2014-07-02 - MALWARE INFECTION FROM LINK IN ASPROX BOTNET EMAIL
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
This blog post compares 2 recent USPS-themed emails from the Asprox botnet. Note the differences between the emails. Changes in the message content complicate efforts to block these malicious messages. For more information on these recent Asprox emails, see the following links:
- https://threatpost.com/usps-spam-campaign-drops-botnet-malware/106393/
- https://www.zscaler.com/blogs/security-research/usps-spam-delivering-asprox-variant
- https://stopmalvertising.com/malware-reports/a-journey-inside-the-asprox-modules.html
SCREENSHOTS OF THE EMAILS
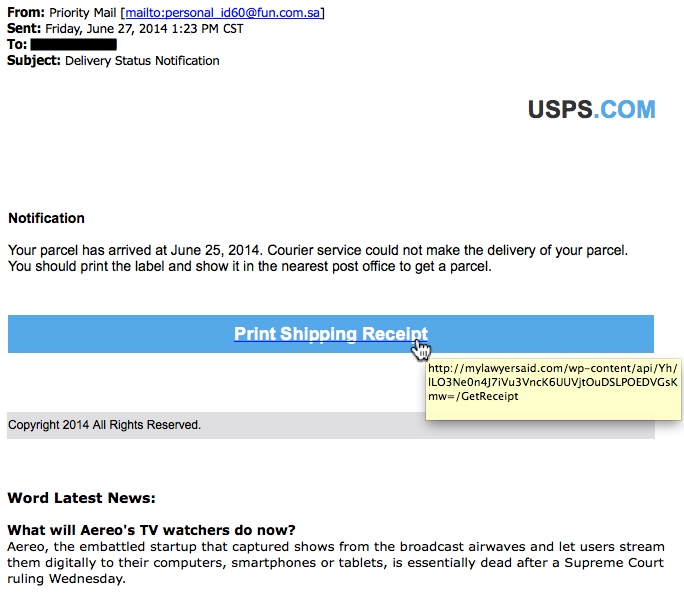
FROM FRIDAY, 2014-06-27:
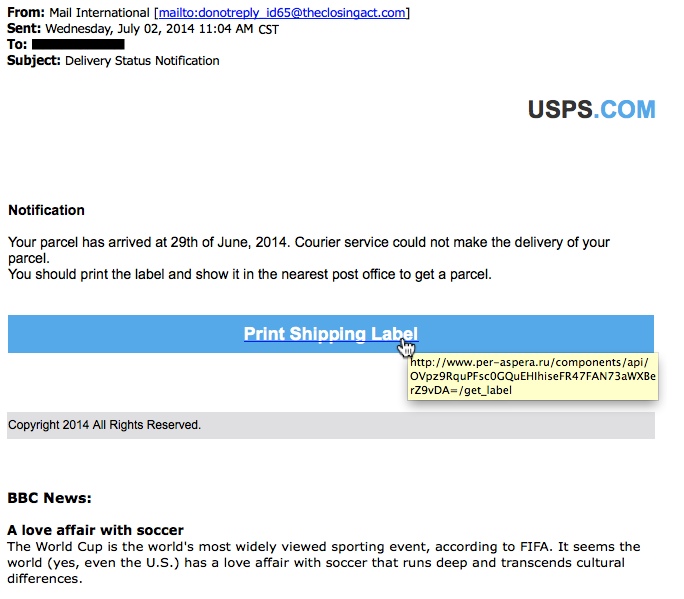
FROM WEDNESDAY, 2014-07-02:
HTTP GET REQUESTS FOR THE MALWARE:
- 2014-06-27 email: mylawyersaid[.]com - GET /wp-content/api/Yh/ILO3Ne0n4J7iVu3VncK6UUVjtOuDSLPOEDVGsKmw=/GetReceipt
- 2014-07-02 email: www.per-aspera[.]ru - GET /components/api/OVpz9RquPFsc0GQuEHIhiseFR47FAN73aWXBerZ9vDA=/get_label
PRELIMINARY MALWARE ANALYSIS
2014-06-27 MALWARE (ZIP FILE)
File name: USPS_Receipt_US_city_name_2014-06-27.zip
File size: 101,141 bytes
MD5 hash: a5eaedb7ad1a651379855477f4164651
Detection ratio: 21 / 54
First submission: 2014-07-02 20:21:09 UTC
VirusTotal link: https://www.virustotal.com/en/file/38e17f76e97ac21b728ebe6d5c5d074df6b7c62ea71c0bc7b723273da5515cf7/analysis/
2014-06-27 MALWARE (EXTRACTED EXE)
File name: USPS_Receipt_US_city_name_2014-06-27.exe
File size: 153,088 bytes
MD5 hash: b1ffe5b1dcf6125bdfd2e713a7c2bdb4
Detection ratio: 20 / 53
First submission: 2014-07-02 20:21:30 UTC
VirusTotal link: https://www.virustotal.com/en/file/4ec0dc7e0fc1806bfd777caa2762d7f6f89d7e9db794c07dad2caea63d3a14ba/analysis/
2014-07-02 MALWARE (ZIP FILE)
File name: Label_US_city_name_2014-07-02.zip
File size: 91,355 bytes
MD5 hash: c62571abb2579a08815a7fe9f444e726
Detection ratio: 4 / 53
