2014-08-01 - ZEUS MALWARE INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
ASSOCIATED EMAILS
SCREENSHOTS:
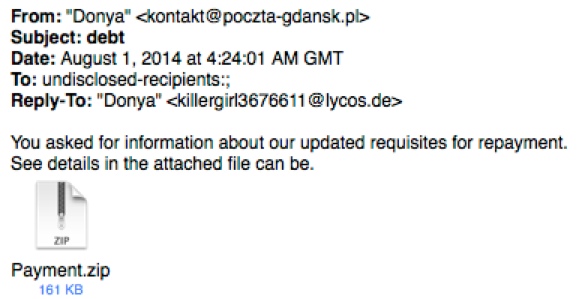
MESSAGE TEXT (FIRST EMAIL):
From: "Donya" <kontakt@poczta-gdansk[.]pl>
Subject: debt
Date: August 1, 2014 at 4:24:01 AM GMT
To: undisclosed-recipients:;
Reply-To: "Donya" <killergirl3676611@lycos[.]de>
You asked for information about our updated requisites for repayment.
See details in the attached file can be.
Attachment: Payment.zip (161 KB)
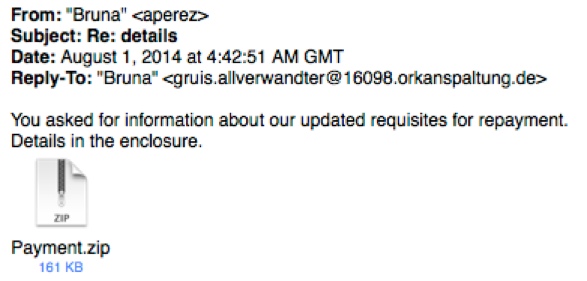
MESSAGE TEXT (SECOND EMAIL):
From: "Bruna" <aperez>
Subject: Re: details
Date: August 1, 2014 at 4:42:51 AM GMT
Reply-To: "Bruna" <gruis.allverwandter@16098.orkanspaltung[.]de>
You asked for information about our updated requisites for repayment.
Details in the enclosure.
Attachment: Payment.zip (161 KB)
PRELIMINARY MALWARE ANALYSIS
FILE ATTACHMENT FROM BOTH EMAILS:
File name: Payment.zip
File size: 160,655 bytes
MD5 hash: 4e29b73523bfef83660badd169622aca
Detection ratio: 0 / 54
First submission: 2014-07-31 22:36:39 UTC
VirusTotal link: https://www.virustotal.com/en/file/4e6f47b5c0a15ed9e8e29fca04ef8dc6eba741ecf5e9274655debdfa8fa7350b/analysis/
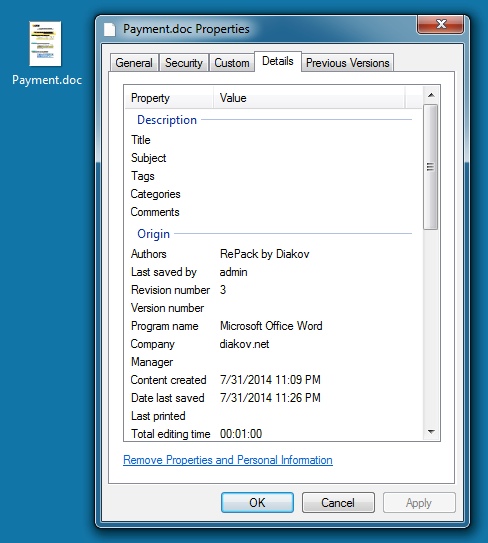
EXTRACTED WORD DOCUMENT:
File name: Payment.doc
File size: 363,520 bytes
MD5 hash: 6eff822dff0d385321d2bacef4537b1c
Detection ratio: 0 / 53
First submission: 2014-08-01 13:34:03 UTC
