2014-07-23 - FLASHPACK EK FROM 178.79.165[.]213 - DRONIKASO.DENISEPHOTOGRAPHER[.]COM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 198.143.153[.]34 - www.emol[.]com - Compromised website
- 184.154.117[.]170 - apps.emol[.]com - Javascript that leads to Cushion redirect
- 37.187.79[.]14 - ae6t91t1amist11vbnbrux7.1911censusuk[.]net - Cushion redirect
- 37.187.79[.]14 - ae6t91t1amist11vbnbrux7535453e0a0c09589142bb43a6ef699596.1911censusuk[.]net - Cushion redirect
- 178.79.165[.]213 - dronikaso.denisephotographer[.]com - FlashPack EK
- 212.58.4[.]190 - Post-infection traffic on TCP ports 19413 and 47133
COMPROMISED WEBSITE AND REDIRECT:
- 01:44:41 UTC - 198.143.153[.]34:80 - www.emol[.]com - GET /
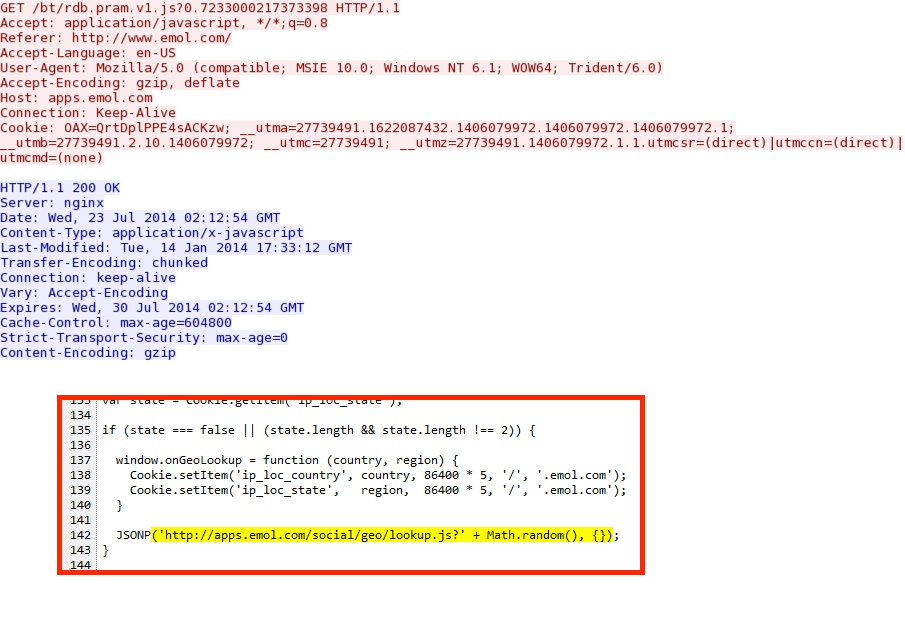
- 01:44:49 UTC - 184.154.117[.]170:80 - apps.emol[.]com - GET /bt/rdb.pram.v1.js?0.7233000217373398
- 01:44:49 UTC - 184.154.117[.]170:80 - apps.emol[.]com - GET /bt/ping
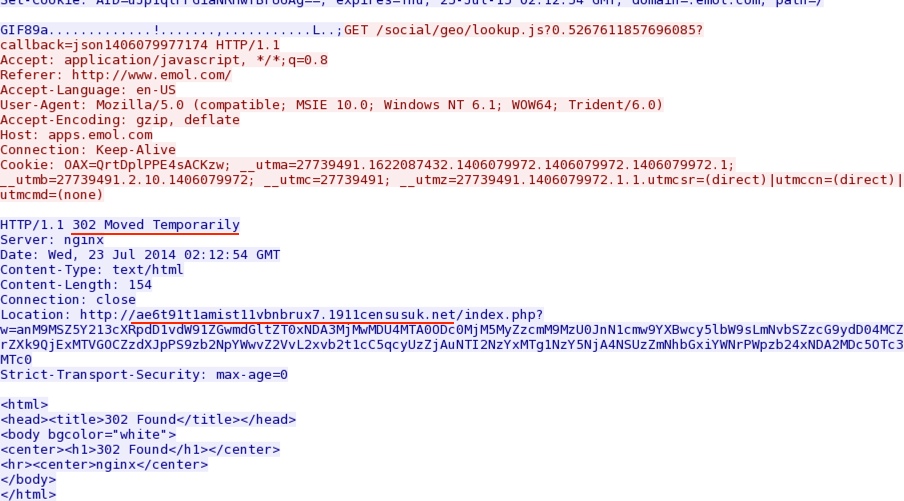
- 01:44:49 UTC - 184.154.117[.]170:80 - apps.emol[.]com - GET /social/geo/lookup.js?0.5267611857696085?callback=json1406079977174
- 01:44:50 UTC - 37.187.79[.]14:80 - ae6t91t1amist11vbnbrux7.1911censusuk[.]net - GET /index.php?w=anM9MSZ5Y213cXRpdD1vdW91Z
GwmdGltZT0xNDA3MjMwMDU4MTA0ODc0MjM5MyZzcmM9MzU0JnN1cmw9YXBwcy5lbW9sLmNvbSZzcG9ydD04MCZrZXk9QjExMTVGOCZzdXJpPS9zb2Np
YWwvZ2VvL2xvb2t1cC5qcyUzZjAuNTI2NzYxMTg1NzY5NjA4NSUzZmNhbGxiYWNrPWpzb24xNDA2MDc5OTc3MTc0 - 01:44:54 UTC - 37.187.79[.]14:80 - ae6t91t1amist11vbnbrux7535453e0a0c09589142bb43a6ef699596.1911censusuk[.]net - GET /index2.php
FLASHPACK EK:
- 01:44:55 UTC - 178.79.165[.]213:80 - dronikaso.denisephotographer[.]com - GET /kafingar/dhelicaba/xentirei.php
- 01:44:56 UTC - 178.79.165[.]213:80 - dronikaso.denisephotographer[.]com - GET /kafingar/dhelicaba/mhardeyedu.js
- 01:44:59 UTC - 178.79.165[.]213:80 - dronikaso.denisephotographer[.]com - GET /kafingar/dhelicaba/kbuttons.php
- 01:44:59 UTC - 178.79.165[.]213:80 - dronikaso.denisephotographer[.]com - GET /kafingar/dhelicaba/rholdingp.php
