2014-07-29 - MALWARE INFECTION FROM EMAIL ATTACHMENT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- This email looks like it went to a Debian developers mailing list.
- The attachment, a malicious Word document, was first noted on 2014-07-10.
TODAY'S PHISHING EMAIL
SCREENSHOT:
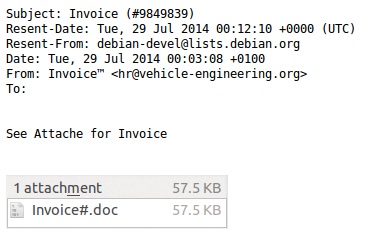
MESSAGE TEXT:
Subject: Invoice (#9849839)
Resent-Date: Tue, 29 Jul 2014 00:12:10 +0000 (UTC)
Resent-From: debian-devel@lists.debian[.]org
Date: Tue, 29 Jul 2014 00:03:08 +0100
From: Invoice™ <hr@vehicle-engineering[.]org>
To: debian-devel <debian-devel@lists.debian[.]org>
See Attache for Invoice
SOME OF THE HEADER INFORMATION:
PRELIMINARY MALWARE ANALYSIS
EMAIL ATTACHMENT:
File name: Invoice#.doc
File size: 58,880 bytes
MD5 hash: 5f6fe4c41ea8f2a4df433148876335c4
Detection ratio: 10 / 54
First submission: 2014-07-10 09:39:57 UTC
VirusTotal link: https://www.virustotal.com/en/file/7ca98c64631632e6ae48187c7adb43c148e55c7e11c38a1bfe2b270a3632b5a9/analysis/
FILE DROPPED ON VM:
File name: svhost.exe
File size: 271.872 bytes
MD5 hash: 3a38fb10925a8f259529dd93ec355dbf
Detection ratio: 30 / 54
First submission: 2014-07-20 06:10:11 UTC
VirusTotal link: https://www.virustotal.com/en/file/4993cdb04d90b27091d1366322fdc7fa018f0b3ed0287072a5ec0c68dec46cee/analysis/
TRAFFIC FROM THE INFECTION
TRAFFIC GENERATED BY THE MALICIOUS WORD DOCUMENT:
- 46.44.132[.]204 - goldriverlinedancers[.]nl/components/dancers/svhost.exe
POST-INFECTION TRAFFIC FROM DROPPED MALWARE:
- Only saw repeated connection attempts to 85.153.24[.]114 over TCP port 2902. All attempted TCP connections were reset by the server.
Click here to return to the main page.