2014-07-16 - ZBOT INFECTION FROM EMAIL ATTACHMENT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
TODAY'S EMAIL
Saw the following email today:
MESSAGE TEXT:
From: Un Saldo <hooversconglomerate@outlook[.]com>
Reply-To: <hooversconglomerate@outlook[.]com>
Date: Wednesday, July 16, 2014 at 22:13 UTC
To: <hooversconglomerate@outlook[.]com>
Subject: Hoovers Order (Urgent!)
--
Hello
Please send us a PI for the following models as attached Purchase Order
Also inform us how many pcs for a full 5*40ft containers so we can add
more as customers request.
We have been trying to contact your colleague who has been corresponding
with our company about the confirmation but no
response.
Kindly check and advise asap
I await for your response.
Best Regards,
Un Saldo
Hoovers Ltd
hooversconglomerate@outlook[.]com
+34 945 891 234
PRELIMINARY MALWARE ANALYSIS
FILE ATTACHMENT
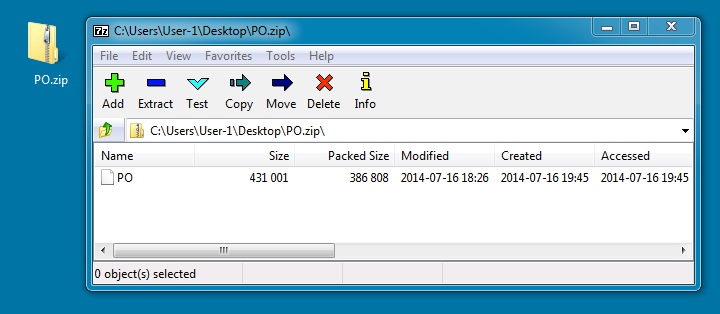
File name: PO.zip
File size: 386,946 bytes
MD5 hash: 5b324144630ee60d4c7e6999bc7f915e
Detection ratio: 2 / 54
First submission: 2014-07-16 23:03:23 UTC
VirusTotal link: https://www.virustotal.com/en/file/31fa3b4f7eef1df37003199d3e9b080b8e4fb2a1d20ce261fafd59cb88d95079/analysis/
EXTRACTED MALWARE:
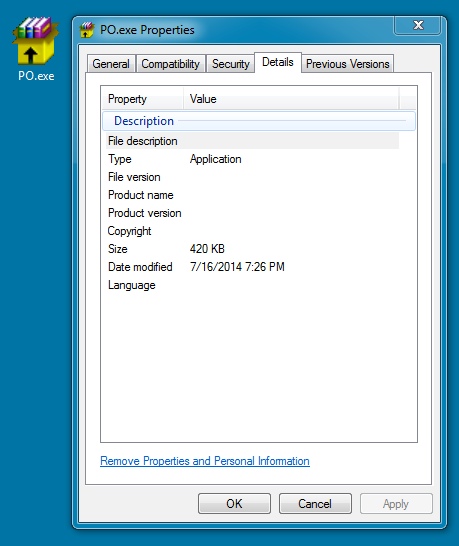
File name: PO
File size: 431,001 bytes
MD5 hash: 9aff15987eb75f2c672acb7574c3eb1c
Detection ratio: 2 / 47
First submission: 2014-07-16 23:04:17 UTC
VirusTotal link: https://www.virustotal.com/en/file/47c20ae8c768c8169f9e49d7dd715a8de03de23d6449ea3f077094a76cd7c4e6/analysis/
Added an .exe file extension on the file to show the proper icon.
