - 216.3.111[.]60 A 185.26.146[.]36 A 189.127.48[.]11 A 191.101.1[.]94
- 15:42:28 UTC - 189.127.48[.]11 port 443
- 15:42:28 UTC - 216.3.111[.]60 port 443
NOTES: These post-infection DNS queries generated by the malware used Google DNS at 8.8.8[.]8. The queries were repeated several times.
PRELIMINARY MALWARE ANALYSIS
JAVA EXPLOIT
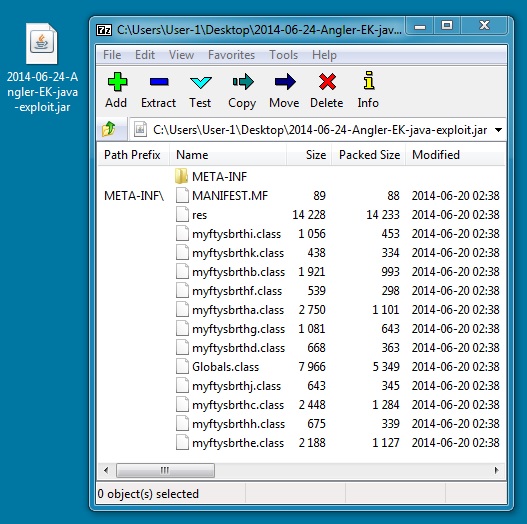
File name: 2014-06-24-Angler-EK-java-exploit.jar
File size: 28,721 bytes
MD5 hash: d9905f9daf40cc3ea7c0f4cf69eeb716
Detection ratio: 17 / 54
First submission: 2014-06-20 12:38:57 UTC
VirusTotal link: https://www.virustotal.com/en/file/959d3ff72d416c2130cfa38e036909c7eb3154f3fcd57bce9b9f1e0522999c07/analysis/
SILVERLIGHT EXPLOIT
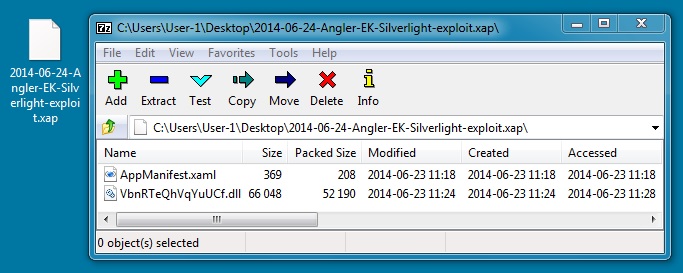
File name: 2014-06-24-Angler-EK-Silverlight-exploit.xap
File size: 52,714 bytes
MD5 hash: e562283bcb93f4ef9aaf89fa481d7ab5
Detection ratio: 0 / 54
First submission: 2014-06-24 16:40:29 UTC
VirusTotal link: https://www.virustotal.com/en/file/3d0a3ebd6e587ac15f2ccaff31b27dd51a660ca4327bcb4a026d2c7397aa20c5/analysis/
MALWARE PAYLOAD
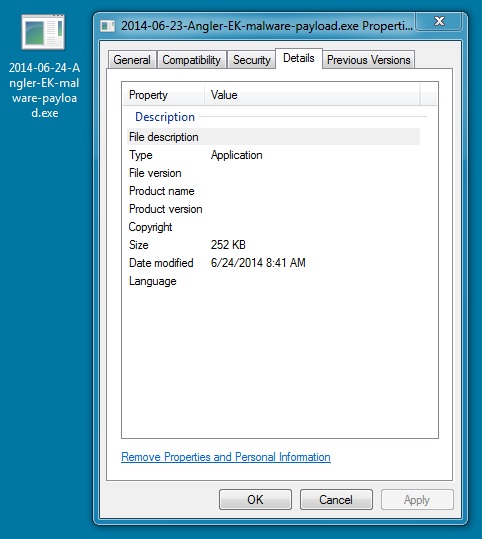
File name: 2014-06-24-Angler-EK-malware-payload.exe
File size: 258,048 bytes
MD5 hash: 0421d581a8be33099b5b140bbd2d97f0
Detection ratio: 6 / 54
First submission: 2014-06-24 13:57:07 UTC
VirusTotal link: https://www.virustotal.com/en/file/a66f4c3292ec70868548891a5933c36f076fbaac6329c4fce54bbdb572e3f511/analysis/
ALERTS
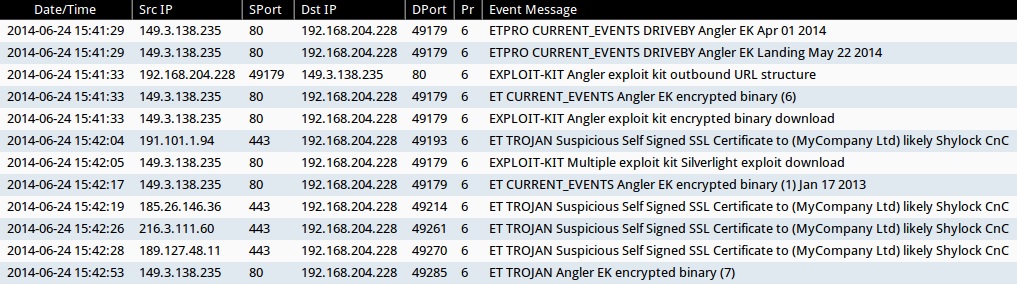
Emerging Threats and ETPRO rulesets:
- 149.3.138[.]235:80 - ETPRO CURRENT_EVENTS DRIVEBY Angler EK Apr 01 2014 (sid:2807913)
- 149.3.138[.]235:80 - ETPRO CURRENT_EVENTS DRIVEBY Angler EK Landing May 22 2014 (sid:2808076)
- 149.3.138[.]235:80 - ET CURRENT_EVENTS Angler EK encrypted binary (6) (sid:2018510)
- 191.101.1[.]94:443 - ET TROJAN Suspicious Self Signed SSL Certificate to (MyCompany Ltd) likely Shylock CnC (sid:2015560)
- 149.3.138[.]235:80 - ET CURRENT_EVENTS Angler EK encrypted binary (1) Jan 17 2013 (sid:2017984)
- 185.26.146[.]36:443 - ET TROJAN Suspicious Self Signed SSL Certificate to (MyCompany Ltd) likely Shylock CnC (sid:2015560)
- 216.3.111[.]60:443 - ET TROJAN Suspicious Self Signed SSL Certificate to (MyCompany Ltd) likely Shylock CnC (sid:2015560)
- 189.127.48[.]11:443 - ET TROJAN Suspicious Self Signed SSL Certificate to (MyCompany Ltd) likely Shylock CnC (sid:2015560)
- 149.3.138[.]235:80 - ET TROJAN Angler EK encrypted binary (7) (sid:2018511)
Sourcefire VRT ruleset:
- 149.3.138[.]235:80 - EXPLOIT-KIT Angler exploit kit outbound URL structure (sid:31332)
- 149.3.138[.]235:80 - EXPLOIT-KIT Angler exploit kit encrypted binary download (sid:31331)
- 149.3.138[.]235:80 - EXPLOIT-KIT Multiple exploit kit Silverlight exploit download (sid:28612)
NOTE: These alerts were taken from Sguil on Security Onion.
Click here to return to the main page.