2014-07-30 - RIG EK FROM 194.58.101[.]116 - FINISH.RESINBONDING[.]COM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
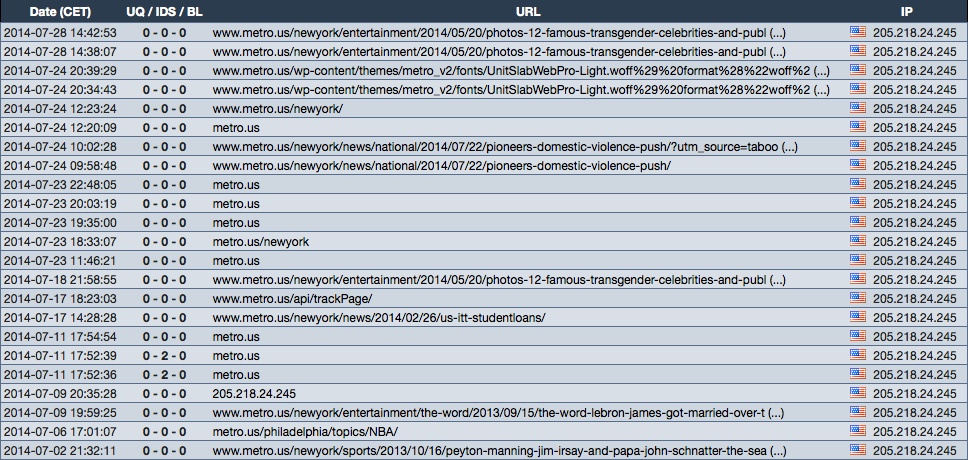
- Since early July 2014, people have been reporting pages from www.metro[.]us to the various malware-related sites I normally review.
- Today I used that site to generate Rig exploit kit traffic and infect a VM with (what I believe is) a Carberp/Rovnix variant.
- Indicators of possible compromise have been noted starting earlier this month:
- From Scumware:
- From Clean MX VirusWatch:
- From URLquery
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 205.218.24[.]245 - www.metro[.]us - Compromised website
- 78.47.178[.]164 - gagle[.]us - Redirect
- 194.58.101[.]116 - finish.resinbonding[.]com - Rig EK
- 91.220.131[.]196 - Post-infection traffic over TCP port 443 (not HTTPS, not HTTP)
COMPROMISED WEBSITE AND REDIRECT CHAIN:
- 2014-07-30 00:54:10 UTC - 205.218.24[.]245:80 - www.metro[.]us - GET /
- 2014-07-30 00:54:11 UTC - 205.218.24[.]245:80 - www.metro[.]us - GET /newyork/
- 2014-07-30 00:54:16 UTC - 78.47.178[.]164 :80 - gagle[.]us - GET /?mt
- 2014-07-30 00:54:17 UTC - 78.47.178[.]164 :80 - gagle[.]us - GET /link.php
RIG EK:
- 2014-07-30 00:54:17 UTC - 194.58.101[.]116:80 - finish.resinbonding[.]com - GET /?PHPSSESID=
njrMNruDMh7HApzBKv7cTKZNKU7YHVnYmMzMhe6JVg|Nzg0MTZhZGVjM2FjODFjMTRhMWZkMjViODhjOTg0MDQ - 2014-07-30 00:54:22 UTC - 194.58.101[.]116:80 - finish.resinbonding[.]com - GET /index.php?req=mp3&num=32&PHPSSESID=
njrMNruDMh7HApzBKv7cTKZNKU7YHVnYmMzMhe6JVg%7CNzg0MTZhZGVjM2FjODFjMTRhMWZkMjViODhjOTg0MDQ - 2014-07-30 00:54:27 UTC - 194.58.101[.]116:80 - finish.resinbonding[.]com - GET /index.php?req=swf&num=8778&PHPSSESID=
njrMNruDMh7HApzBKv7cTKZNKU7YHVnYmMzMhe6JVg|Nzg0MTZhZGVjM2FjODFjMTRhMWZkMjViODhjOTg0MDQ - 2014-07-30 00:54:27 UTC - 194.58.101[.]116:80 - finish.resinbonding[.]com - GET /index.php?req=xap&PHPSSESID=
njrMNruDMh7HApzBKv7cTKZNKU7YHVnYmMzMhe6JVg|Nzg0MTZhZGVjM2FjODFjMTRhMWZkMjViODhjOTg0MDQ - 2014-07-30 00:54:28 UTC - 194.58.101[.]116:80 - finish.resinbonding[.]com - GET /index.php?req=mp3&num=21637&PHPSSESID=
