2014-07-15 - MAGNITUDE EK FROM 5.133.179[.]166 - 241020.2DBA.6D01312.011.A85.6B4.D4.DF92.CFTBMXJLI.FOLKSBUILT[.]IN
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- In this traffic, Magnitude EK appears to have used IE exploit CVE-2013-2551 to infect the vulnerable VM.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 194.254.173[.]148 - windywing.pristineprinting[.]com - Redirect
- 5.133.179[.]166 - 241020.2dba.6d01312.011.a85.6b4.d4.df92.cftbmxjli.folksbuilt[.]in - Magnitude EK
- Various IP addresses - various domains - Post-infection traffic (see below)
REDIRECT:
- 21:10:57 UTC - 194.254.173[.]148:80 - windywing.pristineprinting[.]com - GET /themes/index.php?id=aHR0cDovLzI0MTAyMC4yZGJhLjZkMDEzM
TIuMDExLmE4NS42YjQuZDQuZGY5Mi5jZnRibXhqbGkuZm9sa3NidWlsdC5pbi8=
MAGNITUDE EK:
- 21:10:58 UTC - 5.133.179[.]166:80 - 241020.2dba.6d01312.011.a85.6b4.d4.df92.cftbmxjli.folksbuilt[.]in - GET /
- 21:10:59 UTC - 5.133.179[.]166:80 - 241020.2dba.6d01312.011.a85.6b4.d4.df92.cftbmxjli.folksbuilt[.]in - GET /6382873ee967eb1591c1266c79e8
42e4/5490059a4a13c0261bb96821a1e47145 - 21:11:08 UTC - 5.133.179[.]166:80 - 5.133.179[.]166 - GET /?616b58cf0d17720490b9f8b46312e5b3
- 21:11:25 UTC - 5.133.179[.]166:80 - 5.133.179[.]166 - GET /?090310239f82e2574fe7d9bd3bb31edd
- 21:11:26 UTC - 5.133.179[.]166:80 - 5.133.179[.]166 - GET /?2cfc5da72d98dcf9a701bd9c0d4c210b
- 21:11:27 UTC - 5.133.179[.]166:80 - 5.133.179[.]166 - GET /?c0a8097b350a96460f4894922666dd8d
- 21:11:31 UTC - 5.133.179[.]166:80 - 5.133.179[.]166 - GET /?8b009d50276692d6c61359e036ebc12a
- 21:11:34 UTC - 5.133.179[.]166:80 - 5.133.179[.]166 - GET /?6d3f2fa09704c11a2de462a676565173
- 21:12:33 UTC - 5.133.179[.]166:80 - c3a45.ce7.a6da2f.4b2357.6da628.e2.43ed.sbyvqeajn.folksbuilt[.]in - GET /?30425556585f44525f441e535f5d
- 21:12:39 UTC - 5.133.179[.]166:80 - c3a45.ce7.a6da2f.4b2357.6da628.e2.43ed.sbyvqeajn.folksbuilt[.]in - GET /c5d67277c6b1f35a9fbfcd32a5351
8ca/94b9a6c04950fcf107b67a8f4b6d3432
POST-INFECTION TRAFFIC:
- 21:11:32 UTC - 178.141.97[.]185:80 - come-passere.com - GET /b/shoe/749634
- 21:11:37 UTC - 93.127.86[.]19:80 - la-spazzolino[.]com - GET /mod_articles-php357.446/jquery/
- 21:11:53 UTC - 93.127.86[.]19:80 - la-spazzolino[.]com - GET /mod_articles-php357.446/jquery/
- 21:14:26 UTC - 176.213.137[.]214:80 - la-spazzolino[.]com - GET /mod_articles-php357.446/jquery/
- 21:14:27 UTC - 178.141.97[.]185:80 - la-spazzolino[.]com - GET /mod_articles-php357.446/jquery/
- 21:14:36 UTC - 176.213.137[.]214:80 - la-spazzolino[.]com - GET /mod_articles-php357.446/ajax/
- 21:16:07 UTC - 95.46.199[.]63:80 - la-spazzolino[.]com - GET /mod_jshopping-java984.561/soft64.dll