- 01:44:59 UTC - 178.79.165[.]213:80 - dronikaso.denisephotographer[.]com - GET /kafingar/dhelicaba/dgambleanda.php
- 01:44:59 UTC - 178.79.165[.]213:80 - dronikaso.denisephotographer[.]com - GET /kafingar/dhelicaba/rcaptains.php
- 01:44:59 UTC - 178.79.165[.]213:80 - dronikaso.denisephotographer[.]com - GET /kafingar/dhelicaba/lavailk/6c40f9e.swf
- 01:45:00 UTC - 178.79.165[.]213:80 - dronikaso.denisephotographer[.]com - GET /kafingar/dhelicaba/lavailk/cad39.swf
- 01:45:07 UTC - 178.79.165[.]213:80 - dronikaso.denisephotographer[.]com - GET /kafingar/dhelicaba/uimmediatej.php?id=4
POST-INFECTION TRAFFIC:
- 01:48:26 UTC - 212.58.4[.]190:19413 - GET /stat?uid=100&downlink=1111&uplink=1111&id=0007F594&statpass=bpass&version=20140721
&features=30&guid=6eb60c1d-87ca-4daf-82f3-b3fd9d267c6a&comment=20140721&p=0&s= - 01:48:26 UTC - 212.58.4[.]190:47133 - TCP callback traffic by Glupteba malware
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOITS:
File name: 2014-07-23-FlashPack-EK-flash-exploit-01.swf
File size: 8,387 bytes
MD5 hash: 7d24428037f9dbf5a5c93e87640ba171
Detection ratio: 2 / 52
First submission: 2014-07-18 01:58:41 UTC
VirusTotal link: https://www.virustotal.com/en/file/ccbb1670756811d550f4f624e036c61898a0f2b99418adae01f48584a819160c/analysis/
File name: 2014-07-23-FlashPack-EK-flash-exploit-02.swf
File size: 9,079 bytes
MD5 hash: b4015d0ab77c92881691d60cdf1cc69c
Detection ratio: 0 / 53
First submission: 2014-07-24 00:49:25 UTC
VirusTotal link: https://www.virustotal.com/en/file/ccbb1670756811d550f4f624e036c61898a0f2b99418adae01f48584a819160c/analysis/
MALWARE PAYLOAD:
File name: 2014-07-23-FlashPack-EK-malware-payload.exe
File size: 81,639 bytes
MD5 hash: d67be8ace8999067e95322990a71c3b2
Detection ratio: 27 / 53
First submission: 2014-07-23 02:04:00 UTC
VirusTotal link: https://www.virustotal.com/en/file/20786294a971bb33527e8444c86233078c242f1dbb00334fe2d9df59aa8de62b/analysis/
ALERTS
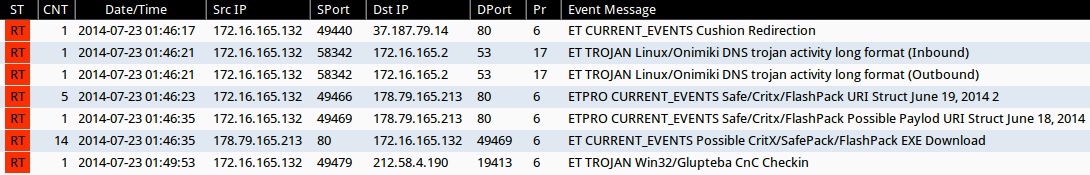
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (not including ET INFO or ET POLICY rules):