njrMNruDMh7HApzBKv7cTKZNKU7YHVnYmMzMhe6JVg%7CNzg0MTZhZGVjM2FjODFjMTRhMWZkMjViODhjOTg0MDQ
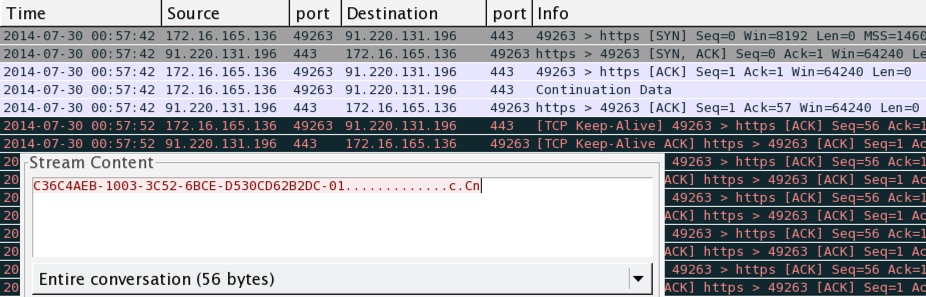
POST-INFECTION TRAFFIC:
- 2014-07-30 00:54:30 UTC - 91.220.131[.]196:443 - C36C4AEB-1003-3C52-6BCE-D530CD62B2DC-01.............c.Cn
- 2014-07-30 00:54:36 UTC - 91.220.131[.]196:443 - C36C4AEB-1003-3C52-6BCE-D530CD62B2DC-01.............c.Cn
- 2014-07-30 00:55:42 UTC - 91.220.131[.]196:443 - C36C4AEB-1003-3C52-6BCE-D530CD62B2DC-01.............c.Cn
- 2014-07-30 00:56:41 UTC - 91.220.131[.]196:443 - C36C4AEB-1003-3C52-6BCE-D530CD62B2DC-01.............c.Cn
- 2014-07-30 00:57:42 UTC - 91.220.131[.]196:443 - C36C4AEB-1003-3C52-6BCE-D530CD62B2DC-01.............c.Cn
- 2014-07-30 00:59:03 UTC - 91.220.131[.]196:443 - C36C4AEB-1003-3C52-6BCE-D530CD62B2DC-01.............c.Cn
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2014-07-30-Rig-EK-flash-exploit.swf
File size: 4,459 bytes
MD5 hash: 9ae59cc660c22ed9c61b70fd61544b0f
Detection ratio: 0 / 54
First submission: 2014-07-30 01:00:47 UTC
VirusTotal link: https://www.virustotal.com/en/file/68b53f82bc7f65dc672699dd72ecd8583b15cf0135ca64922350410238b42f4a/analysis/
SILVERLIGHT EXPLOIT:
File name: 2014-07-30-Rig-EK-silverlight-exploit.xap
File size: 48,324 bytes
MD5 hash: 634437ccafcba0e951d1d1c034f8d736
Detection ratio: 3 / 53
First submission: 2014-07-28 17:46:17 UTC
VirusTotal link: https://www.virustotal.com/en/file/632c769483c1d63e59cb1f9f83375c2fc7aa6fb47d5e13a0898084453090597d/analysis/
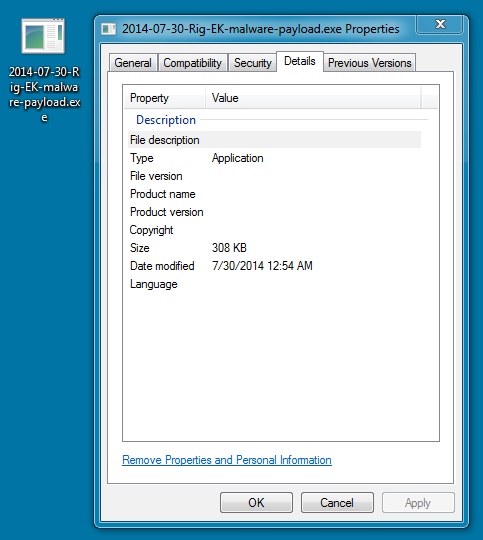
MALWARE PAYLOAD:
File name: 2014-07-30-Rig-EK-malware-payload.exe
File size: 315,392 bytes
MD5 hash: e821d7334d2ecc6bdbe899fa67830dad
Detection ratio: 2 / 53
First submission: 2014-07-30 01:00:00 UTC
VirusTotal link: https://www.virustotal.com/en/file/995c0a36805fe6a95aee37748e24230edad1350321dc6cd7acf0c2de0326010f/analysis/
SNORT EVENTS
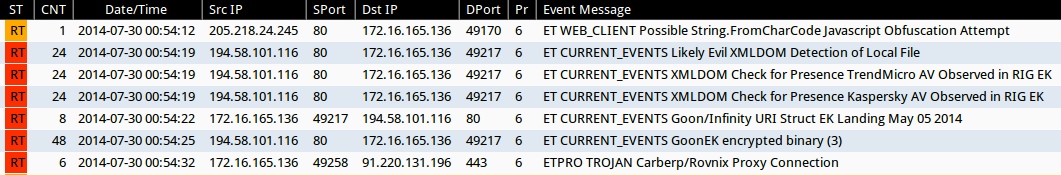
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (not including ET INFO or ET POLICY rules):