- 21:16:12 UTC - 46.219.29[.]102:80 - vision-vaper[.]su - GET /b/eve/7e2ad40fb13829982428cfe3
- 21:12:04 UTC - 8.8.4[.]4:53 - DNS query for nsa.figaina5[.]net
- 21:12:05 UTC - 8.8.8[.]8:53 - DNS query for nsa.figaina5[.]net
- 21:12:06 UTC - 8.8.4[.]4:53 - DNS query for nsa.figaina5[.]net
- 21:12:07 UTC - 8.8.4[.]4:53 - DNS response for nsa.figaina5[.]net as 125.83.138.92
- 21:12:07 UTC - 8.8.8[.]8:53 - DNS response for nsa.figaina5[.]net as 125.83.138.92
- 21:12:07 UTC - 8.8.4[.]4:53 - DNS response for nsa.figaina5[.]net as 125.83.138.92
- 21:12:07 UTC - 85.17.139[.]17:53 - TCP traffic over port 53
- 21:14:58 UTC - 85.17.139[.]17:53 - TCP traffic over port 53
PRELIMINARY MALWARE ANALYSIS
MALWARE PAYLOAD 1 OF 4:
File name: 2014-07-15-Magnitude-EK-malware-payload-1-of-4.exe
File size: 297,492 bytes
MD5 hash: 0e7fcd6595c444f6a829d4763516741f
Detection ratio: 7 / 53
First submission: 2014-07-15 23:33:45 UTC
VirusTotal link: https://www.virustotal.com/en/file/28afa062eb5466531d804fdeb249c28cf7992f983c90fb6b9b60d6171a53648b/analysis/
MALWARE PAYLOAD 2 OF 4:
File name: 2014-07-15-Magnitude-EK-malware-payload-2-of-4.exe
File size: 94,216 bytes
MD5 hash: 8beb666c0c45f74875a3f5882ec957cd
Detection ratio: 4 / 54
First submission: 2014-07-15 23:35:49 UTC
VirusTotal link: https://www.virustotal.com/en/file/cdec45ec8e20bcb710b7971a0e95a8c9fffbb1775fe7e3e9a3e4d847d2c5d08f/analysis/
MALWARE PAYLOAD 3 OF 4:
File name: 2014-07-15-Magnitude-EK-malware-payload-3-of-4.exe
File size: 110,592 bytes
MD5 hash: 33aedc85d46d28321bded7ea27c01f62
Detection ratio: 3 / 54
First submission: 2014-07-15 23:36:51 UTC
VirusTotal link: https://www.virustotal.com/en/file/9d680a28111322cc35e170335c088c826e3dd13f2883f5c57f233dc00303d1f0/analysis/
MALWARE PAYLOAD 4 OF 4:
File name: 2014-07-15-Magnitude-EK-malware-payload-4-of-4.exe
File size: 430,080 bytes
MD5 hash: 95e0f12750a0629fd00551def17207ed
Detection ratio: 5 / 54
First submission: 2014-07-15 23:38:09 UTC
VirusTotal link: https://www.virustotal.com/en/file/3e99add247b060c795512783803c6698b5490bef7c883d7e39ab0223152ae253/analysis/
FOLLOW-UP MALWARE:
File name: UpdateFlashPlayer_dca93f91.exe
File size: 172,032 bytes
MD5 hash: e57ea8653156a1b16414c57378546418
Detection ratio: 4 / 54
First submission: 2014-07-16 01:00:07 UTC
VirusTotal link: https://www.virustotal.com/en/file/666bd304a5c637c74a30a13d466ee7df7142cc70bd3eeca80a66abd9858b1a14/analysis/
ALERTS
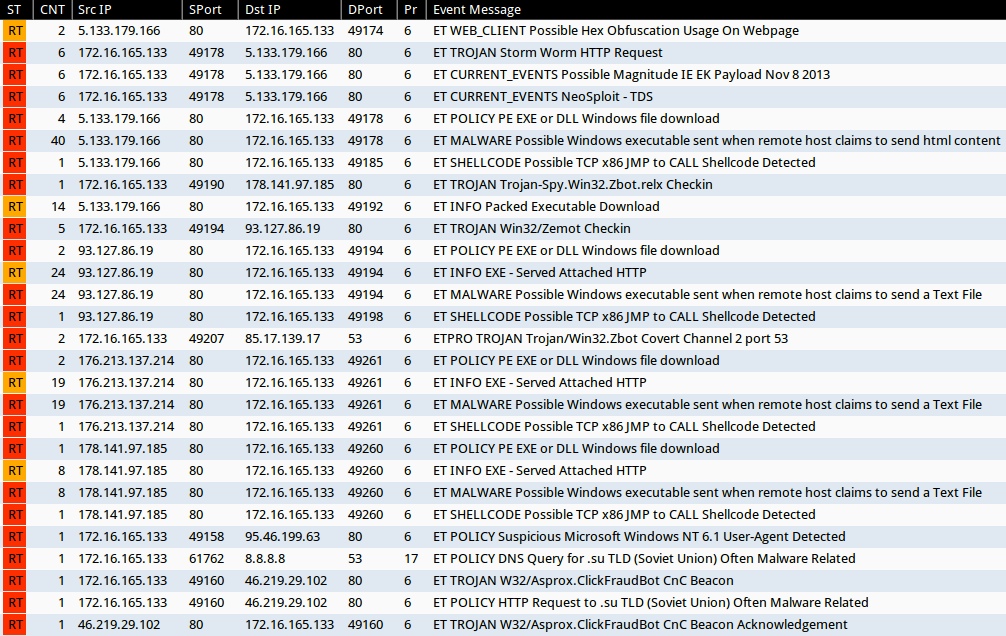
Emerging Threats and ETPRO rulesets from Sguil on Security Onion:
- 2 count - 5.133.179[.]166:80 - ET WEB_CLIENT Possible Hex Obfuscation Usage On Webpage (sid:2012119)
- 6 count - 5.133.179[.]166:80 - ET TROJAN Storm Worm HTTP Request (sid:2006411)