First submission: 2014-07-02 20:18:38 UTC
VirusTotal link: https://www.virustotal.com/en/file/9a39c1ed1e3309fd9f530bc72f4ac84e022a926c9ba6df4266b73cc489d2e065/analysis/
2014-07-02 MALWARE (EXTRACTED EXE)
File name: Label_US_city_name_2014-07-02.exe
File size: 131,584 bytes
MD5 hash: 1e0c7da431950be356ee52985d7a4d8b
Detection ratio: 5 / 54
First submission: 2014-07-02 16:22:57 UTC
VirusTotal link: https://www.virustotal.com/en/file/b7ee27546d19721bdf927c11e217b556264c39584749f79dbfb774290793ff35/analysis/
SANDBOX TRAFFIC AND ALERTS
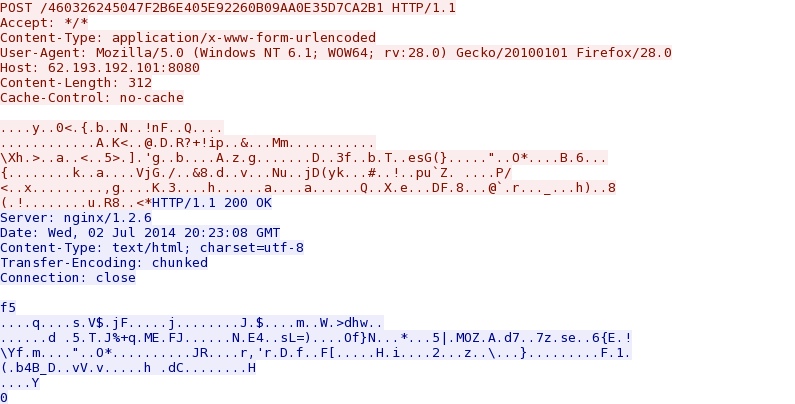
Traffic noted from the Malwr sandbox analysis of the 2014-06-27 malware:
- 2014-07-02 20:23:16 UTC - 62.193.192[.]101:8080 - 62.193.192[.]101:8080 - POST /460326245047F2B6E405E92260B09AA0E35D7CA2B1
Events from the pcap:
- 2014-07-02 20:23:16 UTC - 62.193.192[.]101:8080 - [1:31244:1] MALWARE-CNC Win.Trojan.Kuluoz outbound connection attempt
- 2014-07-02 20:23:16 UTC - 62.193.192[.]101:8080 - [1:2807771:1] ETPRO TROJAN Win32/Kuluoz.D Checkin
- 2014-07-02 20:23:16 UTC - 62.193.192[.]101:8080 - [1:2017895:5] ET CURRENT_EVENTS Kuluoz/Asprox Activity Dec 23 2013
- 2014-07-02 20:23:16 UTC - 62.193.192[.]101:8080 - [1:2018359:1] ET INFO GENERIC SUSPICIOUS POST to Dotted Quad with Fake Browser 2
Traffic noted from the Malwr sandbox analysis of the 2014-07-02 malware:
- 2014-07-02 20:21:00 UTC - 142.4.60[.]242:443 - 142.4.60[.]242:443 - POST /460326245047F2B6E405E92260B09AA0E35D7CA2B1
Events from the pcap:
- 2014-07-02 20:21:00 UTC - 142.4.60[.]242:443 - [1:31244:1] MALWARE-CNC Win.Trojan.Kuluoz outbound connection attempt
- 2014-07-02 20:21:00 UTC - 142.4.60[.]242:443 - [1:2807771:1] ETPRO TROJAN Win32/Kuluoz.D Checkin
- 2014-07-02 20:21:00 UTC - 142.4.60[.]242:443 - [1:2013926:2] ET POLICY HTTP traffic on port 443 (POST)
- 2014-07-02 20:21:00 UTC - 142.4.60[.]242:443 - [1:2006409:8] ET POLICY HTTP POST on unusual Port Possibly Hostile
Click here to return to the main page.