- 2014-07-23 01:46:17 UTC - 37.187.79[.]14:80 - ET CURRENT_EVENTS Cushion Redirection (sid:2017552)
- 2014-07-23 01:46:21 UTC - [local host]:53 - ET TROJAN Linux/Onimiki DNS trojan activity long format (Inbound) (sid:2018276)
- 2014-07-23 01:46:21 UTC - [local host]:53 - ET TROJAN Linux/Onimiki DNS trojan activity long format (Outbound) (sid:2018275)
- 2014-07-23 01:46:23 UTC - 178.79.165[.]213:80 - ETPRO CURRENT_EVENTS Safe/Critx/FlashPack URI Struct June 19, 2014 2 (sid:2808213)
- 2014-07-23 01:46:35 UTC - 178.79.165[.]213:80 - ETPRO CURRENT_EVENTS Safe/Critx/FlashPack Possible Paylod URI Struct June 18, 2014 (sid:2808209)
- 2014-07-23 01:46:35 UTC - 178.79.165[.]213:80 - ET CURRENT_EVENTS Possible CritX/SafePack/FlashPack EXE Download (sid:2017297)
- 2014-07-23 01:49:53 UTC - 212.58.4[.]190:19413 - ET TROJAN Win32/Glupteba CnC Checkin (sid:2013293)
Sourcefire VRT ruleset from Snort 2.9.6.0 on Ubuntu 14.04 LTS:
- 2014-07-23 01:44:56 UTC - 178.79.165[.]213:80 - [1:23878:8] BROWSER-PLUGINS Oracle JRE Deployment Toolkit ActiveX clsid access attempt
- 2014-07-23 01:45:07 UTC - 178.79.165[.]213:80 - [1:11192:16] FILE-EXECUTABLE download of executable content
- 2014-07-23 01:45:07 UTC - 178.79.165[.]213:80 - [1:24791:3] EXPLOIT-KIT CritX exploit kit Portable Executable download
- 2014-07-23 01:45:07 UTC - 178.79.165[.]213:80 - [1:29167:1] EXPLOIT-KIT CritX exploit kit payload download attempt
- 2014-07-23 01:45:07 UTC - 178.79.165[.]213:80 - [1:28593:1] EXPLOIT-KIT Multiple exploit kit payload download
- 2014-07-23 01:45:07 UTC - 178.79.165[.]213:80 - 172.16.165.132:49469 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- 2014-07-23 01:48:26 UTC - 212.58.4[.]190:19413 - [1:30977:1] MALWARE-CNC Win.Trojan.Jaik variant outbound connection
TRAFFIC LEADING TO FLASHPACK EK
apps.emol[.]com/bt/rdb.pram.v1.js?0.7233000217373398
apps.emol[.]com/social/geo/lookup.js?0.5267611857696085?callback=json1406079977174
ae6t91t1amist11vbnbrux7535453e0a0c09589142bb43a6ef699596.1911censusuk[.]net/index2.php
Click here to return to the main page.