- 6 count - 5.133.179[.]166:80 - ET CURRENT_EVENTS Possible Magnitude IE EK Payload Nov 8 2013 (sid:2017694)
- 6 count - 5.133.179[.]166:80 - ET CURRENT_EVENTS NeoSploit - TDS (sid:2015665)
- 4 count - 5.133.179[.]166:80 - ET POLICY PE EXE or DLL Windows file download (sid:2000419)
- 40 count - 5.133.179[.]166:80 - ET MALWARE Possible Windows executable sent when remote host claims to send html content (sid:2009897)
- 1 count - 5.133.179[.]166:80 - ET SHELLCODE Possible TCP x86 JMP to CALL Shellcode Detected (sid:2011803)
- 1 count - 178.141.97[.]185:80 - ET TROJAN Trojan-Spy.Win32.Zbot.relx Checkin (sid:2018643)
- 14 count - 5.133.179[.]166:80 - ET INFO Packed Executable Download (sid:2014819)
- 5 count - 93.127.86[.]19:80 - ET TROJAN Win32/Zemot Checkin (sid:2018644)
- 2 count - 93.127.86[.]19:80 - ET POLICY PE EXE or DLL Windows file download (sid:2000419)
- 24 count - 93.127.86[.]19:80 - ET INFO EXE - Served Attached HTTP (sid:2014520)
- 24 count - 93.127.86[.]19:80 - ET MALWARE Possible Windows executable sent when remote host claims to send a Text File (sid:2008438)
- 1 count - 93.127.86[.]19:80 - ET SHELLCODE Possible TCP x86 JMP to CALL Shellcode Detected (sid:2011803)
- 2 count - 85.17.139[.]17:53 - ETPRO TROJAN Trojan/Win32.Zbot Covert Channel 2 port 53 (sid:2807561)
- 2 count - 176.213.137[.]214:80 - ET POLICY PE EXE or DLL Windows file download (sid:2000419)
- 19 count - 176.213.137[.]214:80 - ET INFO EXE - Served Attached HTTP (sid:2014520)
- 19 count - 176.213.137[.]214:80 - ET MALWARE Possible Windows executable sent when remote host claims to send a Text File (sid:2008438)
- 1 count - 176.213.137[.]214:80 - ET SHELLCODE Possible TCP x86 JMP to CALL Shellcode Detected (sid:2011803)
- 1 count - 178.141.97[.]185:80 - ET POLICY PE EXE or DLL Windows file download (sid:2000419)
- 8 count - 178.141.97[.]185:80 - ET INFO EXE - Served Attached HTTP (sid:2014520)
- 8 count - 178.141.97[.]185:80 - ET MALWARE Possible Windows executable sent when remote host claims to send a Text File (sid:2008438)
- 1 count - 178.141.97[.]185:80 - ET SHELLCODE Possible TCP x86 JMP to CALL Shellcode Detected (sid:2011803)
- 1 count - 95.46.199[.]63:80 - ET POLICY Suspicious Microsoft Windows NT 6.1 User-Agent Detected (sid:2010228)
- 1 count - 8.8.8[.]8:53 - ET POLICY DNS Query for .su TLD (Soviet Union) Often Malware Related (sid:2014169)
- 1 count - 46.219.29[.]102:80 - ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon (sid:2018096)
- 1 count - 46.219.29[.]102:80 - ET POLICY HTTP Request to .su TLD (Soviet Union) Often Malware Related (sid:2014170)
- 1 count - 46.219.29[.]102:80 - ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon Acknowledgement (sid:2018097)