VirusTotal link: https://www.virustotal.com/en/file/12a8f8b09a1952404d8e97fbbe9a8e23941af4298f57948f7b877f6fdb9298da/analysis/
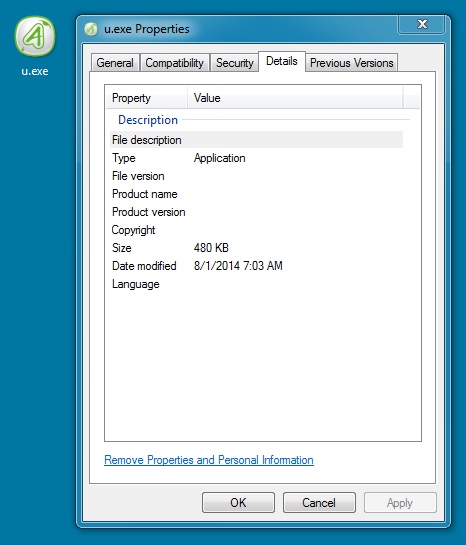
FOLLOW-UP MALWARE (ZEUS)
File name: u.exe
File size: 491,520 bytes
MD5 hash: fa936019d39549ccbb22a05724fb1720
Detection ratio: 6 / 54
First submission: 2014-08-01 02:58:51 UTC
VirusTotal link: https://www.virustotal.com/en/file/992a5ffa1a51492198ccba2a2351640859433a81ab24bafdb92b3b60066e6a9c/analysis/
TRAFFIC FROM THE MALWARE
MALICIOUS WORD DOCUMENT CALLS FOR ZEUS MALWARE:
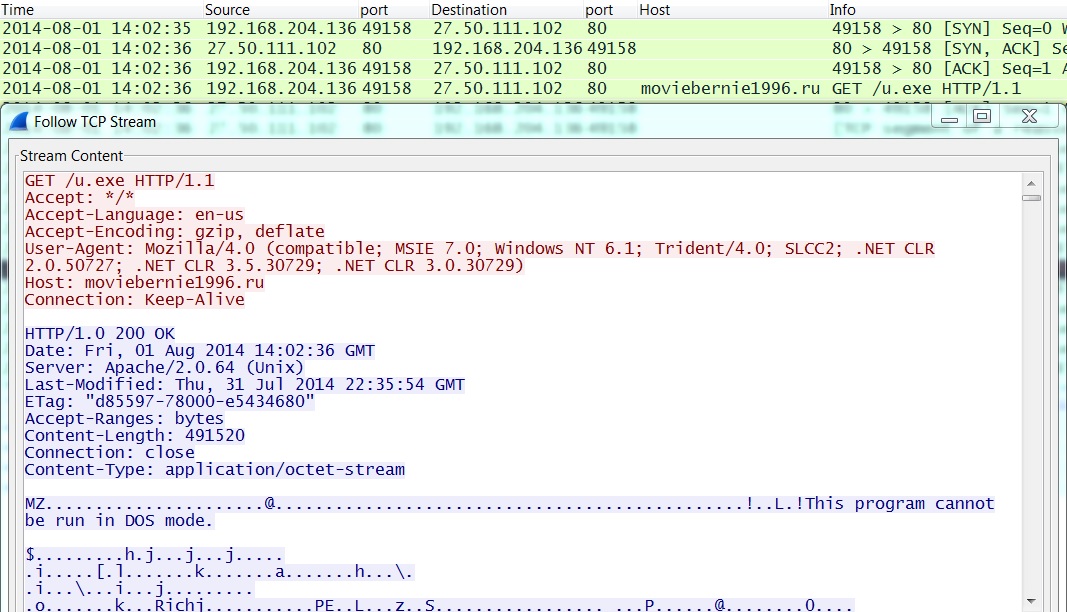
- 2014-08-01 14:02:36 UTC - 27.50.111[.]102:80 - moviebernie1996[.]ru - GET /u.exe
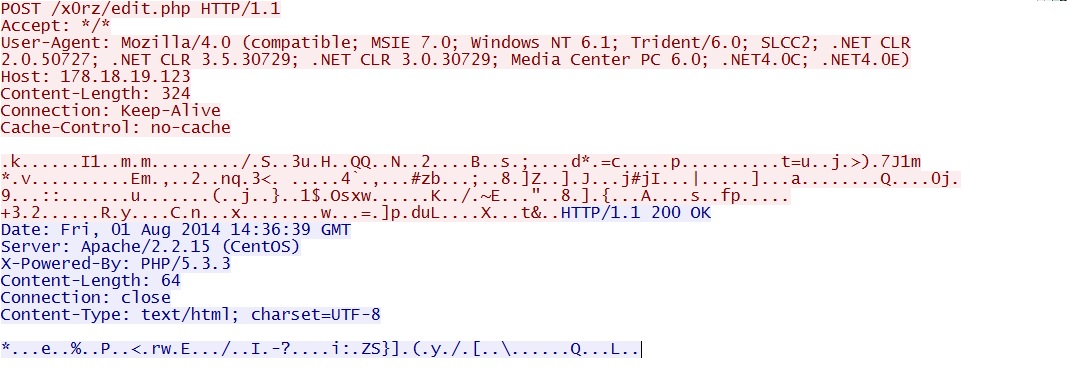
SANDBOX ANALYSIS ON FOLLOW-UP MALWARE:
- 2014-08-01 14:36:40 UTC - 173.194.46[.]116:80 - www.google[.]com - GET /webhp
- 2014-08-01 14:36:40 UTC - 23.4.53[.]163:80 - crl.geotrust[.]com - GET /crls/secureca.crl
- 2014-08-01 14:36:40 UTC - 199.7.54[.]72:80 - gtglobal-ocsp.geotrust[.]com - GET
/MEQwQjBAMD4wPDAJBgUrDgMCGgUABBSxtDkXkBa3l3lQEfFgudSiPNvt7gQUAPkqw0GRtsnCuD5V8sCXEROgByACAwI6aQ%3D%3D - 2014-08-01 14:36:40 UTC - 173.194.46[.]104:80 - clients1.google[.]com - GET
/ocsp/MEkwRzBFMEMwQTAJBgUrDgMCGgUABBTy4Gr5hYodjXCbSRkjeqm1Gih%2BZAQUSt0GFhu89mi1dvWBtrtiGrpagS8CCCwY4Esh3h%2B%2F - 2014-08-01 14:36:41 UTC - 178.18.19[.]123:80 - 178.18.19[.]123 - POST /x0rz/edit.php