TRAFFIC FROM THE MALWR SANDBOX ANALYSIS
HTTP GET REQUESTS:
- 23:25:27 UTC - 192.168.56.102: - 204.188.238[.]141:80 - oluwaisinvolve[.]info - GET /kings/metro/admin/1/ppptp.jpg
- 23:25:55 UTC - 192.168.56.102: - 204.188.238[.]141:80 - oluwaisinvolve[.]info - POST /kings/metro/admin/1/secure.php
- 23:25:55 UTC - 192.168.56.102: - 173.194.78[.]103:80 - www.google[.]com - GET /webhp
- 23:25:56 UTC - 192.168.56.102: - 173.194.78[.]94:80 - www.google[.]nl - GET /webhp?gfe_rd=cr&ei=-gnHU6KCAoqe8gPN8YHIBg
- 23:25:57 UTC - 192.168.56.102: - 204.188.238[.]141:80 - oluwaisinvolve[.]info - POST /kings/metro/admin/1/secure.php
INFO ON THE MALWARE CALLBACK DOMAIN:
- Domain name: oluwaisinvolve[.]info
- Domain Status: Registered And Active Website
- Registered through: Web Commerce Communications Limited dba (WebNic.cc)
- Registered on: 2014-04-08
- Updated on: 2014-07-04
- Expires on: 2015-04-08
- Registrant email address: salesadvert19@gmail[.]com (associated with ~36 domains)
- Registrant name: Neslon Williams (associated with ~29 other domains)
- Registrant country: DE (Germany)
- IP Address: 204.188.238[.]143 (354 other sites hosted on this server)
- IP Location: US - Pennsylvania - Bethel Park - Sharktech
- ASN: US AS46844 ST-BGP - Sharktech,US (registered Mar 31, 2009)

Viewing the malware callback domain name in a web browser.
ALERTS
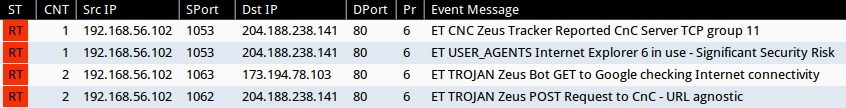
Emerging Threats and ETPRO signature hits from Sguil after using tcpreplay on Security Onion:
- 192.168.56.102: - 204.188.238[.]141:80 - ET CNC Zeus Tracker Reported CnC Server TCP group 11 (sid:2404170)
- 192.168.56.102: - 204.188.238[.]141:80 - ET USER_AGENTS Internet Explorer 6 in use - Significant Security Risk (sid:2010706)
- 192.168.56.102: - 173.194.78[.]103:80 - ET TROJAN Zeus Bot GET to Google checking Internet connectivity (sid:2013076)
- 192.168.56.102: - 204.188.238[.]141:80 - ET TROJAN Zeus POST Request to CnC - URL agnostic (sid:2013976)
NOTE: tcpreplay didn't send all of the packets when I tried playing back the malwr.com pcap, so these may not be all the Emerging Threats signatures.
Sourcefire VRT signature reading the PCAP with Snort 2.9.6.0 on Ubuntu 14.04 LTS:
- 2014-07-16 23:25:27 UTC - 192.168.56.102: - 204.188.238[.]141:80 - [1:30270:2] MALWARE-CNC Win.Trojan.Zbot configuration file download
- 2014-07-16 23:25:55 UTC - 192.168.56.102: - 204.188.238[.]141:80 - [1:30271:2] MALWARE-CNC Win.Trojan.Zbot drop zone file upload
- 2014-07-16 23:25:57 UTC - 192.168.56.102: - 204.188.238[.]141:80 - [1:30271:2] MALWARE-CNC Win.Trojan.Zbot drop zone file upload
FOLLOW-UP NOTES
The Sourcefire VRT signatures above all reference the following malware submitted to Virus Total in October 2013:
MD5 hash: f2461d578f5948ac803d03f40100e240
File size: 193,749 bytes
Detection ratio: 41 / 53
First submission: 2013-10-25 21:10:04 UTC
http://virustotal.com/en/file/2EE81DFCB16F6E9D57CBD114BF16E4237572D1356220BC58B74306841A0D0AE4/analysis/
The same malware was submitted to Malwr almost 5 months later, and it shows traffic patterns similar to today's malware sample:
- 111.90.133[.]131:80 - blessmyhustles[.]com - GET /gee/metro/admin/1/ppptp.jpg
- 111.90.133[.]131:80 - blessmyhustles[.]com - GET /cgi-sys/suspendedpage.cgi
Both blessmyhustles[.]com and today's callback domain oluwaisinvolve[.]info have the same registrant email address in their whois record: salesadvert19@gmail[.]com
Click here to return to the main page.