Sourcefire VRT ruleset from Snort 2.9.6.0 on Ubuntu 14.04 LTS:
- 2014-07-15 21:10:58 UTC - 8.8.8[.]8:53 - [1:254:15] PROTOCOL-DNS SPOOF query response with TTL of 1 min. and no authority
- 2014-07-15 21:10:58 UTC - 5.133.179[.]166:80 - [1:26653:4] EXPLOIT-KIT Multiple exploit kit landing page - specific structure
- 2014-07-15 21:10:58 UTC - 5.133.179[.]166:80 - [1:30766:1] EXPLOIT-KIT Magnitude exploit kit landing page
- 2014-07-15 21:11:08 UTC - 5.133.179[.]166:80 - [1:29189:1] EXPLOIT-KIT Magnitude exploit kit Microsoft Internet Explorer Payload request
- 2014-07-15 21:11:08 UTC - 5.133.179[.]166:80 - [1:17276:15] FILE-OTHER Multiple vendor Antivirus magic byte detection evasion attempt
- 2014-07-15 21:11:08 UTC - 5.133.179[.]166:80 - [1:28593:1] EXPLOIT-KIT Multiple exploit kit payload download
- 2014-07-15 21:11:08 UTC - 5.133.179[.]166:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- 2014-07-15 21:11:25 UTC - 5.133.179[.]166:80 - [1:29189:1] EXPLOIT-KIT Magnitude exploit kit Microsoft Internet Explorer Payload request
- 2014-07-15 21:11:26 UTC - 5.133.179[.]166:80 - [1:29189:1] EXPLOIT-KIT Magnitude exploit kit Microsoft Internet Explorer Payload request
- 2014-07-15 21:11:27 UTC - 5.133.179[.]166:80 - [1:29189:1] EXPLOIT-KIT Magnitude exploit kit Microsoft Internet Explorer Payload request
- 2014-07-15 21:11:27 UTC - 5.133.179[.]166:80 - [1:17276:15] FILE-OTHER Multiple vendor Antivirus magic byte detection evasion attempt
- 2014-07-15 21:11:27 UTC - 5.133.179[.]166:80 - [1:28593:1] EXPLOIT-KIT Multiple exploit kit payload download
- 2014-07-15 21:11:27 UTC - 5.133.179[.]166:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- 2014-07-15 21:11:28 UTC - 5.133.179[.]166:80 - [1:23256:5] FILE-EXECUTABLE Armadillo v1.71 packer file magic detected
- 2014-07-15 21:11:31 UTC - 5.133.179[.]166:80 - [1:29189:1] EXPLOIT-KIT Magnitude exploit kit Microsoft Internet Explorer Payload request
- 2014-07-15 21:11:32 UTC - 5.133.179[.]166:80 - [1:17276:15] FILE-OTHER Multiple vendor Antivirus magic byte detection evasion attempt
- 2014-07-15 21:11:32 UTC - 5.133.179[.]166:80 - [1:28593:1] EXPLOIT-KIT Multiple exploit kit payload download
- 2014-07-15 21:11:32 UTC - 5.133.179[.]166:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- 2014-07-15 21:11:32 UTC - 5.133.179[.]166:80 - [1:23256:5] FILE-EXECUTABLE Armadillo v1.71 packer file magic detected
- 2014-07-15 21:11:34 UTC - 5.133.179[.]166:80 - [1:29189:1] EXPLOIT-KIT Magnitude exploit kit Microsoft Internet Explorer Payload request
- 2014-07-15 21:11:35 UTC - 5.133.179[.]166:80 - [1:17276:15] FILE-OTHER Multiple vendor Antivirus magic byte detection evasion attempt