- 00:54:12 UTC - 205.218.24[.]245:80 - ET WEB_CLIENT Possible String.FromCharCode Javascript Obfuscation Attempt (sid:2011347)
- 00:54:19 UTC - 194.58.101[.]116:80 - ET CURRENT_EVENTS Likely Evil XMLDOM Detection of Local File (sid:2018783)
- 00:54:19 UTC - 194.58.101[.]116:80 - ET CURRENT_EVENTS XMLDOM Check for Presence TrendMicro AV Observed in RIG EK (sid:2018757)
- 00:54:19 UTC - 194.58.101[.]116:80 - ET CURRENT_EVENTS XMLDOM Check for Presence Kaspersky AV Observed in RIG EK (sid:2018756)
- 00:54:22 UTC - 194.58.101[.]116:80 - ET CURRENT_EVENTS Goon/Infinity URI Struct EK Landing May 05 2014 (sid:2018441)
- 00:54:25 UTC - 194.58.101[.]116:80 - ET CURRENT_EVENTS GoonEK encrypted binary (3) (sid:2018297)
- 00:54:32 UTC - 91.220.131[.]196:443 - ETPRO TROJAN Carberp/Rovnix Proxy Connection (sid:2808448)
Sourcefire VRT ruleset from Snort 2.9.6.0 on Ubuntu 14.04 LTS:
- 00:54:22 UTC - 194.58.101[.]116:80 - [1:30936:3] EXPLOIT-KIT Goon/Infinity/Rig exploit kit outbound uri structure
- 00:54:25 UTC - 194.58.101[.]116:80 - [1:30934:2] EXPLOIT-KIT Goon/Infinity/Rig exploit kit encrypted binary download
- 00:54:27 UTC - 194.58.101[.]116:80 - [1:30936:3] EXPLOIT-KIT Goon/Infinity/Rig exploit kit outbound uri structure
- 00:54:27 UTC - 194.58.101[.]116:80 - [1:30936:3] EXPLOIT-KIT Goon/Infinity/Rig exploit kit outbound uri structure
- 00:54:28 UTC - 194.58.101[.]116:80 - [1:30936:3] EXPLOIT-KIT Goon/Infinity/Rig exploit kit outbound uri structure
- 00:54:28 UTC - 194.58.101[.]116:80 - [1:28612:2] EXPLOIT-KIT Multiple exploit kit Silverlight exploit download
- 00:54:28 UTC - 194.58.101[.]116:80 - [1:28612:2] EXPLOIT-KIT Multiple exploit kit Silverlight exploit download
- 00:54:31 UTC - 194.58.101[.]116:80 - [1:30934:2] EXPLOIT-KIT Goon/Infinity/Rig exploit kit encrypted binary download
SCREEN SHOTS FROM THE TRAFFIC
Malicious iframe in page from compromised server:
Redirect chain pointing to Rig exploit kit:
After the Rig EK infection, here's an example of the traffic that triggered snort events for ETPRO TROJAN Carberp/Rovnix Proxy Connection:
Click here to return to the main page.