- 2014-08-01 14:37:04 UTC - 93.184.215[.]200:80 - mscrl.microsoft[.]com - GET /pki/mscorp/crl/mswww(6).crl
- 2014-08-01 14:40:35 UTC - 173.194.46[.]116:80 - www.google[.]com - GET /webhp
- 2014-08-01 14:40:36 UTC - 178.18.19[.]123:80 - 178.18.19[.]123 - POST /x0rz/edit.php
- 2014-08-01 14:44:30 UTC - 173.194.46[.]116:80 - www.google[.]com - GET /webhp
- 2014-08-01 14:44:31 UTC - 178.18.19[.]123:80 - 178.18.19[.]123 - POST /x0rz/edit.php
ALERTS ON THE SANDBOX ANALYSIS

Emerging Threats and ETPRO rulesets from Sguil on Security Onion (not including ET INFO or ET POLICY rules):
- 2014-08-01 14:36:40 UTC - 173.194.46[.]116:80 - ET TROJAN Zeus Bot GET to Google checking Internet connectivity (sid:2013076)
- 2014-08-01 14:36:41 UTC - 178.18.19[.]123:80 - ET TROJAN Zeus POST Request to CnC - URL agnostic (sid:2013976)
- 2014-08-01 14:36:41 UTC - 178.18.19[.]123:80 - ET TROJAN Generic - POST To .php w/Extended ASCII Characters (sid:2016858)
Sourcefire VRT ruleset from Snort 2.9.6.0 on Ubuntu 14.04 LTS:
- 2014-08-01 14:36:40 UTC - 173.194.46[.]116:80 - [1:30570:2] MALWARE-CNC Win.Trojan.Zeus variant outbound connection attempt
- 2014-08-01 14:40:35 UTC - 173.194.46[.]116:80 - [1:30570:2] MALWARE-CNC Win.Trojan.Zeus variant outbound connection attempt
- 2014-08-01 14:44:30 UTC - 173.194.46[.]116:80 - [1:30570:2] MALWARE-CNC Win.Trojan.Zeus variant outbound connection attempt
Click here to return to the main page.