- 2014-07-15 21:11:35 UTC - 5.133.179[.]166:80 - [1:28593:1] EXPLOIT-KIT Multiple exploit kit payload download
- 2014-07-15 21:11:35 UTC - 5.133.179[.]166:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- 2014-07-15 21:11:36 UTC - 8.8.4[.]4:53 - [1:254:15] PROTOCOL-DNS SPOOF query response with TTL of 1 min. and no authority
- 2014-07-15 21:11:37 UTC - 93.127.86[.]19:80 - [1:28809:3] MALWARE-CNC Win.Trojan.Dofoil outbound connection
- 2014-07-15 21:11:37 UTC - 93.127.86[.]19:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- 2014-07-15 21:11:38 UTC - 93.127.86[.]19:80 - [1:23256:5] FILE-EXECUTABLE Armadillo v1.71 packer file magic detected
- 2014-07-15 21:11:53 UTC - 93.127.86[.]19:80 - [1:28809:3] MALWARE-CNC Win.Trojan.Dofoil outbound connection
- 2014-07-15 21:11:53 UTC - 93.127.86[.]19:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- 2014-07-15 21:11:54 UTC - 93.127.86[.]19:80 - [1:23256:5] FILE-EXECUTABLE Armadillo v1.71 packer file magic detected
- 2014-07-15 21:12:07 UTC - 85.17.139[.]17:53 - [1:28996:4] MALWARE-CNC Win.Trojan.Bunitu variant outbound connection
- 2014-07-15 21:12:33 UTC - 8.8.4[.]4:53 - [1:254:15] PROTOCOL-DNS SPOOF query response with TTL of 1 min. and no authority
- 2014-07-15 21:12:35 UTC - 5.133.179[.]166:80 - [1:26653:4] EXPLOIT-KIT Multiple exploit kit landing page - specific structure
- 2014-07-15 21:12:35 UTC - 5.133.179[.]166:80 - [1:30766:1] EXPLOIT-KIT Magnitude exploit kit landing page
- 2014-07-15 21:14:26 UTC - 176.213.137[.]214:80 - [1:28809:3] MALWARE-CNC Win.Trojan.Dofoil outbound connection
- 2014-07-15 21:14:26 UTC - 176.213.137[.]214:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- 2014-07-15 21:14:27 UTC - 176.213.137[.]214:80 - [1:23256:5] FILE-EXECUTABLE Armadillo v1.71 packer file magic detected
- 2014-07-15 21:14:27 UTC - 178.141.97[.]185:80 - [1:28809:3] MALWARE-CNC Win.Trojan.Dofoil outbound connection
- 2014-07-15 21:14:27 UTC - 178.141.97[.]185:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- 2014-07-15 21:14:28 UTC - 178.141.97[.]185:80 - [1:23256:5] FILE-EXECUTABLE Armadillo v1.71 packer file magic detected
- 2014-07-15 21:14:44 UTC - 176.213.137[.]214:80 - [1:28809:3] MALWARE-CNC Win.Trojan.Dofoil outbound connection
- 2014-07-15 21:14:44 UTC - 176.213.137[.]214:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- 2014-07-15 21:14:58 UTC - 85.17.139[.]17:53 - [1:28996:4] MALWARE-CNC Win.Trojan.Bunitu variant outbound connection
- 2014-07-15 21:16:11 UTC - 8.8.8[.]8:53 - [1:27721:3] INDICATOR-COMPROMISE Suspicious .su dns query
- 2014-07-15 21:16:12 UTC - 46.219.29[.]102:80 - [1:29356:1] MALWARE-CNC Win.Trojan.Cidox variant outbound connection
FINAL NOTES
Click here to return to the main page.
